Let’s discuss External Collaboration Settings in Entra ID. Microsoft Entra offers a range of security settings to help protect your organization from identity-related attacks. Microsoft Entra ID, previously known as Azure AD, is an identity and access management service that allows secure access to applications and resources across an organization’s network.
Nowadays, organizations frequently collaborate with external partners, vendors, and contractors. These collaborations require strong security to protect external collaboration securely, which is possible to manage in Entra. These settings are crucial for protecting organizational data while enabling productivity and flexibility.
The settings for working with people outside your organization in Microsoft Enterprise ID help you manage collaboration. These settings let you control who from outside your company can access your resources and how they can use them. It gives you control over how external users interact with your organization’s tools and data, ensuring security and proper management of resources.
External Collaboration settings are essential for companies to work together safely; these settings allow you to define which positions in your company have the authority to invite outside individuals for business-to-business collaboration.
- What is Microsoft Entra ID?
- Security Enhancement with Named Locations in Entra ID
- Enterprise Applications Security Settings in Entra ID
External Collaboration Settings in Entra ID
Cross-tenant access settings are usually okay by default. But it’s best not to automatically trust multi-factor Authentication (MFA) and foreign-compliant devices, or hybrid joined devices from other organizations. You can easily access the External collaboration settings through Microsoft Entra ID and follow the steps to do this
- Sign in to Microsoft Entra Admin Center
- Click on the External Identities
- Select Cross-tenant access settings
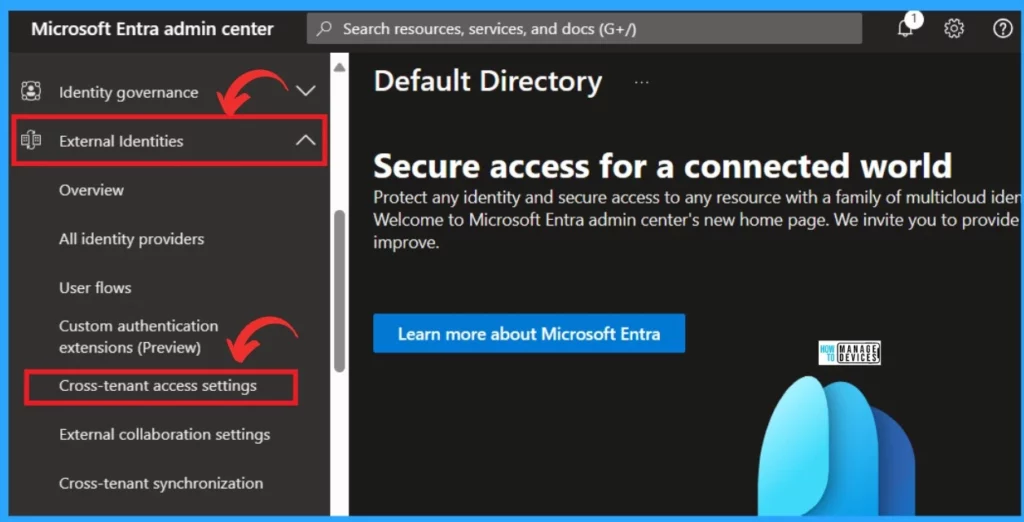
Upon selecting the “cross-tenant access setting,” you will be directed to the cross-tenant setting page. This page allows you to control collaboration with external Microsoft Enterprise tenants. Use these settings to manage how your organization interacts with other Enterprise tenants, ensuring smooth and secure collaboration across different organizations.
- Click on the Default Settings
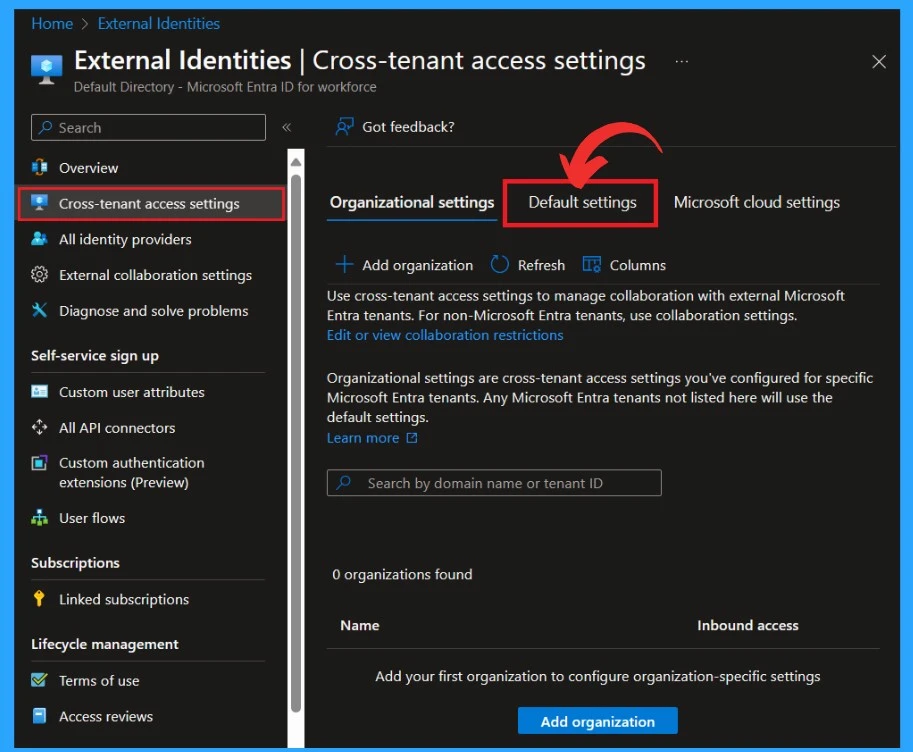
Default settings apply to all external Microsoft Entra tenants not listed on the organizational setting tab. They can be modified but not deleted. Default settings are divided into 3 categories.
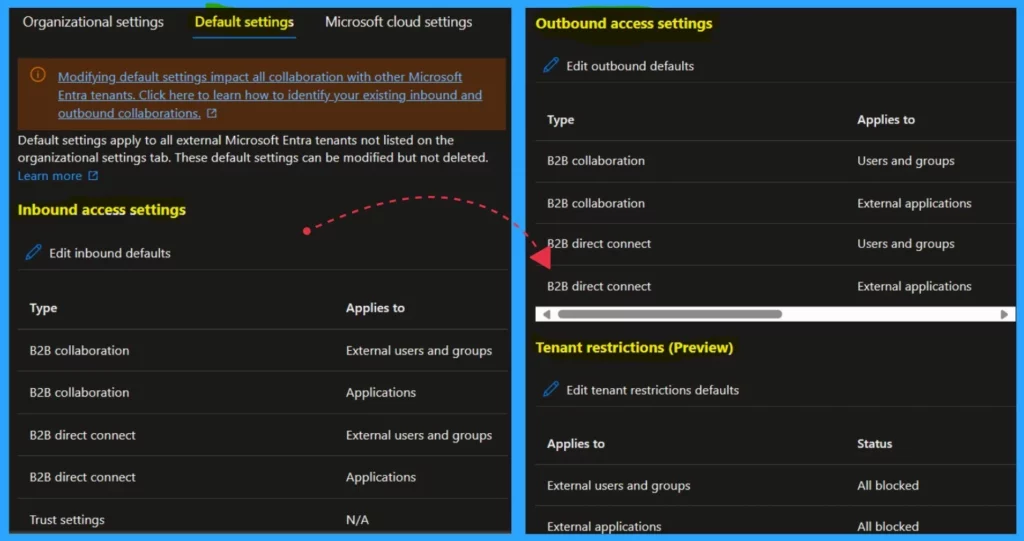
- Inbound access settings – These settings control the level of access that users from external organizations have to resources within your organization.
- Outbound access settings – Determine how your users can collaborate with external organizations
- Tenant Restrictions (Preview)– Its a part of the cross-tenant access settings that allow you to control access to SaaS applications based on the tenant
- Modernize MFA Authentication Policies in Entra ID
- List of Entra ID Ignite 2023 Sessions
- Free Entra Training Videos | Start Learning Entra ID Azure AD
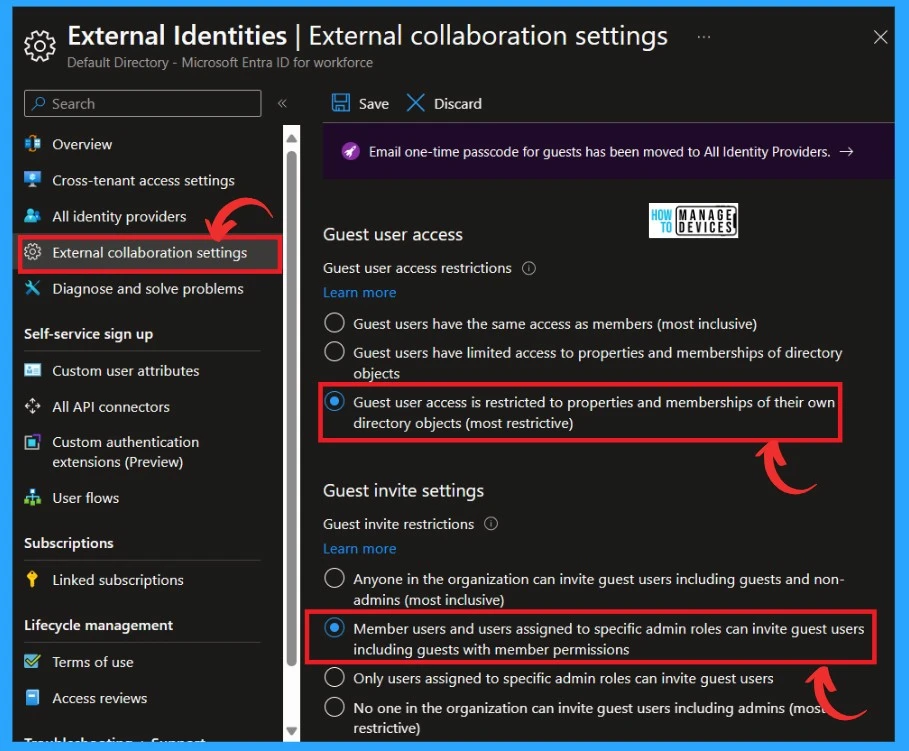
External collaboration settings in Microsoft Entra ID allow organizations to control how outside users can access internal resources. To enhance security, modify the Guest Invite Settings. The default setting permits all users, including guests, to send invitations.
- Under the guest user access restrictions, allow ”Guest user access to be restricted to the properties and membership on their own directory objects. ”
- Allow ”member users and users assigned to specific admin roles can invite guest users, including guests with member permission” under the Guest invite restrictions
| External collaboration settings | Info |
|---|---|
| Guest user access – Guest user access restrictions | This setting determines whether guests have full access to enumerate all users and group memberships (most inclusive), limited access to other users and memberships, or no access to other users and group memberships, including groups they are a member of (most restrictive). |
| Guest invite settings- Guest invite restrictions | This setting controls who can invite guests to your directory to collaborate on resources secured by your company, such as SharePoint sites or Azure resources. |
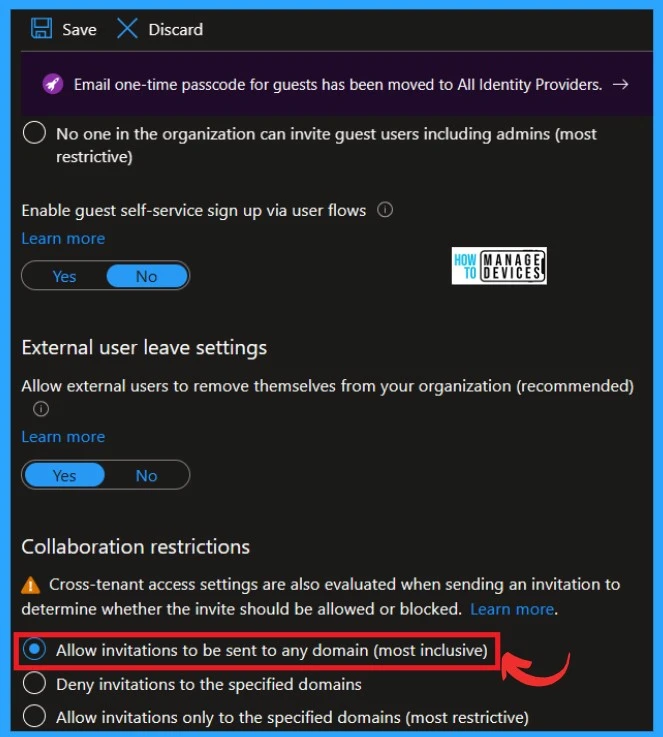
| Enable guest self-service sign-up via user flows | Yes, it means that you can enable self-service sign-up for guests via user flows associated with applications in your directory. No means that applications cannot be enabled for self-service sign-up by guests and require them to be invited to your directory. |
| Allow external users to remove themselves from your organization (recommended) | Yes means that the end user can leave the organization without approval from the admin. No means that the end user will be guided to review the privacy statement and/or contact the privacy contact for approval to leave. |
| Collaboration restrictions | Cross-tenant access settings are also evaluated when sending an invitation to determine whether the invite should be allowed or blocked. |
In collaboration restrictions, cross-tenant access settings are also evaluated when sending an invitation to determine whether the invite should allowed or blocked. I recommend a setting that only allows internal users to extend guest invitations.
- Allow the option ”invitation to be sent to any domain (Most inclusive) under the collaboration restrictions
Reference
How to secure Microsoft Entra ID tenant
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Krishna. R is a computer enthusiast. She loves writing about Windows 11 and Intune-related technologies and sharing her knowledge, quick tips, and tricks about Windows 11 or 10 with the community.
