How to Create Azure AD Dynamic Device Groups for Windows BYOD CYOD Devices Microsoft Intune? In the previous post on how to Create Azure AD Dynamic Groups for Managing Devices using Intune, you might have seen the basic process for creating Azure AD dynamic user and device groups, along with explanations about the syntax of the queries/rules.
We will also experience performance issues with Azure AD dynamic groups when we don’t design our queries properly. This is similar to performance issues with dynamic collections with bad WQL queries, and SCCM admins are very familiar with this kind of performance issue.
This post will show how to create dynamic device groups for Windows devices with the “Device Ownership” attribute in Azure AD. This attribute is populated only when the devices are enrolled through MDM, and if I understand correctly, it is inhabited by Intune in this case.
If this attribute is not populated, you must ensure the device is correctly enrolled in Intune. Because some of these attributes are available only when the Intune portal is migrated to Azure, you may need to wait for your Intune migration to complete if you are still using the Intune Silverlight portal.
- Create AAD Dynamic Groups based on Domain Join Type Hybrid Azure AD and Azure AD
- Create AAD Dynamic Groups based on MDM (Intune & SCCM Management)
- How To Create Nested Azure AD Dynamic Groups.
- Intune Admins Basic Azure AD Dynamic Device Group Rules | Queries
Table of Contents
How to Create Azure AD Dynamic Device Groups for Windows BYOD CYOD Devices Microsoft Intune
Let’s discuss creating an Azure AD device group for Windows BYOD CYOD devices Microsoft Intune. Creating Azure AD device groups for Windows BYOD and CYOD devices with Microsoft Intune is easy. It is explained in detail below.
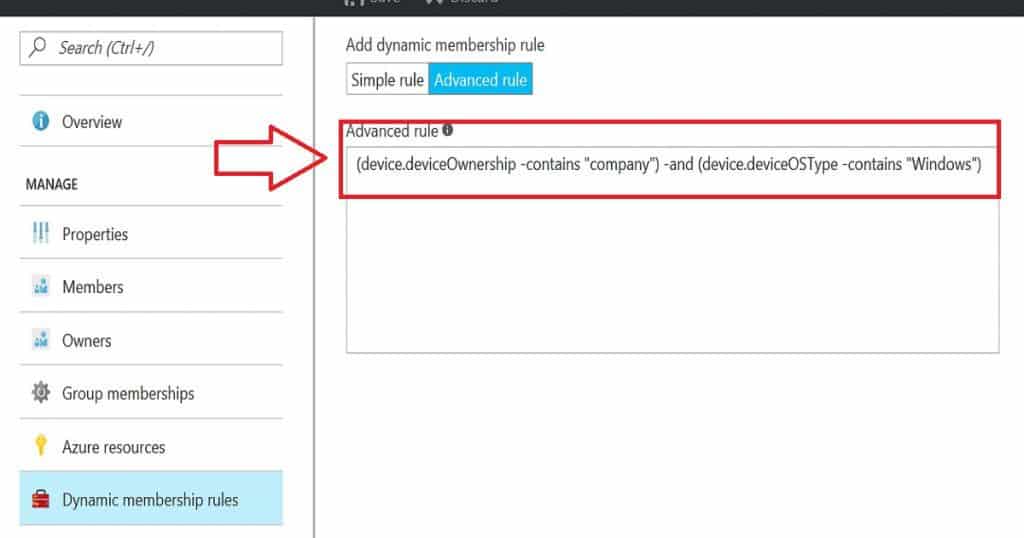
Following are the Advanced membership rules that you can use to create Azure AD and dynamic Device groups to segregate BYOD and CYOD devices! All Windows CYOD Devices Query for Azure Active Directory (device.deviceOwnership -contains “company”) -and (device.deviceOSType -contains “Windows”).
All Windows BYOD Devices Query for Azure Active Directory
(device.deviceOwnership -contains "Personal") -and (device.deviceOSType -contains “Windows”)All BYOD Devices Query for Azure Active Directory (device.deviceOwnership -contains “Personal”) All CYOD Devices Query for Azure Active Directory (device.deviceOwnership -contains “Company”).
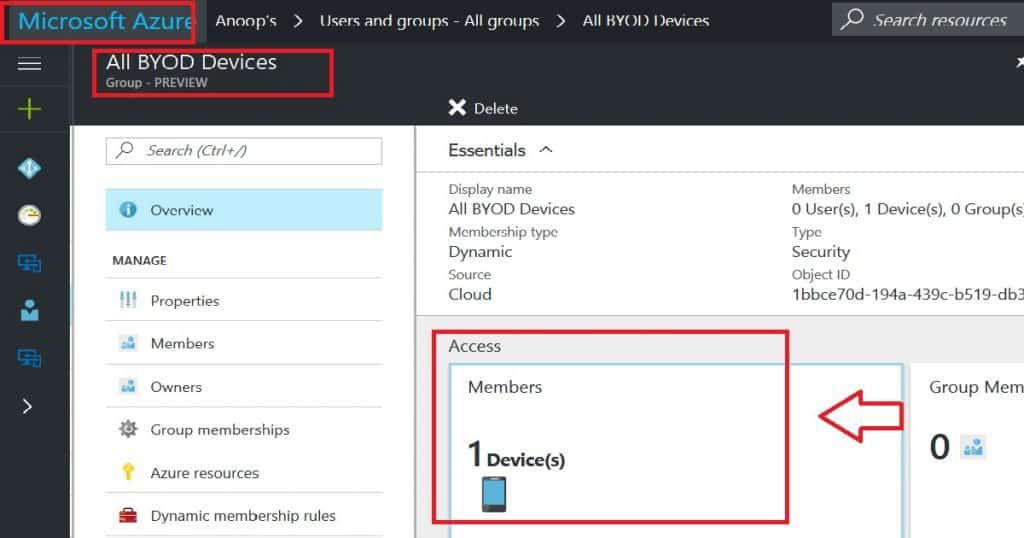
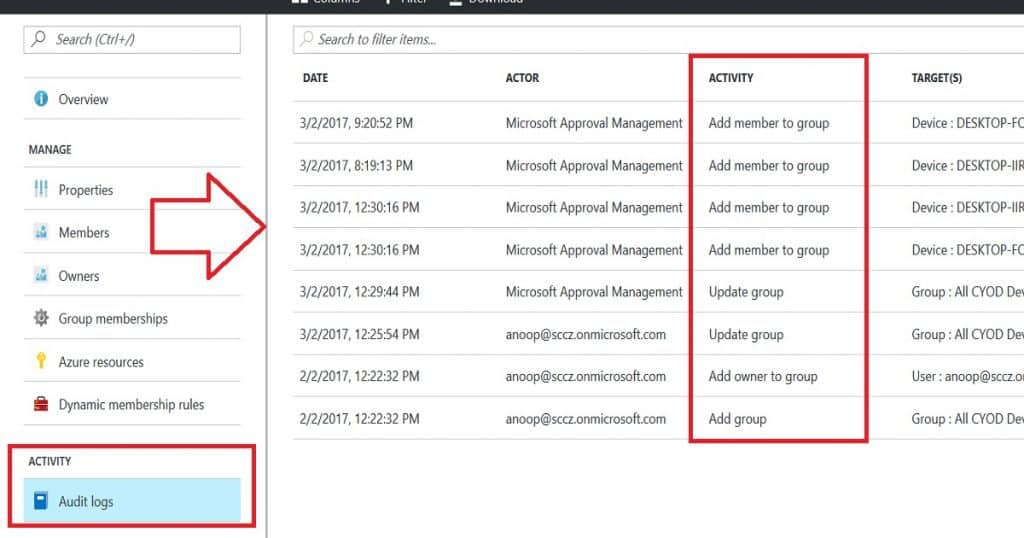
Auditing Azure Active Directory Dynamic groups is very important from the ops teams’ perspective. These auditing options are available in the new Azure portal, and it’s beneficial to track the changes of a particular Azure AD dynamic group.
As you can see in the table below, the ACTOR performed the activity for that group. For example, when I created this group, “Microsoft Approval Management” (probably an AAD automated process in the background) added 2 devices to the device group.
| Date | Actor | Activity | Target |
|---|---|---|---|
| 3/2/2017, 1:42:18 PM | Microsoft Approval Management | Add member to group | Device : DESKTOP-FOSD7L3, Group : All Windows CYOD Devices |
| 3/2/2017, 1:42:18 PM | Microsoft Approval Management | Add member to group | Device : DESKTOP-IIRCSUV, Group : All Windows CYOD Devices |
| 3/2/2017, 1:31:42 PM | anoop@sSDS.onmicrosoft.com | Add owner to group | User : , Group : All Windows CYOD Devices |
| 3/2/2017, 1:31:42 PM | anoop@sSDS.onmicrosoft.com | Add group | Group : All Windows CYOD Devices |
So, it’s recommended that we look at the best practices when we create dynamic devices or user groups in Azure Active Directory. You may not see performance issues with AAD dynamic groups during testing or POC, but when you migrate all the users into Azure AD, this could undoubtedly impact.
I always try to use -eq rather than -contains in the AAD dynamic rules, but it’s not always possible to use -eq! How to Create Azure AD Dynamic Device Groups for Windows BYOD CYOD Devices Microsoft Intune.
Reference
https://learn.microsoft.com/en-us/entra/identity/users/groups-dynamic-membership
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.

Hi Anoop,
Is there a way to create a dynamic group for newly enrolled devices alone?
I think you can do with managementType attribute as I mentioned in the last section of following post https://www.anoopcnair.com/windows-autopilot-profile-aad-dynamic-device-groups/
Hi Anoop,
I am from an Airwatch background, but want to do below in Intune.
A. I want to enable device ownership or category to appear when user enrolls into intune.
B. Depending on what he chooses, (Personal or corporate), i want different policies to get applied
A. Ownership is based on the Enrollment. When you use Azure AD join or Autopilot and MDM Enrollment for Windows 10, it will be treated as CYOD. Otherwise it will be treated as BYOD.
This is same for iOS and Android. If you use DEP to enroll then the device will be CYOD device otherwise BYOD
Hi Anoop
I am not sure if you are monitoring the replies to this blog still but I hope so 🙂
I am being told by Microsoft and other experts that we cannot offer a BOYD solution on the legacy Android device Administrator platform. See the below reply I received when I queried this.
My question then is similar to the one from ram. Is it possible to set it up in a way that when the user enrolls the device they get the option to choose corporate or personal and then different policies are applied based on which option they choose? According to Microsoft it is not.
There is no BYOD support for Android Device Admin. With Intune you can use MAM-only (without device enrollment), otherwise you need to use Work Profile (Android Enterprise)
Thank you for the reply Dan !! Yes work profile is also treated as BYO scenario isn’t it ?