Today we are discussing how to Configure App Data Sharing using SharedLocal Folder in Windows 10 with Intune Policy. In this post we are discussing Microsoft Store app policy deployment called shared app user data.
The policy that controls whether a Windows app can share data between users is important for managing shared and personal content on a device. It decides if the app can use the SharedLocal folder, which is available through the Windows.Storage API.
When this policy is enabled, the app can read and write data in this shared folder, allowing different users on the same device to access the same app data. This helps users work together and maintain balance across accounts. Enabling this policy is especially useful in places where multiple people use the same device, like in offices, schools.
If you disable this policy, this sharing is completely blocked. Each user on the same device can only access their own copy of the app’s data, and nothing is shared through the SharedLocal folder. So in this post lets look how this policy to be deployed.
Table of Contents
What Happens When the Policy to Share App Data is Enabled?
If you enable this policy, a Windows app can share app data with other instances of that app. Data is shared through the Shared Local folder. This folder is available through the Windows Storage API.
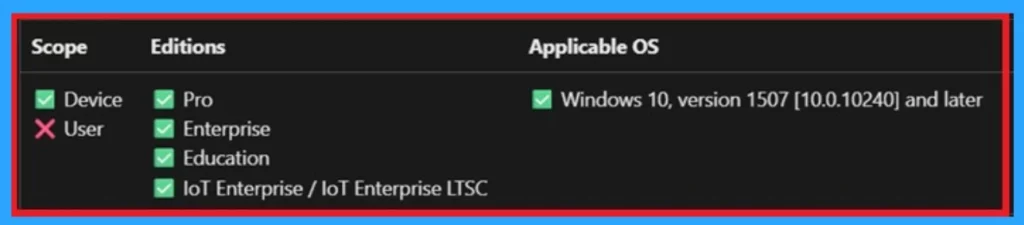
Allow or Block Shared User App Data – Windows CSP Details
Above we discuss a lot of things about delivery of Shared User App Data policy. Now, let’s look into a CSP details. Before deploying this policy, it is essential to know the CSP (Configuration Service Provider) details, and this is very important to know for a admins.
- Easy Guide to Deploy Azure VPN Client Microsoft Store App using Intune
- How to Allow or Block Option to Show Network using Intune Policy
- How to Pause Intune Config Refresh Feature on Windows Device using Microsoft Graph API
OMA-URI for Configuring the Policy
You can easily enable or disable the Shared User App Data on Windows devices using Microsoft Intune or configure a custom OMA-URI setting. Below is a step-by-step guide to help you set this up.
- Sign in to Microsoft Intune
- Go to Devices > Configuration
- Click Create and then new policy
- Choose the platform as Windows 10 and later
- For Profile type, select Templates and then choose Custom
- Provide a Name – e.g. “Shared User App Data.”
- Add a Description if needed
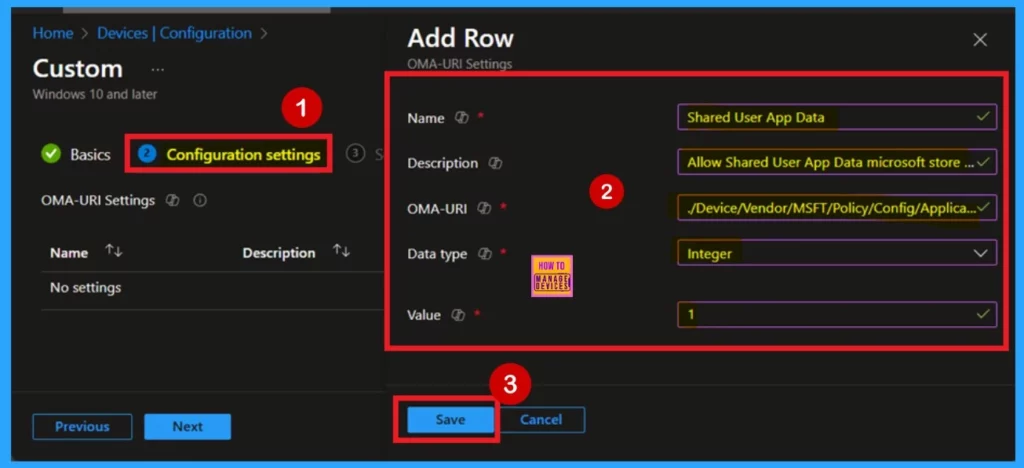
- Click on + Add under OMA-URI Settings to configure the specific setting.
- To Configure the OMA-URI Setting, do the following
- Enter a name for this setting, such as Shared User App Data.
- Briefly describe the setting, e.g., “Allow Shared User App Data microsoft store app.”
- Enter the following OMA-URI path
- ./Device/Vendor/MSFT/Policy/Config/ApplicationManagement/AllowSharedUserAppData
- Set the Data type to Integer.
- Enter the value
- 1 to enable the administrator account.
- 0 to disable the administrator account.
- After entering the above details, click Save.
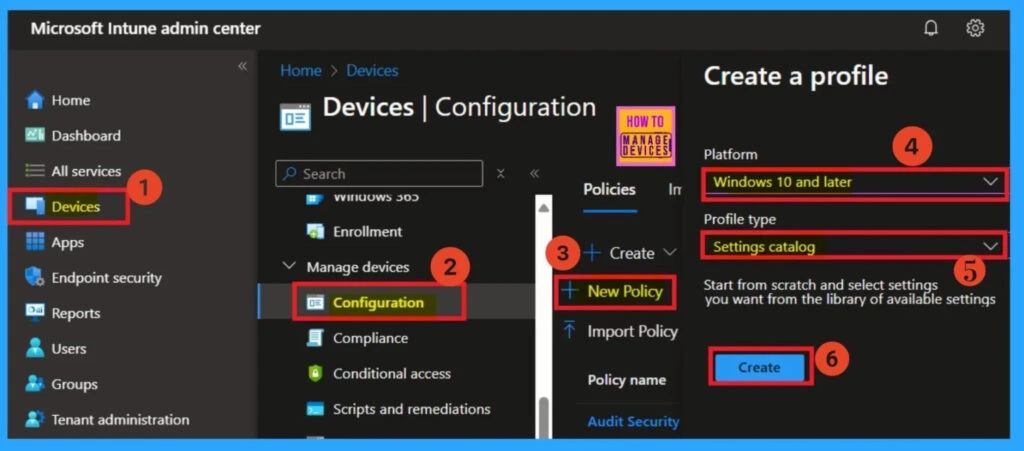
Create a Profile
Creating a profile is the first step you need to complete in the Intune portal. Start by signing in to the Microsoft Intune Admin Center. Then, navigate to Devices > Configuration profiles, and click on + New policy. In the “Create a profile” window, select Windows 10 and later as the platform and choose Settings catalog as the profile type.
- Finally, click on the Create button to proceed.
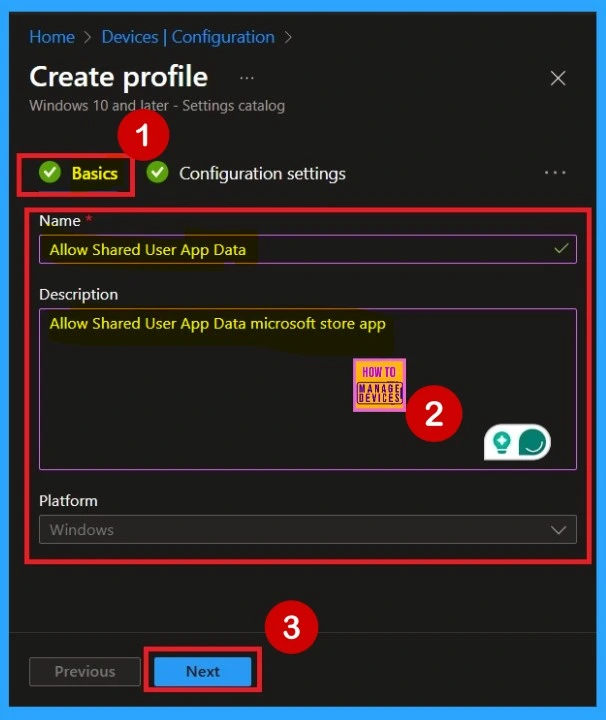
Basics
Basic details are the next step when you start deploying a policy. First, you need to enter the basic information for the policy. This includes providing a name for the policy and an optional description, which can help you understand the purpose of the policy later. The platform is set to Windows by default, so you only need to focus on entering the policy name.
- I named the policy as : Allow Shared User App Data
- Description as : Allow Shared User App Data microsoft store app
- After entering these details, select Next to move forward in the setup process.
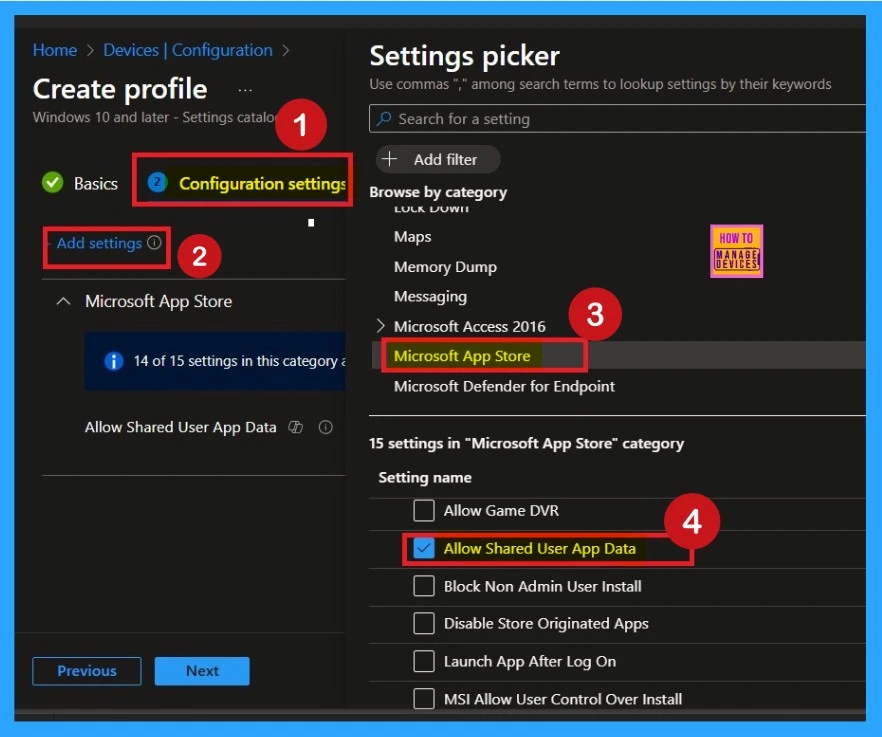
Configuration Settings – Intune Settings Picker
The next step is Configuration Settings click on the Add settings option to open the settings picker window. In the picker, select Microsoft App Store, which includes 15 available settings. From these, choose Allow shared user app data, then close the settings picker window.
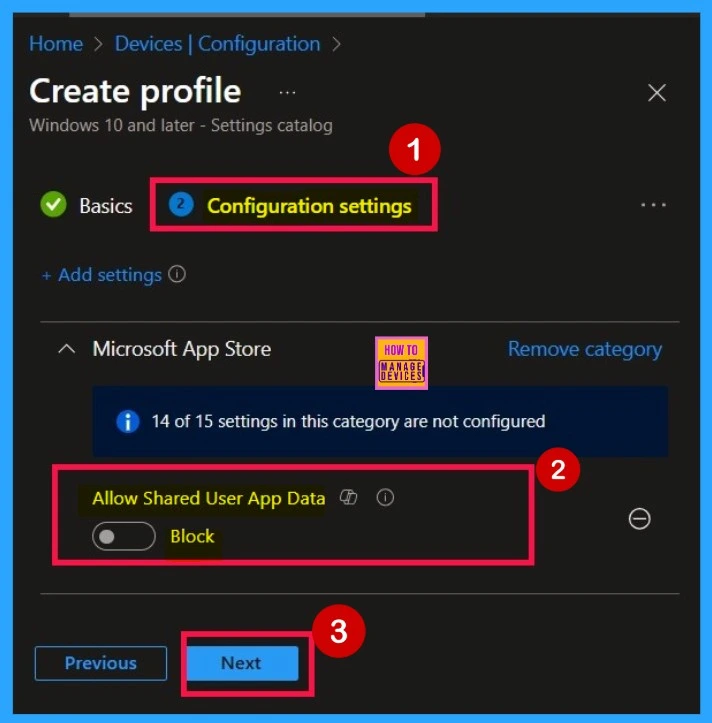
Disable the Policy
After closing the Settings Picker, you will return to the Configuration settings page. Here, you can see that the selected policy has now appeared. By default, it is set to “Disabled“. If you want to proceed with the policy in its disabled mode, you can simply click Next to continue.
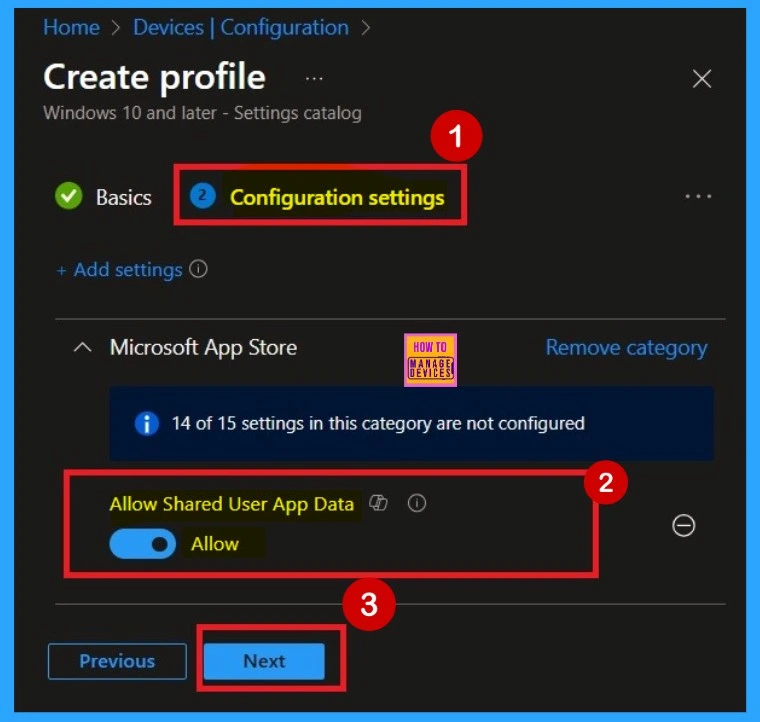
Enable the Policy
On the Configuration settings page, you’ll see the policy name. Next to it, there is a toggle button. To enable the policy, simply click and drag the toggle to the right. It will then turn blue and be labelled “Enabled“, indicating that the policy is now Enabled.
- After enabling it, click Next to continue.
- In this guide, I Continue with the Enable mode of the policy.
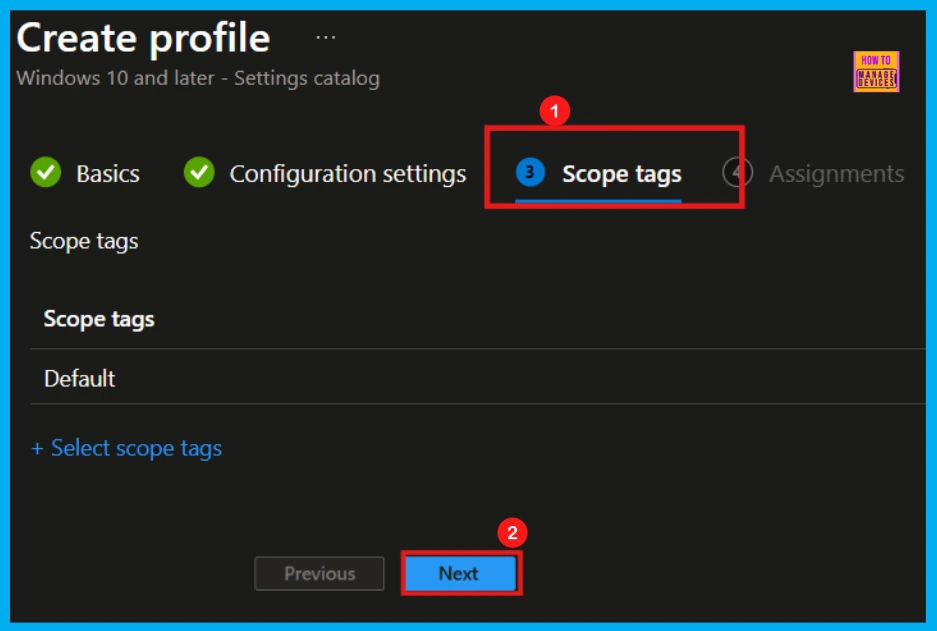
Scope Tags
Now, you are on the Scope tags page. Scope tags can be important in certain cases for policy deployment. In this tutorial, I chose to skip this section. However, if you want to add a scope tag to the policy, you can select the “Add scope tag” option. Here, I’m skipping this step, so I click Next to continue.
Assignments
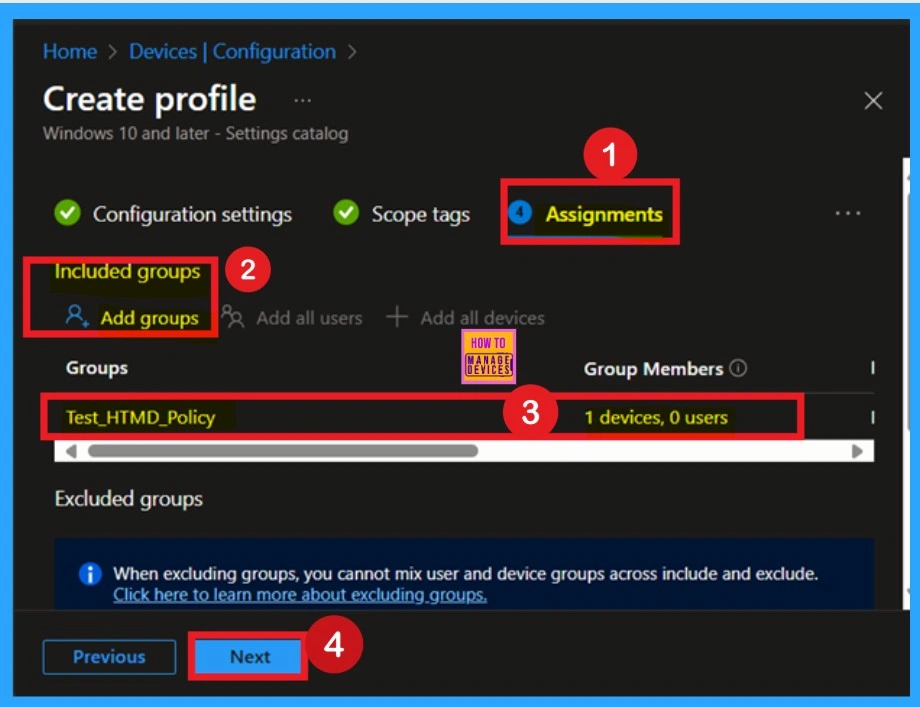
When deploying a policy, the main aim is to specify which organizational group the policy should be applied to. This is done in the Assignments section, which allows administrators to deploy the policy to a specific group. For that click on the “Add groups” under the Include section.
Once you click on that, you’ll see a list of available groups. Here, I selected our Test_ HTMD_ Policy group. After selecting the group, the assignment is complete, and you can click Next to proceed. Always remember you can add 1 or more groups for the policy.
Review + Create
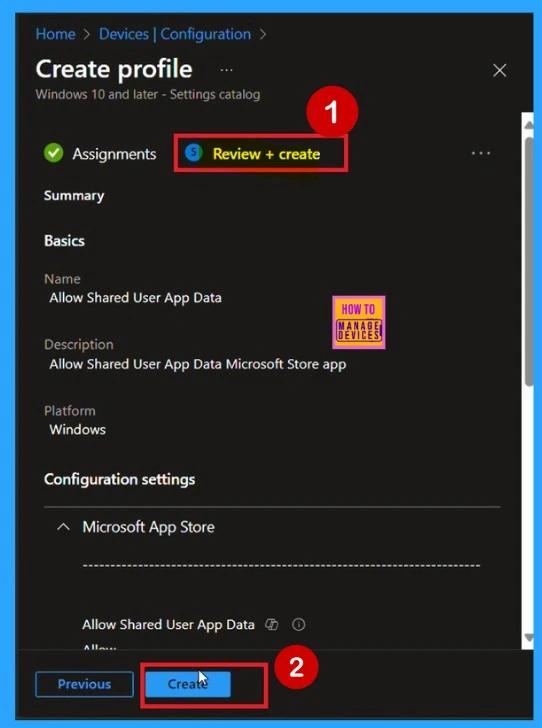
The final step of policy creation is the Review + Create section. In this step, you don’t need to make any changes. You can review a summary of the deployment you configuring. This includes the basic details, configuration settings, assignment details, and more. If you need to make any changes, you can easily go back to the previous tabs and edit them. Once everything looks correct, click on Create.
- You will then receive a notification confirming that the policy has been created successfully.
Monitoring Status
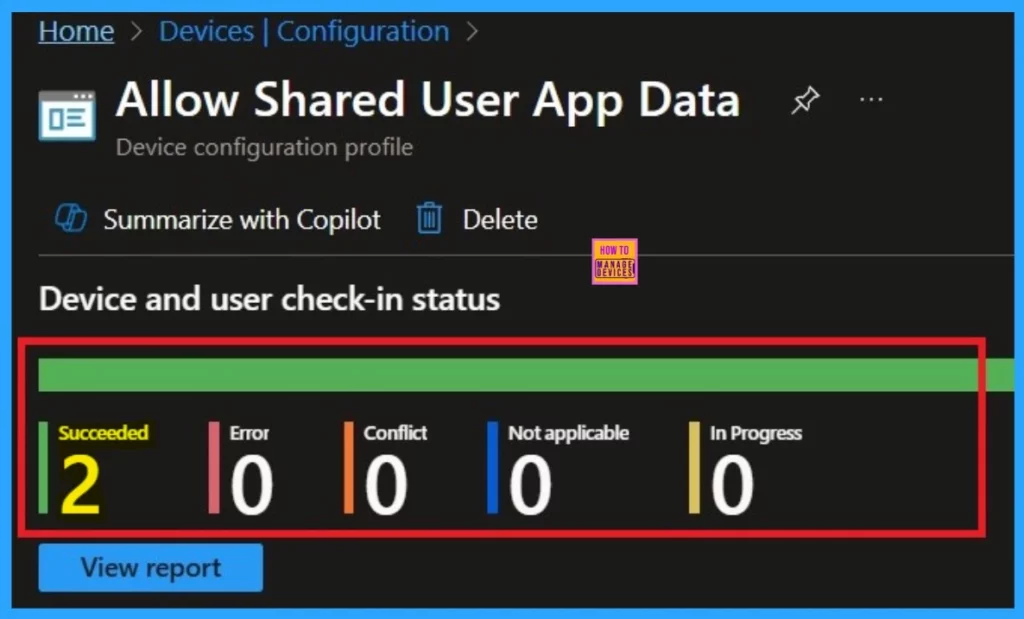
You can verify the policy is succeeded or not through monitoring status. Always remember that policy deployment may take up to 8-hour waiting period. If you’ve synced the policy in through the Company Portal, you can easily check the deployment status.
To do this, go to Devices > Configuration and in the list of configuration policies, search for the name you give to your policy. Once you find it, click on it to view the device and user check-in status.
- Here, you can see the screenshot below to see whether the policy has been successfully not.
- It shows “Succeeded: 2” It indicates that the policy is deployed successfully.
Client- Side verification
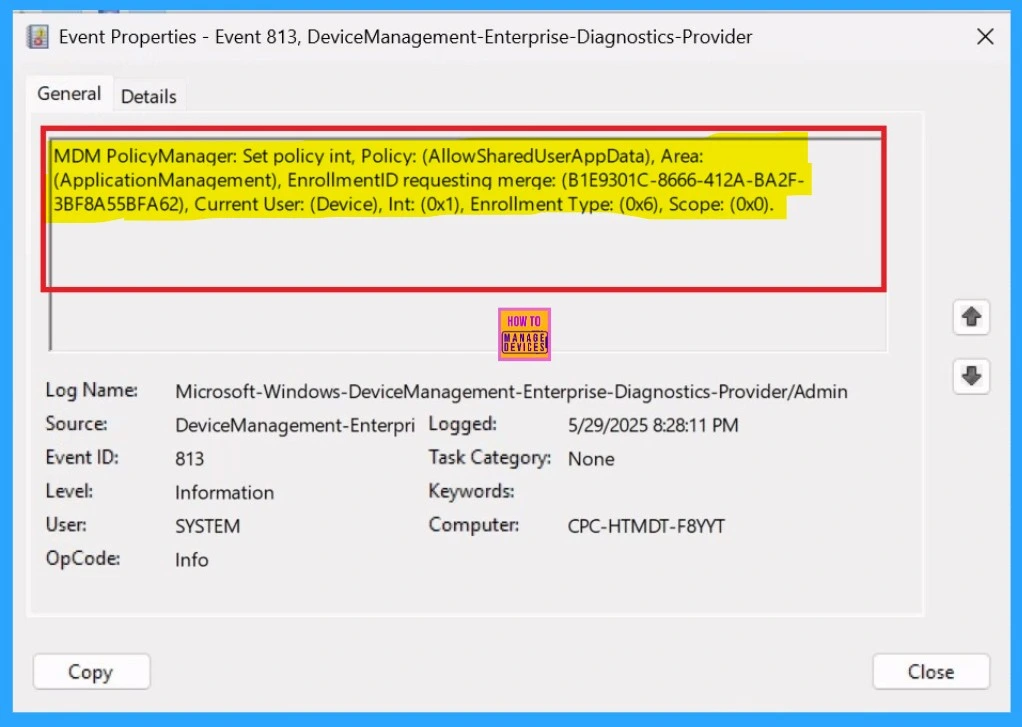
The next step is to verify the policy deployment using Event Viewer. Open Event Viewer and look for Event IDs, typically 813 or 814. Navigate to through the below path:
Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin.
This section displays a list of policy-related events. Since it can be challenging to identify which Event ID contains the specific policy information, use the Filter Current Log option in the right pane to show the results. In this case, the policy details were found under Event ID 813.
| Policy Details |
|---|
| MDM PolicyManager: Set policy int, Policy: (AllowSharedUserAppData), Area: (ApplicationManagement), EnrollmentID requesting merge: (B1E9301C-8666-412A-BA2F- 3BF8A55BFA62), Current User: (Device), Int: (0x1), Enrollment Type: (0x6), Scope: (0x0). |
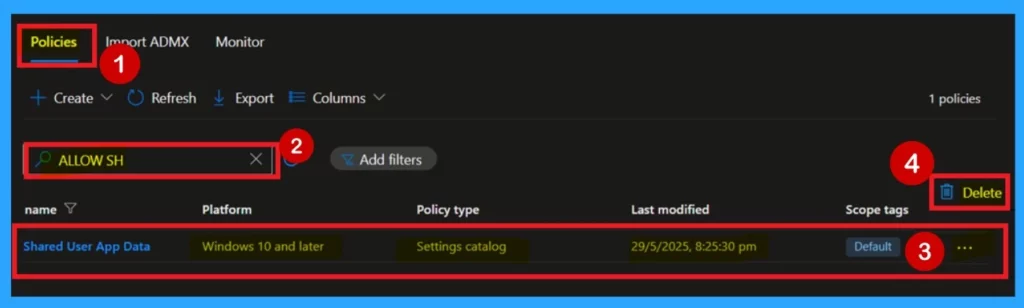
How to Delete App Data Sharing using SharedLocal Folder Policy
First, sign in to the Microsoft Intune Admin Center. Then, navigate to Devices > Configuration profiles, and select the policy you created or the one you want to delete. In the policy details page, you will see a 3-dot menu. Click on the 3 dots, and you will see a Delete option. Click on it to remove the policy. You can also refer to the screenshot below for better understanding.
For more information, you can refer to our previous post – How to Delete Allow Clipboard History Policy in Intune Step by Step Guide.
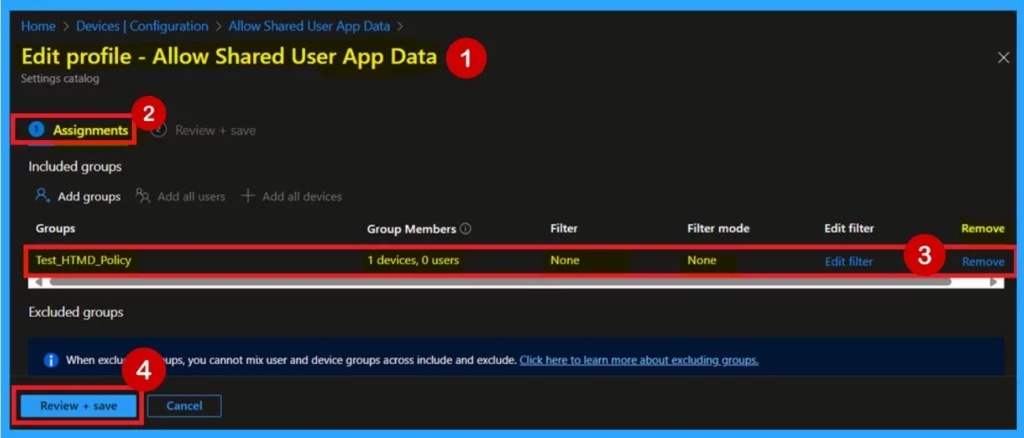
Know How to Remove Assigned Group
You can Remove the any groups from a policy very easily. To do this, open the policy from the Configuration tab and click on the Edit button on the Assignment tab. Click on the Remove button on this section to remove the policy.
For detailed information, you can refer to our previous post – Learn How to Delete or Remove App Assignment from Intune using by Step-by-Step Guide.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


