Key Takeaways:
- Prevents users from saving dial-up connection passwords locally
- Helps to Enforce restrictions across managed Windows devices
- Users must re-enter credentials each time they connect
- strengthens security but may slightly reduce convenience
Let’s discuss Prevent Dial-up Password from being Saved using Intune. The policy specifically targets the LSA (Local Security Authority) and dictates whether the Windows “Save Password” checkbox is available for dial-up and certain VPN connections.
Table of Contents
Table of Contents
Prevent Dial-up Password from being Saved using Intune
Dial-up Password from being Saved critical for hardening the Windows operating system against credential theft. The core purpose of this policy is to eliminate the local caching of network credentials used for Dial-up and Virtual Private Network (VPN) connections.
Without this policy, if a user selects “Save Password,” the credentials are encrypted and stored on the hard drive. If the device is lost or stolen, an unauthorized individual could potentially boot the laptop, click “Connect” on a saved VPN profile, and gain a direct tunnel into your corporate network without ever knowing the password.
- Enable MPR Notifications for System to Easily Sync Passwords using Intune
- Require Password when Computer Wakes on Battery using Intune
- How to Remove Assigned Group from Energy Saver Battery Threshold Policy in Intune Settings Catalog
Example Scenario
Imagine a sales rep working from a public Wi-Fi network at an airport. They use a Windows VPN (which uses the dial-up logic) to access the corporate CRM. Enabling this policy prevents the “Connect” button from working without a manual password entry, effectively stopping the thief at the perimeter.
How to Start Policy Creation
As an Admin, you can quickly configure this policy on your organisation. To start the Policy Creation, open the Microsoft Intune Admin center. Then go to Devices > Configuration >+ Create > +New Policy.
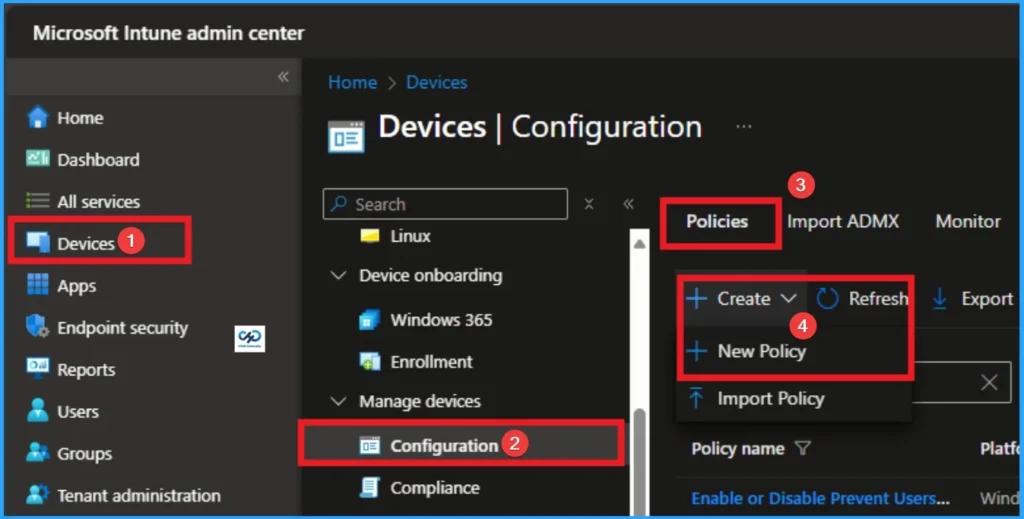
Profile Creation
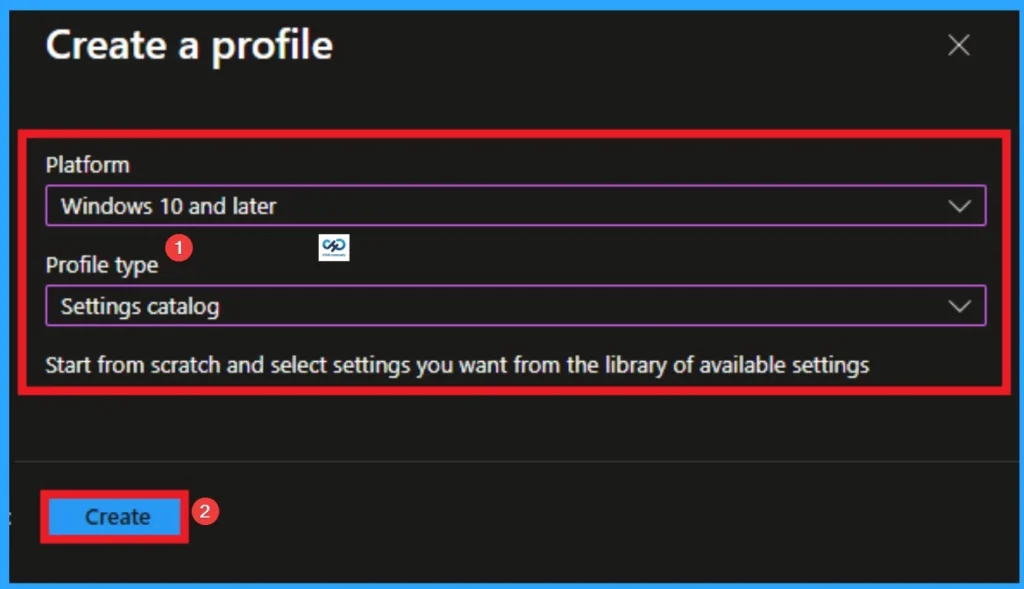
Profile creation is the necessary step that helps you to assign the policy to appropriate platform and Profile. Here I would like to configure the policy to Windows 10 and later platform and settings catalog profile. Then click on the Create button.
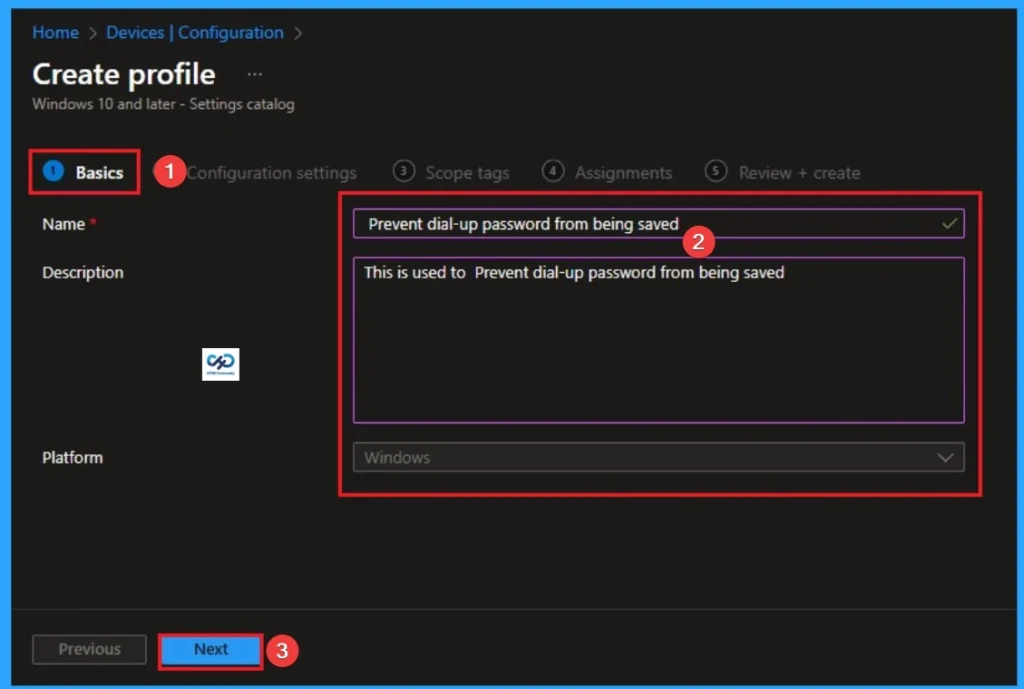
Filling the Basic Tab
Naming the policy is the primary step that help admins to identify the policy later. This is important and necessary step that allows you to know the purpose of the policy. Here is Name is mandatory and description is optional. After adding this click on the Next button.
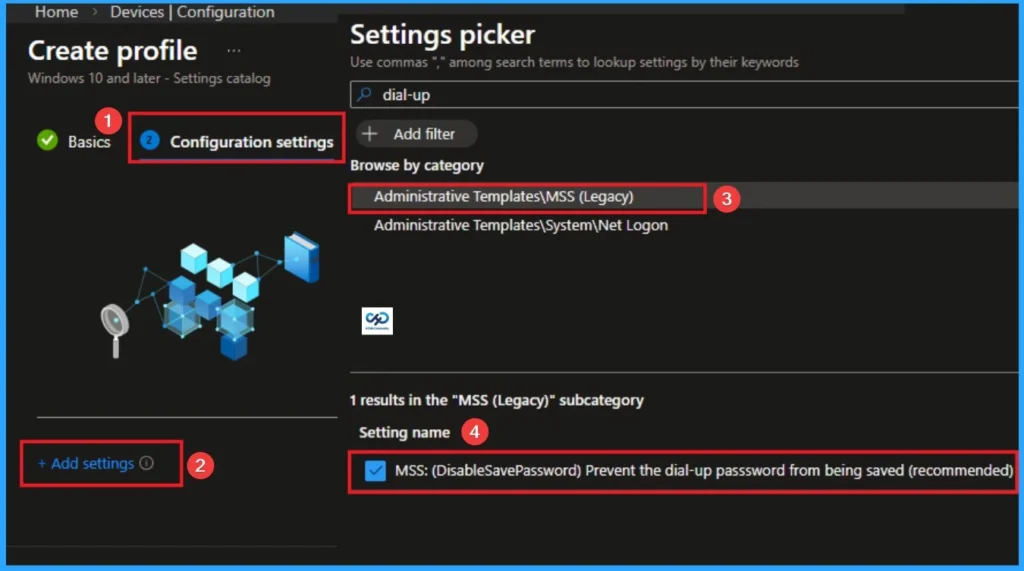
Configure Dial-up Password
With Settings Picker, you can use the Configuration Settings Tab. On this tab, you can click on the +Add Settings hyperlink to get the Settings Picker. The settings picker shows huge number of settings. Here, I would like to select the settings by browsing by Category. I choose System. Then, I choose Administrative Templates > MSS (Legacy) > MSS: (DisableSavePassword) Prevent the dial-up passsword from being saved (recommended) settings.
Disable Dial-up Password
When this policy is Disabled, Windows do not removes the ability for a user to check the “Save Password” box in the connection dialog. This is the default value of this policy.
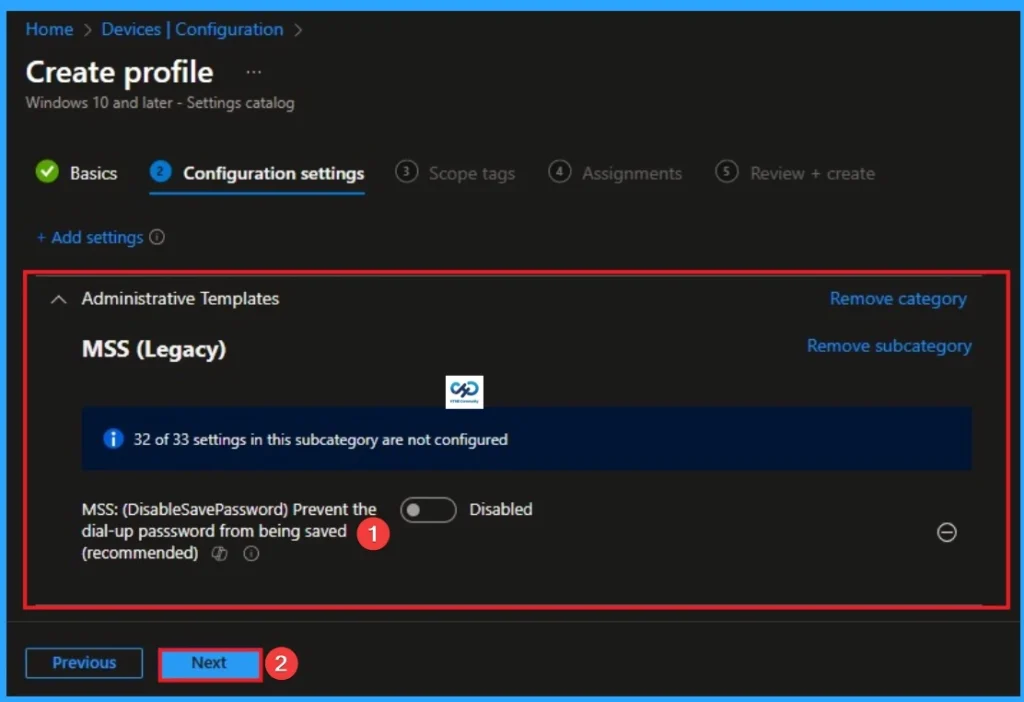
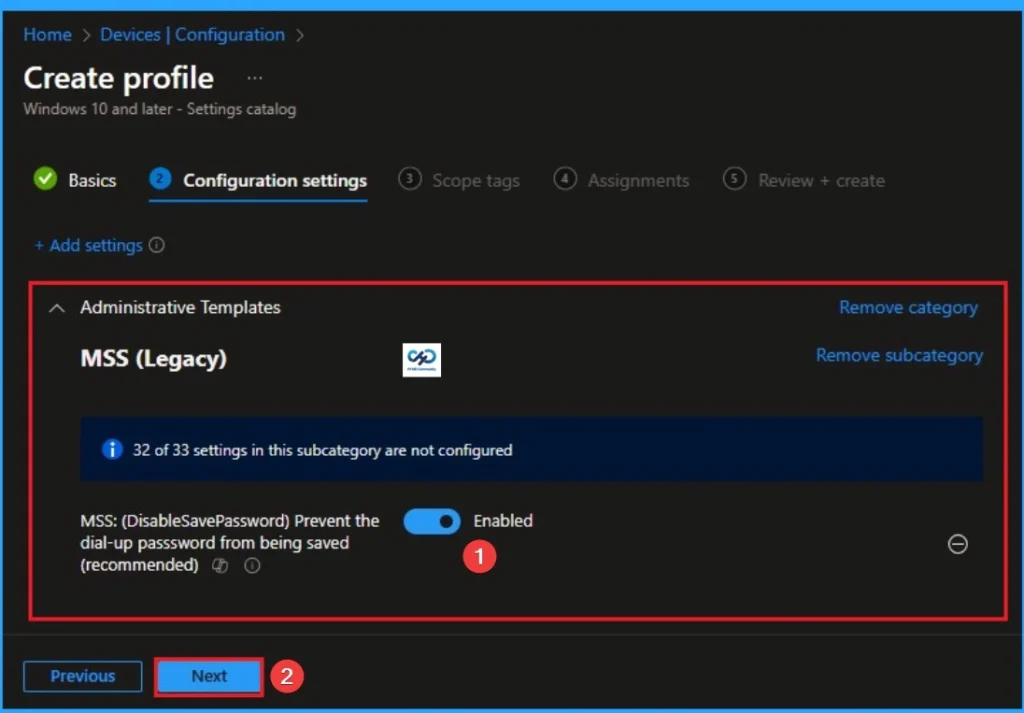
Enable Dial-up Password
When this policy is Enabled, Windows removes the ability for a user to check the “Save Password” box in the connection dialog. This forces the user to manually enter their credentials every single time they initiate a connection.
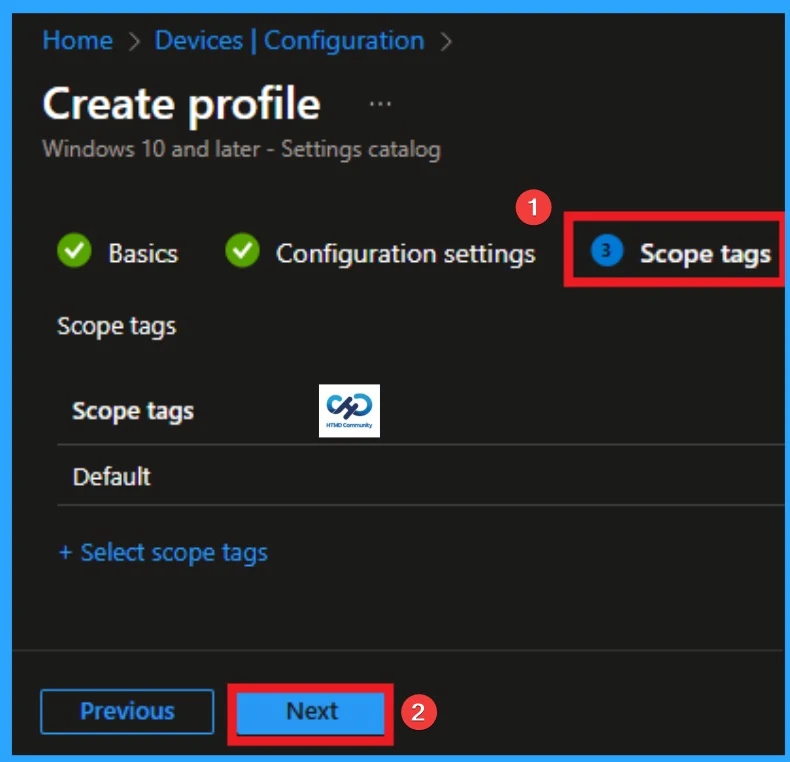
Scope Tags
With scope tags, you create a restriction to the visibility of the Dial-up Password. It helps to organise resources as well. Here, I would like to skip this section, because it is not mandatory. Click on the Next button.
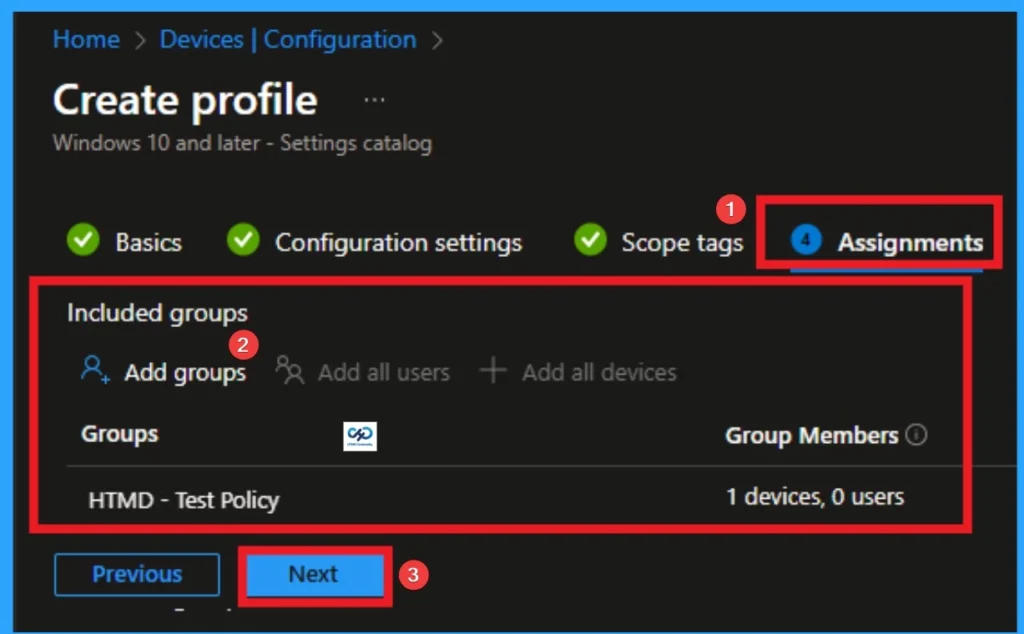
Assignments Tab for Selecting Group
To assign the policy to specific groups, you can use the Assignment Tab. Here I click, +Add groups option under Included groups. I choose a group from the list of groups and click on the Select button. Again, I click on the Select button to continue.
Review + Create Tab
Before completing the policy creation, you can review each tab to avoid misconfiguration or policy failure. After verifying all the details, click on the Create Button. After creating the policy, you will get a success message.
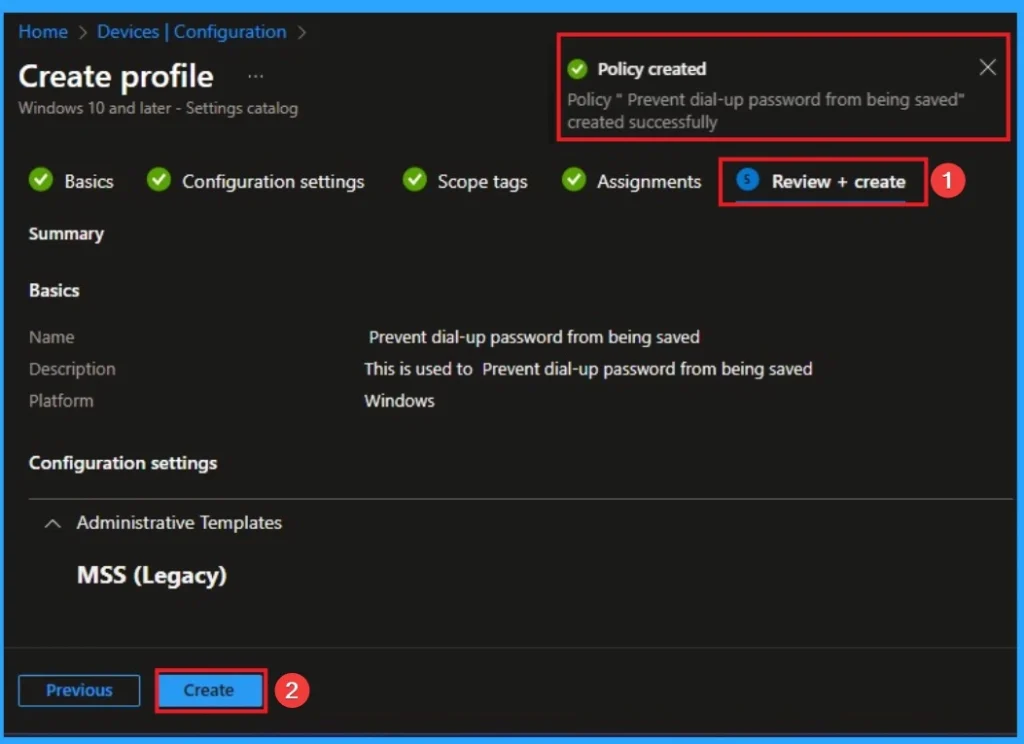
Monitoring Status
The Monitoring Status page shows whether the policy has succeeded or not. To quickly configure the policy and take advantage of the policy sync the assigned device on Company Portal. Open the Intune Portal. Go to Devices > Configuration > Search for the Policy. Here, the policy shows as successful.
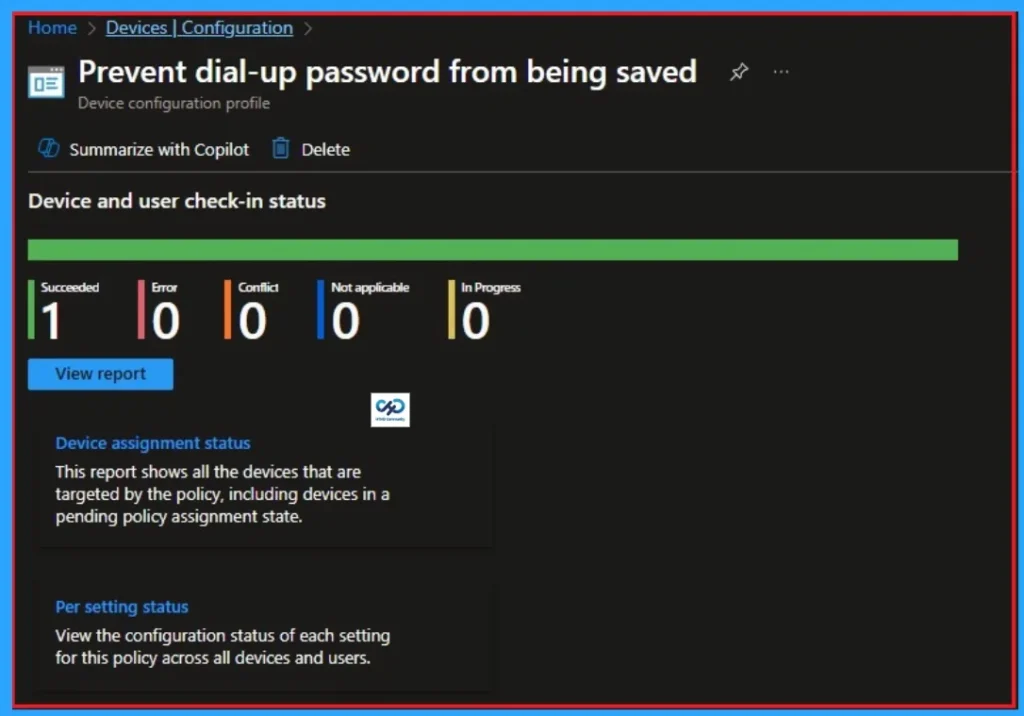
Event Viewer Details
Event Viewer helps you check the client side and verify the policy status. Open the Client device and open the Event Viewer. Go to Start > Event Viewer. Navigate to Logs: In the left pane, go to Application and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin.
| Event Viewer Details |
|---|
| MDM PolicyManager: Set policy string, Policy: (Pol_MSS_DisableSavePassword), Area: (ADMX_MSS-legacy), EnrollmentID requesting merge: (EB427D85-802F-46D9-A3E2- D5B414587F63), Current User: (Device), String: (), Enrollment Type: (0x6), Scope: (0x0). |
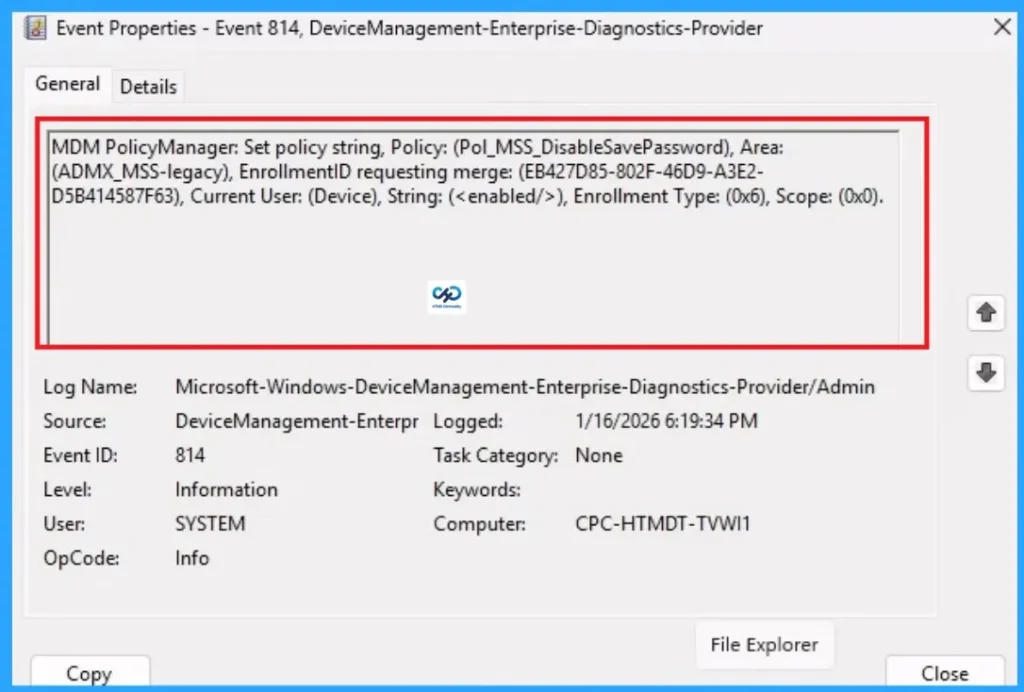
Removing the Assigned Group from Dial-up Password Settings
If you want to remove the Assigned group from the policy, it is possible from the Intune Portal. To do this, open the Policy on Intune Portal and edit the Assignments tab and the Remove Policy.
To get more detailed information, you can refer to our previous post – Learn How to Delete or Remove App Assignment from Intune using by Step-by-Step Guide.
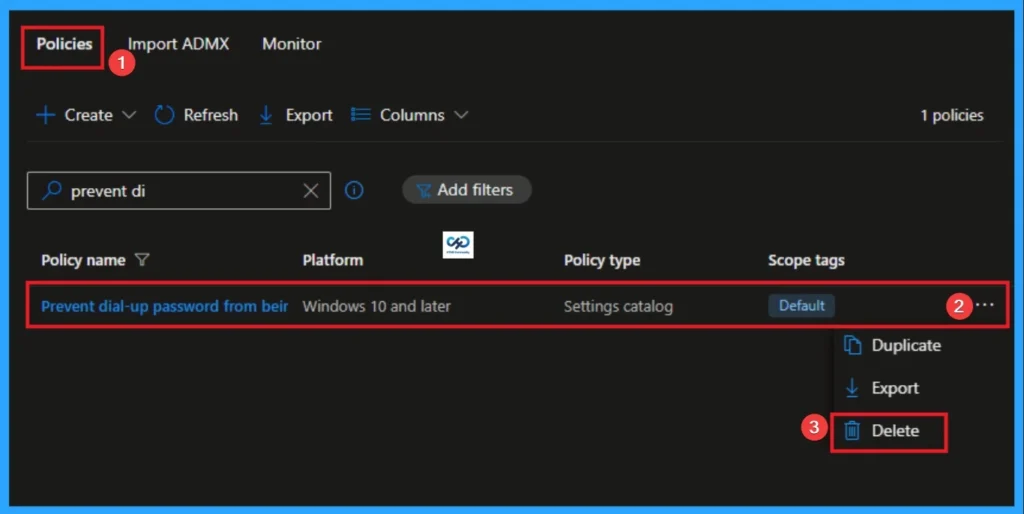
How to Delete Dial-up Password
You can easily delete the Policy from the Intune Portal. From the Configuration section, you can delete the policy. It will completely remove it from the client devices.
For detailed information, you can refer to our previous post – How to Delete Allow Clipboard History Policy in Intune Step by Step Guide.
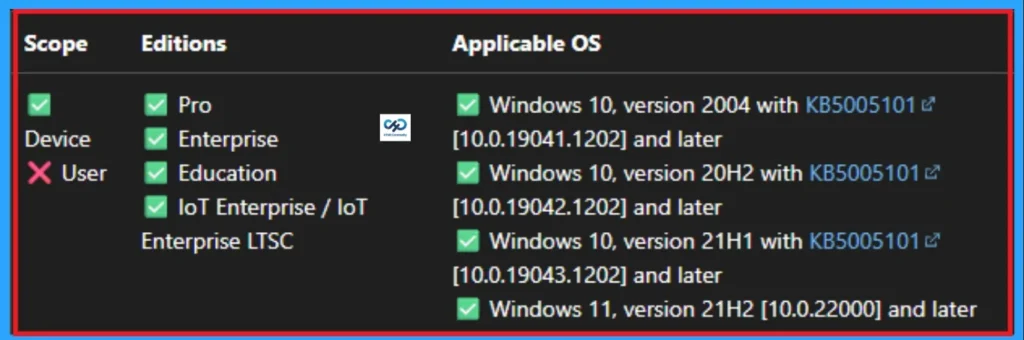
Windows CSP Details
This policy is applicable for Windows 10, version 2004 with KB5005101 [10.0.19041.1202] and later, Windows 10, version 20H2 with KB5005101 [10.0.19042.1202] and later, Windows 10, version 21H1 with KB5005101 [10.0.19043.1202] and later, Windows 11, version 21H2 [10.0.22000] and later.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


