How to Prevent Malware Spread and Remote Attacks by Blocking PsExec and WMI with Intune ASR Rule. This rule helps you to block any processes that are created through PsExec and Windows Management Instrumentation (WMI).
These two tools are commonly used for remote administration and automation tasks. It allows IT administrators to execute commands and manage systems across a network efficiently. However, their powerful capabilities can also make them attractive targets for cybercriminals.
PsExec and WMI are Windows tools that allow administrators to control or manage other computers remotely. For example, an IT admin can use these tools to install software, run commands, or troubleshoot issues on another computer in the same network.
When malware uses PsExec or WMI, it can quickly spread across an organization’s network. For example, ransomware or hacking tools can use these programs to install harmful files on many computers without being noticed. Since PsExec and WMI are trusted parts of Windows, this activity can look normal at first, making it hard to detect the attack.

Table of Contents
Block PsExec and WMI Remote Execution using Intune ASR Rule to Prevent Lateral Movement and C2 Attacks
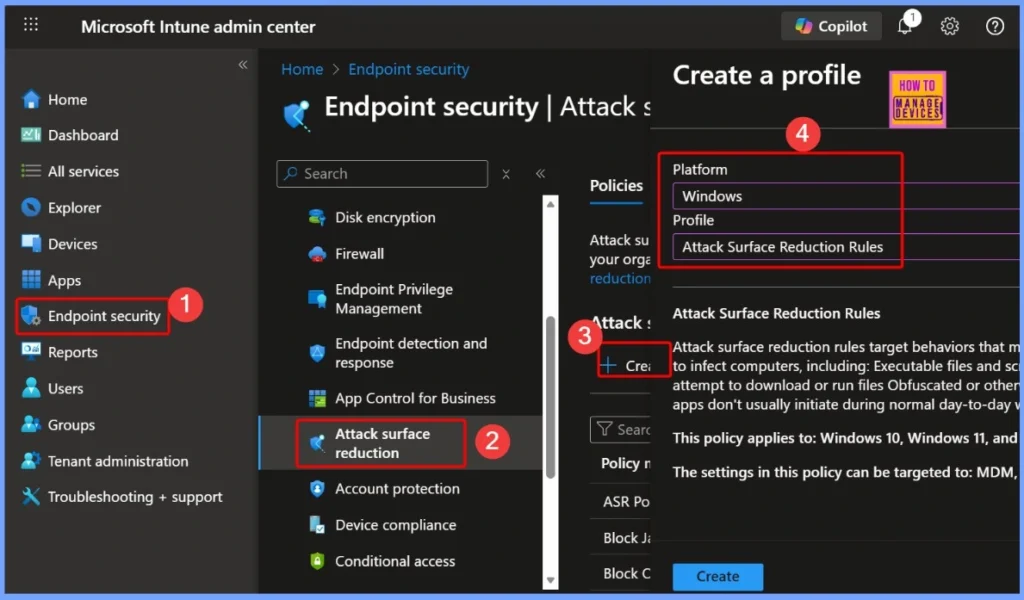
To block PsExec and WMI remote execution using the Intune ASR rule, first sign in to the Microsoft Intune Admin Portal with your admin credentials. After logging in, go to Endpoint security and choose Attack surface reduction from the menu. Then, click Create Policy to make a new ASR rule.
- In the policy settings, select Platform as Windows and choose the Profile type as Attack Surface Reduction Rules.
- Block Executable Files with Prevalence Age or Trusted List Criteria using Intune ASR Rules
- Microsoft Defender ASR Rules to Block Rebooting Machine in Safe Mode
- MDE Microsoft Defender for Endpoint Telemetry Issues
- Unable to Join Teams Meetings Using Links from Outlook Because of ASR Rules
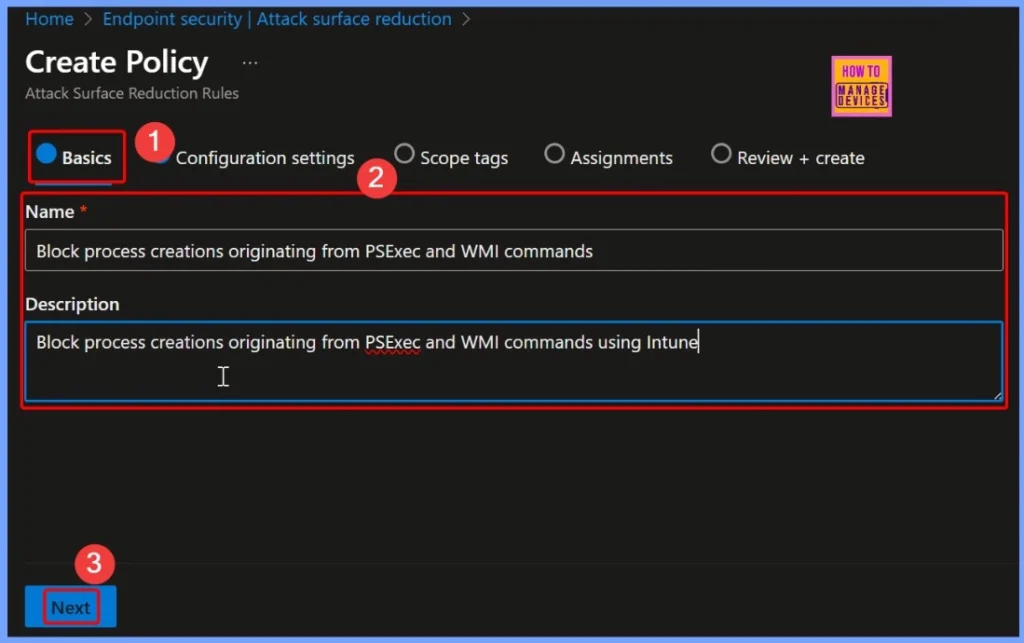
Basics Settings — Name and Description
In the Basics tab, you need to provide a name and description for the policy. These details help you easily identify the purpose of the policy later. The below table and screenshot shows more details.
| Name | Description |
|---|---|
| Block process creations originating from PSExec and WMI commands | Block process creations originating from PSExec and WMI commands using Intune |
Block Process Creations Originating from PSExec and WMI Commands Policy Options
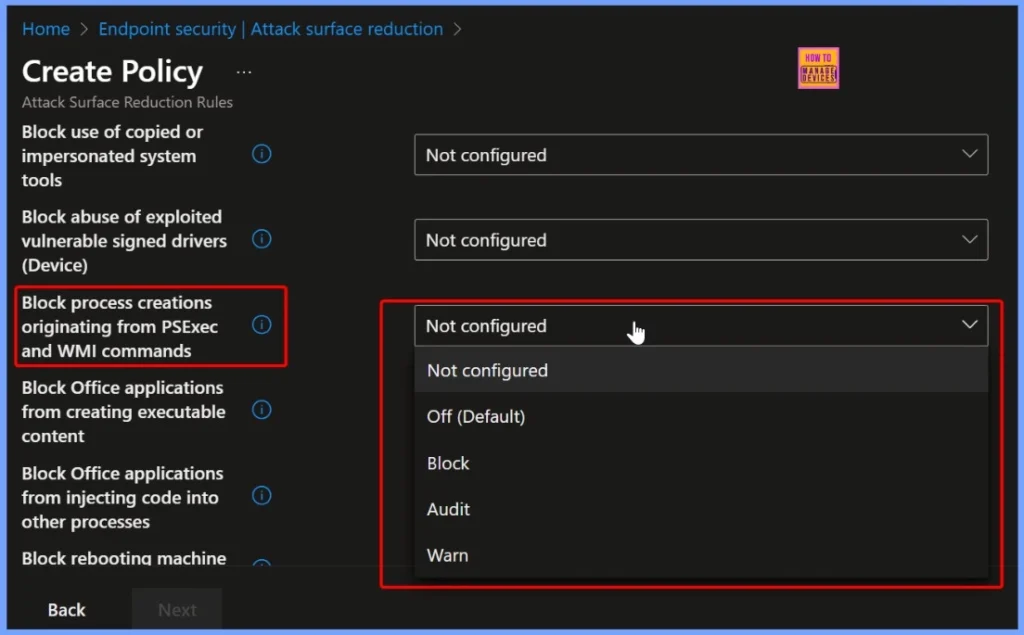
The “Block process creations originating from PSExec and WMI commands” policy offers different configuration modes to control how the rule behaves on managed devices. You can choose from the following options.
- Not Configured: The rule is not applied and devices continue to operate with their current settings.
- Off (Default): The rule is turned off, meaning PSExec and WMI command-based process creations are not blocked or audited.
- Block: This option actively prevents process creations initiated via PSExec or WMI commands, helping to mitigate lateral movement attacks and unauthorized remote execution.
- Audit: The rule only logs attempts to create processes through PSExec or WMI, allowing administrators to monitor activity without enforcement.
- Warn: End users receive a warning before executing processes via PSExec or WMI, giving them a chance to cancel the action before it runs.
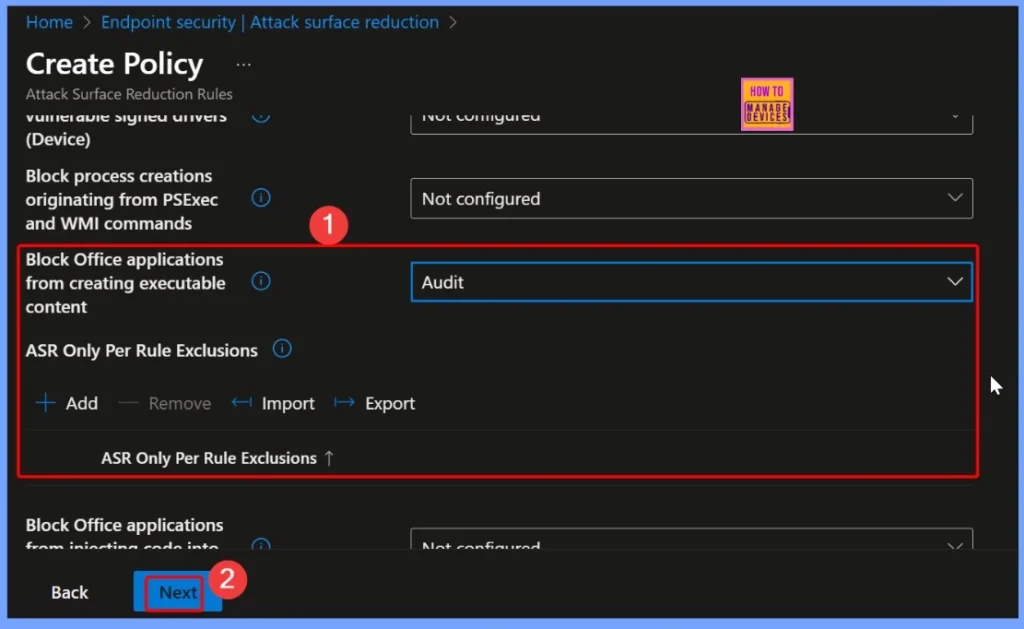
Block Process Creations Originating from PSExec and WMI Commands Audit Mode
In this policy, we select the Audit option. When configured to Audit, the rule only logs any attempts to create processes using PSExec or WMI commands. This mode allows administrators to monitor activity and review potential risks without enforcing restrictions.
| Policy Name | Mode |
|---|---|
| Block process creations originating from PSExec and WMI commands | Audit |
Scope Tag for the Block Process Creations Originating from PSExec and WMI Commands Policy
The Scope Tag in Intune defines which administrative groups can view or manage a particular policy. For the “Block Process Creations Originating from PSExec and WMI Commands” policy, the scope tag ensures that only authorised administrators have access to create, edit, or monitor this policy.
| Name | Description |
|---|---|
| Default | Default Role Scope Tag. This will exist by default on all Intune entities whenever a user defined Role Scope Tag is not present. |
Assignments of the Policy
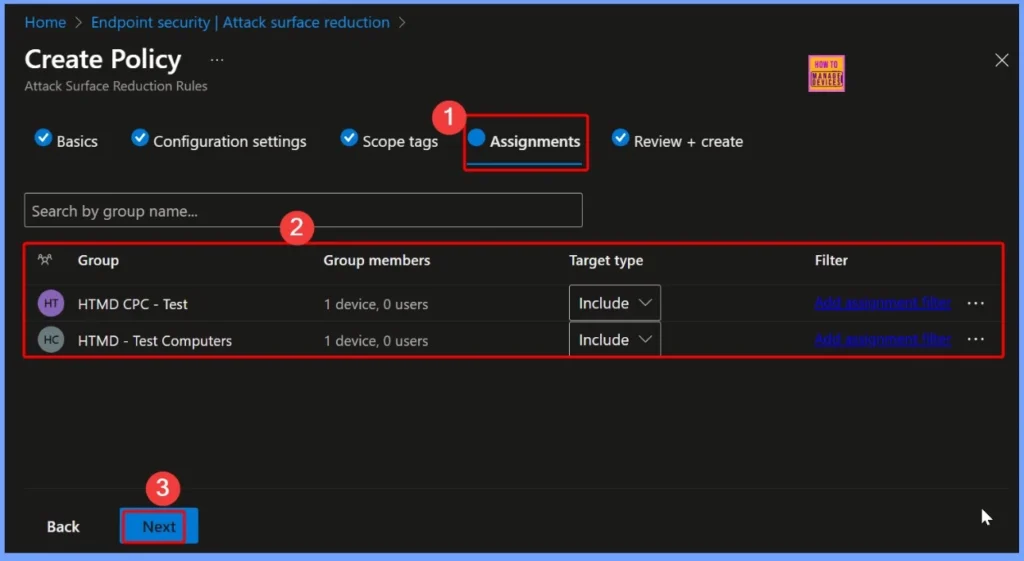
The Assignments section determines which device groups the policy applies to. For the “Block Process Creations Originating from PSExec and WMI Commands” policy, you can target specific device groups based on your organization’s security requirements.
- Here we select 2 groups that HTMD CPC Test and HTMD Test Computer.
Review + Create to Verify All the Settings Configured
In the Review + Create step, you can verify all the settings configured for the “Block Process Creations Originating from PSExec and WMI Commands” policy before finalizing it. This includes checking the policy name, description, configuration mode (Audit, Block, etc.), scope tags, and assignments.
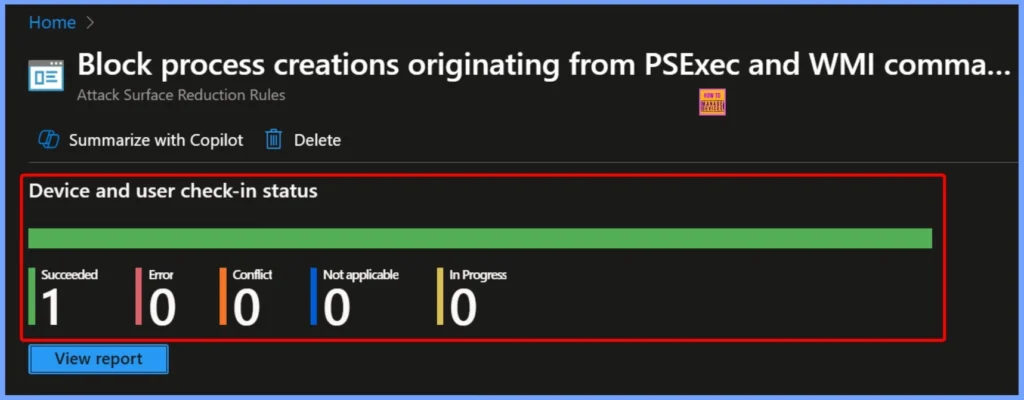
Device and User Check in Status
The Device and User Check-in Status for the “Block Process Creations Originating from PSExec and WMI Commands” policy shows the following results: Succeeded – 1, Error – 0, Conflict – 0, Not Applicable – 0, and In Progress – 0.
Client Side Verification
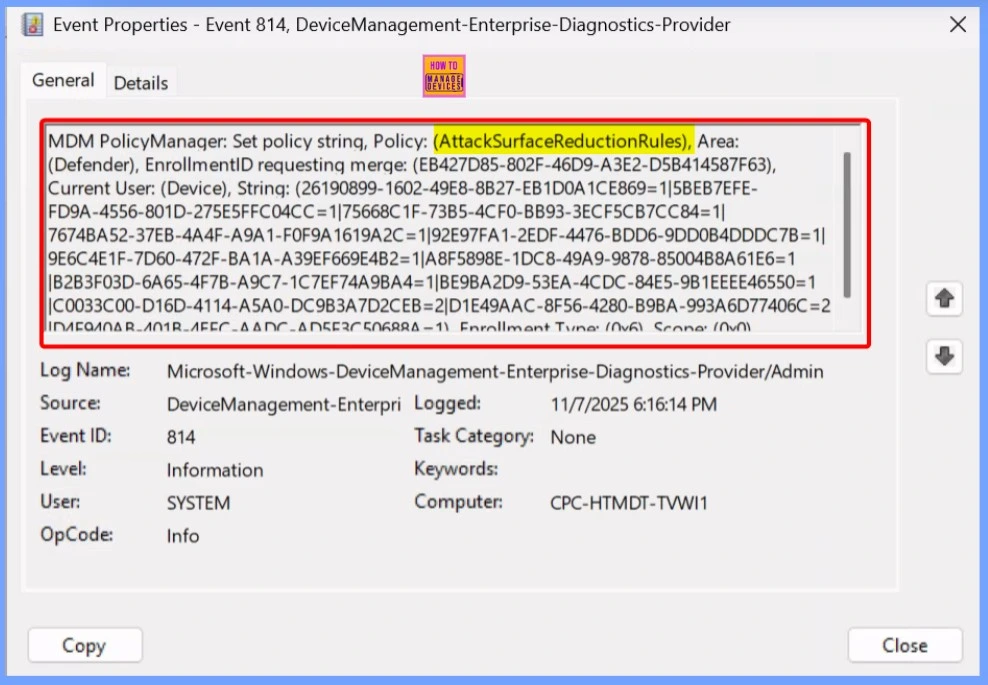
To verify that the Block PsExec and WMI Remote Execution ASR rule has been successfully applied through Intune, you can use the Event Viewer on the target device. Open Event Viewer and go to the following location.
Applications and Services Logs → Microsoft → Windows → DeviceManagement-Enterprise-Diagnostics-Provider → Admin.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


