Let’s discuss How to Configure Sign-In Frequency Every Time and Periodic Reauthentication Policies in Microsoft Entra. Sign-in frequency enhances security by forcing users to re-authenticate after a set time or period of inactivity. Administrators can configure this by specifying hours, days, or enforcing re-authentication Every time for maximum security.
The Every time reauthentication setting only functions with Microsoft Remote Desktop and Windows Cloud Login when single sign-on is active for Cloud PCs. Users will be asked to reauthenticate every 5 to 10 minutes when starting a new connection.
By default, Microsoft Entra ID asks users to sign in every 90 days. While secure, this practice can lead users to automatically enter credentials, potentially exposing them to malicious prompts. While reducing frequent sign-in prompts might seem risky, Microsoft Entra ID cancels sessions when security rules are broken, like after a password change or on a risky device.
Previously, sign-in frequency only controlled the initial sign-in, not ensuing multifactor authentication (MFA) prompts, on joined or registered devices. Responding to customer requests, Microsoft Entra ID now extends sign-in frequency policies to also enforce periodic MFA re-authentication.
Table of Contents
What Applications Support Microsoft Entra ID’s Sign-in Frequency Policies?
Sign-in frequency policies work with applications that use standard OAuth2 or OIDC protocols, which includes most Microsoft native apps like Office 365, the Azure portal, and Teams.
It also supports non-Microsoft SAML and OAuth2/OIDC applications, as long as they redirect authentication requests back to Microsoft Entra ID and do not manage their own session cookies.
Sign-In Frequency Every Time and Periodic Reauthentication Policies
The Every Time reauthentication option forces users to fully sign in for critical actions, like accessing sensitive apps, VPNs, privileged roles, virtual desktops, or when risks are detected. This is highly secure but can lead to MFA fatigue if overused. It works best with apps that properly manage token refreshes, with web apps being less disruptive.
To prevent excessive prompts, a five-minute grace period is applied. For Microsoft 365, time-based sign-in is recommended. For the Azure portal and Entra admin center, time-based or PIM activation reauthentication via authentication context provides a better user experience.

- Top 40 Microsoft Entra Interview Questions and Answers: Modern Identity and Access Management Solution
- Enhancing OAuth App Security And Governance With Microsoft Defender For Cloud Apps
- Methods To Break The Token Theft Cyber-Attack Chain On Entra
Sign-in Frequency in Managed and Personal Devices
For company-managed devices (Microsoft Entra joined/hybrid), unlocking or signing in updates a Primary Refresh Token (PRT) every 4 hours, which is then checked against the sign-in frequency policy. Personal devices (Microsoft Entra registered) don’t work the same way, but Microsoft Entra WAM can update the token during app sign-ins.
Sign-In Frequency Behavior Based on Application Type
Microsoft Entra app selection influences the behavior of sign-in frequency policies. The following table showcases different types of applications and the behavior of sign-in frequency policies.
| App Name | App ID | Behavior |
|---|---|---|
| Windows 365 | 0af06dc6-e4b5-4f28-818e-e78e62d137a5 | Forces re-login when users access their Cloud PC list or initiate Cloud PC actions, such as a restart. |
| Azure Virtual Desktop | 9cdead84-a844-4324-93f2-b2e6bb768d07 | Users must re-authenticate when authenticating with the Azure Virtual Desktop Gateway. |
| Windows Cloud Login | 270efc09-cd0d-444b-a71f-39af4910ec45 | For Cloud PC authentication, administrators should configure both the Microsoft Remote Desktop and Windows Cloud Login apps. |
| Microsoft Remote Desktop | a4a365df-50f1-4397-bc59-1a1564b8bb9c | With single sign-on activated, users must re-authenticate upon Cloud PC login. |
Configuring Every Time Sign-In Frequency
Re-authentication is only required when a new access token is requested for a resource. Existing connections remain uninterrupted, regardless of the sign-in frequency. However, network issues that force a new session will trigger re-authentication, leading to potentially more frequent prompts on unreliable networks.
To manage how frequently users must re-authenticate, you can define a time interval. This setting determines the duration of a user’s active session, which can be configured in hours or days to align with your security requirements.
- Log in to the Microsoft Intune admin center with appropriate administrative credentials.
- Select Endpoint Security
- Click on Conditional Access
- Click Policies under Overview
- To configure sign-in frequency, open your policy that you created previously.
- For example, I select Edge-App Protection Policy.
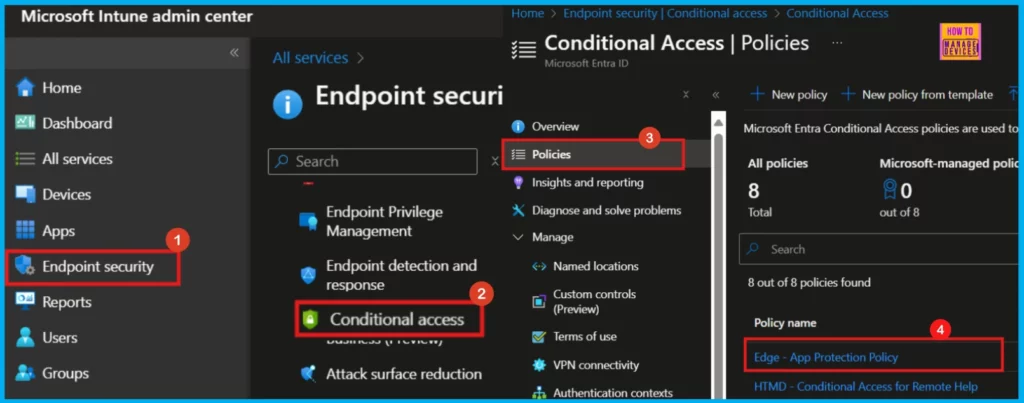
Upon clicking the which you want to configure sign-in frequency (here, Edge-App Protection Policy), another window will open, where we can control the policy access according to our needs. Conditional Access allows you to bring together diverse signals, make access decisions, and enforce organizational policies.
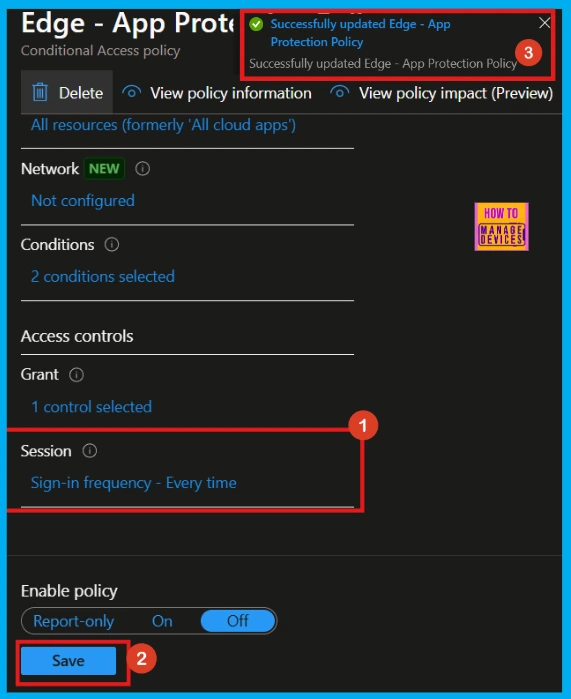
- Under the session pane, select the sign-in frequency option.
- Then choose either periodic reauthentication or Every Time.
- Here, I select Every Time.
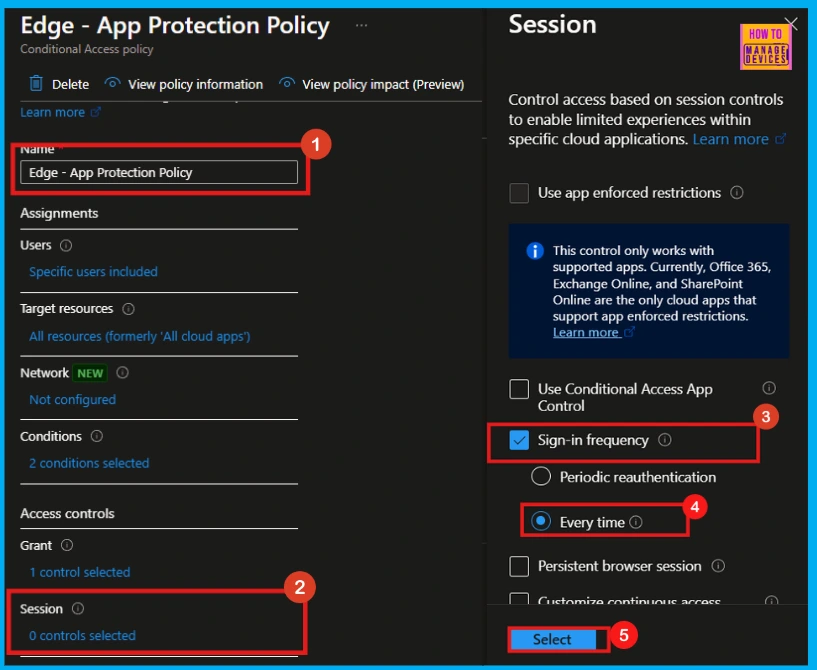
Once Every time is selected, the Session tab will show that Sign-in frequency Every Time is enabled. Click Save to complete the process.
- Now, a notification will be received saying that the Successfully updated Edge-App Protection Policy.
Resources
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been a Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.