Let’s discuss modernizing MFA Authentication Policies in Entra ID. Microsoft Entra ID is an extensive cloud-based identity and access management service with strong user and group management capabilities. You all know that Microsoft Entra ID was previously known as Azure AD.
We live in a world where online security threats are constantly progressing. Microsoft Entra ID is a strong protector in these situations, offering credible methods to verify and confirm user identities. Learning about and using their strongest security settings to keep safe is vital.
Microsoft Entra ID offers extraordinary configuration options. The initial default settings for new users aren’t very secure. Many organizations fail to adjust these settings enough, so they don’t get the strongest security possible.
Microsoft EntraID is shifting its focus toward eliminating passwords as authentication methods. Instead, it offers new, safer, and simpler login options. The latest updates introduce passkeys that operate seamlessly with your device and security keys to protect you from fraudulent sign-ins.
- What is Microsoft Entra ID?
- Entra ID Backup using Microsoft 365 Documentation Tool
- Optimize Entra License with New Entra License Utilization Feature
- What is Face Check Feature in Entra
Modernize MFA Authentication Policies in Entra ID
To prevent these fake login attempts, update your Multifactor Authentication (MFA) policies to the latest management style. You must turn off all the old options in the Password Reset and the previous MFA portal.
This change will give you much better control over the login methods people can use and when they need to use them. After the password reset, you can change the migration settings.
- Sign in to Microsoft Entra Admin Center
- After the password reset option
- Click on the Authentication method under the Protection policy
- Click on the Policies
- Select Manage Migration
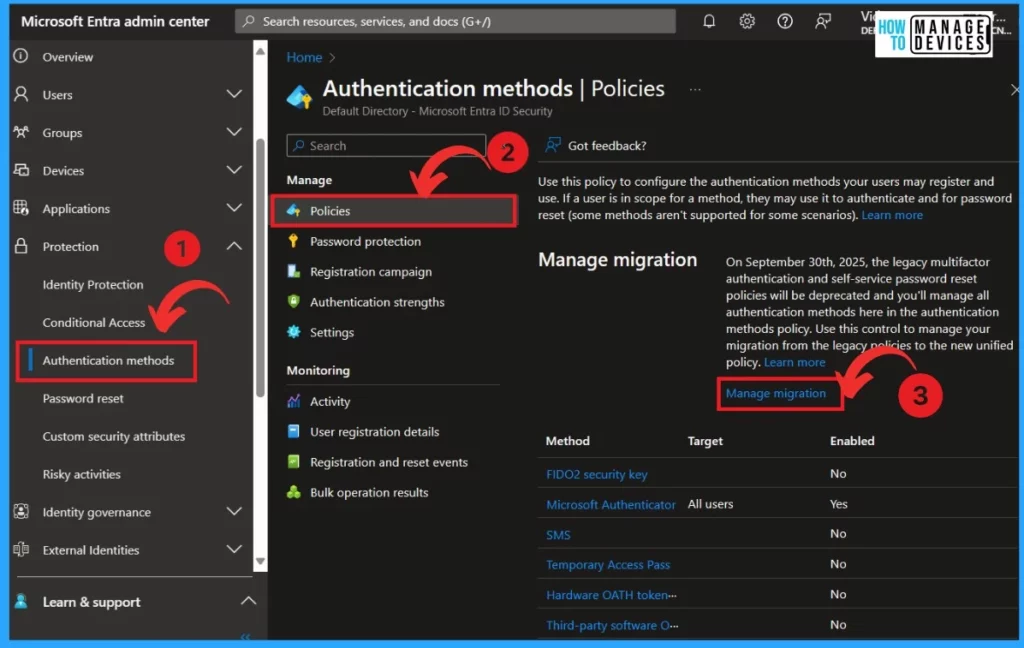
When you click on the Manage migration(”On September 30th, 2025, the legacy multifactor authentication and self-service password reset policies will be deprecated, and you’ll manage all authentication methods here in the authentication methods policy. Use this control to manage your migration from the legacy policies to the new unified policy’‘)
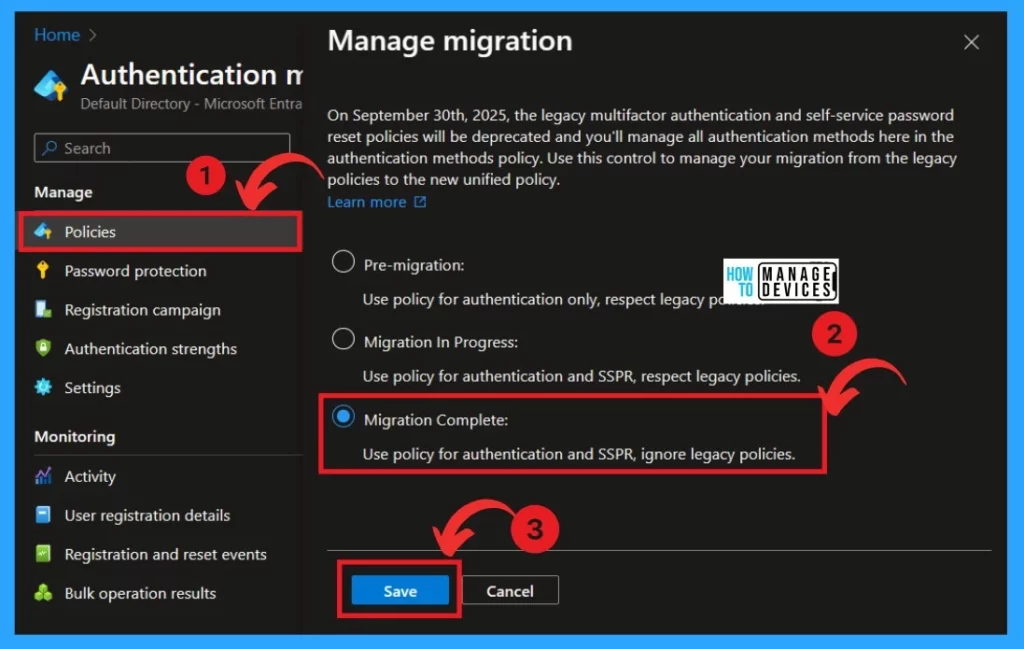
- You can adjust the migration option; there are 3 options available for migration.
| Migration Options | Info |
|---|---|
| Pre-migration | Use Policy authentication only; respect legacy policies |
| Migration in Progress | Use policy for authentication and SSPR,respect legacy policies |
| Migration complete | Use policy for authentication and SSPR; ignore legacy policies |
- List of Entra ID Ignite 2023 Sessions
- Free Entra Training Videos | Start Learning Entra ID Azure AD
- Create Dynamic Group based on Employee Hire Date in Entra ID
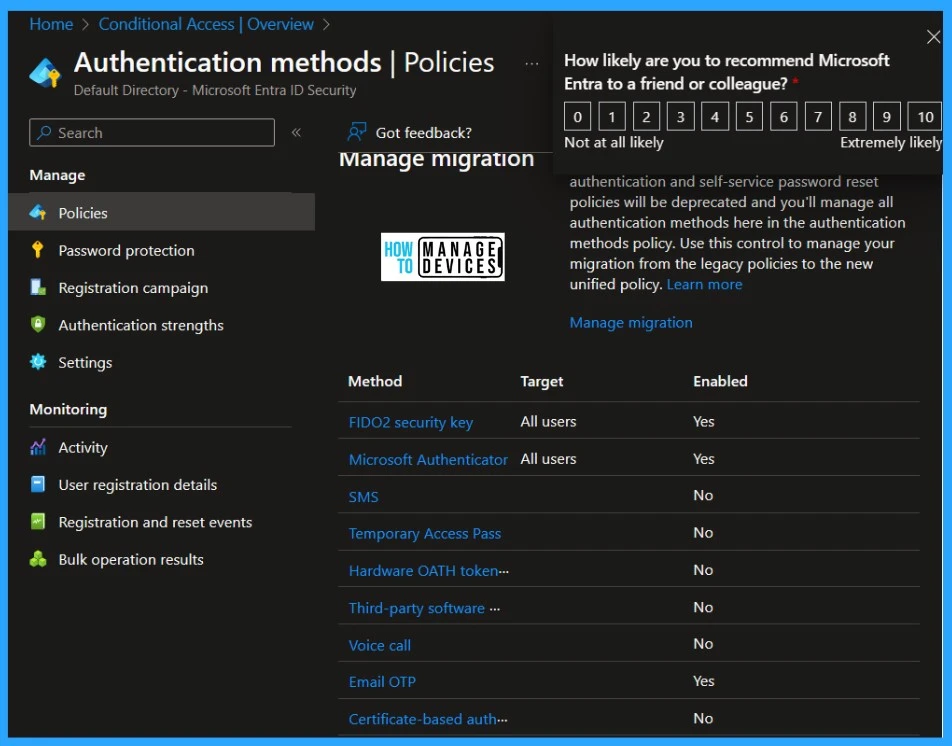
FIDO2 and Certificate–based authentication are the safest choices. They’re good at protecting against fake login attempts. You can also adjust these methods to fit your needs. For example, with FIDO2, you can ask for evidence of a device’s authenticity or restrict it to specific keys.
Reference
How to secure Microsoft Entra ID tenant
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Krishna. R is a computer enthusiast. She loves writing about Windows 11 and Intune-related technologies and sharing her knowledge, quick tips, and tricks about Windows 11 or 10 with the community.
