How to Use SCCM ConfigMgr Tool Policy Spy exe Endpoint Manager. Policy Spy is System Center 2012 Configuration Manager Client Troubleshooting Tool.
Policy Spy can be used to troubleshoot the policy system of the SCCM/ConfigMgr Client. Have you ever played with PolicySpy.exe? If not, start using it.
How to Use SCCM ConfigMgr Tool Policy Spy exe Endpoint Manager
In this post, I‘m trying to explore the Policy Spy tool in more detail how it can be used more effectively. The documentation provided with this toolkit is excellent (ToolkitHelp); however, I’ve seen many of us never look into those documentations.
This is a continuation of my post about Client Spy.
Policy Spy is part of ConfigMgr 2012 Toolkit and can be downloaded from This LINK.
Before going into deep dive, I would like to remind you Policy Spy MUST be run as administrator.
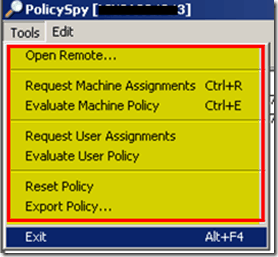
Open Remote : If you want to run Policy Spy on a remote computer.
All the following features will be disabled when viewing the exported policy file.
Request Machine Assignments: Select this option to trigger the machine policy. Default machine policy polling interval is 60 minutes. This is useful when troubleshooting and you want a machine to immediately ask for policy from the management. Monitor PolicyAgent.log to get more details about the policy request and reply from Management Point.
Evaluate Machine Policy: If you want to trigger the MACHINE policy evaluation on a target computer, you can use this option. Once you have triggered the policy evaluation, you can look at the log file called PolicyEvaluator.log for further troubleshooting. It will help you to understand whether the policy is getting evaluated successfully or not.
Request User Assignments: If you want to trigger the User policy for the currently logged-on users, select this option. The Default user policy polling interval is 60 minutes. This is useful at the time of troubleshooting. Monitor PolicyAgent.log to get more details about the policy request and reply from Management Point.
Evaluate User Policy: If you want to trigger the USER policy evaluation on a target computer, you can use this option. Once you have triggered the policy evaluation, you can look at the log file called PolicyEvaluator.log for further troubleshooting. It will help you to understand whether the policy is getting evaluated successfully or not.
Reset Policy: This option will remove all non-default policies and reset the policy cookies for the site. It then triggers a request for machine policy assignments.
Export Policy: If you want to export the policy details to further troubleshooting or analysis, use this option. Exports the target computer system’s policy to an XML-format export file. This file can be viewed on any computer by selecting Open File on the Tools menu and opening the export file.
We are going to cover the following topics in detail.
Actual tab
Requested tab
Default tab
Events tab
Client Info Pane
Details Pane
Actual Tab
Have a look at the screenshots below? This tab will provide you with client agents policies details configured on the site level Machine Policy Interval, Software Inventory, Hardware Inventory, etc. Results are displayed in tree format with a root node for the Machine namespace and each user-specific namespace.
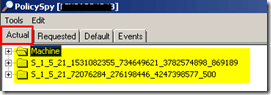
Expand the machine namespace will show you the classes (CCM_ClientActions), and you can expand the classes to see {00000000-0000-0000-0000-000000000001}- Class for hardware Inventory, {00000000-0000-0000-0000-000000000002} – Class for Software Inventory and
{00000000-0000-0000-0000-000000000003} – Class for Discovery Inventory.
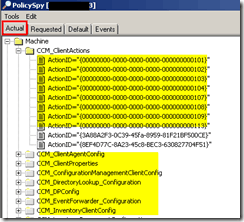
Requested tab
This tab displays the policy assignments retrieved from the client’s assigned site. Results are displayed in tree format with a root node for the Machine namespace and each user-specific namespace. All the following details in this section are taken from the ToolkitHelp document.
Results are displayed in tree format with a root node for the Machine namespace and each user-specific namespace. Expanding a namespace node shows the Configuration and Settings nodes.
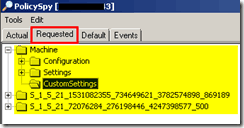
a. Configuration node – displays a list of configuration classes derived from CCM_Policy_Config, including policy objects, assignments, and others.
b. Settings node – Expanding the Settings node displays all active settings generated by policies. Settings are displayed under the Configuration node.
Note
Multiple instances can exist with the same names because these settings have not been merged into a resultant final set. Policy Spy displays instances under this node using the RealKey properties instead of their true policy keys to easily correlate to the resultant set shown on the Actual tab.
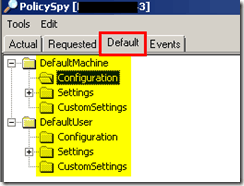
Default tab
The default tab displays the same information that the Requested tab does and the contents of the DefaultMachine and DefaultUser namespaces.
Events Tabs
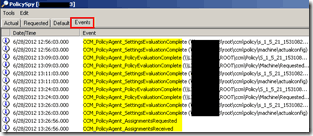
Events tab displays policy agent events as they happen. The view creates a WMI event subscription for all events derived from CCM_PolicyAgent_Event.
The view shows a maximum of 200 events and removes the oldest events from the top of the list, as required. If the last item in the list is selected, the list automatically scrolls down as new events are added. Otherwise, the view maintains its current position, and you must scroll down or press the End key to view new events. This view is always empty when viewing an exported policy.
Client Info Pane
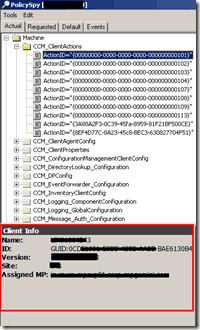
Client Info pane provides us the details about the client name, GUID, Client Version, Assigned Site Code, and assigned MP; also Resident MP. Form this pane, we can understand that the client is communicating with proper MP or it’s under global roaming, etc.
Details Pane
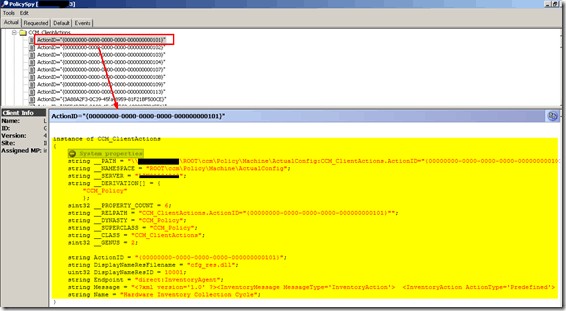
The details pane displays the policy body of the current selection the MOF that displays.
If the body has not been downloaded by the client, Policy Spy displays a hyperlink so you can download the policy body directly from the client’s management point. Clicking the link causes Policy Spy to send an HTTP query to the management point.
If the policy body download succeeds, the hyperlink is replaced with the contents of the reply. Otherwise, the display is updated, indicating that the request failed.
Author
Anoop is Microsoft MVP! He is a Solution Architect in enterprise client management with more than 20 years of experience (calculation done in 2021) in IT. He is a blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. E writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc…


Great explanation!