The MITRE Vulnerability Report outlines CVE-2023-44487, also known as the HTTP/2 Rapid Reset Attack. Amazon Web Services (AWS), Cloudflare, and Google shared that they have taken actions to stop really big cyber-attacks. Microsoft released a workaround to mitigate this issue for Web servers.
They have implemented measures to ensure these attacks don’t cause major problems. In late August 2023, the companies discovered the layer 7 attacks. They worked together to tell everyone about it. They call this vulnerability CVE-2023-44487, which has a score of 7.5 out of 10, which means it’s pretty serious.
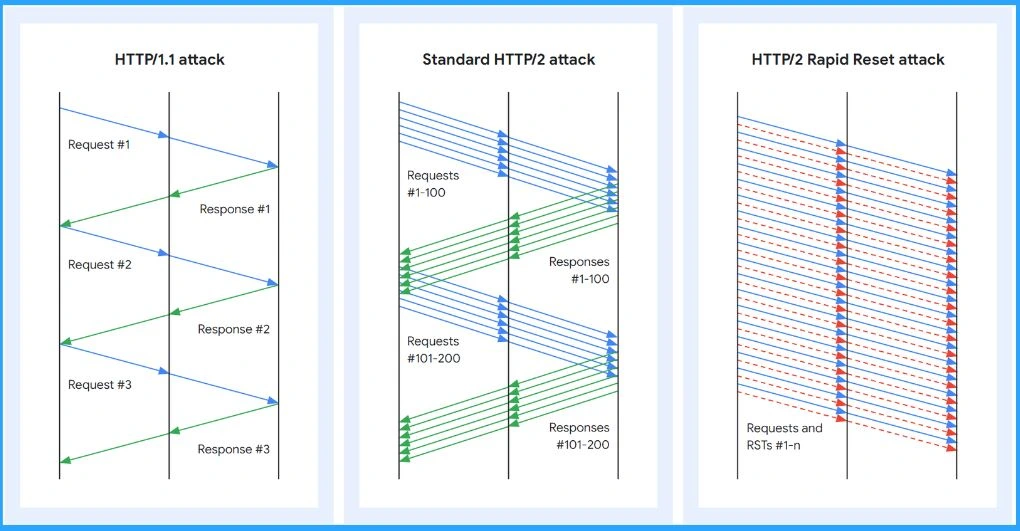
The attacks on Google’s cloud infrastructure reached a high point with 398 million requests per second. These attacks used a new method called HTTP/2 Rapid Reset. Meanwhile, AWS faced attacks with over 155 million requests per second, and Cloudflare had attacks with more than 201 million requests per second.
The ‘Rapid Reset‘ trick uses a special feature in HTTP/2 called ‘stream multiplexing‘. It works by sending lots of requests and quickly cancelling them. This makes the server work hard, while the attacker doesn’t have to do much. This attack messes up the website or app, making it ineffective.
In October 2023, Microsoft released updates to fix problems with Windows 11, specifically KB5031354 and KB5031358. They also released an update for Windows 10, known as KB5031356. Additionally, Microsoft mentioned that they are ending support for Windows 11 version 21H2.
- Download SCCM 2309 Early Ring Version using PowerShell Script
- SCCM 2309 Upgrade Guide | New Key Features
- 3 Zero Day and 104 flaws – October Patch Tuesday
What is CVE-2023-44487?
The CVE-2023-44487 is known as the HTTP/2 Rapid Reset Attack. It is a cybersecurity vulnerability that exploits a feature in the HTTP/2 protocol to overload a target website or application. It potentially leads to service disruptions.
How Does the HTTP/2 Rapid Reset Attack Work?
This attack works by using a special feature in HTTP/2 called ‘stream multiplexing’. The attacker sends lots of requests and quickly cancels them. This makes the server work hard, while the attacker doesn’t have to do much.
What are the Risks Associated with CVE-2023-44487?
The main risk is Distributed Denial of Service (DDoS) attacks. These attacks can overwhelm a target server, slowing the website or app or stopping working altogether.
Which Systems or Services are Affected by CVE-2023-44487?
The HTTP/2 capable web servers are vulnerable to this attack. Companies such as Amazon Web Services (AWS), Cloudflare, and Google have mitigated this vulnerability.
What is the CVSS Score for CVE-2023-44487?
The CVE-2023-44487 has a CVSS score of 7.5 out of a maximum of 10.
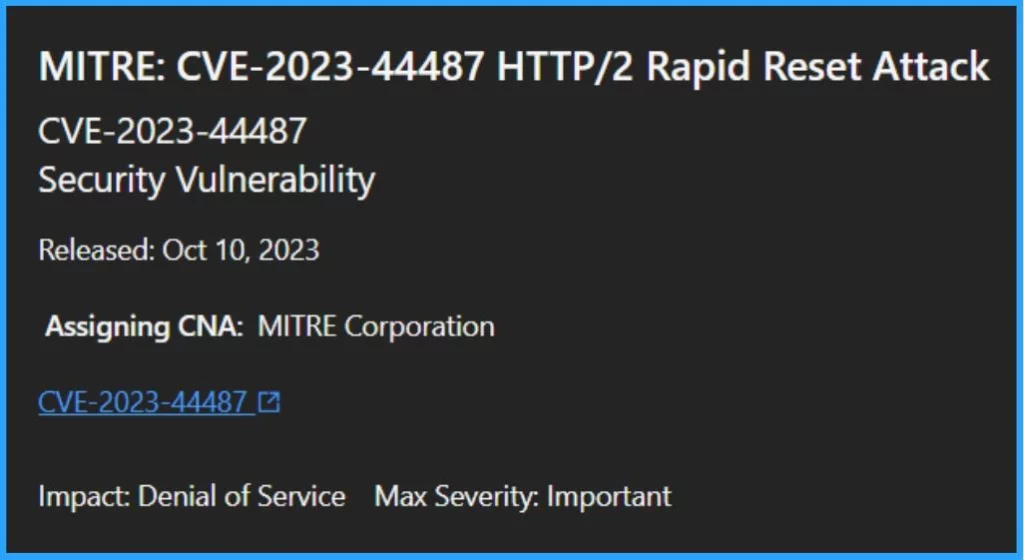
MITRE Vulnerability Report CVE-2023-44487 HTTP/2 Rapid Reset Attack
Let’s delve into the MITRE Vulnerability Report CVE-2023-44487, which focuses on the HTTP/2 Rapid Reset Attack. HTTP/2 has a built-in safety feature that aims to control how many tasks it handles at once to prevent overwhelming attacks, but sometimes, it doesn’t work as well as it should.
| Vulnerability | Details |
|---|---|
| CVE-2023-44487 | Security Vulnerability |
| Released Date | October 10, 2023 |
| Assigning CNA | MITRE Corporation |
| Impact | Denial of Service |
| Max Severity | Important |
What Steps Should Organizations Take?
To protect against HTTP/2 Rapid Reset attacks, a multi-faceted approach is essential. Strong HTTP flood protection tools and various DDoS defence strategies are essential. Implementing rate controls is important since these attacks target the protocol directly, and there is no universal solution.
- The core preventive measure is timely system updates and patching.
- Customers should install available patches to fortify their defences and create a robust barrier against potential exploitative attacks.
Stream Multiplexing
HTTP/2 uses “streams”, channels for sending messages, or “frames” between two points. The special thing about HTTP/2 is it can make the most out of one connection. It is like sending multiple messages on a single road, but everyone knows which message is for them.
- This means you can send many requests without having many separate connections. It is like a smart way of managing traffic on the internet road.
HTTP/2 Rapid Reset Attack
In HTTP/2, a client can signal the server to cancel a previous stream using a RST_STREAM frame. The protocol does not demand coordination between the client and server for this cancellation.
The client can do it on its own. It’s also assumed that the cancellation happens immediately once the server gets the RST_STREAM frame, even before it processes any other data from that connection.
- This type of attack is known as Rapid Reset.
- It relies on this ability to promptly cancel a request after making the server start processing.
- Although the request gets cancelled, it still keeps the HTTP/2 connection open.
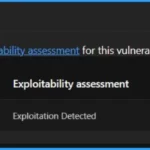
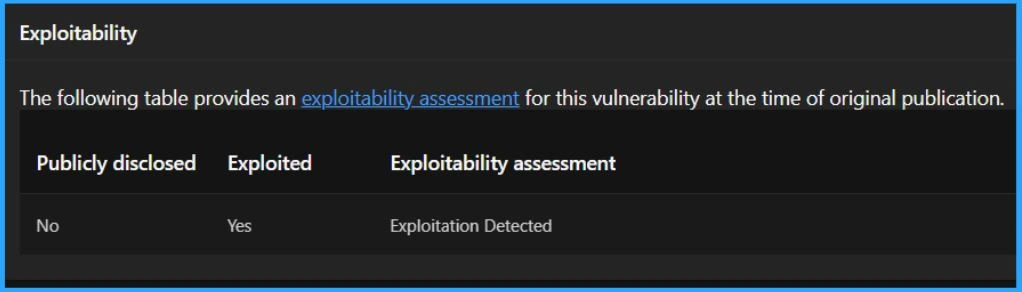
Exploitability Assessment of the Vulnerability
The Exploitability Index is a tool Microsoft provides to help customers assess the risk of a vulnerability. Microsoft assesses the likelihood of a vulnerability being exploited and shares this information in its monthly security updates.
- At the time of the original publication, there was no detected exploitation of this vulnerability.
- This means that no one had used it to do damage.
- Still, staying alert and implementing necessary security measures to prevent potential future exploitation is very important.
| Publicly Disclosed | Exploited | Exploitability Assessment |
|---|---|---|
| No | Yes | Exploitation Detected |
The table below helps you to provide a quick reference for understanding the level of risk associated with each Exploitability Index value.
| Exploitability Index | Short Definition |
|---|---|
| 0 | Exploitation detected |
| 1 | Exploitation more likely |
| 2 | Exploitation less likely |
| 3 | Exploitation Unlikely |
Workarounds
You have the option to consider certain workarounds to address the issue. It is important to note that Microsoft advises installing the updates for this vulnerability promptly, even if you decide to implement any of these workarounds. This ensures comprehensive protection against potential risks.
Important – Utilizing Registry Editor improperly can lead to severe issues that might require full reinstallation of your operating system. Microsoft cannot assure resolution for problems arising from incorrect Registry Editor usage. Use Registry Editor at your own risk.
1. Disable the HTTP/2 Protocol on your Web Server by using the Registry Editor
Begin by clicking on the Start menu, then select Run. In the Open box, type ‘Regedit‘ and click OK. In the Registry Editor, navigate to the following subkey: HKLM\SYSTEM\CurrentControlSet\Services\HTTP\Parameters
Locate and click on the DWORD type values named EnableHttp2TIs and EnableHttp2Cleartext.
- Modify these values as follows-
- Set it to 0 if you want to Disable HTTP/2.
- Set it to 1 if you want to Enable HTTP/2.
- After making the necessary changes, close the Registry Editor.
- Finally, Restart your computer for the adjustments to take effect.
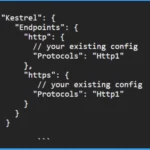
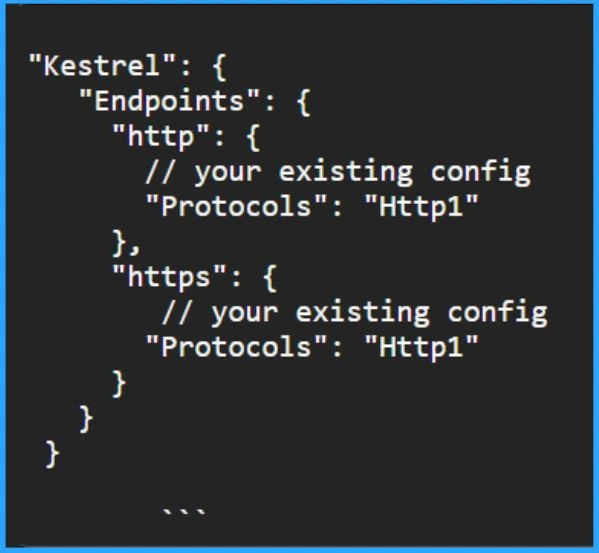
2. Include Protocols Setting for each Kestral Endpoint to Limit your Application to HTTP1.1
You are safe from this issue using .NET and Kestrel servers without HTTP/2. To ensure your application sticks to HTTP 1.1, you can change your appsettings.json file. Just add a ‘protocols’ setting for each endpoint.
"Kestrel": {
"Endpoints": {
"http": {
// your existing config
"Protocols": "Http1"
},
"https": {
// your existing config
"Protocols": "Http1"
}
}
}
```
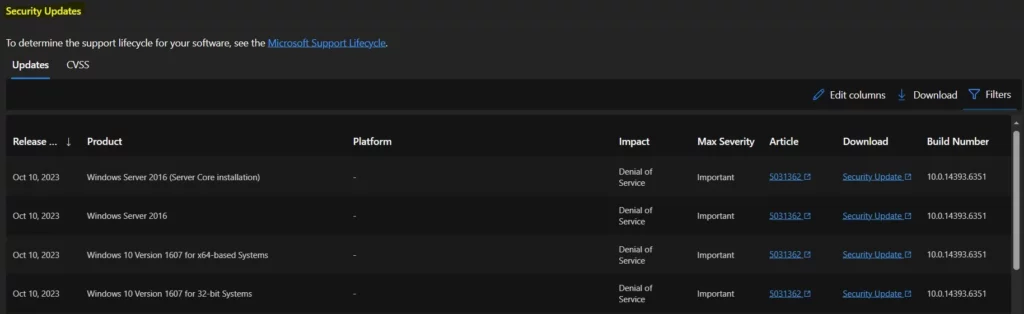
Security Updates
The Security Updates section has two categories: Updates and CVSS Details. Under the Updates menu, you can find details like Release Date, Product Name, Platform, Impact, Maximum Severity, Article, Download Link, and Build Number.
Next Steps
If you use HTTP/2, all providers must check if this problem could affect them. There might be updates or patches for popular web servers and programming languages that you can use soon or now. Putting those fixes in place as soon as possible is a good idea.
Author
About the Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.
