Hey, let’s discuss about Stop Hidden Threats Your Step by Step Guide to Activating Network File Scanning using Intune. This policy helps control whether antivirus scans include files that are accessed over a network. When this policy is enabled, both scheduled and manually started scans check files shared through a network connection, ensuring no infected files spread between computers.
The importance of this policy lies in its role in protecting networked environments. Many organizations use shared drives or remote file storage, and infected files in these locations can harm multiple computers at once. Enabling this policy ensures that even these remote files are scanned, reducing the chances of a virus spreading across the network.
This policy helps both users and organizations maintain security and productivity. Users benefit from safer file access without worrying about hidden threats, while IT departments gain better control over the health of all connected systems. For organizations, this helps reduce data breaches, downtime, and repair costs caused by malware infections.
An example of this policy in action is within a company where employees share files using a central server. If someone uploads an infected document, the antivirus will scan it before others can access it. This prevents the malware from spreading to other employees’ devices, keeping the entire network secure and the workflow uninterrupted.
Table of Contents
What are the Advantages of Enabling this Policy using Intune?
Enabling this policy increases overall network security by ensuring that all files accessed over the network are scanned for threats. It helps protect users and organizations from spreading malware through shared drives or remote connections.
1. Ensures network files are scanned for viruses and malware
2. Prevents the spread of infections across multiple computers
3. Protects shared drives and servers from threats
4. Enhances overall system and data security
5. Reduces downtime and repair costs caused by infections
Stop Hidden Threats Your Step by Step Guide to Activating Network File Scanning using Intune
The Allow Scanning Network File policy can be easily configured on Windows devices using either Microsoft Intune or by setting a custom OMA-URI (Open Mobile Alliance Uniform Resource Identifier).
- Block Untrusted and Unsigned Processes that Run from USB using Attack Surface Reduction Rules in Intune
- How to Allow or Block Email Scanning using Intune Policy
- Monitoring Defender Updates using Intune Portal
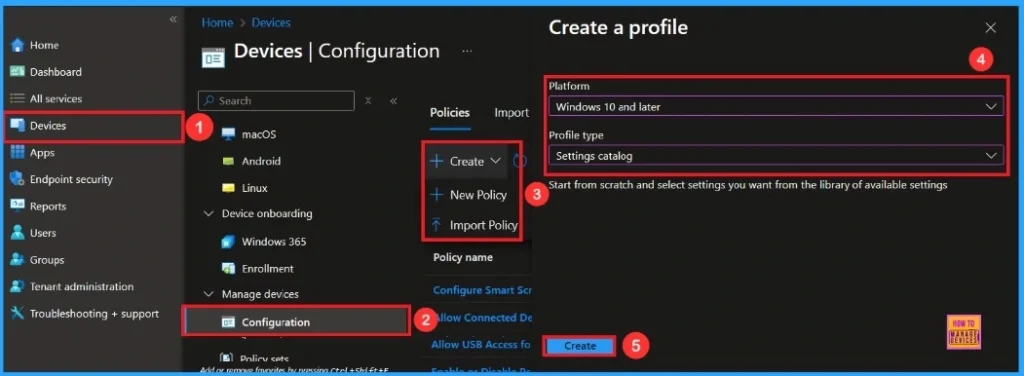
Create a Profile
To start deploying a policy in Intune, sign in to the Microsoft Intune Admin Center. Then, go to Devices > Configuration profiles > Create New Policy. Select Platform as Windows 10 and later, and profile is Settings catalog.
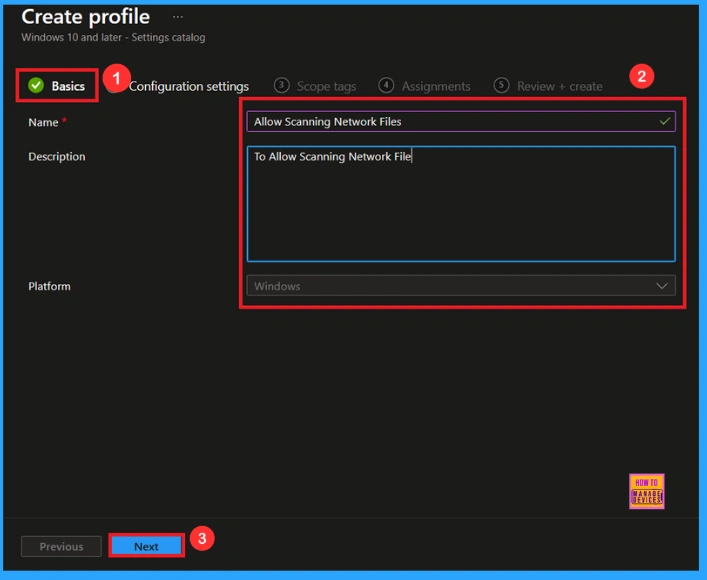
First Step
To begin configuring a policy in Intune, start with the Basics step. Here, we can add the name of the policy and give a brief description.
- Name of the Policy: Allow Scanning Network Files
- Description: To Allow Scanning Network Files
- Platform: Windows
Configuration Settings
In the Configuration settings tab, click the Add settings button to open the Settings picker. Search the settings for Defender, then select the Allow Scanning Network Files Policy.
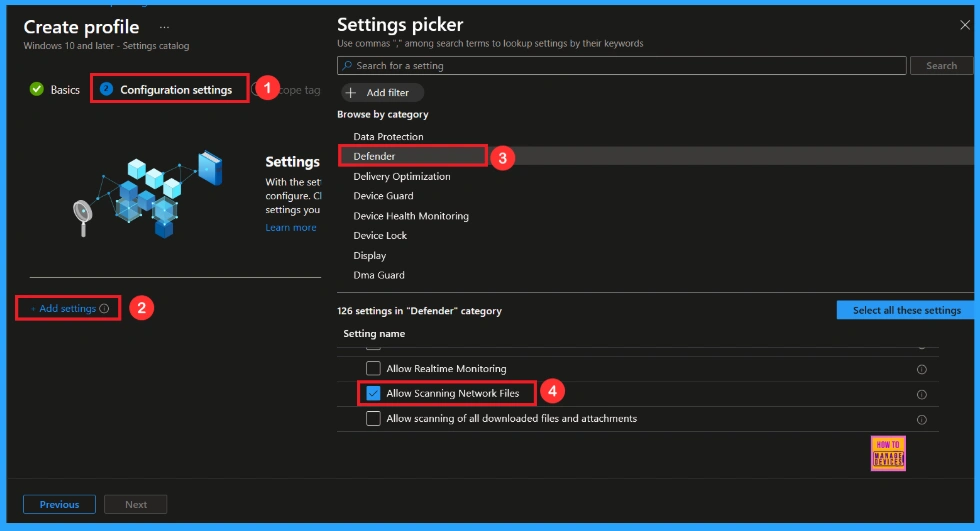
Once you have selected Allow Scanning Network Files and closed the Settings picker. You will see it on the Configuration page. Here we have only two settings: Allow or Block. By default, Scanning Network Files will be set to Allowed. If you want to allow these settings, click on the Next button.
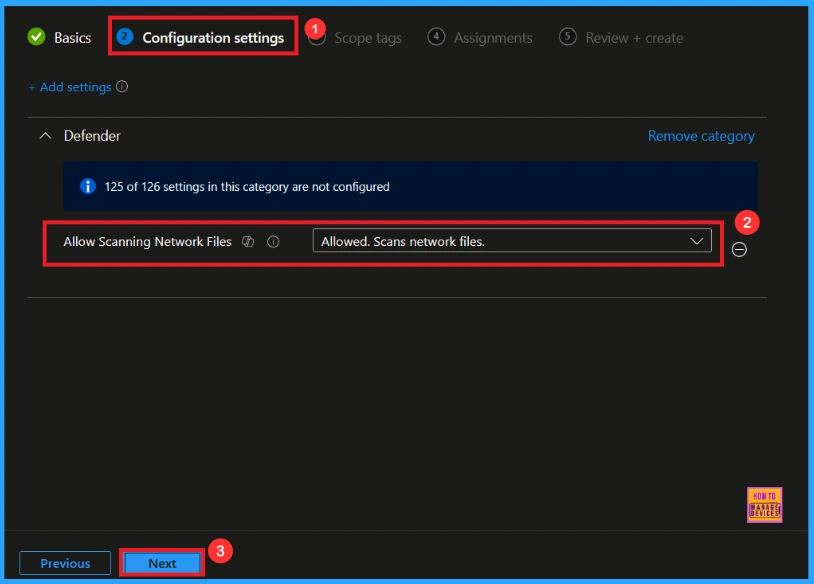
Block Scanning Network Files
If we Not allowed or don’t configure this policy, you can block the Scanning Network Files policy by clicking the dropdown menu and select Not allowed, Turns off scanning of network files. After reviewing or adding more settings, you can click the Next button to proceed.
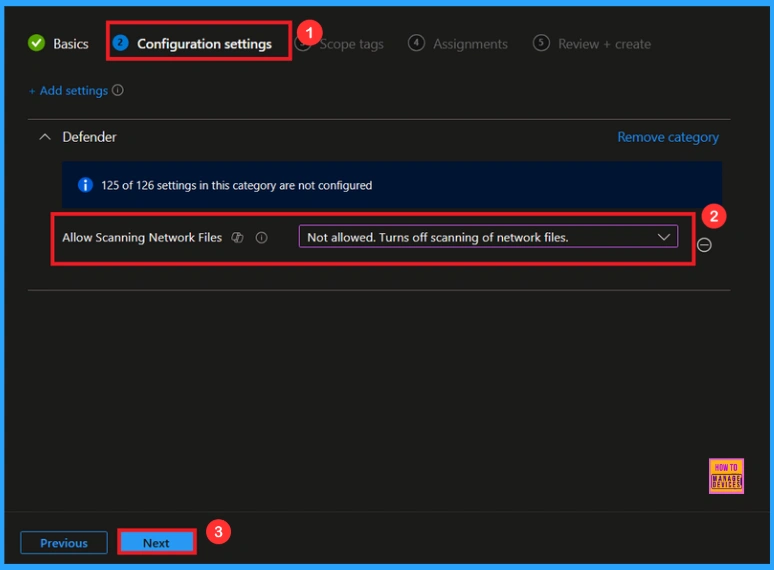
Scope Tags
In Intune, Scope Tags are used to control who can view and modify a policy. The scope tag is not mandatory, so you can skip this section. It functions as a tool for organisation and access management, but assigning it is optional. Click Next if they’re not required for your setup.
Assignments
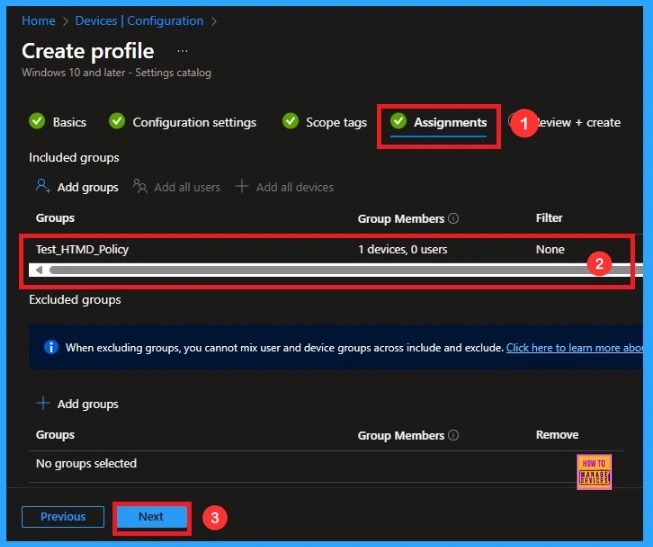
In the Assignments tab, you choose the users or devices that will receive the policy by clicking Add Group under Include Group, select the group that you want to target (e.g Test_HTMD_Policy) and then click Next to continue.
Last Step
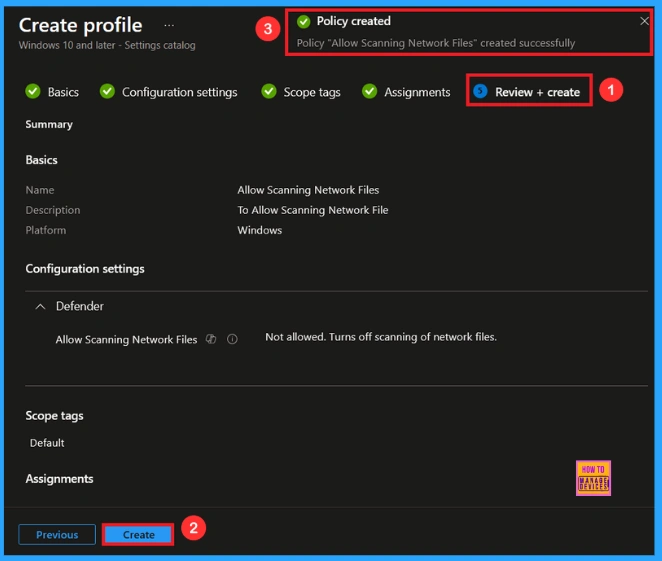
At the final Review + Create step, we see a summary of all configured settings for the new profile; after reviewing the details and making any necessary changes by clicking Previous. We click Create to finish, and a notification confirms that the “Allow Scanning Network Files created successfully”.
Monitoring Status
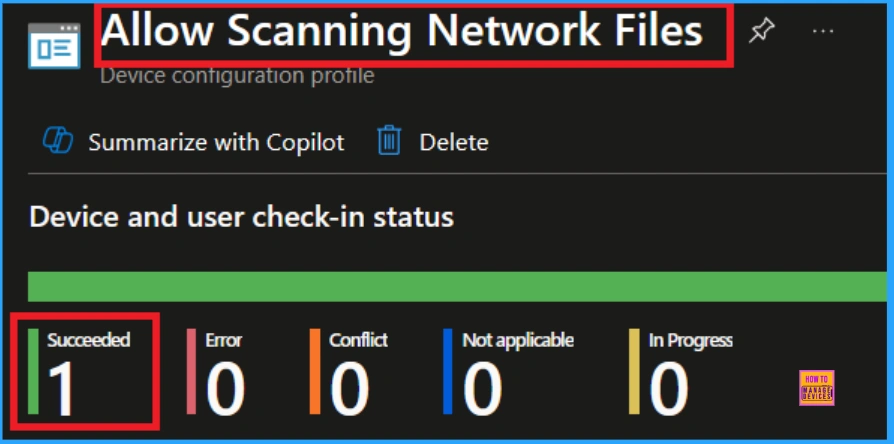
To view a policy’s status, go to Devices > Configuration in the Intune portal, select the policy (like Allow Scanning Network Files), and check that the status shows Succeeded (1). Use manual sync in the Company Portal to speed up the process.
Client Side Verification
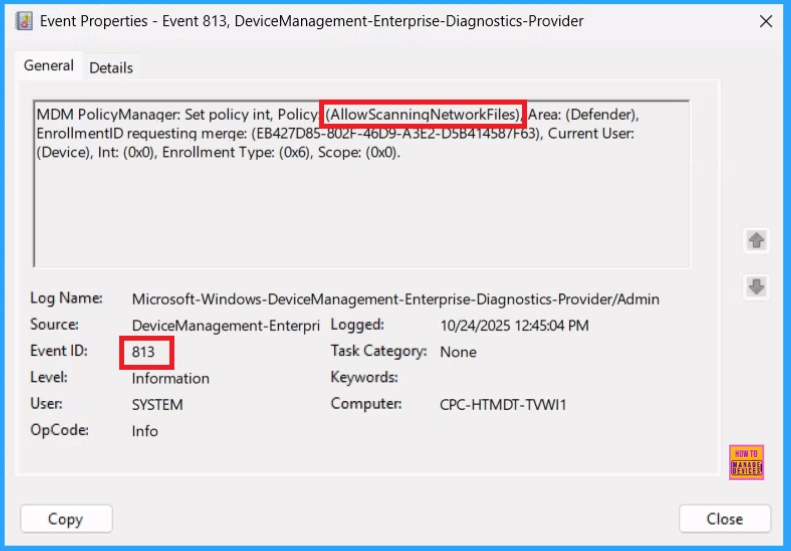
To confirm if a policy has been applied, use the Event Viewer on the client device. Go to Applications and Services Logs > Microsoft > Windows > Device Management > Enterprise Diagnostic Provider > Admin. From the list of policies, use the Filter Current Log option and search for Intune event 813.
MDM PolicyManager: Set policy int, Policy (AllowScanninqNetworkFiles), Area: (Defender),
EnrollmentID requestinq merqe: (EB427D85-802F-46D9-A3E2-D5B41458/F63), Current User:
(Device), Int: (0x0), Enrollment Type: (0x6), Scope: (0x0).
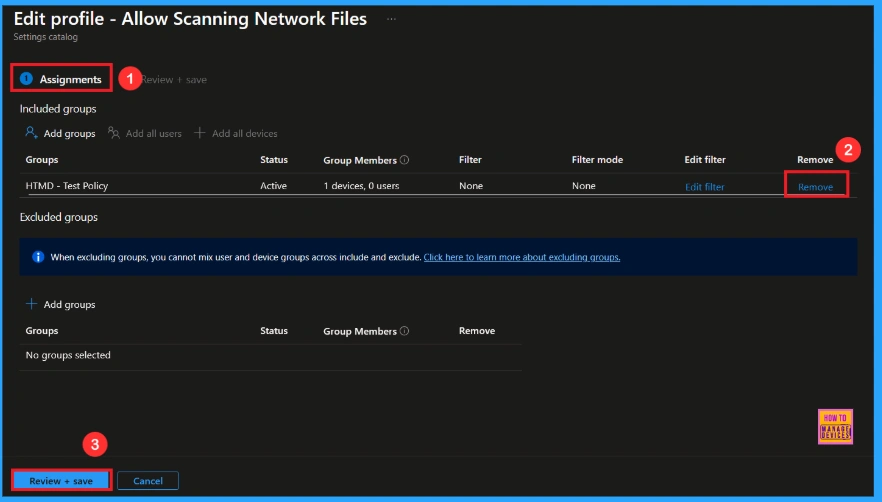
How to Remove Assigned Group from Scanning Network Files Policy
Sometimes, we need to remove a group from a policy assignment for security updates. Open the policy from the Configuration tab and click on the Edit button on the Assignment tab. Click on the Remove button on this section to remove the policy. Click Review + Save after making the change.
For detailed information, you can refer to our previous post – Learn How to Delete or Remove App Assignment from Intune using by Step-by-Step Guide.
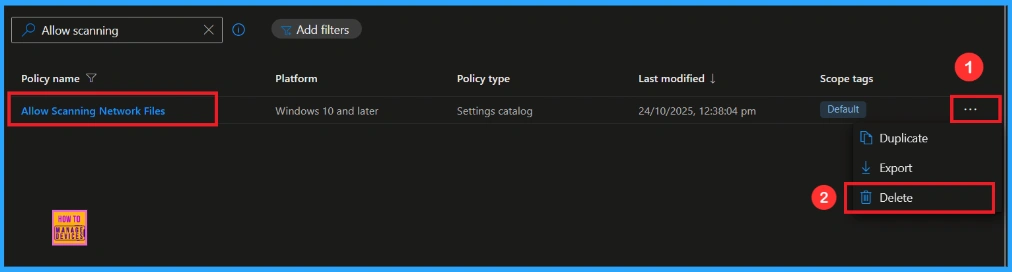
How to Delete Scanning Network Files from Intune
To delete an Intune policy for security or operational reasons. It is simple to do. I will demonstrate how to delete an Intune policy through the Enable First Logon Animation Policy. Click the three dots, then click the Delete option.
For detailed information, you can refer to our previous post – How to Delete Allow Clipboard History Policy in Intune Step by Step Guide.
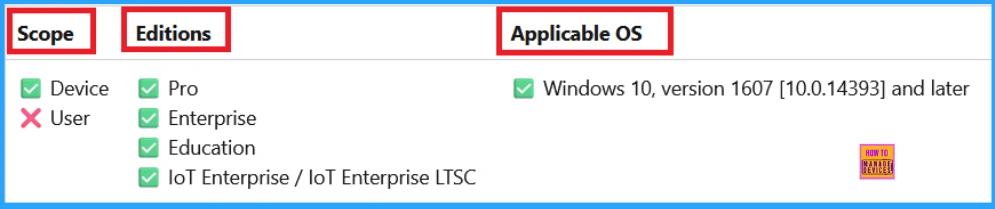
Windows Configuration Service Provider (CSP)
The policy Configuration Service Provider (CSP) is a tool for businesses to manage settings on Windows 10 and 11 devices. It details each policy’s function (Description Framework Properties), available choices (Allowed Values), and how it relates to older Group Policy settings (Group Policy Mapping details).
Description Framework Properties
- Format – Int
- Access Type – Add, Delete, Get, Replace
- Default Value – 1
Allowed Values
- 0 – Not Allowed
- 1(Default) – Allowed
Group Policy Mapping details
| Name | Value |
|---|---|
| Name | Scan_DisableScanningNetworkFiles |
| Friendly Name | Configure scanning of network files |
| Location | Computer Configuration |
| Path | Windows Components > Microsoft Defender Antivirus > Scan |
| Registry Key Name | Software\Policies\Microsoft\Windows Defender\Scan |
| Registry Value Name | DisableScanningNetworkFiles |
| ADMX File Name | WindowsDefender.admx |
OMA-URI Settings to Power Sleep Policy
An OMA-URI is a unique string used to configure specific settings on Windows 10 or 11 devices through a Configuration Service Provider (CSP). Its format is determined by the CSP and is used to apply custom device configurations.
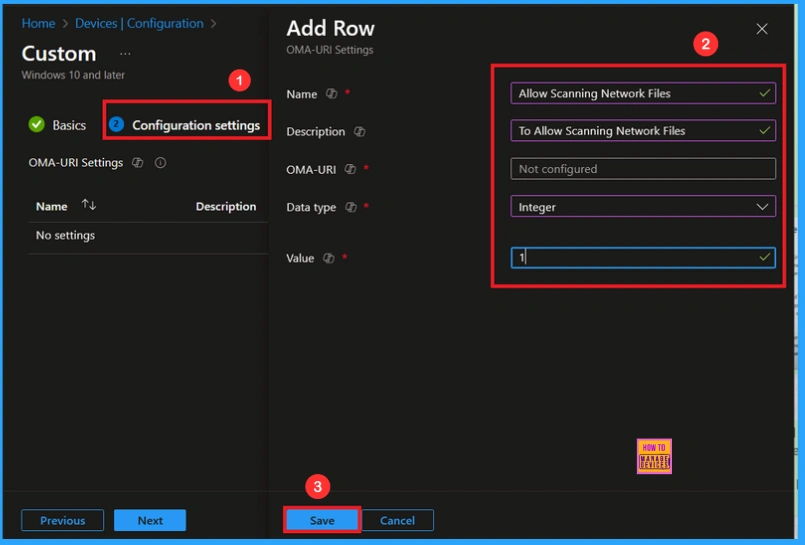
To create a new policy in Microsoft Intune, sign in and navigate to Devices > Configuration. Click on Create to start a new policy. Choose the platform as Windows 10 or later. For the Profile type, select Templates, then choose Custom. Provide a name for the policy (Allow Scanning Network Files) and add a description if needed.
- Click on + Add under OMA-URI Settings to configure the specific setting.
- To Configure the OMA-URI Setting, do the following
- Enter a name for this setting, such as Enable First Logon Animation.
- Description of the setting: To Enable First Logon Animation .
- Enter the following OMA-URI path:n./Device/Vendor/MSFT/Policy/Config/WindowsLogon/EnableFirstLogonAnimation
- Set the Data type to Integer.
- Enter the value
- 1 to Not allowed Scanning Network Files Policy
- 0 to allowed Scanning Network Files Policy
- After entering the above details, click the Save button.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.