Welcome to today’s post titled Intune Management Extension Deep Dive – Win32 App Deployment Troubleshooting Help Guide.
This post will show you how Intune Management Extension (IME), a.k.a Intune Sidecar, handles win32 app deployment on a managed Windows 10 endpoint.
This post intends to help you easily identify why a particular win32 app deployment from Intune is in an error state.
The post includes the below list of errors I encountered related to the Intune win32 app deployment.
- (0x80070004)
- (0x8007026B)
- Access is denied.(0x80070005)
- Error downloading content.(0x87D30067)
- Error unzipping downloaded content.(0x87D30065)
- Failed to retrieve content information.(0x87D30065)
- The Application was not detected after the installation was completed successfully(0x87D1041C)
- The content delivery network used for downloading application content times out(0x87D33006A)
- The system cannot find the file specified(0x80070002)
- The unmonitored process is in progress. However, it may timeout(0x87D300C9)
- The user logged off while the app policy was being processed(0x87D300CD)
- Unknown(0x87D30000)
However, the above list is not exhaustive, and there is a good chance you can encounter a different error. The aim is to help you relate to the error source and determine the cause.
Before starting with the actual content, and since this post targets Level 300 knowledge, let’s first understand how an application is packaged to be deployed as a win32 app from Intune.
Get to know the.INTUNEWIN package
Intune natively supports the deployment of Windows applications with extensions MSI, MSIX, APPX, and APPXBUNDLE as Line-of-Business (LOB) applications to the managed Windows 10 endpoints.
However, Intune cannot natively deploy an application as an EXE app package to an endpoint. From my understanding, this is probably the same reason you can’t send/receive an EXE file directly as an email attachment (security risk!).
This is where the Intune Management Extension (IME), a.k.a. Intune Sidecar, comes into play. It comes with the new app package extension “INTUNEWIN.”
.INTUNEWIN is a wrapper to contain the application executable source file (.EXE) along with its INSTALL and UNINSTALL commands (and other dependent files, if any)
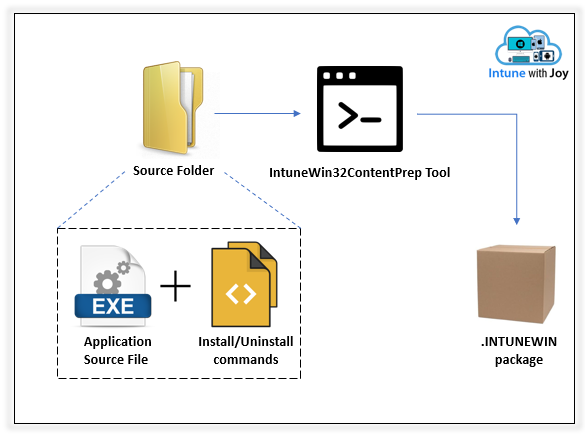
- Arrange the application source file (.EXE) and the Install/Uninstall commands (VB script/PS script/CMD/Batch) in a single folder, which will be specified as the Source folder.
- Get the Intune Win32 Content Prep Tool and run it.
- Specify the path to the Source folder.
- Specify the application source (.EXE) file.
- Specify the path to the Output folder. [This is where you will find the prepared.INTUNEWIN file]
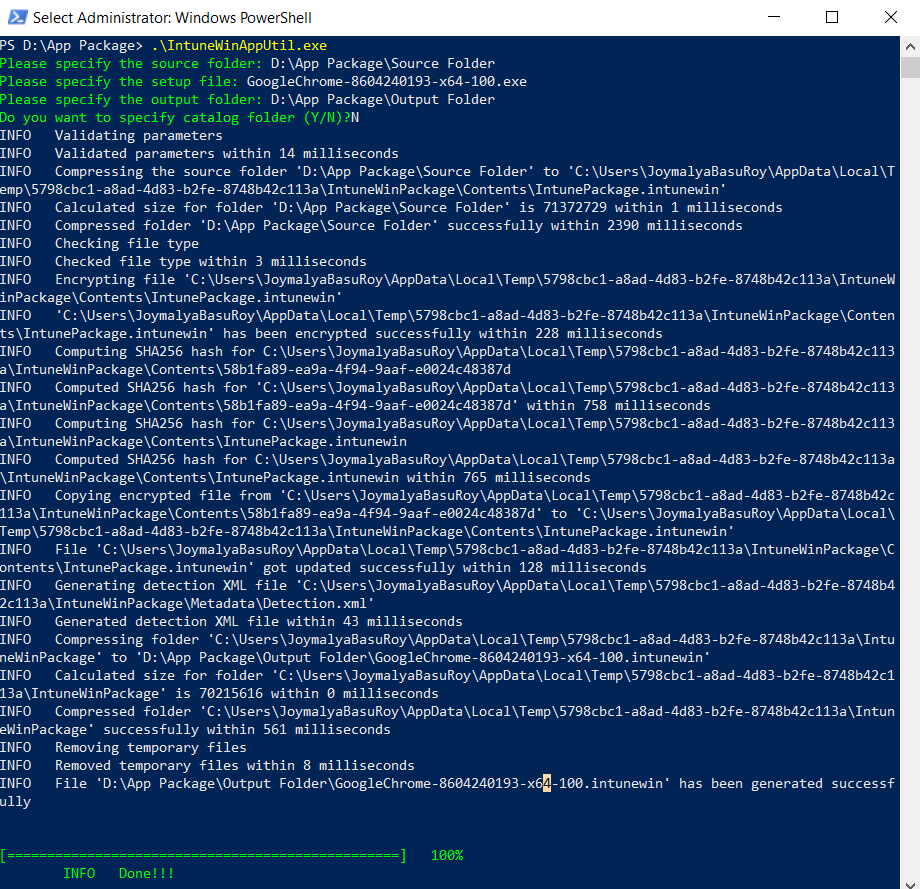
PS D:\App Package> .\IntuneWinAppUtil.exe Please specify the source folder: D:\App Package\Source Folder Please specify the setup file: GoogleChrome-8604240193-x64-100.exe Please specify the output folder: D:\App Package\Output Folder Do you want to specify catalog folder (Y/N)?N INFO Validating parameters INFO Validated parameters within 14 milliseconds INFO Compressing the source folder 'D:\App Package\Source Folder' to 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\IntunePackage.intunewin' INFO Calculated size for folder 'D:\App Package\Source Folder' is 71372729 within 1 milliseconds INFO Compressed folder 'D:\App Package\Source Folder' successfully within 2390 milliseconds INFO Checking file type INFO Checked file type within 3 milliseconds INFO Encrypting file 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\IntunePackage.intunewin' INFO 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\IntunePackage.intunewin' has been encrypted successfully within 228 milliseconds INFO Computing SHA256 hash for C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\58b1fa89-ea9a-4f94-9aaf-e0024c48387d INFO Computed SHA256 hash for 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\58b1fa89-ea9a-4f94-9aaf-e0024c48387d' within 758 milliseconds INFO Computing SHA256 hash for C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\IntunePackage.intunewin INFO Computed SHA256 hash for C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\IntunePackage.intunewin within 765 milliseconds INFO Copying encrypted file from 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\58b1fa89-ea9a-4f94-9aaf-e0024c48387d' to 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\IntunePackage.intunewin' INFO File 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Contents\IntunePackage.intunewin' got updated successfully within 128 milliseconds INFO Generating detection XML file 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage\Metadata\Detection.xml' INFO Generated detection XML file within 43 milliseconds INFO Compressing folder 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage' to 'D:\App Package\Output Folder\GoogleChrome-8604240193-x64-100.intunewin' INFO Calculated size for folder 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage' is 70215616 within 0 milliseconds INFO Compressed folder 'C:\Users\JoymalyaBasuRoy\AppData\Local\Temp\5798cbc1-a8ad-4d83-b2fe-8748b42c113a\IntuneWinPackage' successfully within 561 milliseconds INFO Removing temporary files INFO Removed temporary files within 8 milliseconds INFO File 'D:\App Package\Output Folder\GoogleChrome-8604240193-x64-100.intunewin' has been generated successfully [=================================================] 100% INFO Done!!!
A simple process, isn’t it?
If you look into the output of the IntuneWinAppUtil as above, you will see that the tool is doing the below steps.
- Creates a folder named IntuneWinPackage in the Output folder as specified.
- Compresses the contents of the Source folder as specified to create a .intunewin file and encrypts it using the SHA256 algorithm.
- Creates a subfolder named Contents under the IntuneWinPackage folder to store the compressed and encrypted file (.intunewin) created in the above step.
- It creates another subfolder named Metadata under the IntuneWinPackage folder, where it stores the encryption information for the Detection.xml file.
- Compresses the IntuneWinPackage folder as a whole to create the outcome as a .intunewin package.
Creating Win32 App in Intune – Know the backend activities performed by Intune
As we make the application in Intune, what happens in the background? You can see the high-level steps below:
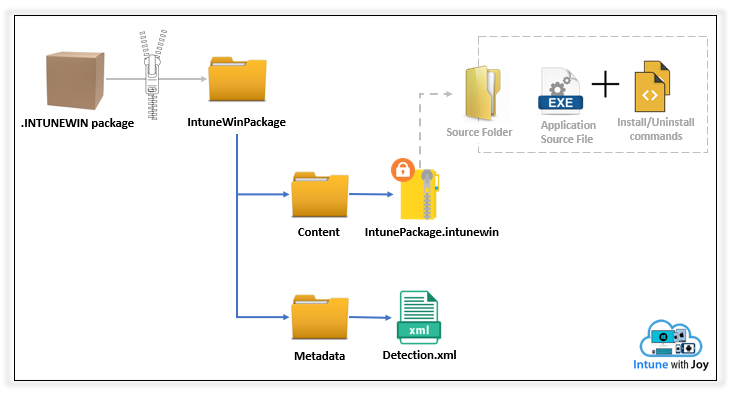
- The .intunewin app package gets uploaded to the Azure Storage account of the tenant
- Intune decompresses the package to retrieve the Detection.xml from the Metadata folder of the IntuneWinPackage as obtained.
- The actual app content, which is present as an encrypted .intunewin within the Contents folder, is submitted to the CDN.
- The decryption info (as retrieved from Detection.xml) is tagged to the app
When a request for the app comes (user-initiated for Available deployment, Intune initiated for Required deployment), the download URL to the encrypted .intunewin is delivered to the endpoint.
The IME agent creates a download job to download the file to the endpoint. Intune also sends down the decryption info so that the IME agent can decrypt and unzip the contents.
GET CONTENT INFO FROM SERVICE,RET =
{
"DOWNLOADURL\": "LINK TO CDN"
"DECRYPTINFO\":}
If you want to retrieve the source contents from a win32 app package uploaded to Intune, check this awesome blog post on Oliver Kieselbach.
Overview of how the Intune Management Extension (IME) agent handles Win32 app deployment
In a nutshell, the activity as performed by the Intune Management Extension (IME) agent to handle a win32 app deployment can be summarized below.
The IME agent on the managed Windows endpoint polls the Intune service to check for active app deployments. If found, it starts processing the application according to the conditions (Applicability) and criteria (Detection) set by the Admin while creating the app package.
The IME agent retrieves the.INTUNEWIN package file from the service, unwraps it to recover the original application. EXE file and execute it using the provided INSTALL command.
After executing the application, the IME agent monitors the installer process and, after installing it, checks the installation success as per the criteria (Detection) to report back to the service.
The above is only to help you understand the process easily, as we will dive deeper into the details below.
Deep Dive into IME Agent Win32 App Deployment Backend Process
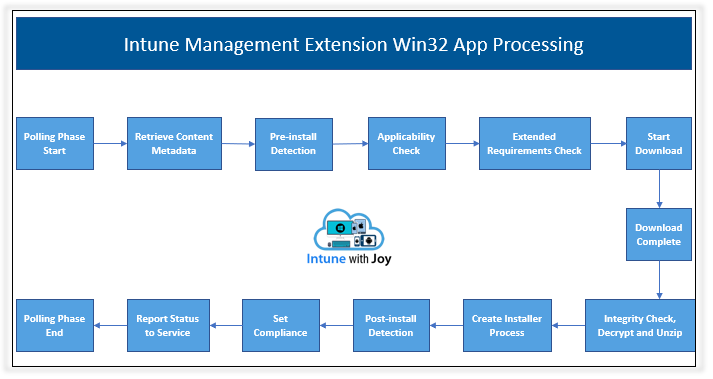
IME Agent has to go through the following phases to process a Win32 app deployment on the endpoint.
- Polling Phase Start
- Retrieve Content Metadata
- Pre-Install Detection
- Applicability
- Extended Requirements
- Download
- Integrity Check and Unzip
- Installation
- Post-Install Detection
- Set Compliance
- Report Status
- Polling Phase
You can easily see this by going through the Intune Management Extension logs located at C:\ProgramData\Microsoft\IntuneManagementExtension\Logs
A summarized step of action is given below.
- IME agent initializes.
- IME agent discovers Intune endpoint https://fef.msuc##.manage.microsoft.com/SideCar/StatelessSideCarGatewayService
- IME agent fetches AAD token via impersonating logged-in user account.
- IME agent starts application polling to query available/required Win32 app.
- IME agent gets application policy (detection/applicability/extended requirement check details).
- IME agent checks if the application as queried has any dependencies declared.
- IME agent post dependency check, if the app is standalone, starts running the Detection Logic
- SideCar will run a WMI query against the MSI code defined for MSI code-based detection.
- For Path-based detection, SideCar will traverse the PATH as defined to check the presence.
- For Registry-based detection, SideCar will check the specified reg_path for the presence of the reg_key and its value.
- SideCar ExecManager triggers the script and determines the result based on the hand’s exit status for a custom script-based detection.
- If pre-install detection is determined as False, the IME agent will check the applicability and extended requirements.
- If all parameters are satisfied, the IME agent will download the package, which will be matched by a BITS job created for it.
- Once the download job is complete, it will check the package integrity, decrypt the package using the encryption info provided in the content response, and unzip the content to IMECache.
- IME agent creates the Machine/User session installer process based on the app deployment context.
- After executing the installer process, the IME agent runs the Detection rules again to confirm the installation.
- The IME agent has deemed the app install successful only if post-install detection is determined as True.
- IME sets the compliance state and creates an app report based on the post-install detection result to be returned to the service.
- The report is sent and locally saved to the cache.
- IME agent stops the current app polling session.
Relating errors to each phase of IME in which it handles a win32 app
The error you get from the Intune portal for a Win32 app deployment can be due to a mistake in the win32 app handling by the IME agent at any of the phases discussed above.
As such, it is important to relate the displayed error to its source to identify if the error is due to
- The app package itself (problems with the source), or
- Any configuration issues while creating the app in Intune (problem with detection or another config), or
- Network-related issues (problem with delivery and download of the package).
So, let’s start by seeing what probable errors you might get in each phase of the Intune Management Extension while the IME agent processes a Win32 app deployment on the endpoint.
IME Win32 SideCar Agent Polling Phase Start
For IME to work, it needs the token, which it fetches by querying the currently logged-on user profile.
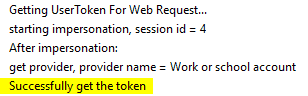
With the AAD token, IME proceeds to the next phase, where it contacts the service to get the application policies made available to the user/device.
As you can understand, the most common error in this phase is due to IME’s inability to get the token. In such a case, you can expect to see a log entry like the one below.
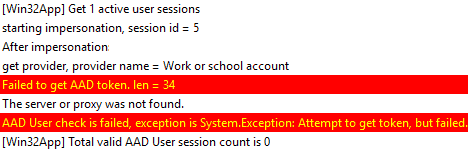
Or, if you have AAD joined post-OOBE setup from Settings, you would expect to get this unless you switch users and login with your AAD account.
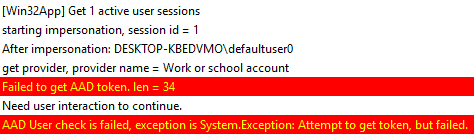
Retrieve App Metadata
Once IME has got the token, it checks the current proxy and sends a network request to the service to fetch the Win32 apps (policies)
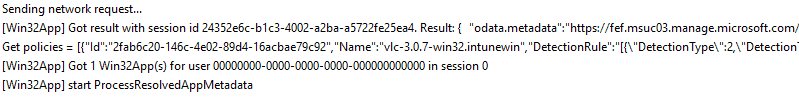
The result, as received, is used by IME to configure the detection methods, applicability checks, and requirements checks for this app.
An error that can occur in this phase is due to network connectivity resulting in failure to retrieve content information(0x87D30065)
Pre-Install Detection Check
Detection can be based on Registry, MSI Product code, or File Path, as configured while creating the app in the Intune portal.
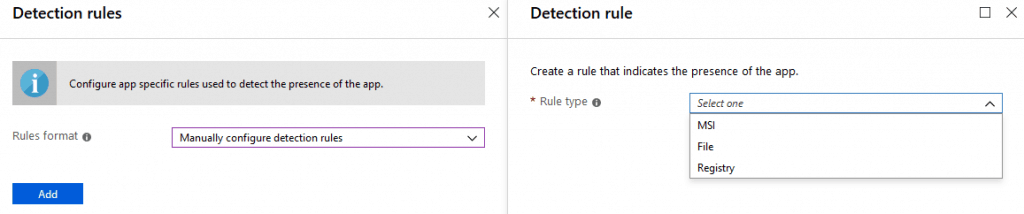
It can also be a custom script, where the IME triggers the script, and the detection result is based on the script’s exit status.
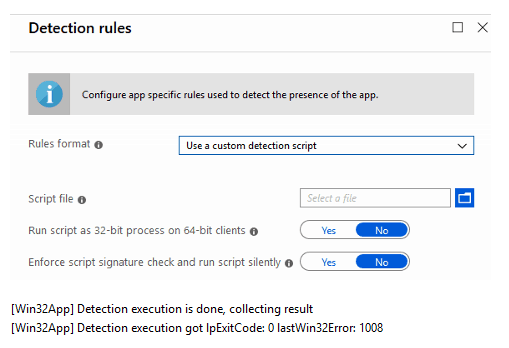
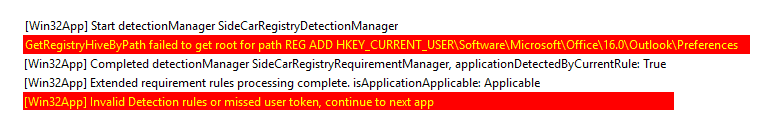
The error that can occur in this phase is caused due to improper detection logic, which will cause IME to skip further app processing. Sample error in log show like this
Applicability Check
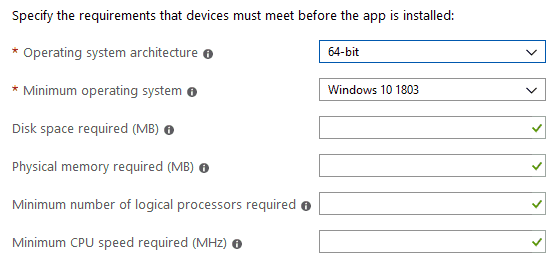
IME processes the settings as specified in the app policy to check if the system meets the requirements.
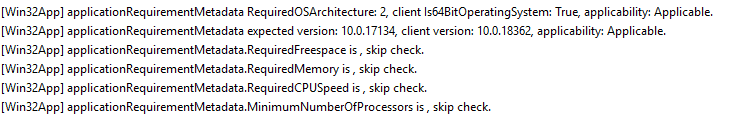
An error can occur when IME fails to query the requirements, which can be due to generic system issues.

In such cases, it will report back with the error Unknown (0x87D30000). The other common errors you can get are
- Device architecture (e.g., x86/amd64) does not apply to the application.
- OS version on the target device is less than the configured minimum.
Extended Requirements Check

If any additional requirements have been specified in-app, IME checks if the system satisfies the same.

Error in this phase depends if the IME encounters any System Exception while querying the specified rules or if a custom script is used for the purpose, then the exit code of the hand.
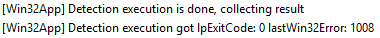
The most common error in this phase is RegistryRequirementNotMet. If the specified requirement is not met, a log entry like this can be expected in both the Applicability check and Extended Requirement check.

Download Phase
This is when IME downloads the app package (.intunewin) from the Intune CDN to the device. The download is done to path C:\Program Files (x86)\Microsoft Intune Management Extension\Content\Incoming
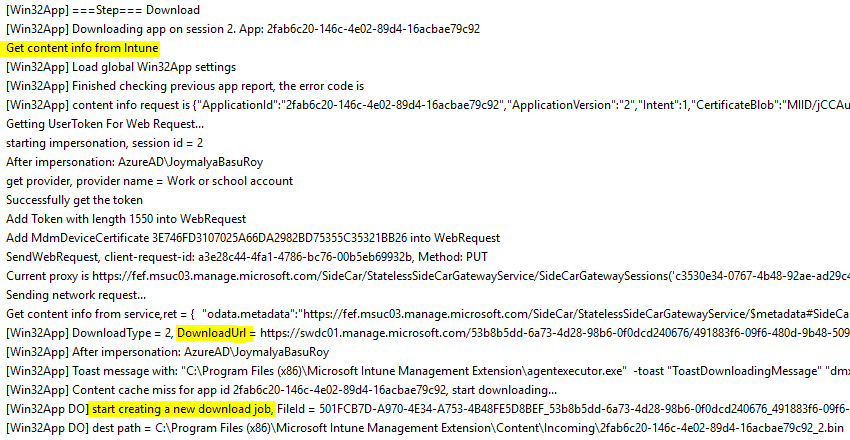
The error that can occur in this phase is usually due to network and dependency on the BITS service, which handles the download job as created, resulting in errors not limited to
- Unknown (0x87D30000) – the error that is reported when the last step is defined as a success, but the current step has no defined output
- Incorrect function (0x80070001) – generally related to invalid tasks
- The unmonitored process is in progress. However, it may timeout. (0x87D300C9)
- Error downloading content. (0x87D30068)
- The content delivery network is used for downloading application content timed out. (0x87D3006A)
- The physical resources of this disk have been exhausted (0x8007013A)
Integrity Check and Unzip the package
Post download, the file is moved to the path C:\Program Files (x86)\Microsoft Intune Management Extension\Content\Staging\ where the IME checks the integrity of the application package as downloaded.
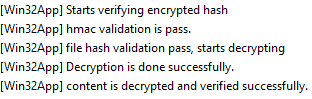
At this point, you can encounter the error The system cannot find the file specified. (0x80070002) which happens due to AV.
It is recommended that the locations used by IME be excluded from being monitored by an AV, as this may interfere with the process.
After post successful integrity check and decryption, the file (this is the .intunewin file as present within the Contents subfolder of the IntuneWinPackage folder) is unzipped to location C:\Windows\IMECache\
The errors that can occur during this phase are
- Error unzipping downloaded content. (0x87D30067)
- The physical resources of this disk have been exhausted (0x8007013A)
- Incorrect function (0x80070001)
- Unknown (0x87D30000)
Installation Phase
IME starts the execution and sets the retry count (there are a total of 3 retries with 5-minute intervals).
Flow for the app in the User Context
It creates the installer process by fetching an elevated token for the current user if the app is in the User Context. It is not very common, but if IME fails to get an elevated token for the user, it can result in access being denied. (0x80070005)
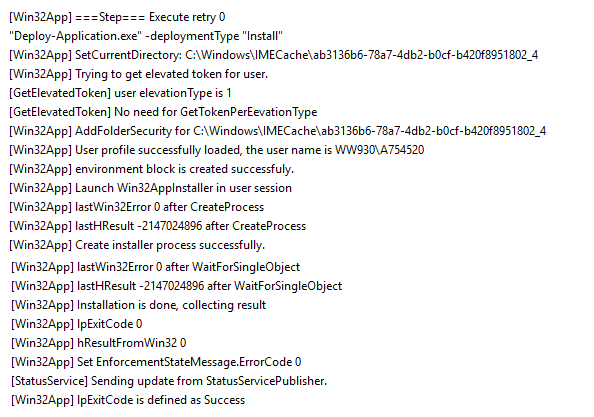
Before IME could create the installer process, if a change in session is detected, like log-off, it will cause an error like the one below, resulting in The user logging off while the app policy was being processed. (0x87D300CD)
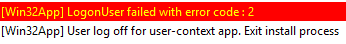
Flow for the app in Device Context
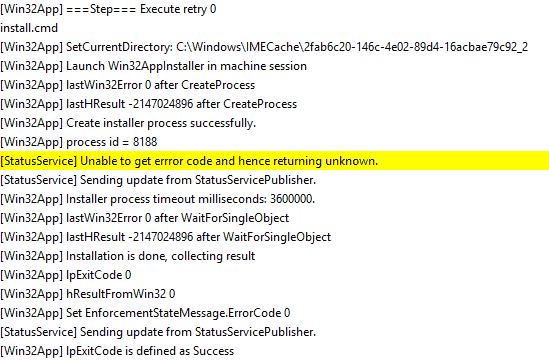
You can safely ignore that StatusService warning.
The installer process created by IME has a predefined timeout of 60 minutes. If the function fails to install the application during this time, which may be due to system activity (high CPU utilization), such a case results.
- Unknown (0x87D30000)
- The unmonitored process is in progress. However, it may timeout. (0x87D300C9)
In general, errors in this phase are directly related to the application and are usually thrown by the IPExitCode or last result. For example, if the installation is triggered via a script, the IPExitCode will define Success or Error.
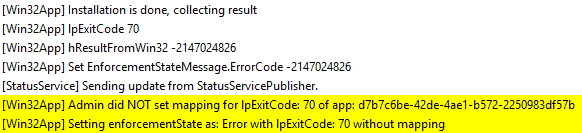
You will mostly see the undefined errors thrown by LastHResult like this.
- (0x80070004)
- (0x8007EA61)
- (0x8007EA68)
If the installer process fails, IME has a retry check of 3 – it tries 3 times to install the app if it encounters any failure during a processing cycle.
The retry interval is 5 minutes from the last failure. However, IME will start from the beginning of the app processing phase for each retry. The detection, applicability, and extended requirements will again be checked.
Regarding the download phase, it will not again initiate a download but will find the app package from the Cache itself.
This is because the contents of the C:\Windows\IMECache\ folder are cleaned up successfully post-install only. At this point, you are most likely to encounter the error. The system cannot find the file specified. (0x80070002) which happens due to AV.
Post-Install Detection Phase
This is the phase where IME triggers the detection manager to execute the detection rules once more to confirm the app install status.
Even if the installation is done, but the detection rule cannot check the right place, it will result in an IME report the same as a failure.
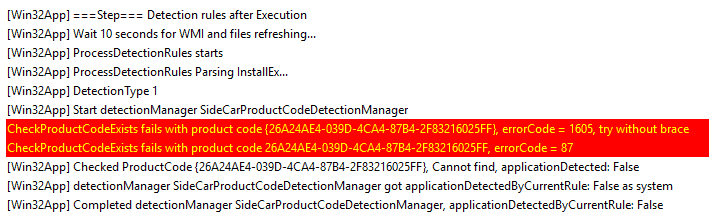
Error in this phase is caused again due to improper detection logic
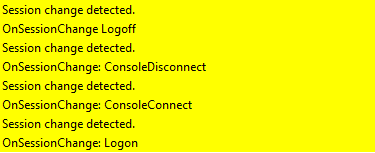
At this stage, a change in session will cause IME to report back as The application was not detected after the installation was completed successfully (0x87D1041C).
Set Compliance State
This is the phase where IME sets the compliance for the app policy based on the outcome of the Installation phase and Post-Install Detection phase results, cleans the contents from the IMECache folder, and creates the app report.
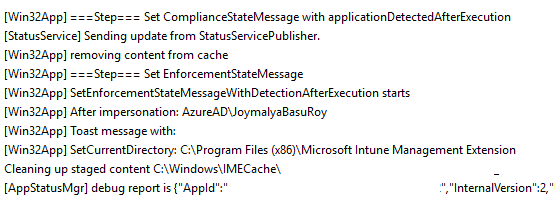
Same as above, if a change in session is detected, it will result in The application was not detected after the installation was completed successfully (0x87D1041C). If the install succeeds but the post-install detection result is false, it will still report as an error as below.
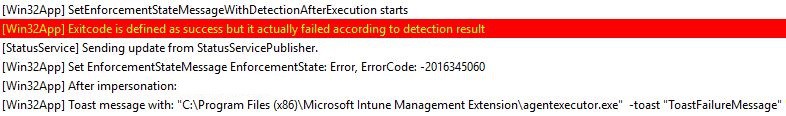
Report Status to Service
The last phase of app processing is where IME sends the result to the service and saves the results locally.
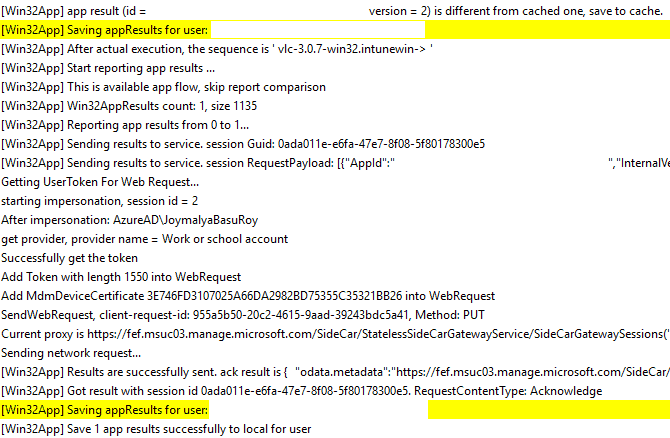
IME can fail to send the report and save it for the following reasons
- Network connectivity issue
- User logs off before IME can send the final app results or any Session change detected
- The system goes to sleep due to inactivity
which all points to the same error. The application was not detected after the installation was completed successfully (0x87D1041C)
In the case where the IME client itself faces some error, it might cause the Client error to occur (0x87D300CA)

and requires evaluation of the ClientHealth.log from C:\ProgramData\Microsoft\IntuneManagementExtension\Logs
The Client Health evaluation is performed every 8 hours.
Since the application is not enforced by Intune but depends on the user in the Available app flow, IME does not re-evaluate the app status if it fails in the 1st instance.
IME will continue re-evaluating each app result in each cycle in case of Required app flow.
As such, even if the application was installed but due to any issues reported as “The application was not detected after installation completed successfully (0x87D1041C)“, IME won’t re-evaluate to correct it in the subsequent sync cycles.
But for a required application, even if it is reported as an error (unless an error is related to the package itself), it is good to be corrected in the subsequent sync cycles.
The End – Intune Management Extension
That was all. I hope you will find this post useful.
Starting 1st Jan 2021, I have started my blog site. You will find all my latest posts on Intune here at joymalyabasuroy.com
Resources
- Intune Standalone – Win32 app management
- Convert MSI package to IntuneWin
- Intune Win32 App Troubleshooting Client-Side Process Flow
- Intune Application Model Deployment Guide
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Joymalya Basu Roy is an experienced IT service professional with almost 5 years of experience working with Microsft Intune. He is currently working as a Senior Consultant – Architect with Atos India. He is an ex-MSFT, where he worked as a Premiere Support Engineer for Microsoft Intune. He was also associated with Wipro and TCS in the early stages of his career. He was awarded the Microsoft MVP award for Enterprise Mobility in 2021. You can find all his latest posts on his own blog site MDM Tech Space at https://joymalya.com

Great stuff, Joymalya. Thanks.
Good to see this issue on unzipping error in your blog: “Error unzipping downloaded content. (0x87D30067)”. In my case this has to do with a “PathTooLongException” where the depth of some package files after unzipping becomes too lengthy (something over 248 characters…??). Any idea on how to resolve this, please?
Thank you
same here =(
same here. Does anyone have a solution?
What does AV stand for?
Anti-Virus program running on the system
Great post.
How does IME handle an version update to a package marked as successful install? Can the existing app be reused or do you need to create a second version?
Error code: 0x87D30067
Error unzipping downloaded content.
That is usual Microsoft ZERO helpful error. How can I even start tackling it?
I have seen this for win32 app packages which contain not only files but nested folders within which need to be created upon unzipping, however, it was more of a problem with filenames which was fixed with the Intune Win32 Prep Tool v.17 with support for Unicode file and folder name. Also, the incoming win32 package is downloaded to location C:\Program Files (x86)\Microsoft Intune Management Extension\Content\Incoming\ post which is then moved to C:\Program Files (x86)\Microsoft Intune Management Extension\Content\Staging\ from where the IME client tries to unzip the contents to C:\Windows\IMECache. Thus there can be any file operation error resulting in the IME error you see. Also, the IME client works by impersonating the current logged in user if the app is a user-context app, and if the end-user is a standard user on the endpoint, may result in privilege issues while creating the processes. There can be many possibilities and it really requires a proper check-up by the app packaging team who handles and tests app packages.
Though I do agree with you that sometimes, Intune errors really don’t make sense unless we dig deeper.
Excellent post. Thank you. Question : what s the reason for the detection rules be checked before installation? Makes no sense to me.
To see if it’s already installed.
Hi,
I have a question regarding the post-install detection. I have a detection (custom script looking for a file in user’s appdata) which works and app that installs (actually uninstalls an application from the endpoints) flawlessly. What I’ve noticed is that it detects very slowly when the file appears again so it should trigger the app again. It takes about 2-3 days no matter how much I sync the device for it to detect that the file is there again.
1. Is this normal behavior? Why does it take so much time and syncing does not retrigger the detection script?
2. Is there a way to make this happen faster?
Thank you in advance.
Hello Joy,
Thanks for this incredibly helpful post.
I was curious, what could an admin do should the IME be unable to get the token and provide and error in the logs.
Thanks again!
This is a great article, however I am receiving a “Error code: 0x87D30067 Error unzipping downloaded content” on about 10% of our devices, this package deploys fine on all other devices, so I can rule out the package. Also on the devices where it fails all other Intune apps deploy without issue, so its not the directory or the unzip process or AV. Any assistance would be greatly appreciated.