Let’s find out the Best Way to Deploy Powershell Script using Intune. First, we can use Intune to upload the PowerShell scripts and then run the scripts on Windows 10 devices.
Microsoft Intune management extension enhances Windows device management, making it easy to move to modern management. This feature applies to Windows 10 and later versions (excluding Windows 10 Home).
The Intune PowerShell script deployment is done using the Intune management extension agent, which is an additional agent automatically deployed to Intune-managed devices.
Note: If you assign the PowerShell script or Win32 app to the users or devices as part of the prerequisites, the Intune Management Extension will install automatically in the system.
- If you assign the PowerShell scripts to the user context and the user has admin rights, the PowerShell script will run with administrator privileges by default.
- The PowerShell script will run for every new user who enters a shared device.
- PowerShell script can be executed without user login if the script is assigned to a device.
- PowerShell script will be executed first, and then the Win32 app will run.
- The Intune management extension agent will check with Intune every hour to see if any changes are made to the script or if a new script is assigned. This process will also run on the machine after every reboot.
- PowerShell scripts will time out after 30 minutes.
Prerequisites to Deploy PowerShell Script using Intune
Below are the prerequisites required to install the Intune management extension. One of the prerequisites must be met to run the PowerShell script or Win32 app.
- The machine must run Windows 10 version 1607 or later. If devices are enrolled using bulk auto-enrollment, they must run Windows 10 version 1709 or later.
- Devices must be joined with Azure Active Directory, including Hybrid Azure AD.
- Devices must be registered with Azure Active Directory.
- Devices must be enrolled into Intune.
- Co-managed devices are also supported.
Deploy PowerShell Script Using Intune (MEM)
The following steps will help you upload the PowerShell to Intune (MEM portal).
- Sign in to the Microsoft Intune Admin or Endpoint.microsoft.com
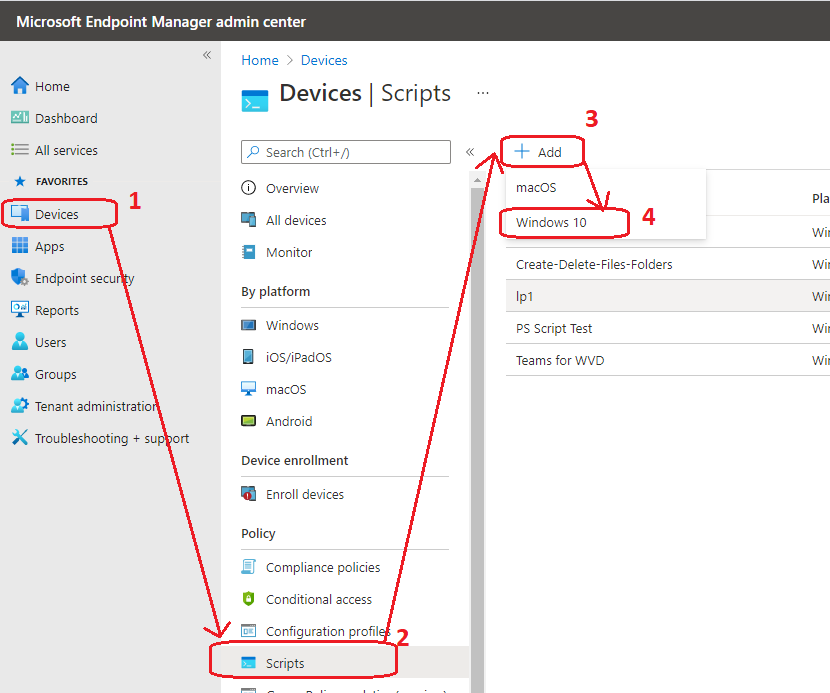
- Select Devices > Scripts.
- Click on Add > Select Windows 10.
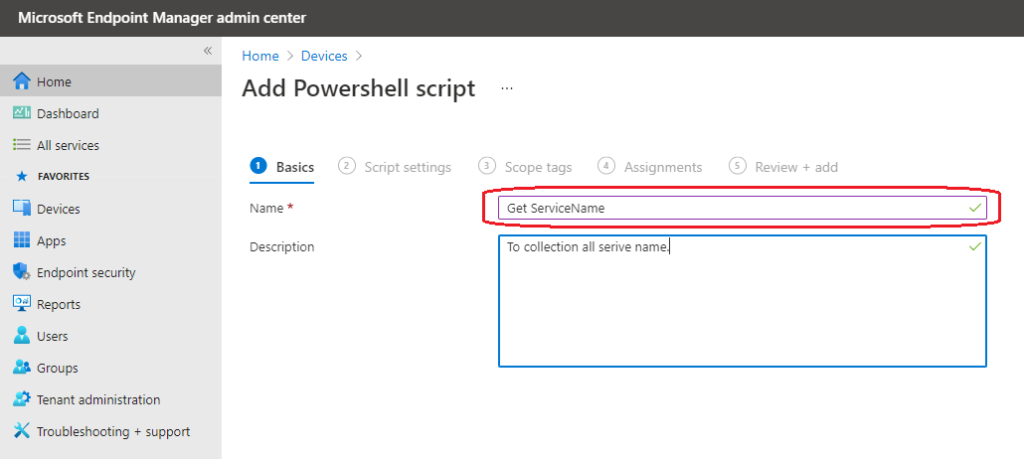
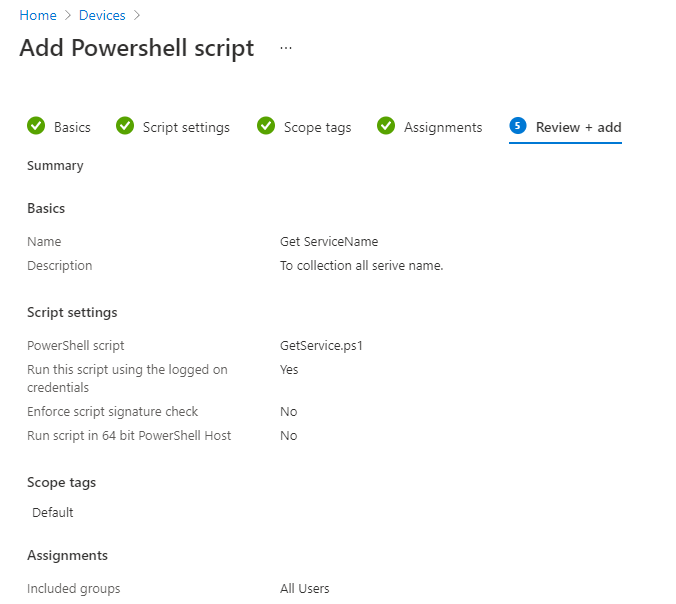
In Basics, provide the script’s name, and the Description is optional > Click Next.
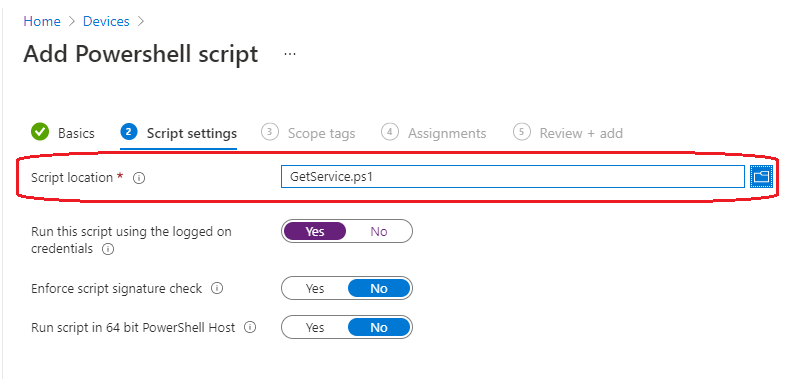
In Script Settings, enter the information below according to the requirement and click Next. Then, follow the steps to upload PowerShell.
- Script Location: Browse the PowerShell script where you placed it. The script must be less than 200 KB.
- Run the script using the logged-on credentials: Select Yes to run the script on the user credential. Otherwise, select No (default); it will run in a system context. The administrator must decide on this setting according to the requirements.
- Enforce script signature check: Select Yes if the script is signed by a trusted publisher; otherwise, select No (default) if no requirement exists.
- Run the script in a 64-bit PowerShell host: Select Yes to run the script in a 64-bit PowerShell host on a 64-bit client. Otherwise, select No (default) to run the script in a 32-bit PowerShell host.
- Select Scope tags; this is optional. According to the requirements, select an existing scope tag from a list you created earlier. Then click Next when you’re ready.
Deployment Setting – Assignment Details
Now, we are to Deploy a PowerShell Script using Intune. You need to decide whether this PS script should be deployed to the Azure AD User Group or Device Group.
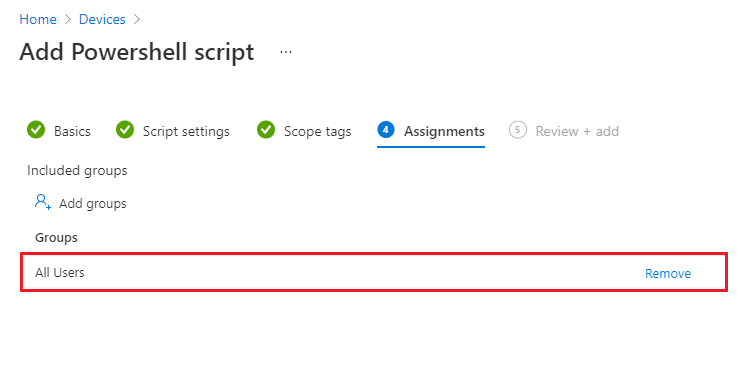
- Select Assignments > Select Included groups > Click Add groups. Select the appropriate group you want to deploy and click Next. You can also select multiple groups.
In Review + Add, you will see the settings you have configured. Select Add to save the script, and then the policy will be deployed to the assigned groups.
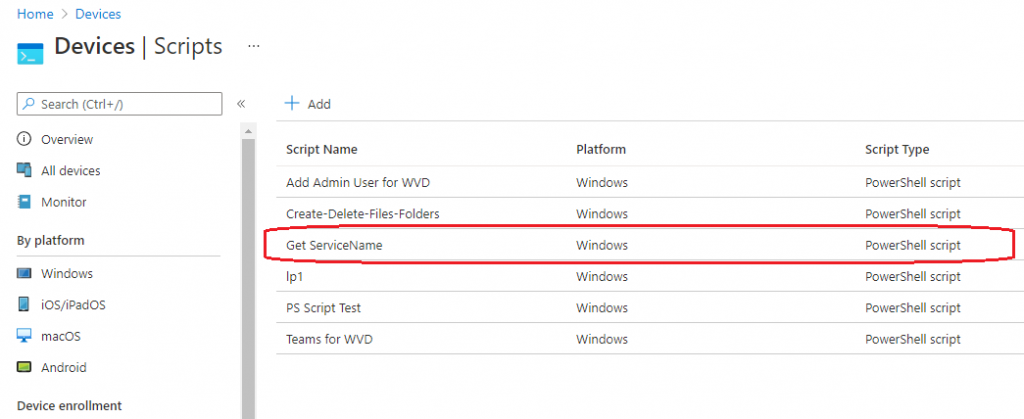
You can see the script in the Devices > Scripts section.
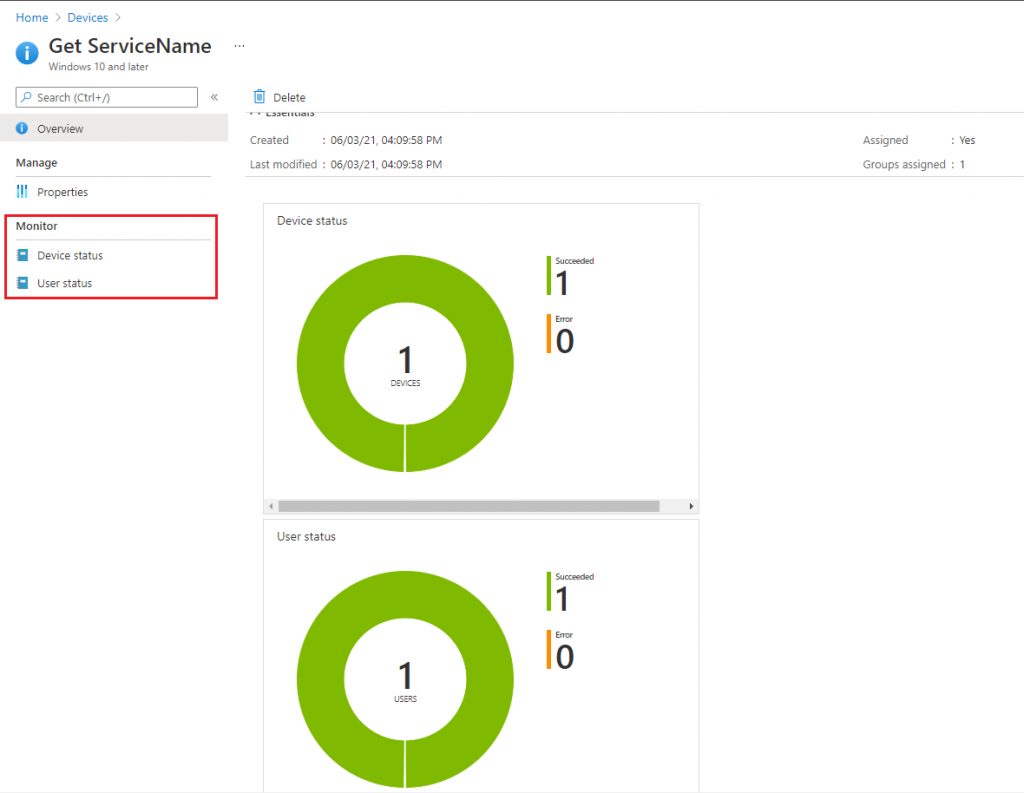
How to Monitor the Run Status in the Intune Portal
Let’s see how to monitor the run status of the PowerShell script. You can monitor the run status of the PowerShell scripts for users and devices in the Intune portal.
- Select the script you created under Devices > Scripts. Then, choose Monitor and see the reports below.
- Device Status
- User Status
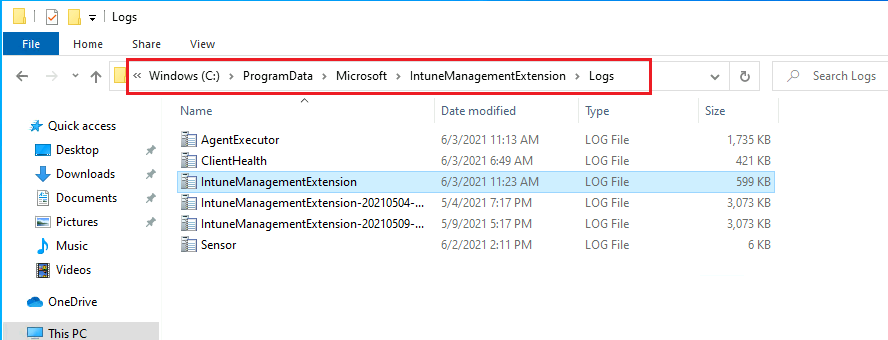
How to check Intune Management Extension Logs
Intune Management Extension agent logs will be available on client machines under this location: C:\ProgramData\Microsoft\IntuneManagementExtension\Logs.
For more details on troubleshooting, you can refer to this Intune Management Extension Deep Dive – Win32 App Deployment Troubleshooting Help Guide.
Resources
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.

Anoop,
I want to be specific, whether this powershell script should be applied to devices or users? For example changing the admin account password on a local machine what would be the best option (User Group or Device Group)?
Tom,
When you’re considering where to apply a PowerShell script, specifically one that modifies local machine settings such as changing the admin account password, you should target the device itself rather than the user.
Here’s why:
Scope of Impact:
Changing a local machine’s admin password is a device-specific operation. The password change impacts the machine, not the user’s profile or account in Azure AD or on-premises AD. Hence, applying this at a device level ensures that the change affects the intended target: the machine.
Security Consideration:
Applying a script that changes local admin passwords to a user group can inadvertently impact machines the user logs into if they log into multiple devices. This may not be the desired effect. Targeting the device directly ensures precision.
Principle of Least Privilege:
The operation pertains to device configuration. It’s a best practice to limit the scope of scripts to the smallest necessary target. If the intent is to change a setting on a device, then target the device group.
I need help as the GUI is changed for “scripts” option now. On the basis of Tenable report, I want to push a powershell script to the affected Windows 11 devices to uninstall the vulnerable MS store apps such as Paint 3D, VP9, HEIF etc. I know that we can find the installed version with the command Get-AppxPackage -AllUsers *paint*
Similarly we can find the the installed version for HEIF with the command Get-AppxPackage -AllUsers *HEIF*
Sometimes the store apps doesn’t get uninstalled easily with generic commands because those are installed in user context. So we use the below 2 commands to uninstall it properly from all user profiles in 1 go.
Add-AppxPackage “C:\Program Files\WindowsApps\Microsoft.HEIFImageExtension_1.0.63001.0_x64__8wekyb3d8bbwe\AppxManifest.xml” -Register -disabledevelopmentmode
Get-AppxPackage -PackageTypeFilter Main, Bundle, Resource -AllUsers| Where-Object {$_.PackageFullName -like “*HEIF*”} | Remove-AppxPackage -AllUsers
How can I write these things in 2 parts now? I see there are “Detection script file” and “Remediation script file” in Intune -> Devices -> Scripts and remediations. My requirement is to append the vulnerable MS store apps in powershell script as and when I get it in tenable report every month so day by day the script will be growing as vulnerable applications with older versions will be getting added. I believe I can write the last 2 commands in a powershell script and then browse that file under “Remediation script file”.
What to be written in “Detection script file”?
What to be written in “Remediation script file” if my above understanding is wrong?