SCCM Architecture Diagrams Decision Making Guide for 2023 or later | Configuration Manager | Microsoft Intune. I have prepared a sample SCCM Architecture Visio Template ready to download from GitHub.
SCCM Infrastructure setup step-by-step guide is available with HTMD for free of cost – New ConfigMgr Primary Server Installation Step By Step Guide.
SCCM (ConfigMgr) Architecture decisions are based on loads of factors, including requirement gathering understanding of the existing infrastructure and environment. This guide is to give you some tips and tricks along with best practices.
The design of the SCCM hierarchy entirely depends upon your network and computing environment and your business requirements. There is no common design that suits every environment.
We can plan to implement Configuration Manager by using the minimal number of servers and the least amount of administration overhead to meet your organization’s goals.
Video What are Intune Architecture Considerations or Intune Design Considerations?
Existing Investments (External to Intune) – Helps to make better Intune Design/Architecture Decisions Cloudification Initiatives for your organizations.
Azure AD Join Vs Hybrid AAD Join – How this impacts Intune Architecture/Design Decisions Kerberos Vs Modern Authentication Organization is looking for another migration project in 3-4 years? Feature parity with Hybrid AAD Join Complex to design and implement.
SCCM Architecture Decisions
Let’s quickly list down some of the key decisions that you need to take while planning to implement a new SCCM infrastructure.
#1 – Double confirm (SCCM or Intune?) whether you want to build the SCCM infrastructure or use Microsoft Intune as a SaaS solution. Personally, I would go with Intune if this is a new infrastructure and you don’t have any existing SCCM infra.

#2 – Flat SCCM Hierarchy using Peer to Peer / Client Cache / DO technologies. Try to build a flat SCCM hierarchy with less number of site servers and site systems servers using Cloud integrated technologies such as SCCM Cloud Management Gateway and Tenant Attach.
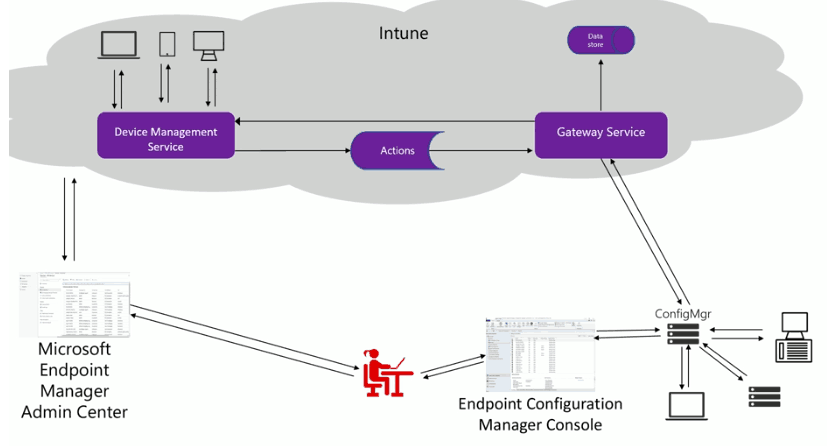
The design decisions will be based on the existing SCCM/ConfigMgr CB environment and will replicate some of the features as per the requirement. An SCCM solution will be implemented to provide device management facilities for fully managed Windows servers and Windows endpoints.
A standalone Intune platform will also be installed on managed mobile devices (iOS, Android, and Windows 10 modern devices via MDM channel).
Contents
- SCCM Servers On-Premises or AZURE?
- CAS and NO CAS SCCM Server
Intune Hybrid – Intune Standalone?- Integration with ISVs ServiceNow/Remedy?
- Windows 10 Co-Management?
- SCCM/Intune High Availability-DR Options?
- Intune + SCCM Architecture Diagram
- Other Design Decisions
SCCM Servers On-Premises or AZURE?
Can we install SCCM/ConfigMgr CB infrastructure in Microsoft Azure? Installing SCCM servers in Azure supported? Yes, we can install SCCM CB infra in Microsoft Azure. And this is fully supported by Microsoft.
Microsoft doesn’t provide any supporting statement about hosting SCCM infra in the AWS IaaS solution, but it should work well if all the communication ports are open. I know some customers are running SCCM infra in AWS. This is the first step toward SCCM architecture decision-making.
I think the better option is to look for Intune management as a permanent modern management solution.
Decision – CAS and NO CAS SCCM Server
A CAS (Central Administration Site) is the SCCM/ConfigMgr site server role. I would recommend avoiding SCCM/ConfigMgr CAS server wherever possible.
I don’t think; you need to have an SCCM hierarchy with CAS in 99% scenarios. There are several blog posts about CAS or NO CAS decision-making. “Determine when to use a central administration site (CAS).”
I will surely go with a standalone SCCM primary server in most SCCM infrastructures.
Intune Standalone?
Intune hybrid is no more supported. So the only option is to go with Intune standalone. If you already have SCCM infra, then try using SCCM Tenant Attach and Co-management features.
Do not go with Intune Hybrid Solution with SCCM/ConfigMgr. The hybrid SCCM solution is already removed or deprecated.
Integration with ISVs ServiceNow/Remedy?
Can Intune get integrated with ISVs like ServiceNow or Remedy? SCCM can get integrated with various 3rd parties service providers like ServiceNow or Remedy. IT service management tools are essential for most organizations.
As SCCM is having the vast majority of the market share in the device management world, this is one of the critical points that we should consider while architecture decision making.
Microsoft Intune has a way to hook into ISVs like Remedy and ServiceNow for IT service management and as well as for asset management. This integration can be achieved through Microsoft Graph APIs. But, I didn’t hear anything from Remedy or ServiceNow about Intune integration.
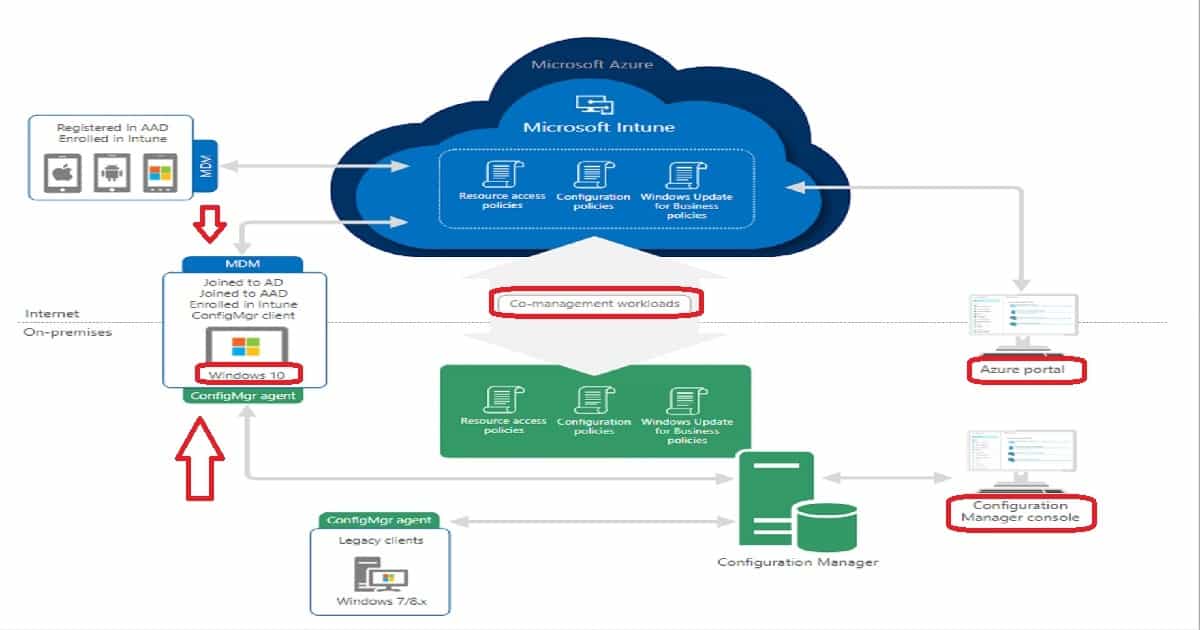
Decision – Windows 10 or Windows 11 Co-Management?
Windows 10 co-management is a dual management capability available with Windows 10 1709 version (Fall Creators Update) and later. Co-management is the bridge between traditional management and modern management.
Managing Windows 10 with Intune is a possible option for some scenarios. But there are some challenges with Intune management for large enterprises. These challenges could be because of
- Win 32 Application Delivery Mechanism
- Application Deployment Automation with ISV
- Bandwidth Issues (Delivery Optimization is only available for some channels)
- Complex Operating System Deployment (OSD) scenarios
- Existing investment in the SCCM echo system
The co-management option could allow the organization to process the workload from on-prem to the cloud. The co-managed Windows 10 devices would be visible in the SCCM and Intune console ( + Database).
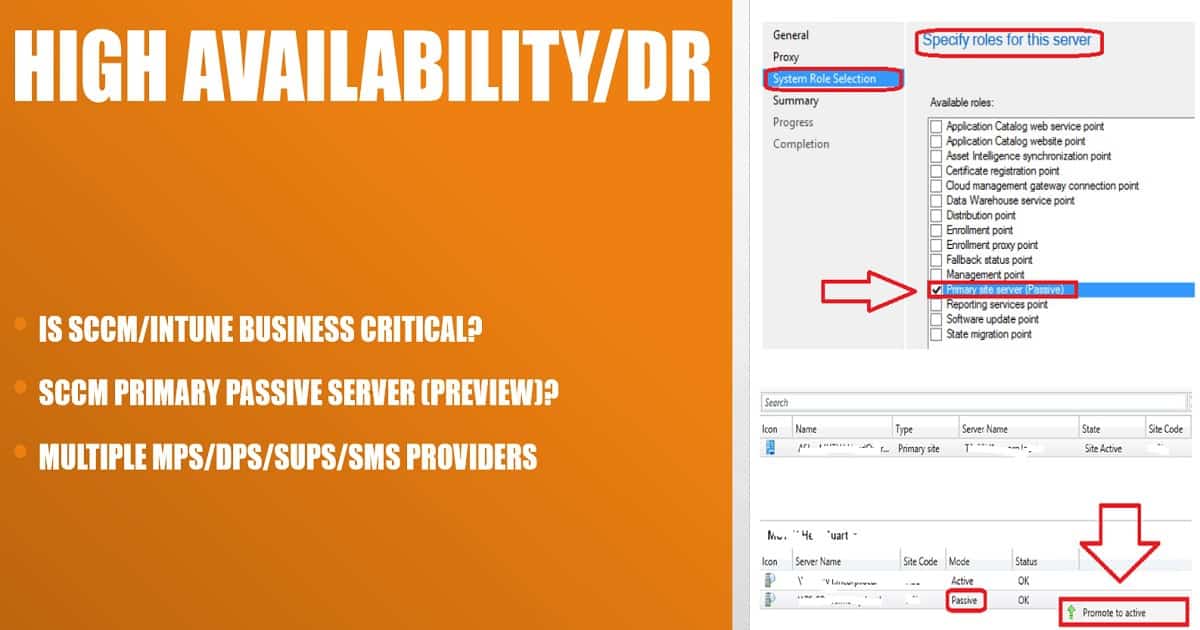
SCCM/Intune High Availability-DR Options?
Is SCCM/Intune treated as a business-critical service within your organization? Most organizations won’t treat SCCM as an essential business service (unlike exchange online).
But, in the modern world, with Intune and co-management options, we may need to rethink this strategy. From my perspective, SCCM is not business-critical. We can live without SCCM for hours (4-8).
What are the DR or High Availability(HA) options available for SCCM? Microsoft SCCM product group (development team) is working to improve the HA/DR options for SCCM/ConfigMgr.
One of the improvements which are already there in the production version of SCCM CB 1706 and later is SQL Availability groups. SQL Server Always On availability groups as high availability and disaster recovery solution for the site database.
When you use the SQL availability group, then, you need to adjust your backup and restore procedure of your SCCM infra.
The SCCM Primary Passive Server installation option is available in the Preview versions of SCCM CB. SCCM’s primary passive site server option is not enabled for production versions of SCCM CB.
The Passive mode SCCM site server is in addition to your existing SCCM primary site server that is in Active mode.
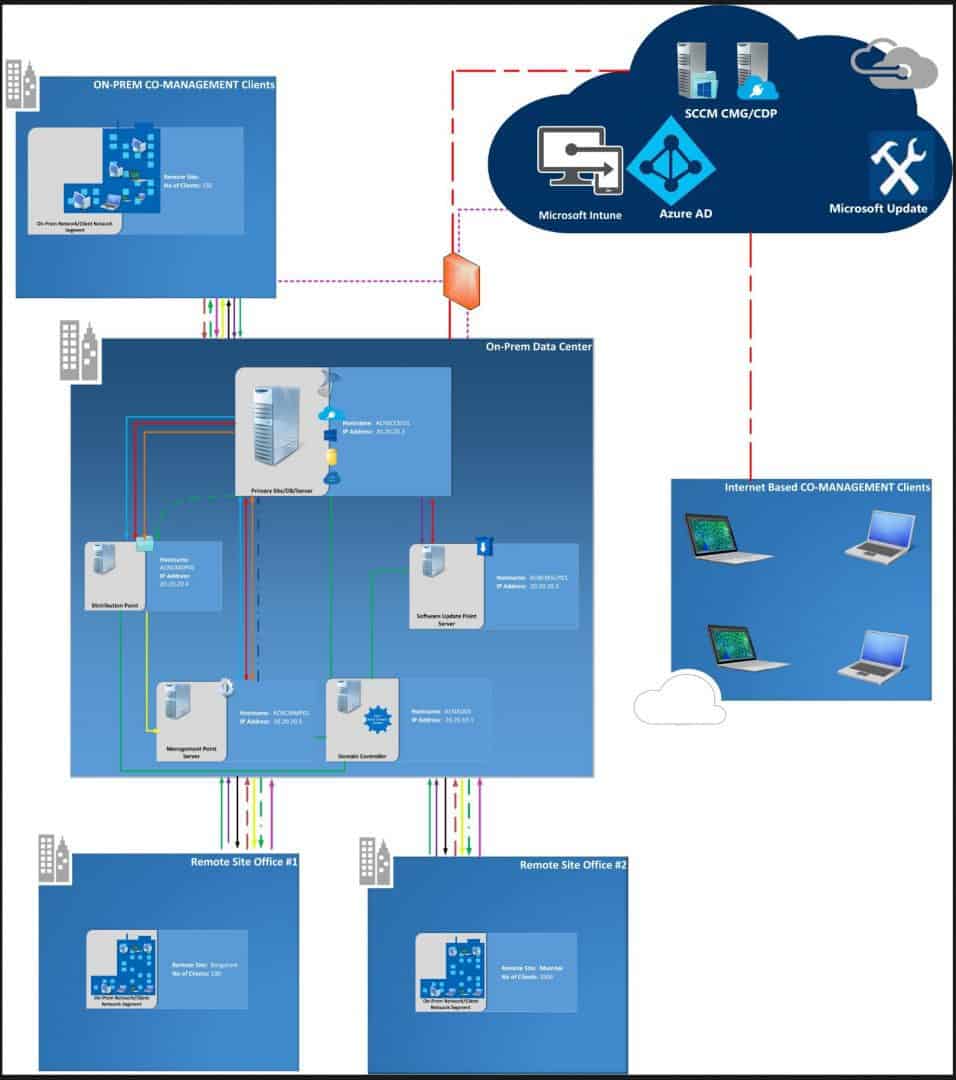
Intune SCCM Architecture Diagram
Following is the sample Intune SCCM/ConfigMgr architecture diagram. This explains the high-level flow between Intune/SCCM/CMG/Cloud DP and the Co-managed Windows 10 devices.
Download Visio Template – SCCM Architecture Visio Template Download From GitHub 1 (anoopcnair.com)
Other Design Decisions
There are several other critical design decisions. I won’t be able to cover all these in this post. Some of them will be discussed at the Bangalore IT Pro event on 16th Dec 2017.
I will try to share the presentation deck after the event.
- SCCM Tier 2/3 Hierarchy Strategies (Secondary servers/Remote DPs/MPs)
- SCCM Servicing Strategy
- SCCM Client Management Strategy
- SCCM Application Management Strategy
- SCCM Software Update Strategy
- SCCM Backup and Restore Strategy
Resources
- SCCM Backup, Restore, and Availability Requirements
- SCCM/ConfigMgr 2012 and 2007 High-Level Architecture Design Guide
Useful links to help design decisions and implement SCCM ConfigMgr 2012 / Intune infrastructure !!
- SCCM Backup, Restore, and Availability Requirements more details.
- SCCM/ConfigMgr 2012 and 2007 High-Level Architecture Design Guide here
In the following portion of the post, I will share super cool design diagrams of the SCCM 2012 Infrastructure.
SCCM OSD Best Practices
SCCM Download Whitepaper on Top 10 Best Practices on Windows 10 OSD Configuration Manager ConfigMgr?
ConfigMgr/SCCM Operating System Deployment (OSD) is a huge topic! Because it is so complex, OSD has a lot to consider, especially in environments where security is extra important. Things to consider:
Restrict access to the ConfigMgr Console and Media. Make sure that only those users that should have access to the ConfigMgr Console and Media have access.
If someone were to have gained unauthorized access to your environment, they could maybe deploy Task Sequences to your computers and resulting in accident data loss, system outages, and discovery of sensitive information like account credentials and volume licensing keys used by ConfigMgr/SCCM for OSD tasks.

Top 10 Best Practices on Windows 10 OSD Configuration Manager ConfigMgr
Use built-in ConfigMgr Security Roles! Such as the Operating System Deployment Manager and, if necessary, custom security roles to ensure only those OSD users have access and can only deploy to certain collections.
The last thing we want is people who shouldn’t access OSD, causing problems on purpose or because they have features they don’t understand, and they end up deploying to a Collection like All Systems or others that are a big deal if targeted wrong.
Collection Variables
Be careful with the use of collection variables! Administrators could maybe read sensitive information they might be in there. SCCM Download Whitepaper on Top 10 Best Practices on Windows 10 OSD Configuration Manager ConfigMgr?
State Migration Points
There’s no way to limit the amount of data a machine stores on a state migration point (SMP). So is it possible for an attacker’s machine to take all disk space on the SMP, which would cause a denial of service…
Block the Client Certificate if compromised
If you discover the client certificate has been compromised (is required to deploy an OS), revoke it if it is a PKI certificate. Also, you block it in the ConfigMgr. Not blocking might let attackers be able to impersonate ConfigMgr Client and have the capability to download Policies that can contain sensitive information.
Don’t enable Command Support on your production Boot Images
Enabling Command Support, you can press F8 to start Command Prompt if a machine build fails, so you perform troubleshooting and look at the smsts.log. Obviously a security risk… attacker potentially has access to your network and access to variables in the Task Sequence environment could have sensitive data.
Protect the Client Authentication Certificate during its capture
If attackers could get the Client Authentication Certificate, they can impersonate a valid Client on your network. This happens because they would have access to the Private Key in the certificate.
Do not grant the Network Access Account (NAA) excessive rights
The NAA gives you access to this computer from the network right on any Distribution Points or other servers that hold package content the machine needs to access.
Do not re-use the account configured as the NAA | Try to avoid Network Access Account
Ideally, the NAA can only be used by Client computers when they cannot access the local computer account to access content on DPs.
Do not configure the same account used for the NAA for these:
- Capture Operating System Image Account.
- Task Sequence Editor Domain Joining Account.
- Task Sequence Run As Account
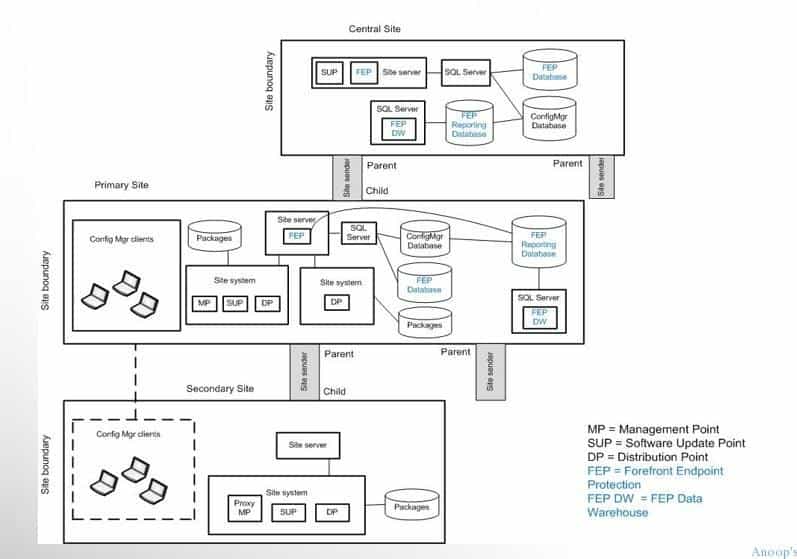
Sample architectural diagrams of Native SCCM with CAS server
SCCM Architecture Diagrams Decision Making Guide | ConfigMgr Configuration Manager Endpoint Manager.
Sample architectural diagrams of Native SCCM 2012 with a Single Primary server
Following is the sample Architectural design diagram, which is available in the IPD guide provided by Microsoft. This diagram is for SCCM 2007 not applicable to SCCM 2012.
SCCM Architecture Visio Template Download From GitHub 1 (anoopcnair.com)
Author
Anoop is Microsoft MVP! He is a Solution Architect in enterprise client management with more than 20 years of experience (calculation done in 2021) in IT. He is a blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. E writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc…


Great ! Nicely Elaborated 🙂
Thank you Raman 😉 !
Great stuff
Thanks !
Hi Anoop..
Great Document.
I am preparing for the interview and need a few basic questions and ans on SCCM Architecture level.
Can you pls share if have any
Thanks in advance
Excellent Document Anoop. Can you please share document for Troubleshooting Software Updates in Client Machines.
Hi Narayan ! – See http://blogs.technet.com/b/sudheesn/archive/2010/11/10/troubleshooting-sccm-part-iii-software-updates.aspx
Hello Anoop,
Nice article first of all. 🙂
Not sure my query is applicable in this post?
My scenario:
1 PRI–> 2 Secondaries(with DP on same server). DPs in other remote locations configured on Windows 7/Windows 8 PCs.
Questions:
a. What is recommended hardware configuration for the DPs on client OS?
b. What all services are required on those DPs? for all other activities except PXE(pretty obviously as there is no WDS).
c. Can we use PXE/Multicast on the secondary server which has DP on itself? Is there any caveat?
d. What is the suggested bandwidth between DP and primary site?
Any information is highly appreciated. Many thanks.
——- Ravi Sharma
Can i install the SUP role with MP role in SCCM 2012?
Yes
Hello Anoop.
I’m very new to sccm environment. And tasked to deploy sccm current branch and request you if you could advise any best practice to design high level architecture depicting high availability options including site resilency if any options.
thank you
I’m sorry, if you are very new to SCCM then, how can you design SCCM CB environment?
hello Anoop
I’m very new to sccm environment. And tasked to deploy sccm current branch.
I request if you could suggest me any best practice to design high level architecture depicting high availability options