Let’s discuss Enable HTTPS Warning Page Policy for MS Edge Browser to Control User Access from SSL Errors using Intune. Microsoft Intune provides policy to users to proceed from the HTTPS warning page in the Microsoft Edge Browser. With this policy, the warning page shows when users visit sites that have SSL errors.
As you know that, SSL errors are a major red flag for potential security risks, such as a man-in-the-middle (MitM) attack, Expired or Invalid Certificates, Self-Signed Certificates. The MitM attack mean a malicious actor is intercepting the connection to steal data.
This policy helps to enhance the security of your organization. By showing a warning page, Edge is trying to prevent the user from being tricked into sending sensitive information (like passwords or credit card numbers) to a malicious third party.
By enabling this policy Admins can enforce strict security across your organization. Admins can manage this policy for all devices using Intune settings catalog. The policy is a critical tool for mitigating the risk of data breaches, intellectual property theft, and other cyberattacks that could result from insecure web connections.
Table of Contents
Enable HTTPS Warning Page Policy for MS Edge Browser to Control User Access from SSL Errors using Intune
By configuring this policy, admins can prevent users from visiting websites designed to install malware or trick them into giving away personal information. HTTPS warnings are a key indicator of such threats. This policy provide consistency for al users in your organisation.
- Enable or Disable Insecure Download Warning Policy for Microsoft Edge using Intune
- How to Establish the Allow Warning for Other Disk Encryption through Intune Setting Catalog
- Enable Disable Show Downloads Insecure Warnings in Edge via the Microsoft 365 Admin Portal
Configure HTTPS Warning Page Policy
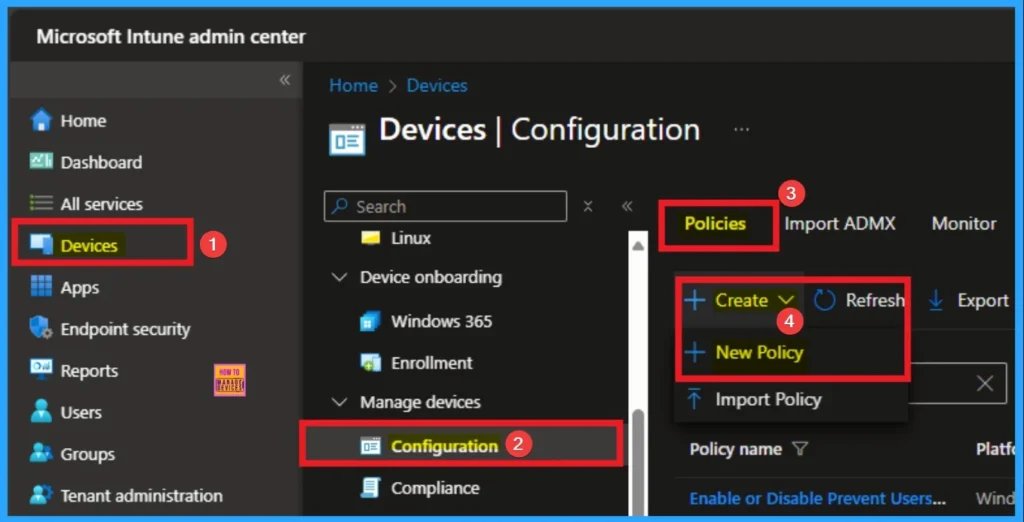
By signing in Microsoft Intune admin center, you can start configuring HTTPS Warning Page Policy. Open the Microsoft Intune Admin center. Go to Devices > Configuration > +Create >+ New Policy.
Selecting Profile and Platform
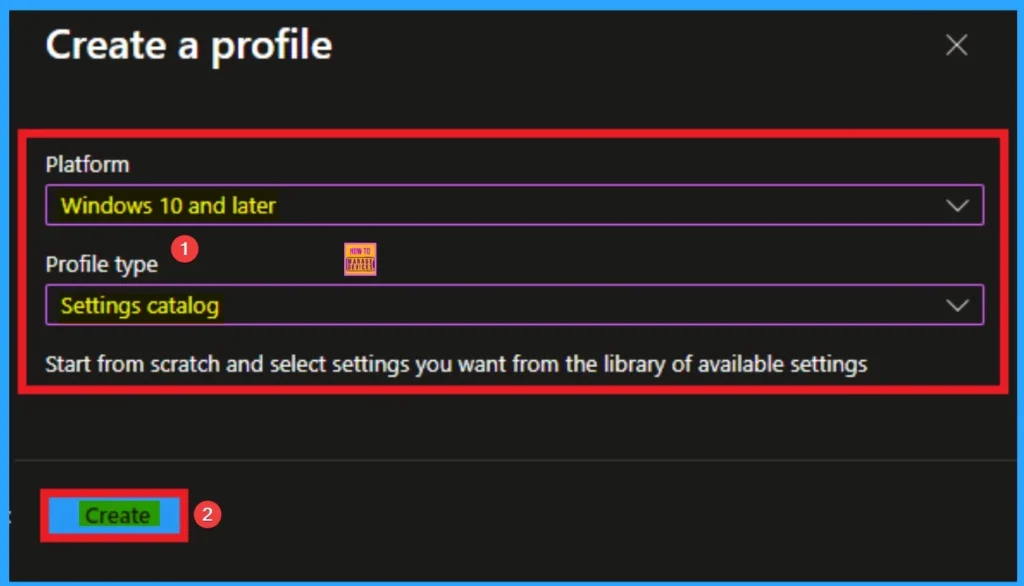
After that, you have to select platform and profile. It is important to select the platform and profile before configuring the policy. Here, I selected Windows 10 and later as the Platform and Settings catalog as the profile type. Then click on the Create button. Then you will get the basic tab.
Note that, if you start the policy creation with the tabs like basic tab, configuration settings, you can’t change the profile and platform. If you want makes changes in profile, you should start once more from Create profile page.
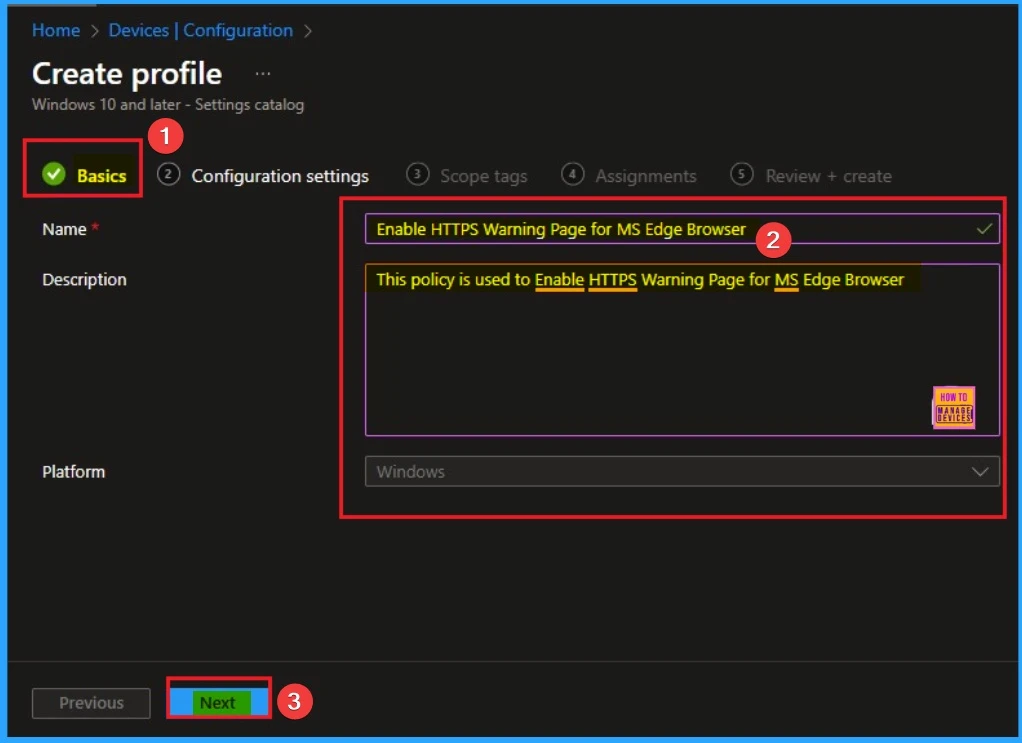
Adding Basic Details
Adding basic details is necessary and important in policy creation. It gives an identify for the settings you will select to create the policy. Policy name and description is useful for identifying the policy purpose. After adding this, click on the Next button.
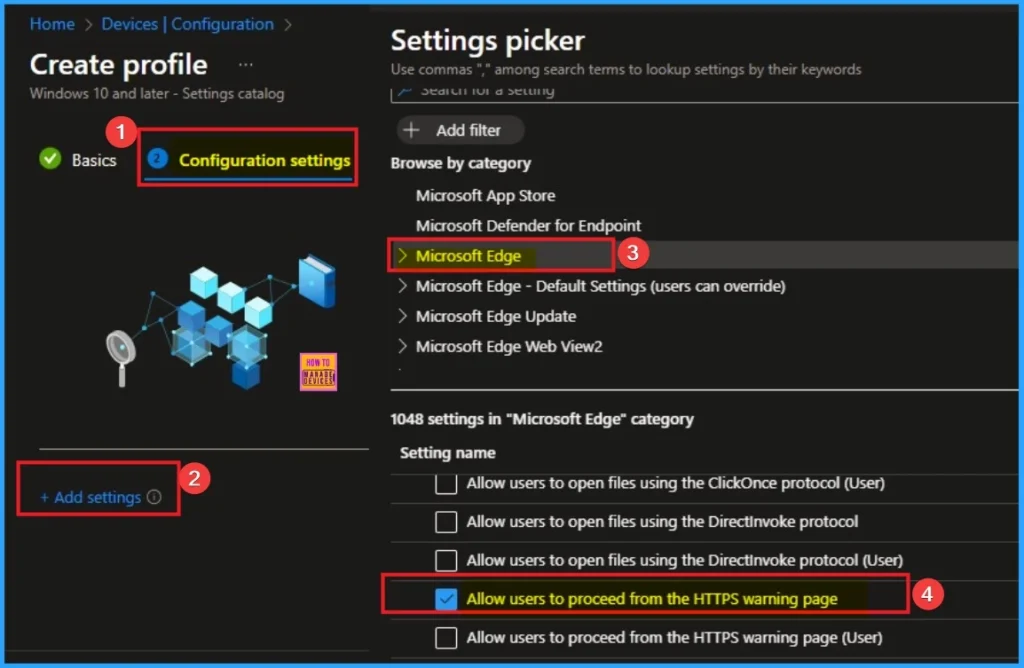
Configure the settings from Settings Picker
Using configuration settings tab, you can access the specific settings. For this you have to click on the +Add settings hyperlink to get the settings picker. From the Settings Picker I choose Microsoft Edge category and select Allow users to proceed from the HTTPS warning page settings. Then you can close settings picker.
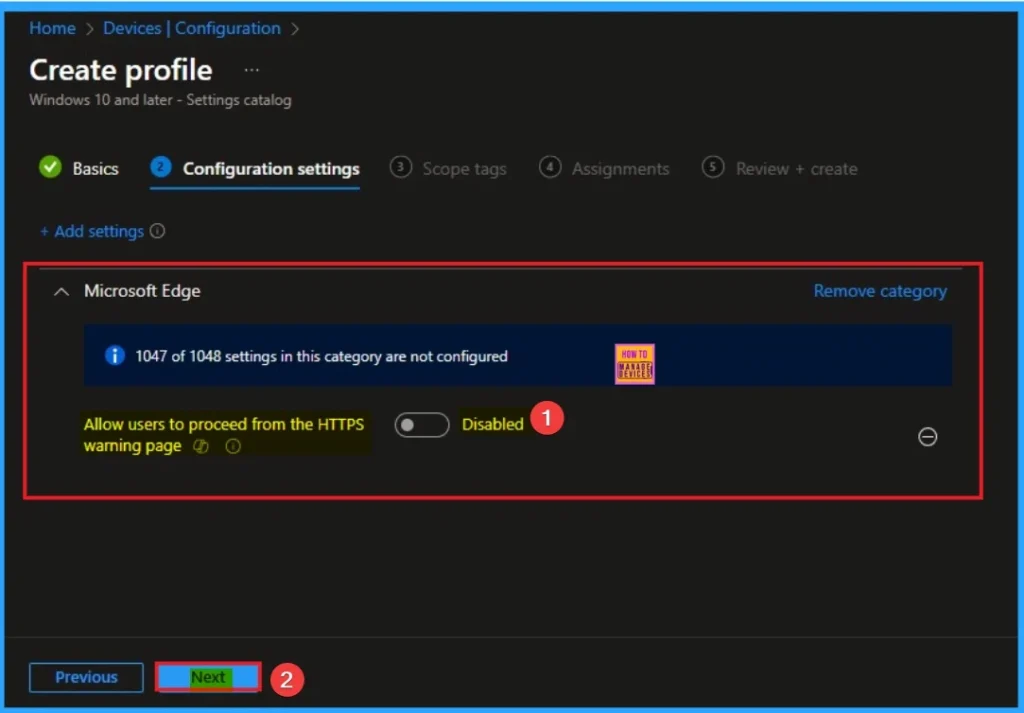
Disable HTTPS Warning Page
Users are blocked from proceeding no bypass option is shown. By default, this policy is disable. If you want to disable the Click on the Next button.
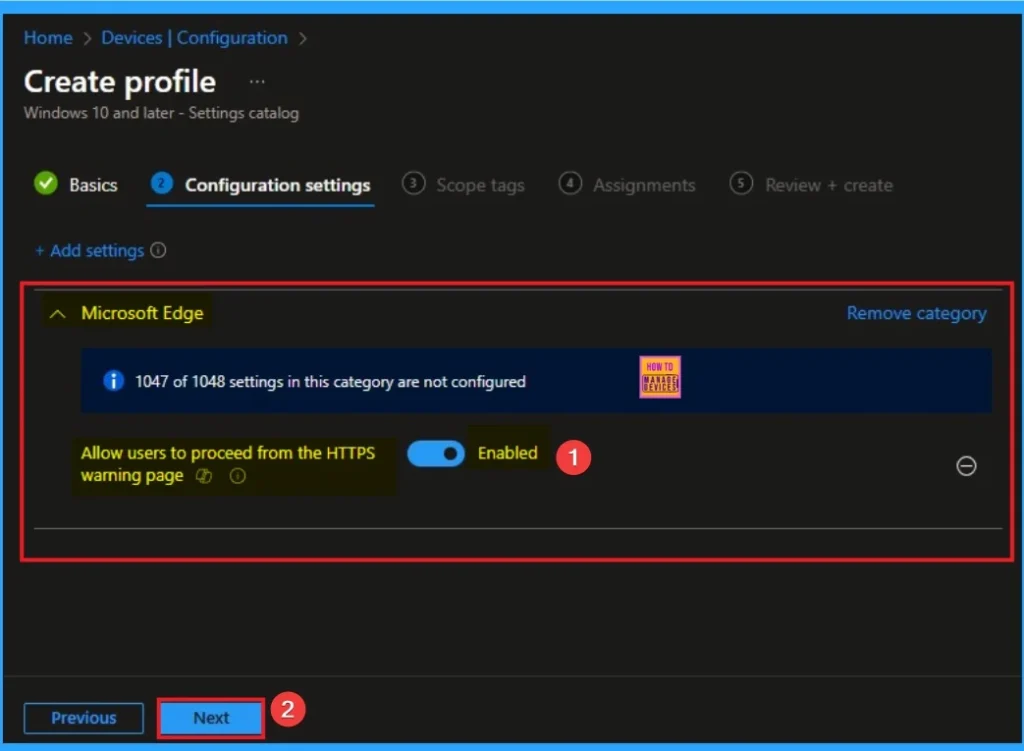
Enable HTTPS Warning Page
By Enabling this policy on Microsoft Edge browser Users see a warning but can click through to proceed. Here, I would like to enable theHTTPS Warning Pages.
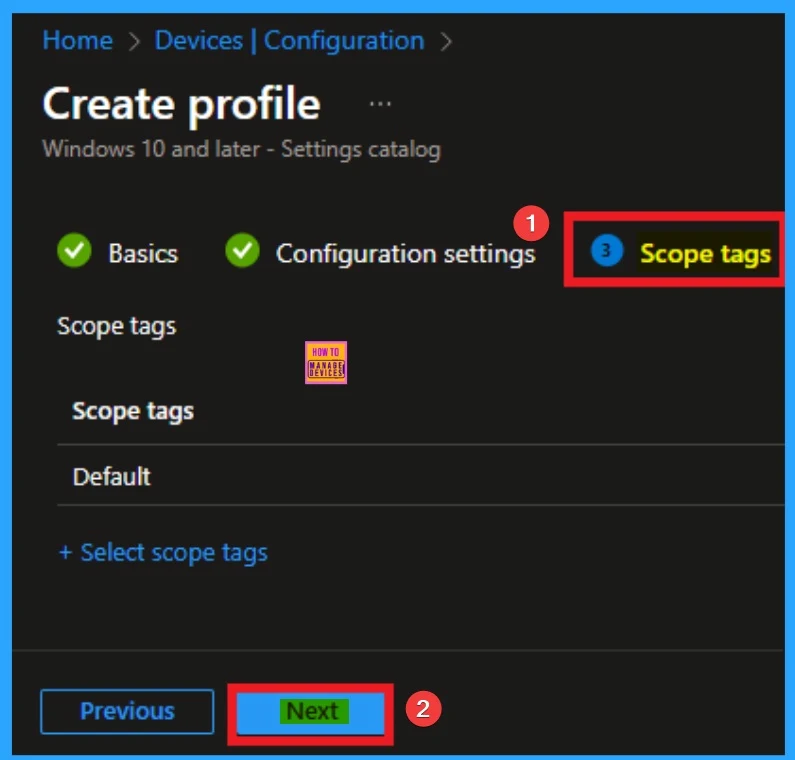
Scope Tags for Policy
With scope tags, you create a restriction to the visibility of the HTTPS Warning Page. It also helps to organise resources. Here, I would like to skip this section, because it is not mandatory. Click on the Next button.
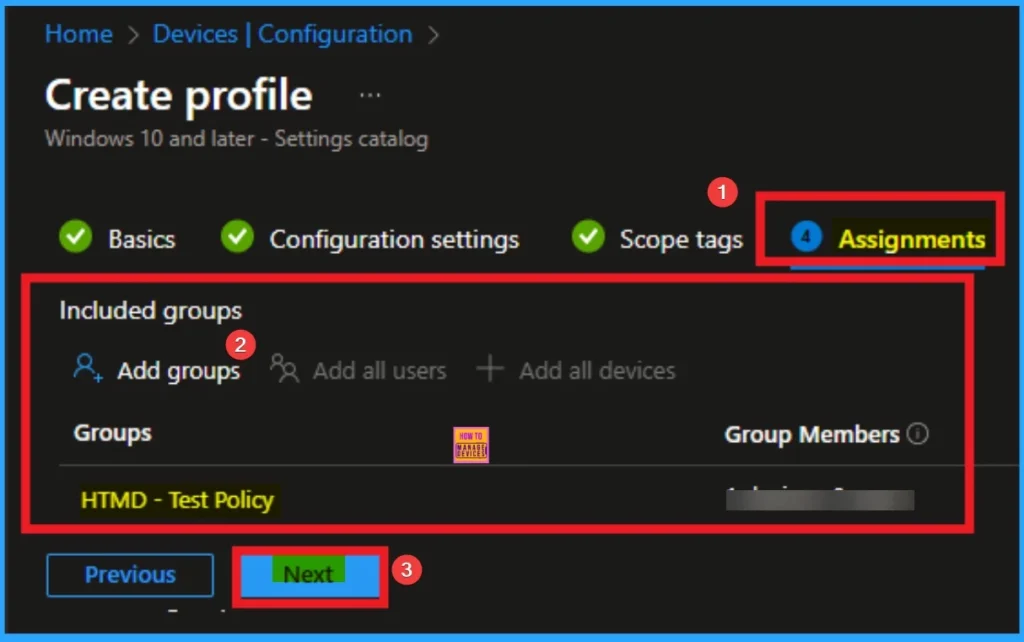
Assigning Specific Groups
To assign the policy to specific groups, you can use the Assignment Tab. Here I click, +Add groups option under Included groups. I choose a group from the list of groups and click on the Select button. Again, I click on the Select button to continue.
Review + Create Tab for Policy Creation
Review + Create Tab helps you recheck all the details of the policy you entered on all the tabs. After verifying all the details, click on the Create Button. After creating the policy, you will get a success message.
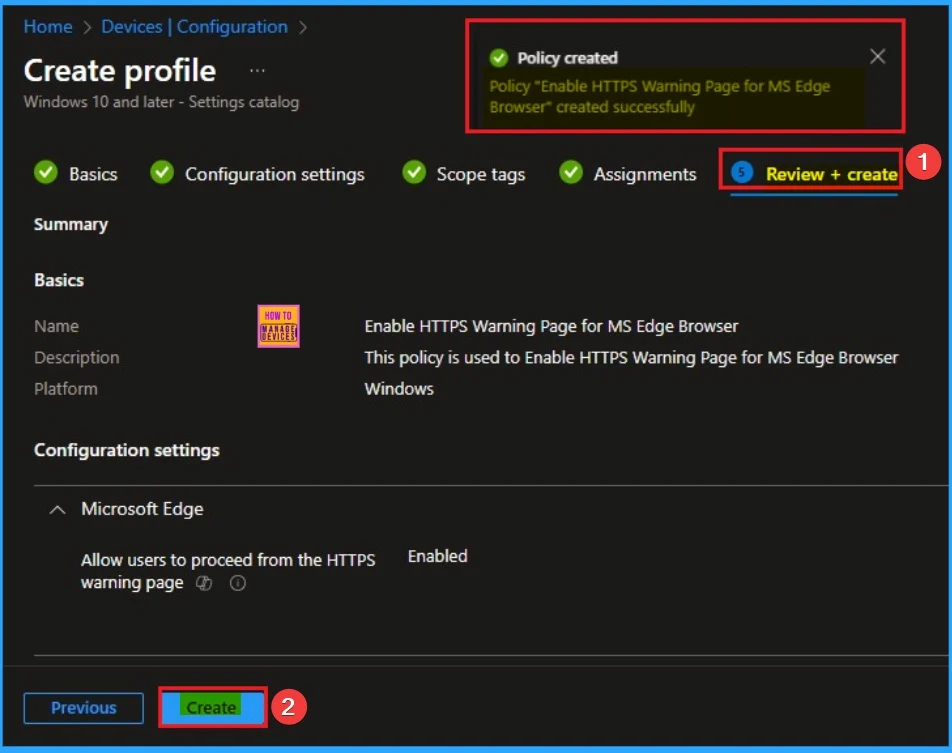
Device Check-in Status
After the policy is created, you can check the staus of the policy on Intune Portal. This status is shows the policy succeeded or not. Open the Intune Portal. Go to Devices > Configuration > Search for the Policy. Here, the policy shows as successful.
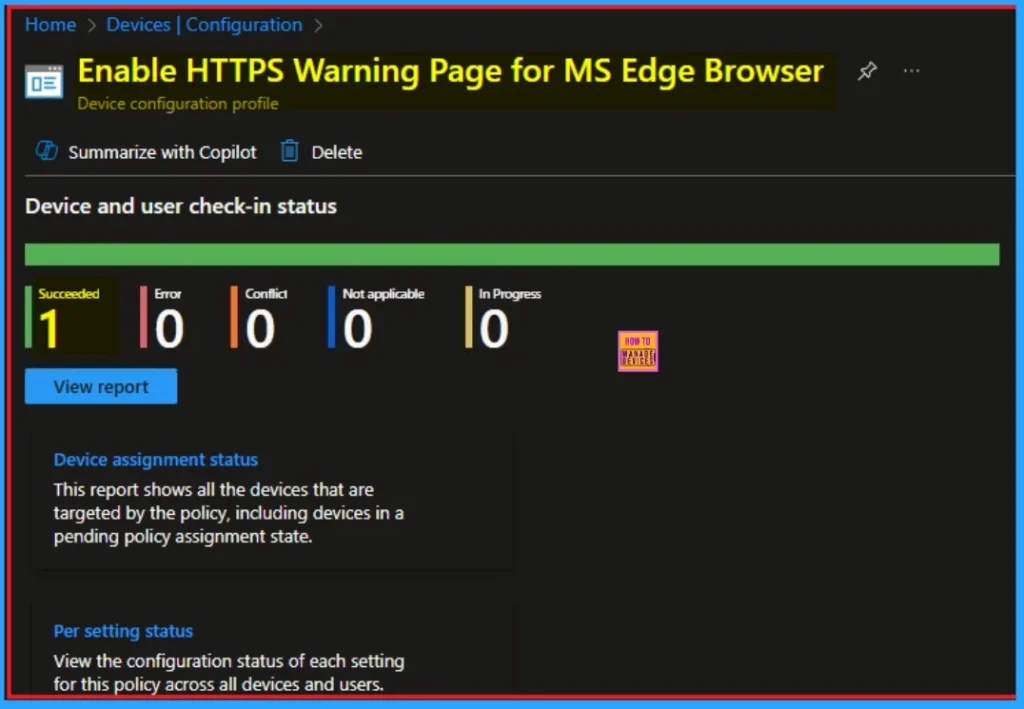
Event Viewer Details
Event Viewer helps you check the client side and verify the policy status. Open the Client device and open the Event Viewer. Go to Start > Event Viewer. Navigate to Logs: In the left pane, go to Application and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin
- Filter for Event ID 814: This will help you quickly find the relevant logs.
| Event ID Details |
|---|
| MDM PolicyManager: Set policy string, Policy: (SSLErrorOverrideAllowed), Area: (microsoft_edge~Policy~microsoft_edge), EnrollmentID requesting merge: (EB427D85-802F-46D9- A3E2-D5B414587F63), Current User: (Device), String: (), Enrollment Type: (0x6), Scope: (0x0). |
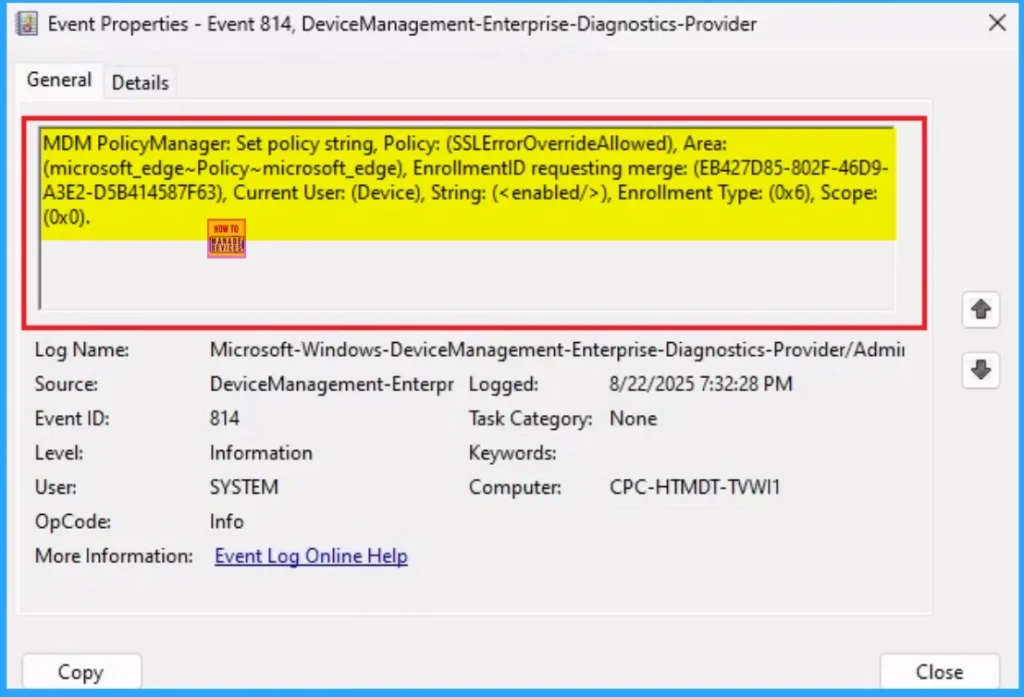
Removing the Assigned Group from these Settings
If you want to remove the Assigned group from the policy, it is possible from the Intune Portal. To do this, open the Policy on Intune Portal and edit the Assignments tab and the Remove Policy.
To get more detailed information, you can refer to our previous post – Learn How to Delete or Remove App Assignment from Intune using by Step-by-Step Guide.
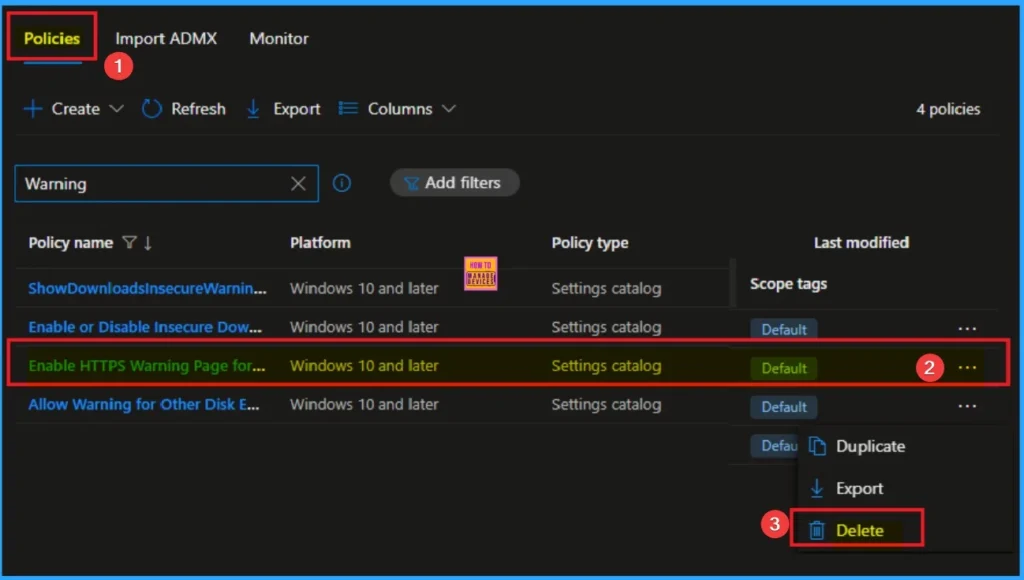
How to Delete HTTPS Warning Page Policy
You can easily delete the Policy from the Intune Portal. From the Configuration section, you can delete the policy. It will completely remove it from the client devices.
For detailed information, you can refer to our previous post – How to Delete Allow Clipboard History Policy in Intune Step by Step Guide.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


