Let’s discuss Methods to Break the Token Theft Cyber-Attack Chain on Entra. Recently, Microsoft Introduced MFA for Microsoft Entra to protect Users’ privacy and security. MFA in Microsoft Entra is really helpful for Users to maintain their security.
However, password attacks are common issues, and Entra users also face them. Attackers can break passwords, so Entra Users’ privacy is a big question now. The security of every user is very important for the organisation’s growth.
In this Critical situation, Microsoft decided to defeat more advanced attacks, starting with token theft. A token is an authentication artefact that grants access to resources. When users sign in to an identity provider such as Microsoft Entra ID using a set of credentials, they will get a Token.
This article will discuss Tokens, how token theft works, and how to protect tokens. It will help you ensure the security of every Entra user in your Organization and easily break the Token Theft Cyber-Attack Chain on Entra.
| Index |
|---|
| Methods to Break the Token Theft Cyber-Attack Chain on Entra |
| Tokens |
| How Token Theft Works |
| Protecting Token |
| Methods to Reduce the Risk of Token Theft |

- Retirement of Legacy Authentication Methods Management in Microsoft Entra ID
- High Level Overview of Identity Protection in Microsoft Entra ID
- Retirement of Legacy Authentication Methods Management in Microsoft Entra ID
Methods to Break the Token Theft Cyber-Attack Chain on Entra
As I mentioned, attackers’ intrusion into an individual’s privacy is a major problem in different scenarios. Nowadays, Microsoft Entra Users face Token Theft cyber-attacks, and Microsoft is plain to Break the Token Theft Cyber-Attack Chain. Before breaking this theft chain, we must know more about Tokens and how token theft works.
Tokens
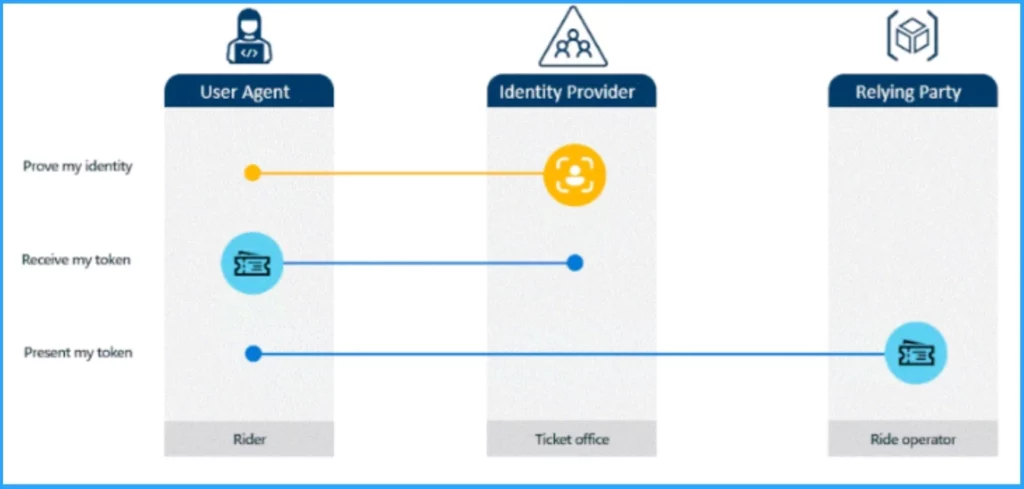
As I mentioned before, Tokens are issued by an IDP(identity provider)such as Microsoft Entra for a user when they successfully sign in using a set of credentials. The tokens describe who you are and what you have permission to do.
When you want to access an application or service, you get permission to talk to that resource by presenting a correctly signed token from a trusted issuer. The software on the client device handles all the tokens.
- Users get a token for the first time can be called a session token
- It shows that you successfully signed into the IDP and how you signed in.
- When the user signs into an app, it can exchange that session token for an access token
- Access token gives you access to specific resources for a certain amount of time without reauthenticating.
| Tokens | Life Time |
|---|---|
| Session Token | Less Life Time |
| Access Token | More Life Time |
- Longer lifetimes(session token) are more convenient for users and more resilient against potential IDP outages, and it is a risk
- Shorter lifetimes(access token) are safer
- When a token expires, or continuous access evaluation reports heightened risk, the client returns to the IDP and requests a refresh.
- If the user loses the session token, the attacker gets the ability to access the token
How Token Theft Works
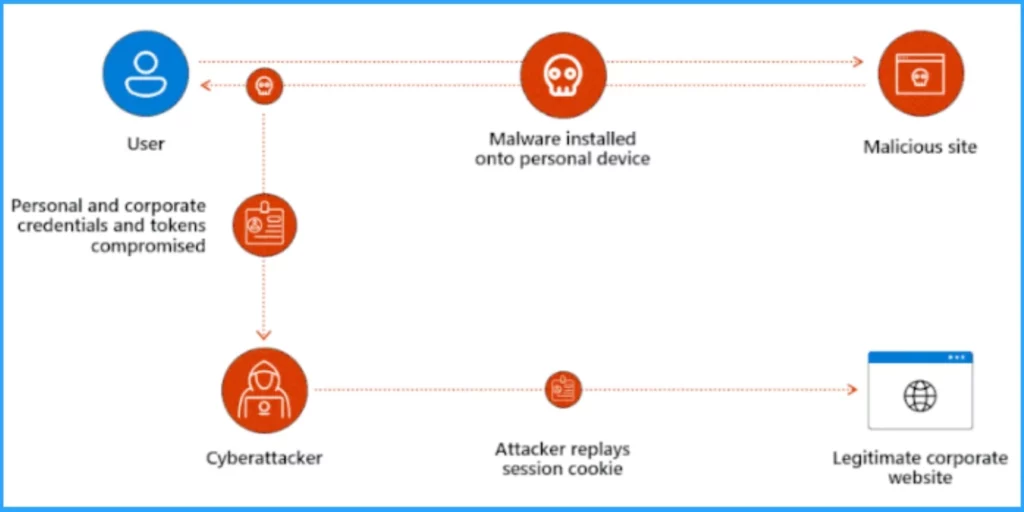
Attackers steal tokens to impersonate you and access your data for as long as the stolen token lives. They get access to a token from where it is stored (on the client, in proxy servers, or, in some cases, in the application or network logs) to acquire it and replay it from somewhere else.
When the attacker steals a user’s session token, makes a copy of your session, and uses it to get unlimited new access tokens to keep stealing your data. Users cannot identify this theft and your token seems fine. The attacker steals the tokens in different ways, such as:
- Copying tokens from the network as they pass through a proxy or router that the attacker controls.
- Extracting tokens from unsecured server logs of the relying party.
Protecting Token
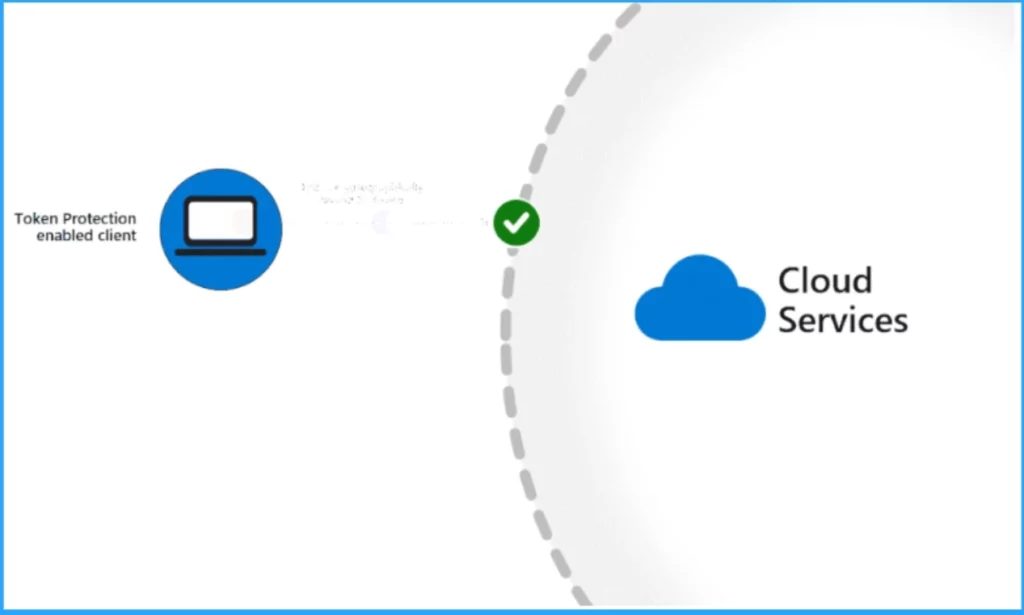
Microsoft Protects Tokens by using tokens that are cryptographically tied to the device. This is often called token binding but may also be called sender-constrained tokens or token proof of possession.
Token protection makes it harder to execute the main types of attacks designed to steal tokens, including network-based attacks and those using malware on the device, by restricting the use of the stolen token from devices they weren’t issued to.
Methods to Reduce the Risk of Token Theft
Users must try to defend attackers from stealing tokens the first time. We can follow some steps to reduce token theft. With these methods, users can control most of the token thefts. Users must use managed and compliant devices. Turn on the Credential Guard for your Windows users.
- What is Entra ID One Person One License Details
- External Collaboration Settings in Entra ID
- Modernize MFA Authentication Policies in Entra ID
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.
