In this article let’s learn how to create Azure network connection for Windows 365 Cloud PCs in Microsoft Intune. Entra Joined Azure Network Connection (ANC) for Windows 365 Cloud PCs allows you to provision Cloud PCs that are joined directly to Microsoft Entra ID without requiring a connection to on-premises Active Directory. This simplifies deployment, especially for cloud-first or fully cloud-native organizations, reducing dependency on traditional domain infrastructure.
When configuring an Entra Joined ANC in Intune, you select the Microsoft Entra Join option during setup. You also specify the Azure virtual network, subnet, and resource group where the Cloud PCs will be provisioned. This ensures the Cloud PCs have secure network connectivity to cloud resources and internet-based applications, while eliminating the need for line-of-sight to domain controllers.
The Entra Join model improves security and modern identity management through integration with Conditional Access, password less sign-in, and device compliance policies. Using Intune, you can monitor ANC health, validate configuration, and troubleshoot provisioning issues, all through a unified portal. This setup is ideal for organizations looking to streamline their Windows 365 deployments with modern, cloud-based identity.
There are two types of Network connections available in Windows 365. Microsoft Entra join: no connectivity to a Windows Server Active Directory (AD) domain is needed. Hybrid Microsoft Entra Join: requires connectivity to a Windows Server AD domain. Provide the AD domain details when creating the ANC.

Table of Contents
Key Uses of Entra Joined Azure Network Connection
Entra Joined Azure Network Connection (ANC) for Windows 365 Cloud PCs offers several key uses and benefits for modern organizations. Refer to the table below.
| Key Uses | Description |
|---|---|
| Cloud-First Identity Integration | It enables Cloud PCs to be joined directly to Microsoft Entra ID (formerly known as Azure AD), eliminating the need for on-premises Active Directory. This supports a fully cloud-native identity model, ideal for remote and hybrid workforces. |
| Simplified Provisioning | Entra Join ANC allows organizations to deploy Windows 365 Cloud PCs without requiring a VPN or domain controller access. This reduces infrastructure complexity and speeds up provisioning, especially for users working from anywhere. |
| Enhanced Security and Management | Cloud PCs provisioned with Entra Join can leverage Microsoft Entra Conditional Access, compliance policies, and password less sign-in. They are fully manageable through Intune, supporting modern endpoint security and access control strategies. |
- How to Deprovision Windows 365 Cloud PC in Intune When they are in Grace Period Status
- How to Change Two New Display Language Packs for Windows 365 Cloud PCs using Intune
- How to Create Autopilot Device Preparation Policy for Windows 365 Frontline Devices using Intune
Create an Entra Joined Azure Network Connection for Windows 365 Cloud PCs in Intune
To Create an Entra Joined Azure Network Connection for Windows 365 Cloud PCs in Intune, follow these steps. First, sign in to the Microsoft Intune Admin Center with your administrator credentials.
- Navigate to > Devices > Device onboarding > Windows 365
- Click on Azure network connection > +Create > Choose Microsoft Entra Join
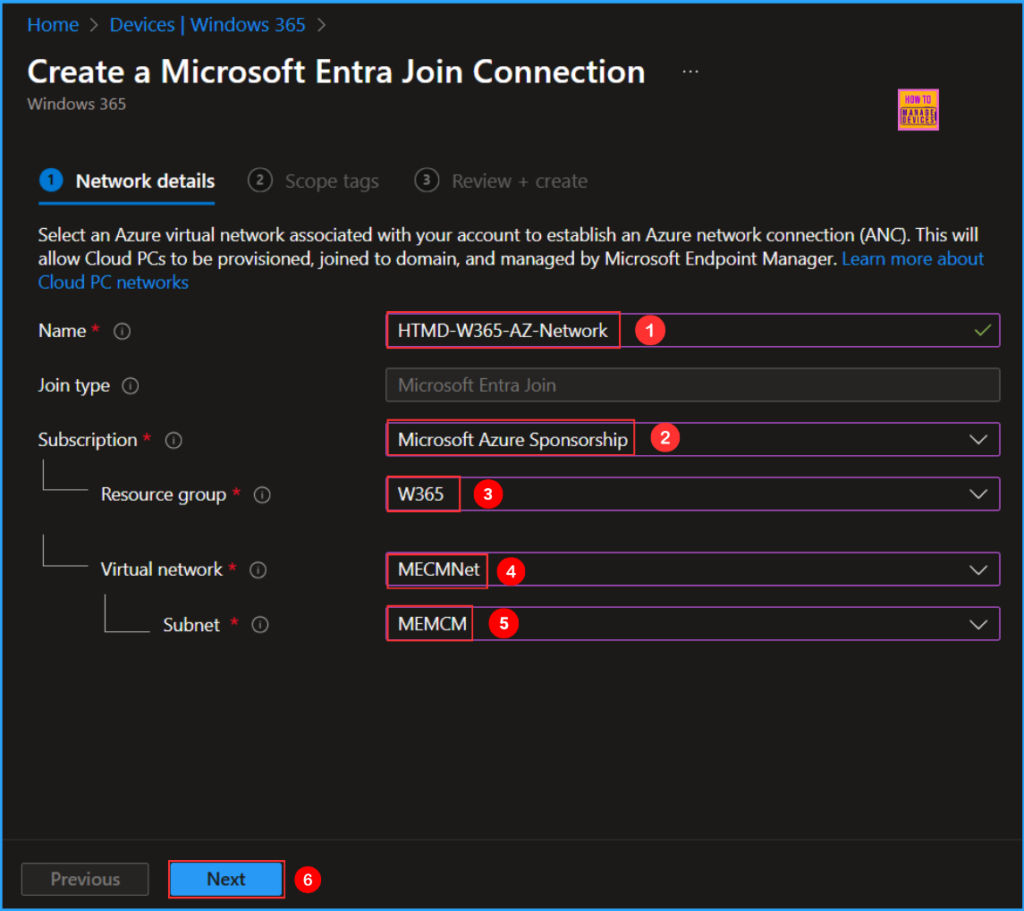
On the Network details tab, select the appropriate options to associate an Azure virtual network with your account. This will enable the establishment of an Azure Network Connection (ANC). As a result, Cloud PCs can be provisioned, joined to the domain, and managed through Microsoft Endpoint Manager.
- Name – HTMD-W365-AZ-Network (Use a connection name that can be easily identified when provisioning your Cloud PCs.)
- Join type – Microsoft Entra Join (The join type determines how this Cloud PC will be joined to Microsoft Entra ID.)
- Subscription – Microsoft Azure Sponsorship (Select the Azure subscription that contains the virtual network connected to your on-premises domain controller and network.)
- Resource Group – W365 (Select the Azure resource group that will contain the Network Interface Cards created by the Windows 365 service.)
- Virtual network – MECMNet (Select the virtual network to which Cloud PCs will be attached. For provisioning to succeed, the virtual network must be connected to a Microsoft Entra domain.)
- Subnet – MEMCM (Select the subnet for which Cloud PCs will assign an IP address for. For provisioning to succeed, the subnet must be routed back to a network with access to a domain controller. For Disaster Recovery purposes, make sure there are 50% IP addresses available at all times)
On the next page, keep the Scope tags set to Default. If your tenant has custom scope tags, select the appropriate ones based on your requirements, then click Next.
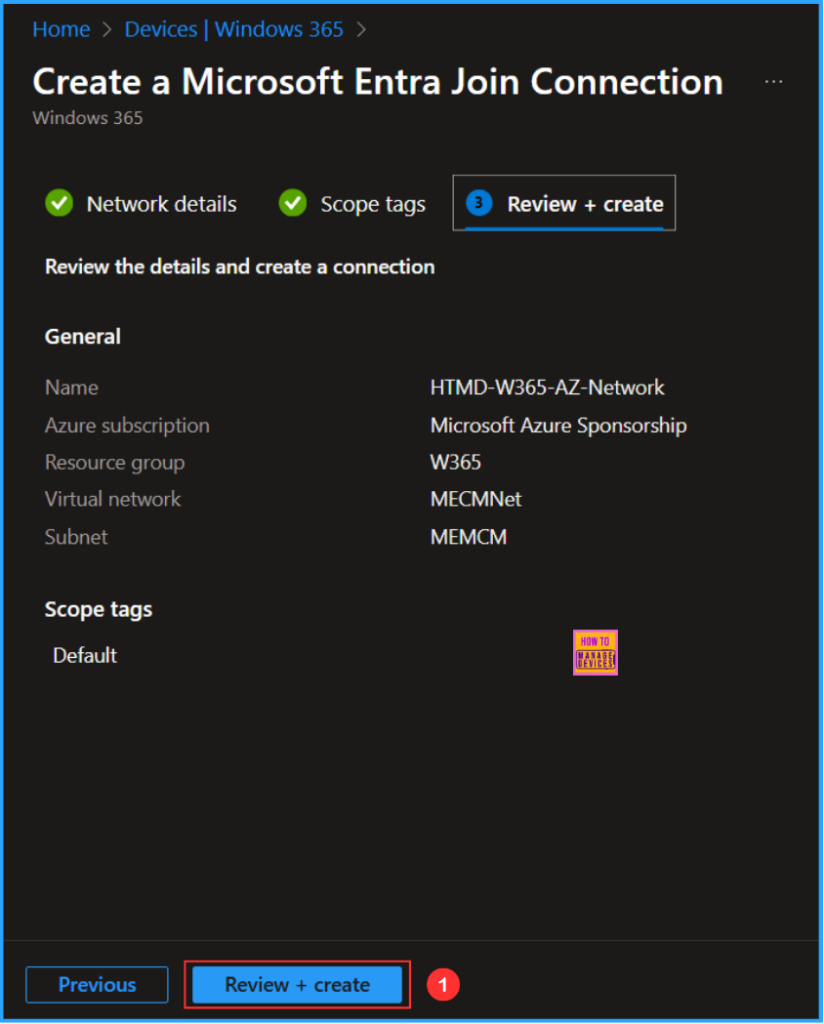
On the Review + create tab, check all settings for the Entra Joined Azure Network Connection for Windows 365 Cloud PCs. Once confirmed, select Create.
Overview of Entra Joined Azure Network Connection for Windows 365 Cloud PCs
Let’s explore a detailed overview of the newly created Microsoft Entra Connected Azure Network Connection (ANC) for Windows 365 Cloud PCs. The names and their descriptions are mentioned in the table below.
| Check Name | Description |
|---|---|
| Azure tenant readiness | This check verifies if the Azure subscription and necessary Azure resources are prepared for use. |
| Azure virtual network readiness | This check verifies if the Azure virtual network is ready for use. |
| Intune enrollment restrictions allow Windows enrollment | This check verifies if the Intune enrollment restrictions are configured to validate Windows enrollment does not block provisioning. |
| First party app permissions exist on Azure subscription | This check verifies if sufficient Azure permissions are exist on the subscription. |
| First party app permissions exist on Azure resource group | This check verifies if sufficient Azure permissions are exist on the resource group. |
| First party app permissions exist on Azure virtual network | This check verifies if sufficient Azure permissions are exist on the virtual network. |
| Azure subnet IP address usage | This check verifies if enough IP addresses are available in the configured subnet. |
| Endpoint connectivity | This check verifies if Windows 365 can connect to the necessary external URL’s for provisioning. |
| Localization language package readiness | This check verifies if the localization language package download link is reachable. |
| UDP connection check | This check verifies if the network configuration prevents the negotiation or use of a UDP connection to enhance the performance and reliability of your Cloud PC. |
- How to Configure Explicitly Deny EPM Rule with Microsoft Intune | New Updates | Demo
- How to Create New Platform Specific Device Clean-up Rule in Intune
- Cross-Region Disaster Recovery Now Available for Windows 365 Frontline in Dedicated Mode
To view an Overview of the newly created Entra Joined Azure Network Connection, click on the Overview tab for the network named HTMD-W365-AZ-Network. You can review and verify the various details, including the Check Name, Status, Last Check Date and Time, and any Actions taken.
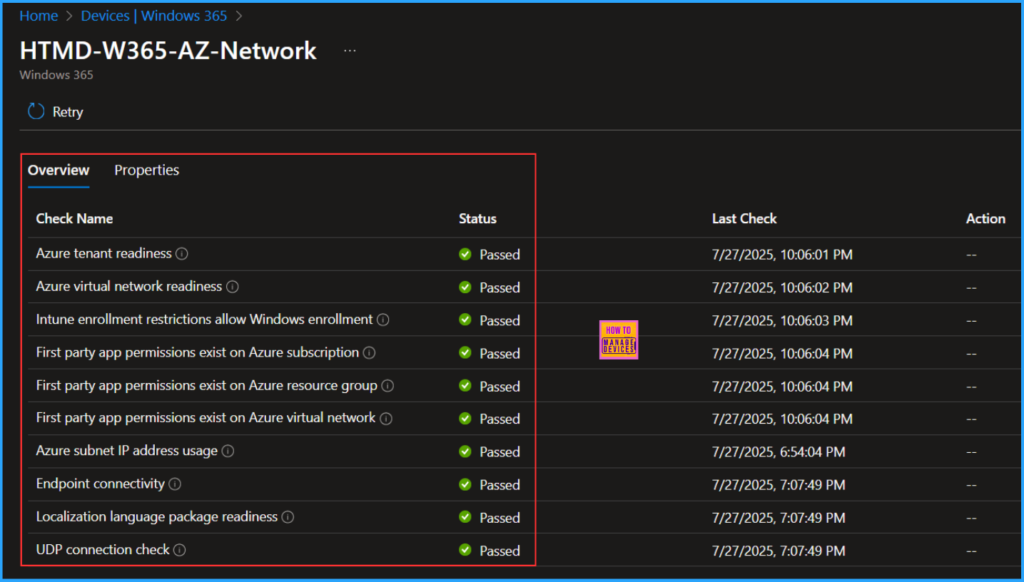
Monitor the Entra Joined Azure Network Connection
It’s time to verify the newly established Entra Joined Azure Network Connection (HTMD-W365-AZ-Network) for Windows 365 Cloud PCs.
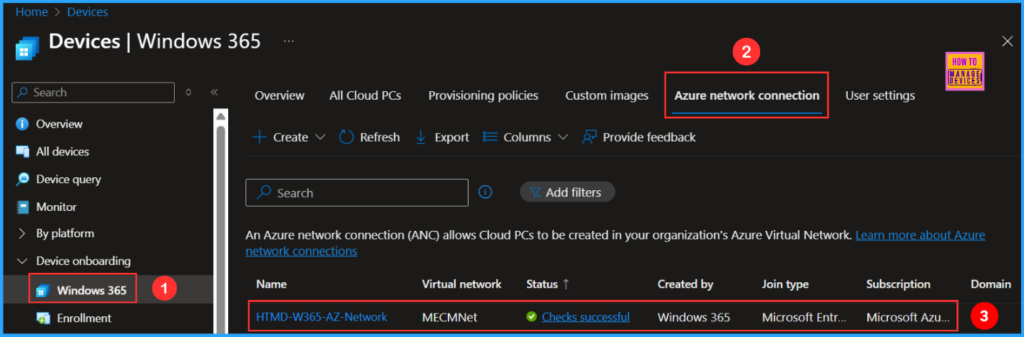
- Navigate to Devices > Device onboarding > Windows 365 > Azure network connection > In the search box, type the name “HTMD-W365-AZ-Network” If you have a limited number of Azure network connections available, you should be able to find it easily.
Now you can see HTMD-W365-AZ-Network has been created and the Status also changed from Running checks to Checks Successful.
HTMD-W365-AZ-Network has been created, and its status has changed from Running checks to Checks Successful!
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. Writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out my profile on LinkedIn.


