Hey, let’s discuss about Reducing Credential Theft Risk by Limiting Local Account Access using Intune Policy. This policy controls how local accounts are used for remote access. It decides what permissions the account gets when someone connects through the network. It is important because remote access can be risky. Hackers often try to use weak or repeated local passwords. So this policy helps protect the system.
This policy is important because many organisations use the same local account password on many computers. If one password is stolen, all computers become unsafe. This policy reduces that danger. It protects sensitive data in the organisation. It keeps the whole network more secure.
When the policy is Enabled, Windows removes admin power from local accounts during network logon. Even if the account is an administrator, it becomes limited. This helps stop attackers from doing harmful actions. It reduces the risk of system damage. It makes the organisation safer.
When the policy is Disabled, local accounts keep full admin rights during network logon. This is very risky because attackers can control the system if they get the password. It can spread attacks to other computers. It increases the chance of data loss. So organisations should enable this policy for better protection.
Table of Contents
What are Advantages of Enabling this Policy using Intune?
Enabling this policy gives better security for the organisation. It limits the power of local accounts when they log in through the network. This helps stop attackers from using stolen passwords to control systems. It also reduces the risk of malware spreading. Overall, it keeps the network much safer.
1. Gives stronger security for remote logons.
2. Stops attackers from using local admin accounts.
3. Protects systems when the same password is used on many devices.
4. Reduces the chance of malware spreading through the network.
5. Keeps important data safe by limiting access.
6. Prevents misuse of admin rights during remote access.
7. Follows security best practices for Windows environments.
Stop Admin Share Attacks Lock Down Local Accounts using Intune
Apply UAC restrictions to local accounts on network logons means local accounts get limited permissions when they connect through the network. This helps block misuse by removing admin rights during remote access. This post will explain how we can easily configured this on Windows devices using Microsoft Intune.
- Block Network Printing Restrictions using Intune Settings Device Control Printing Restrictions
- Enable Disable Device Control Printing Restrictions Policy using Intune
- How to Prevent Malware Spread and Remote Attacks by Blocking PsExec and WMI with Intune ASR Rule
Create a Profile
Using simple steps, you can easily complete the policy creation. Open the Intune admin center. Go to Devices > Configuration > Policies> + Create > + New policy. After that, you will get a profile window to select the platform and profile type. Select Windows 10 and later as the platform, and select settings catalog as the profile type. Click on the create button.
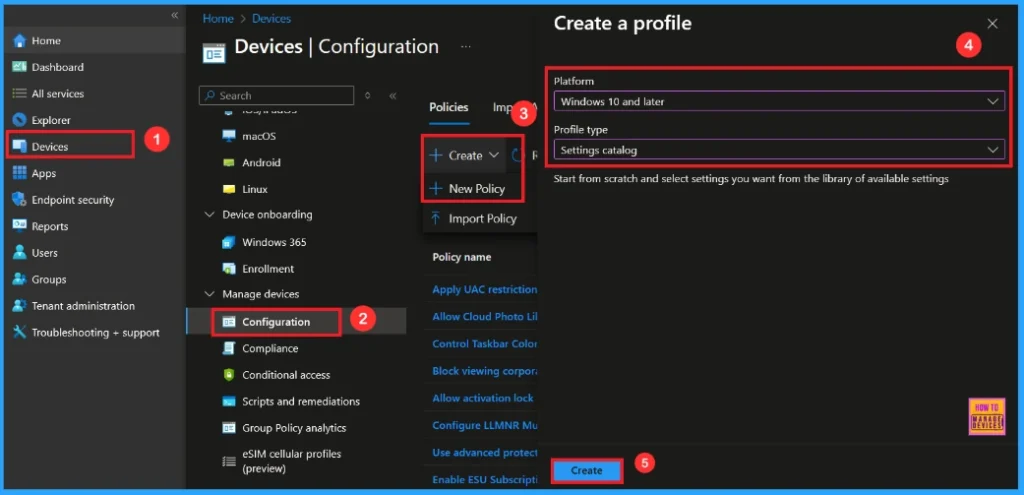
Basic Step
On this tab, you have to give a name(Apply UAC restrictions to local accounts on network logons) for the policy that you want to create. The name field is mandatory. Without giving a name, you can’t create a policy on the basic tab. You can also describe the policy, which description is not mandatory. Click on the next button.
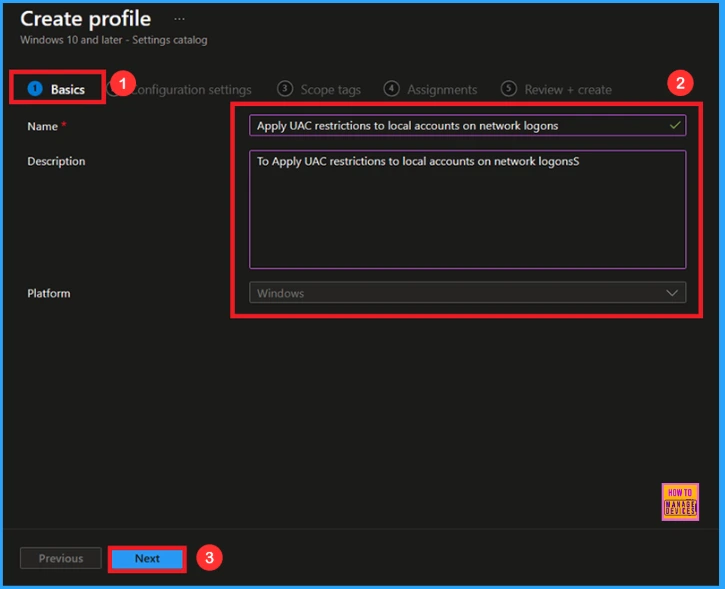
Configuration Settings
The configuration tab allows you to select specific policy settings to manage your organisation’s devices. On this page, we click on the + Add Settings. Then you will get a settings picker that will show different types of categories to select specific settings. Here, I choose to Administrative Templates\MS Security Guide the category and select the Apply UAC restrictions to local accounts on network logons.

Once you have selected Apply UAC restrictions to local accounts on network logons policy, and closed the Settings picker. You will see it on the Configuration page. Here we have only two settings: Enable or Disable. By default, this policy will be set to Disable.
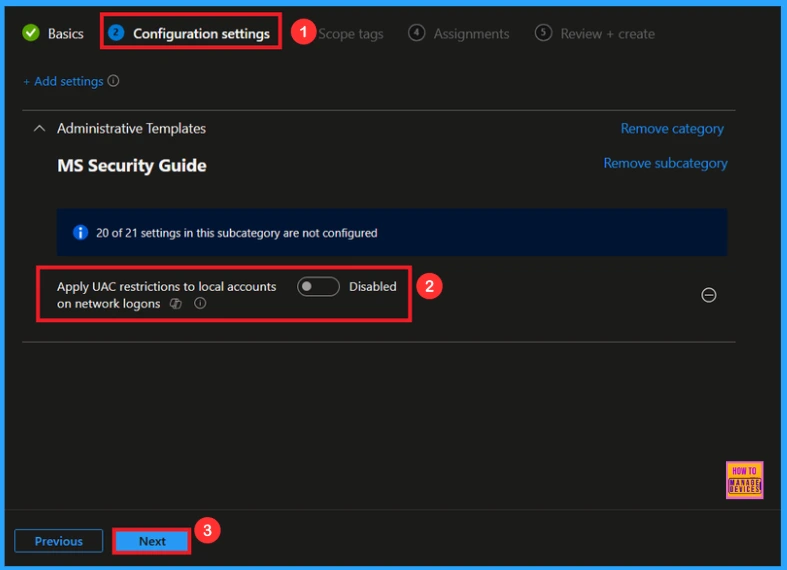
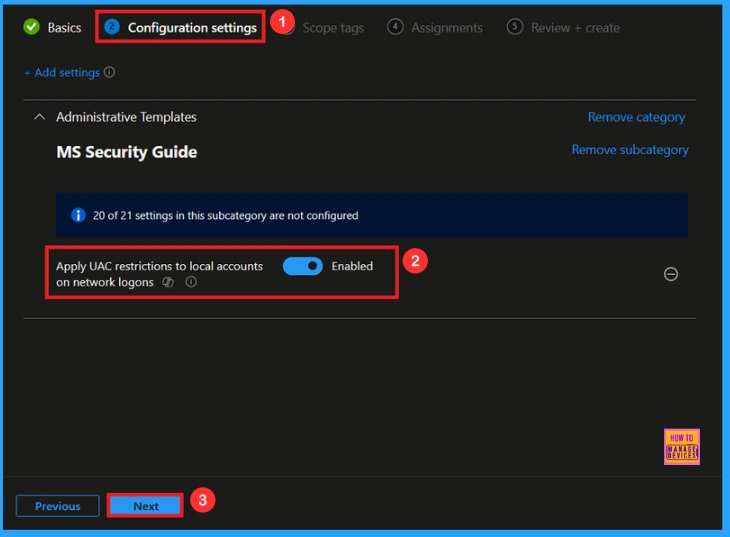
Enable UAC Restrictions Policy
If we Enable or configure this policy, you can enable the Apply UAC restrictions to local accounts on network logons Policy by toggling the switch. Then, click the Next button to proceed.
Scope Tag
In Intune, Scope Tags are used to control who can view and modify a policy. The scope tag is not mandatory, so you can skip this section. It functions as a tool for organisation and access management, but assigning it is optional. Click Next if they’re not required for your setup.

Assignment
In the Assignments tab, you choose the users or devices that will receive the policy by clicking Add Group under Include Group, select the group that you want to target (e.g Test_HTMD_Policy) and then click Next to continue.
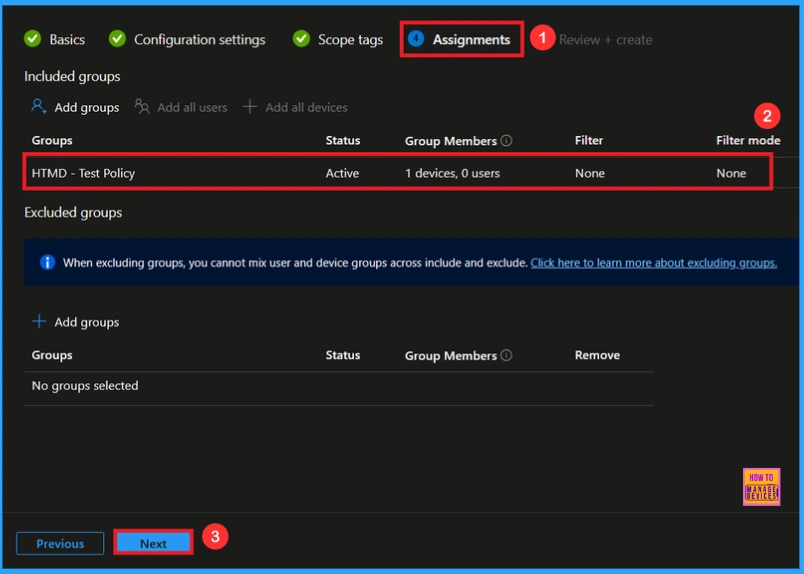
Final Step
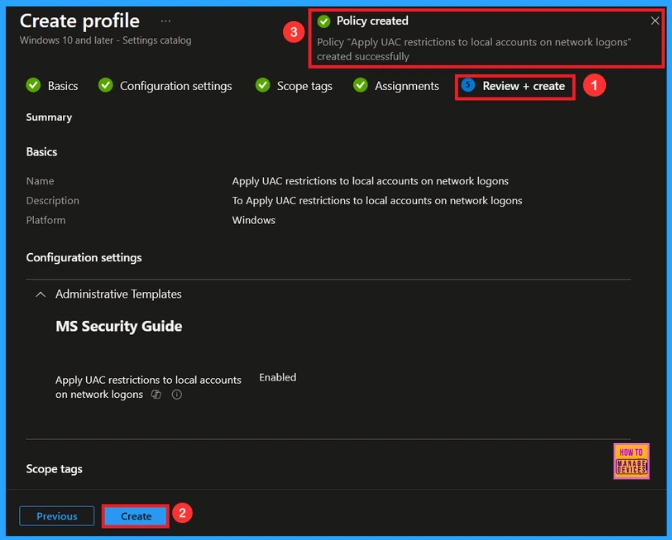
At the final Review + Create step, we see a summary of all configured settings for the new profile; after reviewing the details and making any necessary changes by clicking Previous. We click Create to finish, and a notification confirms that the “Apply UAC restrictions to local accounts on network logons created successfully”.
Monitoring Status
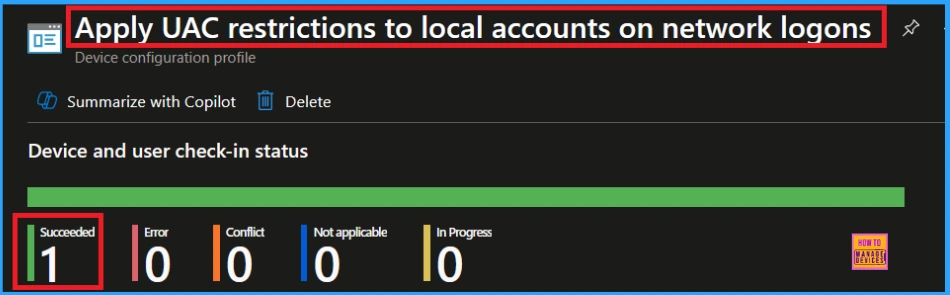
To view a policy’s status, go to Devices > Configuration in the Intune portal, select the policy(Apply UAC restrictions to local accounts on network logons) and check that the status shows Succeeded(1). Use manual sync in the Company Portal to speed up the process.
How to Remove Assigned Group from UAC Restrictions Policy
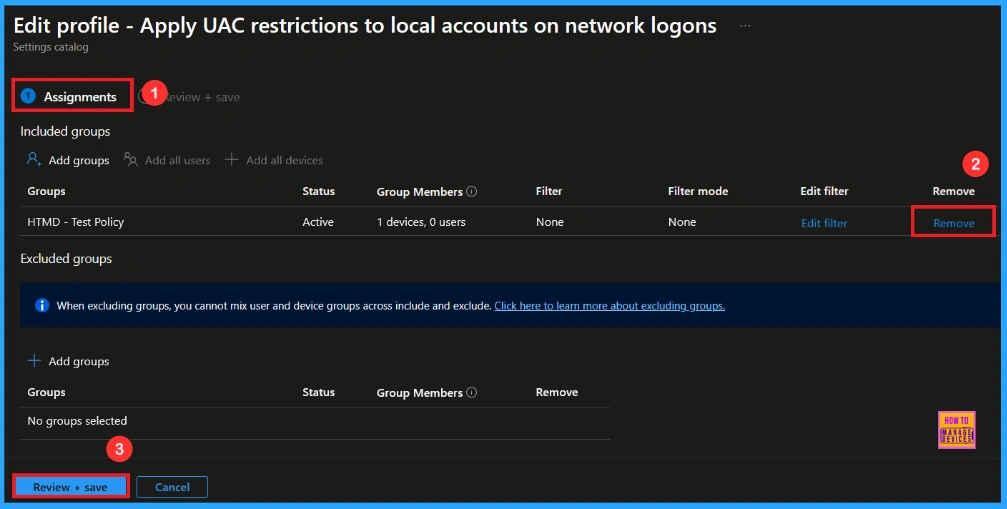
Sometimes, we need to remove a group from a policy assignment for security updates. Open the policy from the Configuration tab and click on the Edit button on the Assignment tab. Click on the Remove button on this section to remove the policy. Click Review + Save after making the change.
For detailed information, you can refer to our previous post – Learn How to Delete or Remove App Assignment from Intune using by Step-by-Step Guide.
How to Delete UAC Restrictions Policy from Intune
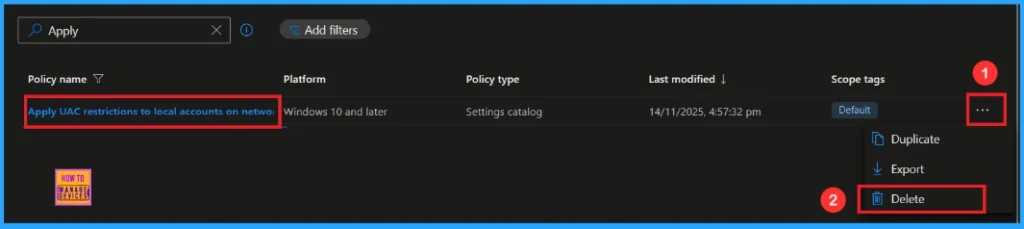
To delete an Intune policy for security or operational reasons. It is simple to do. I will demonstrate how to delete an Intune policy through the Apply UAC restrictions to local accounts on network logons Policy. Click the three dots, then click the Delete option.
For detailed information, you can refer to our previous post – How to Delete Allow Clipboard History Policy in Intune Step by Step Guide.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


