Let’s learn how to create a custom role to read BitLocker Keys for managed devices. BitLocker Recovery Key Reader roles have required to help ensure that only an authorized person can unlock your Windows PC and restore access to your encrypted data.
BitLocker likely ensured a recovery key was safely backed up before activating protection. There are several places that your recovery key may be, depending on the choice that was made when activating BitLocker:
BitLocker is a built-in Windows data protection feature capable of encrypting entire hard drives, including both system and data drives. BitLocker pre-provisioning can drastically reduce the time required to provision new PCs with BitLocker enabled.
Microsoft also added support to hide recovery keys from end users. This helps improve the devices’ security poster and prevents attackers from getting Bitlocker encryption keys from Windows devices.
This new feature restricting access to the BitLocker Recovery Key allows users to choose whether they can view their BitLocker recovery key. At this point, many organizations don’t have the option to disable this feature.
- Block Hide BitLocker Recovery Key From Users Using MS Graph And PowerShell
- Intune Bitlocker Drive Encryption A Deeper Dive To Explore
Create Custom BitLocker Recovery Key Reader Role
You can create a custom BitLocker Recovery Key Reader role that includes any permissions required for a specific job function. After creating a custom role, you can assign it to any users that need those permissions. Here’s how you can create Bitlocker Keys RBAC Roles in Azure AD:
To create, edit, or assign roles, your account must have Global Administrator or Privileged Role Administrator permissions in Azure AD.
- Sign in to the Azure portal or Azure AD admin center.
- Select Azure Active Directory > Roles and administrators.
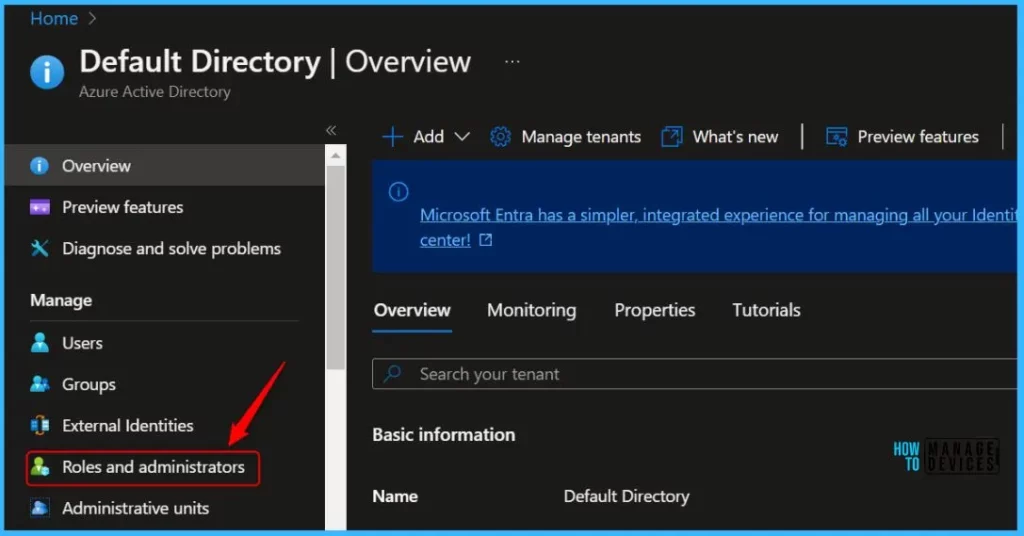
In the Roles and administrators, click on the New custom role.
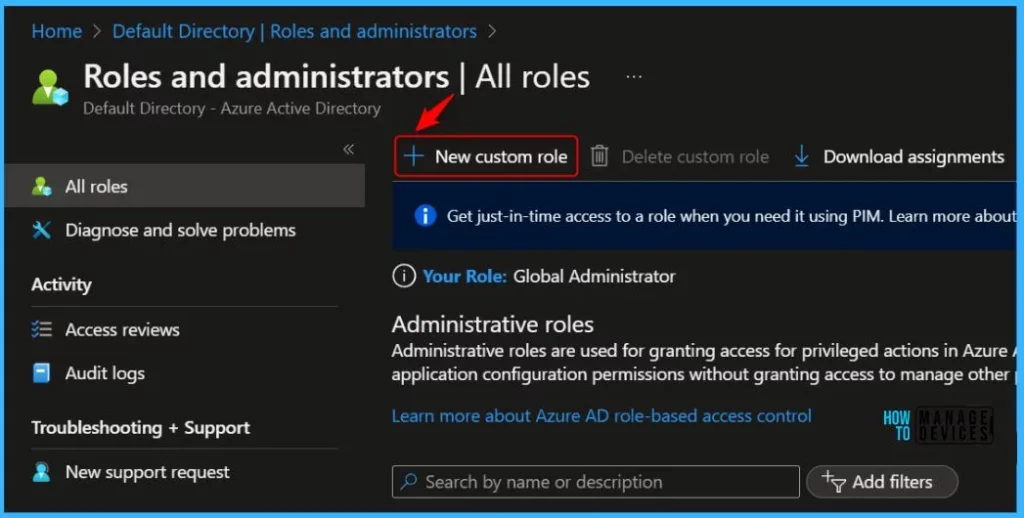
On the Basics page, enter a name for the Bitlocker Recovery Key Reader role (For Example, Bitlocker Recovery Key Reader) and a description for the new role, then choose Next.
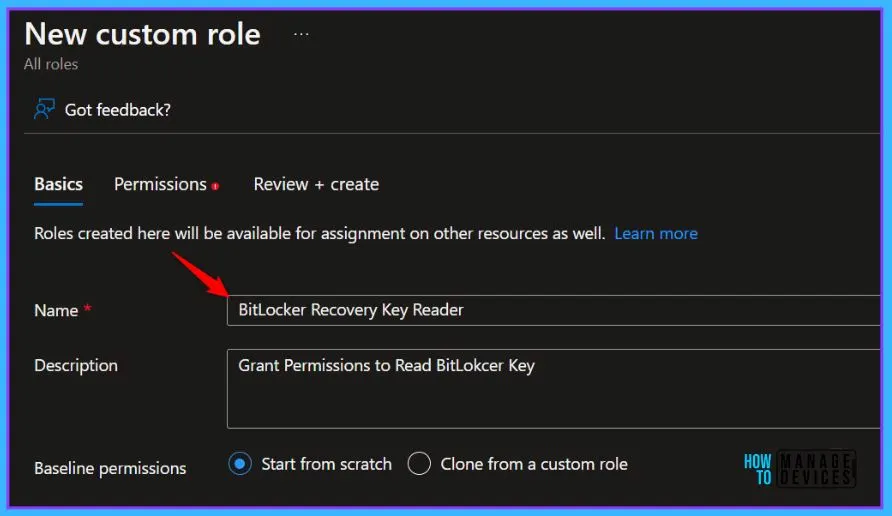
On the Permissions page, choose the permissions you want to use with this role. To add BitLocker keys read permission, search with the keyword “Bitlocker Key” and select microsoft.directory/bitlockerKeys/key/read permission will appear. Select the permission.
| Permission | Description |
|---|---|
| microsoft.directory/bitlockerKeys/key/read | Read bitlocker metadata and key on devices |
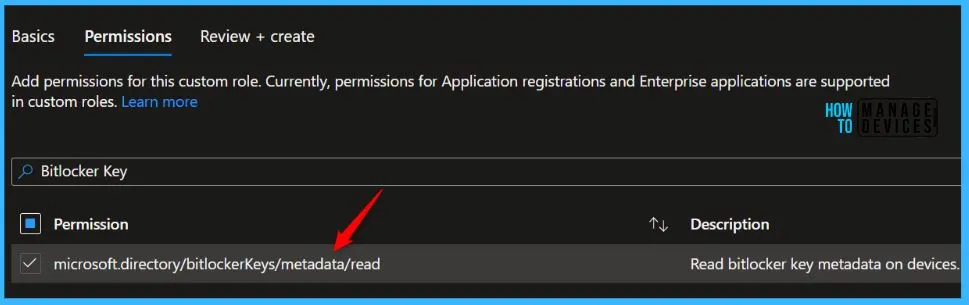
On Review + create, review assigned roles. Click on Create.
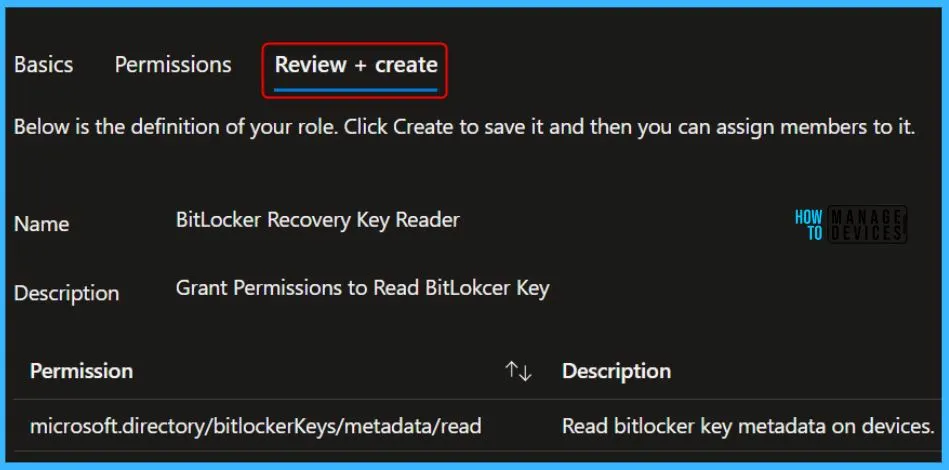
A notification will appear automatically in the top right-hand corner with a message. Here you can see, Successfully created ‘BitLocker Recovery Key Reader’ custom role. Click the Refresh button at the top to quickly see the roles. You can see the Custom BitLocker Recovery Key Reader role created.
What minimum role-based access control (RBAC) rights are required to access the Intune console recovery key? To access the recovery keys, an administrator must be granted Helpdesk Administrator permissions.
Assign Bitlocker Recovery Key Reader Role to Azure AD Group
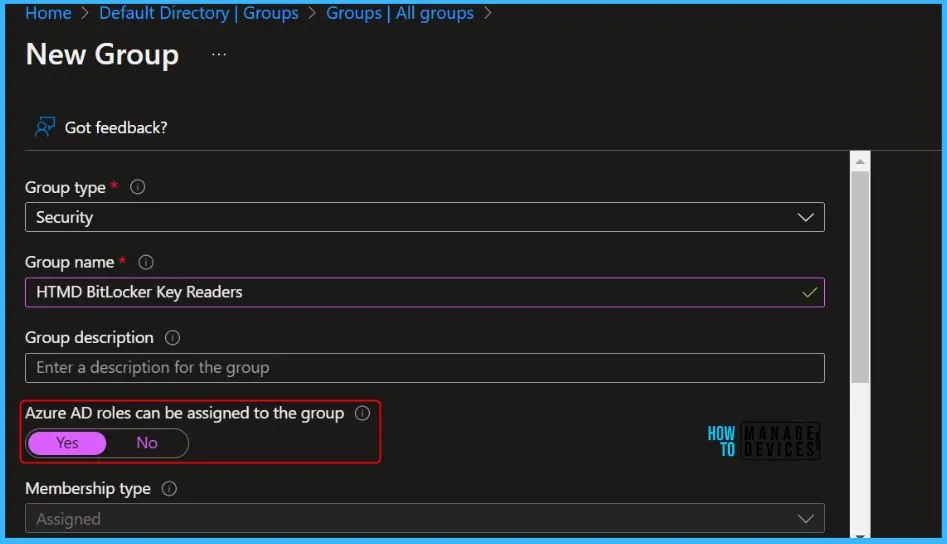
Only Global Administrators and Privileged Role Administrators can create a role-assignable group. The membership type for role-assignable groups must be Assigned and can’t be an Azure AD dynamic group.
- In Azure AD, Select Groups, and Click New Group.
- Here you need to Enter a Name, Description (optional). Set Azure AD roles can be assigned to this group to Yes.
- Next, you can add members to the group
Click on the Roles and select the role (Bitlocker Recovery Key Reader Role) you want to assign. Click Create.
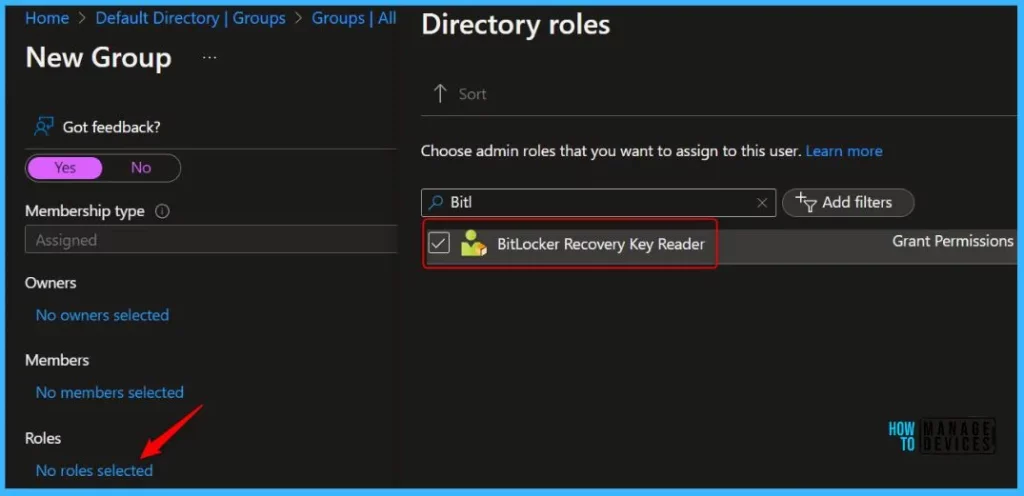
You can also later assign the roles to the group from the Roles and administrators tab. Once the role has been mapped to the groups or users.
🛎️You must activate the role assignment when performing privileged actions if you have been made eligible for an administrative role, More information can be found here Assign Azure AD Roles Using Privileged Identity Management PIM
Find BitLocker Recovery Key in Intune Portal
BitLocker recovery key has required to help ensure that only an authorized person can unlock your Windows PC and restore access to your encrypted data. How can we get my BitLocker recovery key? The BitLocker recovery depends on how Windows PC is set up; there are different ways to get your recovery key.
You can access the BitLocker recovery key of the device registered in Intune. Here’s how you can access the keys for the device. You can also access it directly from AzureAD.
- Sign in to the Microsoft Intune admin center https://endpoint.microsoft.com/.
- Choose Devices > All devices and select the device from the list. For Example, I selected the device CPC-jitesh53-DE.
Select Recovery Keys in the Monitor section to view the BitLocker recovery passwords.
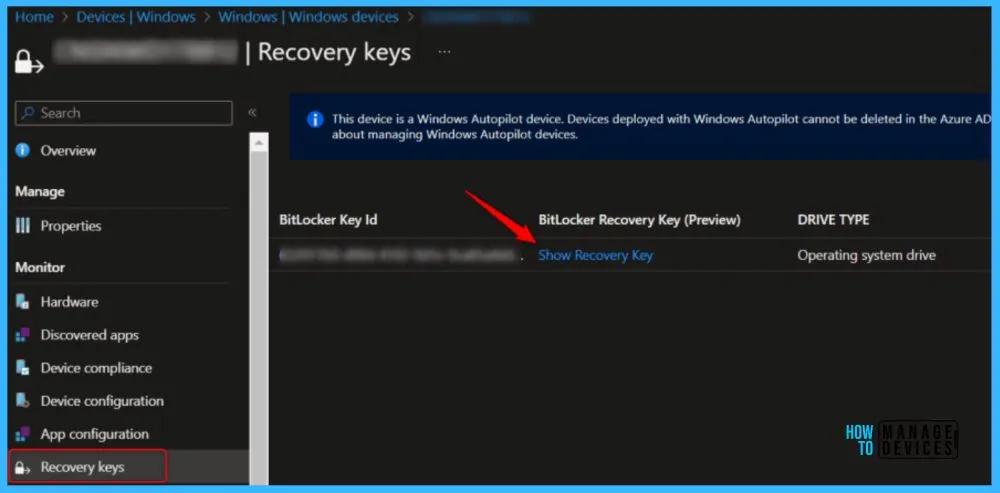
Select Show Recovery Key. If multiple entries exist, use the BITLOCKER KEY ID to select the correct BITLOCKER RECOVERY KEY.
Here’s how you can assign Azure AD Roles. The Azure AD PIM service also allows Privileged role administrators to make permanent admin role assignments, Assign Azure AD Roles Using Privileged Identity Management PIM
Author
About Author – Jitesh, Microsoft MVP, has over six years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus is Windows 10/11 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.

Facing an error after following above steps while seeing recovery keys in intune portal “you do not have access to view this bitlocker key”
You Suppose to activate the role, if assigned with PIM. Can you please validate the assigned role to you.
Hello Kumar.
I’ve an issue. Recovery Key are showing in Azure AD but Intune returns no results. What’s wrong ?
I know this is an old post. We are having a weird issue where the custom role worked on all devices prior to a certain time. Now users with the same custom role are not able to view new devices bitlocker recovery keys “You do not have access to view this bitlocker recovery key”.
Martin – where you able to get this sorted? About to open a premier ticket tomorrow – but identical problem. Hoping to maybe avoid the ticket if you already opened one…
Hi,
We are seeing the same thing, any update? Did you create a ticket? Did MS change anything and didnt say or we missed it?
Hey! Add microsoft.directory/auditLogs/allProperties/read and it will fix this issue that apparently broke in February 2024.
@John Doe: Is there any public doc about the additional required permission?
Is it possible to restrict users to view BitLocker recovery key only for specified group of devices?
I did all according to the guide and it works but user see all Bitlocker keys including our top managers devices. I want to restrict access to top managers devices