Hey, let’s discuss about Sysmon Built into Windows for Easy Setup and Better Threat Detection. Windows 11 and Windows Server 2025 now include Sysmon as a built-in feature. This removes the need to download or install it manually. It provides fast threat visibility with the same strong monitoring as before. This update helps reduce work and improve
Built-in Sysmon sends events directly to Windows event logs and works well with SIEM tools. You can still use custom configuration files to control which events you want to collect. Monthly Windows updates keep Sysmon repaired and updated automatically. This lowers the risk of outdated versions and saves time.
ysmon helps detect suspicious processes, network connections, file activity, and credential theft attempts. Key events like Process Creation and Network Connection help reveal attack behavior early. These signals help uncover hidden malware or unusual traffic. Security teams can use them to investigate incidents more quickly.
You can enable Sysmon through Windows Features and a simple command: sysmon -i. After enabling, all events appear in the Sysmon/Operational event log. These logs can be used directly with SIEMs or analysis tools. This built-in capability provides strong security data with less effort.
Table of Contents
Sysmon Built into Windows for Easy Setup and Better Threat Detection
| Configuration Type | Description |
|---|---|
| Config.xml | The default configuration. Includes events considered “interesting” and excludes very noise ones. |
| Exclude Only | Logs everything except for a defined list of noisy exclusion. |
| Super Verbose/Research | Logs all possible events. No filtering or exclusions applied. |
| MDE Augmentation | Designed to run alonsgside Microsoft Defender for Endpoint(MDE) |
The screen shifts to Visual Studio Code, displaying the cloned repository’s directory structure. The view emphasizes the modularity, showing folders named after Sysmon events (e.g ProcessCreate) containing multiple, smaller XML rule files.

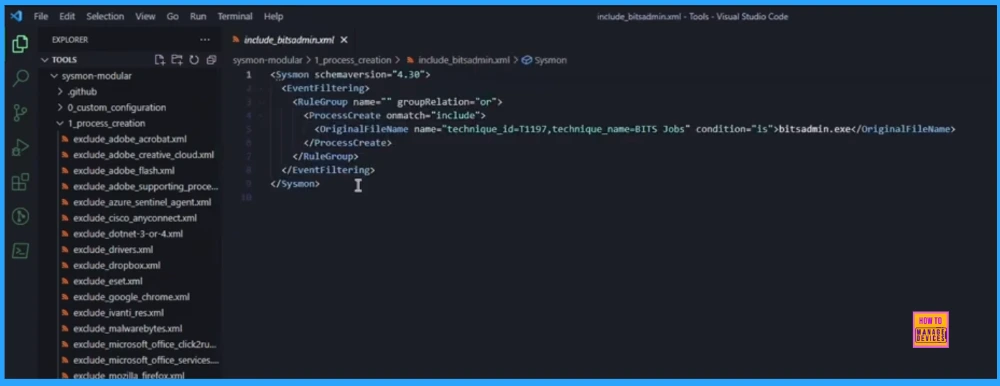
A specific XML file is opened (ProcessCreate\Include_BitsAdmin.xml) to show an include rule. The key visual element is the XML tag that explicitly references the MITRE ATT&CK Technique ID (T1197) used to tag the event.
Full Sysmon XML configuration file for the custom rule they just added (windsock). The visual confirms that the new rule has been correctly incorporated into the large configuration file.

The final custom configuration is successfully updated in the command prompt. The view then shifts to the Windows Event Viewer, which immediately shows a surge of new, detailed Sysmon logs (Image Loads, Process Access events) proving the new verbose rules are active.

Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


