Security patching is vital to every organization. Now with Intune, you can restrict Windows 10 devices that are not patched with the latest patches. Non-patched devices are risky to the organization. Use Intune to limit non-patched Windows devices from accessing mail.
There are two options to limit Windows devices from connecting to the corporate network. We will see these options in the following sections of the article.
Windows version = Specify the major.minor.build.CU number here. The version number must correspond to the version returned by the winvercommand.
Subscribe to the YouTube channel
I have uploaded a video tutorial to my YouTube channel. I hope this video will help you to set these restrictions upon your Intune test tenant.
I would recommend testing these in a staging environment before implementing them in production. As you are aware, patching is essential in any modern workplace project implementation.
Intune and Windows Update for Business can ensure all the Windows devices managed through Intune are patched promptly.
There is no need for on-prem components like WSUS to patch Windows 10 devices using Intune and Windows update for Business. There won’t be any security concerns when you set the Windows 10 Update rings in Intune.
Read my previous post, “How to Setup Windows 10 Software Update Policy Rings in Intune Azure Portal,” to learn more about Windows 10 update rings.
How to Restrict Non patched Windows Devices from Enrolling into Intune?
This option is available only for NEW Windows devices that are getting enrolled in Intune environment via the MDM channel. This option is not available for Intune PC agent-managed devices.
The setting explained in this section won’t apply to already enrolled and non patched Windows devices.
If you have already enrolled and non patched Windows devices, then, you need to check out the compliance policy option mentioned in the below part of the post.
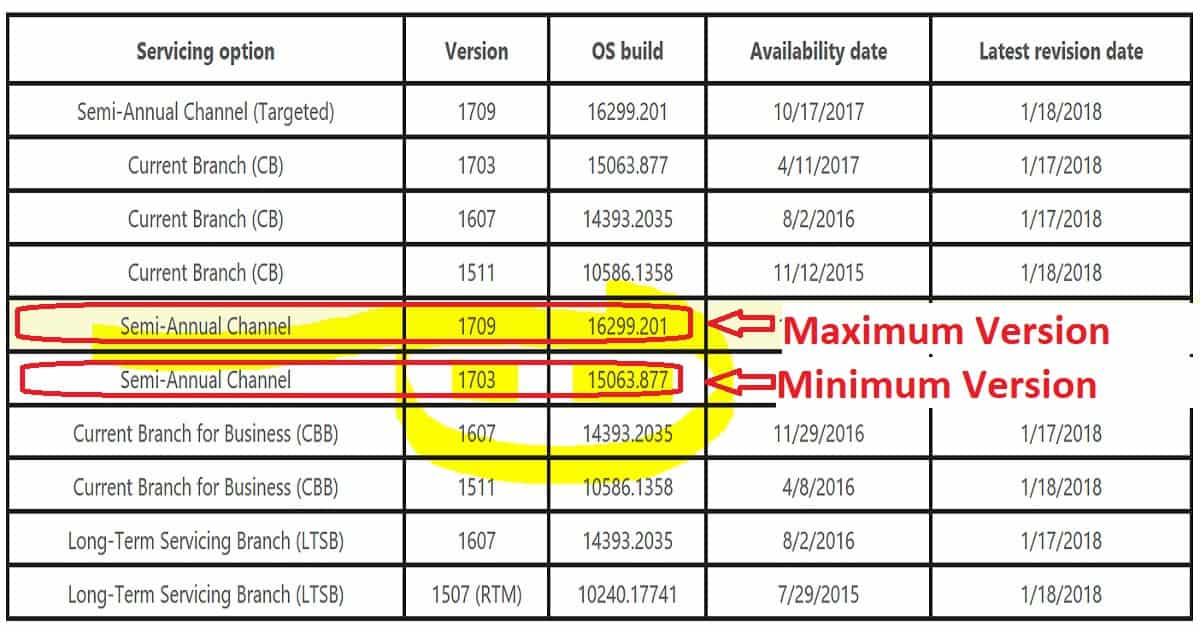
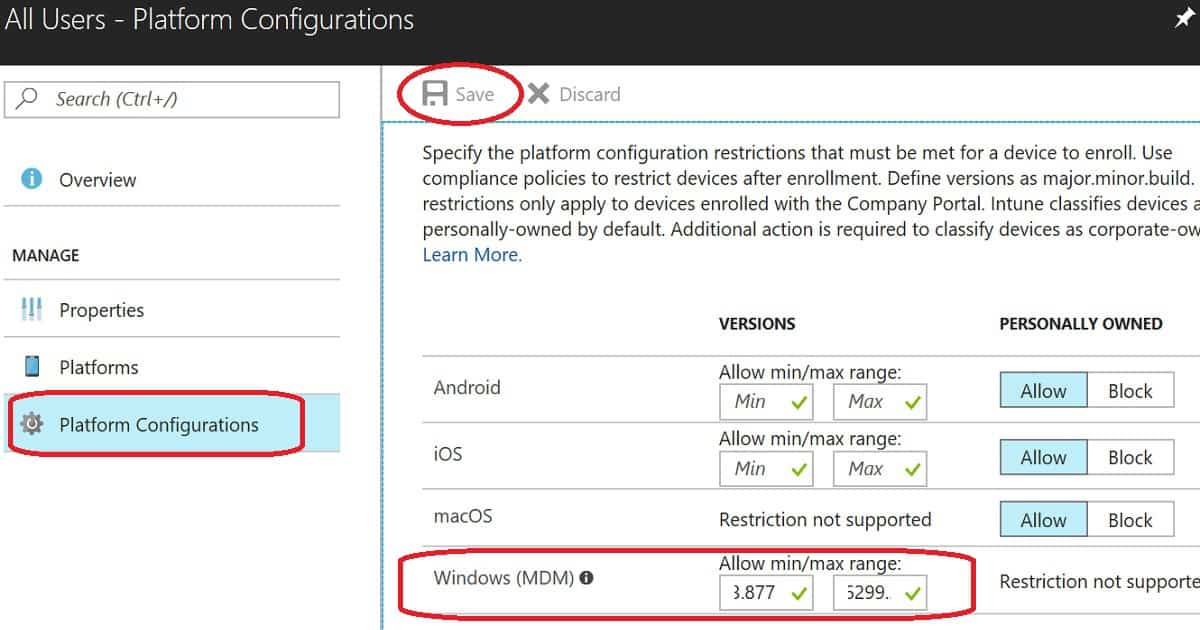
We need to set up Intune enrollment restriction policies to restrict Windows devices from enrolling in Intune. The above table is the best reference to set up Intune enrollment restriction policies for non patched Windows devices.
First, we need to decide about your Windows 10 minimum and maximum patch level requirement. You can have more patch-level version details from http://aka.ms/win10releasenotes.
In my video, I have selected Windows 10 minimum patch level 10.0.15063.877 & maximum patch level 10.0.16299.201. You can also leave the top patch level as blank if you want to support all the latest patched Windows devices.
I have uploaded a video tutorial to my youtube channel. And this video has a more detailed explanation of how to set up enrollment restriction policies.
You can read my previous post, “How to Prevent Windows Devices from Enrolling to Intune“. This post provides more details about settings up Intune enrollment policies. And this also covers the end-user experience of Windows 10 devices if the device patch level is lesser than “Minimum version”.
For example
I have a Windows 10 device, and it’s non patched device. And the patch version of that device is “10.0.15063.250”. In this scenario, Intune will check whether the device is patched with a minimum version of the patch required for the organization, and that version is 10.0.15063.877.
The current patch level of the Windows 10 device is below the minimum version requirement set in the enrollment restriction policy. Hence the device won’t be allowed to enroll in Intune. Update the patches on that Windows 10 device to get successfully registered to Intune.
How to Force Users to Install Patches on Windows 10 Devices to Get Access back to eMails?
Most end-users are not always happy to install the latest patches and restart the devices on time. But as an IT admin, it’s our responsibility to make the enterprise environment secure with the latest patches.
Intune can probably help you force users to install patches on their non patched Windows devices.
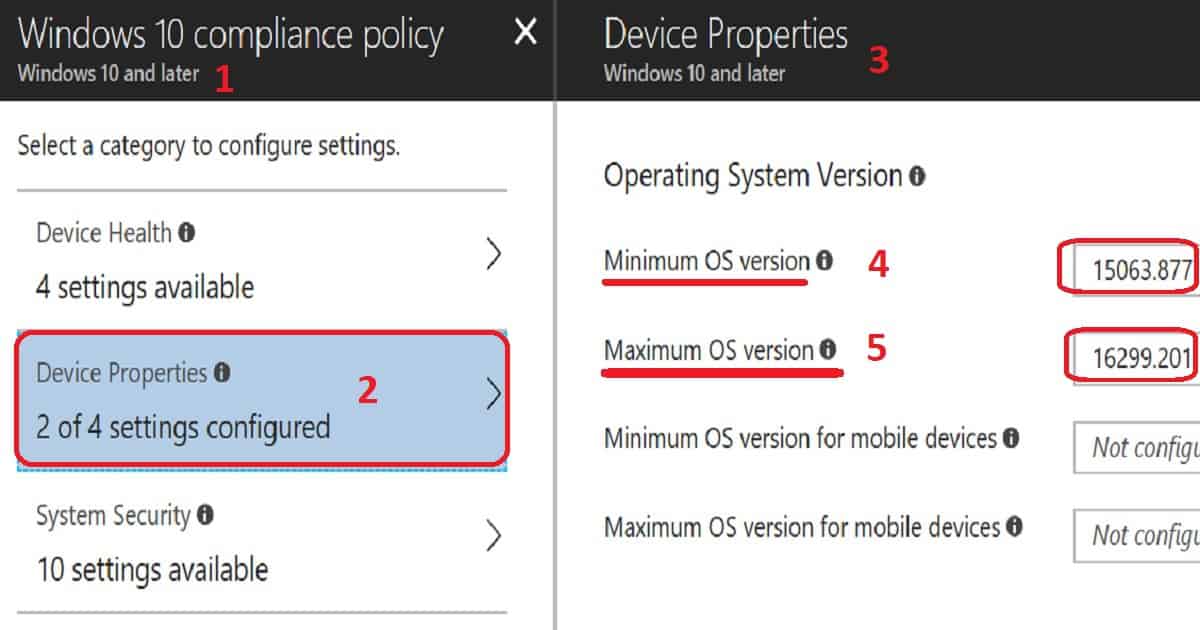
We can create a new compliance policy in Intune to set rules and force users to install patches immediately. Intune compliance policy gives an option to set minimum & maximum patch levels for Windows devices.
When a device does not match the minimum compliance requirement, that device will be flagged as a non compliant device.
When you have conditional access associated with compliance policies, the Windows device will lose access to enterprise applications (like mail, SharePoint online, Skype, etc.) associated with that conditional access policy.
Once users update their Windows version with the latest patches, their devices get the access back to mail.
You can create a WINVER command to decide the baseline Windows 10 version with a certain patch level for your organization. Or you can use the following links to get the latest patch versions of Windows 10.
In my scenario, I set up a new compliance policy with a minimum patch level is 10.0.15063.877 and a maximum patch level is 10.0.16299.201.
This will ensure that all Windows 10 devices which have access to enterprise applications are patched, and the patch level version will be greater than 10.0.15063.877.
I have uploaded a video tutorial to my YouTube channel. And this video has a more detailed explanation of how to create a new compliance policy for minimum and maximum patch levels supported within your organization.
In my previous post, I explained the best practices for building compliance policies for Windows devices. Get more details from “How to Setup Intune Compliance Policy for Windows 10 Devices“.
Navigate via Azure portal “Microsoft Azure – Microsoft Intune – Device compliance – Policies” and create a new compliance policy called “Restrict Window device depending on patches“.
Resources
- Intune Windows 10 Compliance Device property settings
- Windows 10 Compliance Policy – OS Version granularity
Author
Anoop is Microsoft MVP! He is a Solution Architect in enterprise client management with more than 20 years of experience (calculation done in 2021) in IT. He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc……………