One of the current challenges when moving from a group policy to MDM with Intune is the lack of support for group policy preferences (GPP). Apart from the ability to configure preferences that the user can override/customize, Intune also has some other useful features, such as network drive mappings.
There isn’t any native support for doing this within Intune today, although some MVPs and members of the MEM community have already documented some great alternative solutions. These solutions typically use a combination of PowerShell, Scheduled Tasks, etc., to map the drives at Windows sign-in.
In this post, I will share another way of mapping drives on Intune-managed Windows 10 devices without using anything other than MDM policy. Yes… Network Drive Mappings without PowerShell. The main requirements I had when I developed this solution were:
- Configure the drive mappings directly in Intune
- Control assignment of drive mappings via Azure AD groups
- Easily change/remove mappings without having to edit/re-deploy scripts
- Create mapped network drives without requiring network connectivity to the remote path
- Ensure mapped drives switch from “offline” to “online” when connectivity to the remote path is available
Table of Contents
About Network Drive Mappings
The configuration is stored in the registry when a network drive mapping is marked as persistent. This is so the drive mappings can be rebuilt at each user sign-in. It is possible to configure network drive mappings by simply creating the required registry keys/values.
Understanding this then opens up other mechanisms to configure the mapped drives without dependency on network connectivity to the remote path. This is particularly useful when users will enrol devices on the internet without any connectivity to the on-premises network or a VPN connection that may not be available immediately after enrolment.
Network drive mappings are stored in the HKCU\Network registry hive. There is a subkey for each mapped drive with a number of registry values within each key.
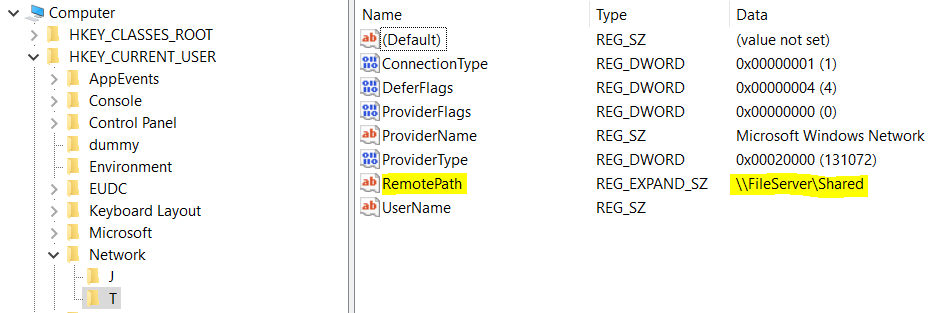
| Value Name | Type | Description | Default Value |
|---|---|---|---|
| Connection Type | REG_DWORD | The username is used to connect to the share. If the current user credentials are used then the value will be blank. | 1 |
| DeferFlags | REG_DWORD | Indicates whether the drive needs to be connected immediately at sign-in. If the mapped drive credential is the same as that of the logged on user or the credentials have been saved the value will be 4. If it is an alternative credential and the password has not been saved the value will be 1. | 4 |
| ProviderFlags | REG_DWORD | Indicates whether the RemotePath refers to a DFS root. If the RemotePath refers to a DFS root then the value is set to 1, otherwise set to 0. | 0 |
| ProviderName | REG_SZ | The name of the network provider being used to connect to the network drive. | Microsoft Windows Network |
| ProviderType | REG_DWORD | What type of Provider is used. For the Microsoft LanMan Provider the value will be 0x20000. | 0x20000 (131072) |
| RemotePath | REG_SZ | UNC path to the share. | |
| UserName | REG_SZ | Username |
All but two registry keys are the same for each mapped drive. The RemotePath value must be set to the correct remote path (UNC) for each drive. In addition, the ProviderFlags value should be set to 0 or 1 depending on whether the remote path refers to a DFS root.
Note: There have been some reports of network drive mappings failing since Windows 10 2004, and setting the ProviderFlags registry value (set to 1) seems to resolve the issue.
If you are happy using PowerShell to manage the drive mappings, you could just create the appropriate registry keys and values using PowerShell. Using this method, you could deploy a PowerShell script via Intune (user context) without having to worry about whether the user will have network connectivity to the on-premises network when the script is executed on the client.
ADMX-Backed Policy
However, there is also a way of creating the required registry keys and values via MDM policy, thanks to ADMX-backed policy support. I won’t go into the full details of ADMX-backed policy. If you want more insights into this, then there is some great documentation on docs.microsoft.com:
The ADMX-backed policy is the underlying mechanism the Administrative Templates configuration profile template uses in Intune. In addition to natively available settings via Administrative Templates, you can also configure other settings via custom policy in Intune. The complete list of ADMX-backed policies supported by Policy CSP is documented here:
It is also possible to ingest your own ADMX templates via Intune policy to configure settings for 3rd party apps such as Google Chrome, Adobe Acrobat, etc. Both the ingestion of the ADMX template and the configuration of the required settings have to be done using a custom policy. In fact, before the Administrative Templates feature shipping this is exactly how I used to configure hundreds of settings for Office 365 Pro Plus. As indicated by @MikeDanoski (Device Configuration Policy PM, MSFT) recently on Twitter the engineering team is working on a better way to manage any ADMX template via the UX.
In addition to 3rd party ADMX templates provided by ISVs, you can also author your templates to configure apps or other settings in the operating system. However, you cannot update all registry parts using the ADMX-backed policy. Some registry keys are blocked (by Microsoft) due to security concerns (\System, \Software\Microsoft, etc.). A complete list of those keys is detailed in this article:
Managing network drive mappings via ADMX-backed policy
In this scenario, we only need to update HKCU\Network, and as that isn’t on the blacklist, we can use ADMX-backed policy to create the required registry keys. There are two steps to deploy the ADMX-backed policy via Intune:
- Ingest the ADMX XML template (required for settings that are not native to the OS)
- Configure settings from the template
I have authored an ADMX template for network drive mappings, you can download a .zip file containing the ADMX and ADML files here. If you want to quickly test this outside of Intune just copy the ADMX file to C:\Windows\PolicyDefintions and the corresponding ADML file to C:\Windows\PolicyDefinitions\en-US. After copying the files run gpedit.msc to launch the local group policy editor. You will find the settings under User Configuration\Administrative Templates\Network Drive Mappings:
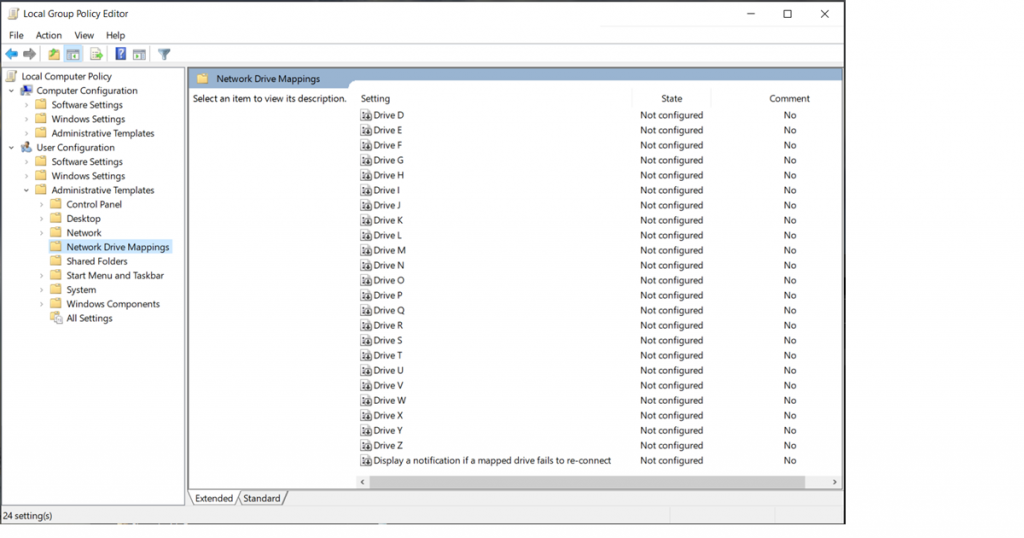
You can enable the policy by double-clicking one of the settings and specifying the remote path. The other registry values required to configure the network drive mapping are hard-coded into the ADMX template and will be created when the policy applies to the client.
You can test with any UNC path; it doesn’t have to be something valid that you can connect to. In this example, I am mapping drive Q to MyFileServerMyFileShare.
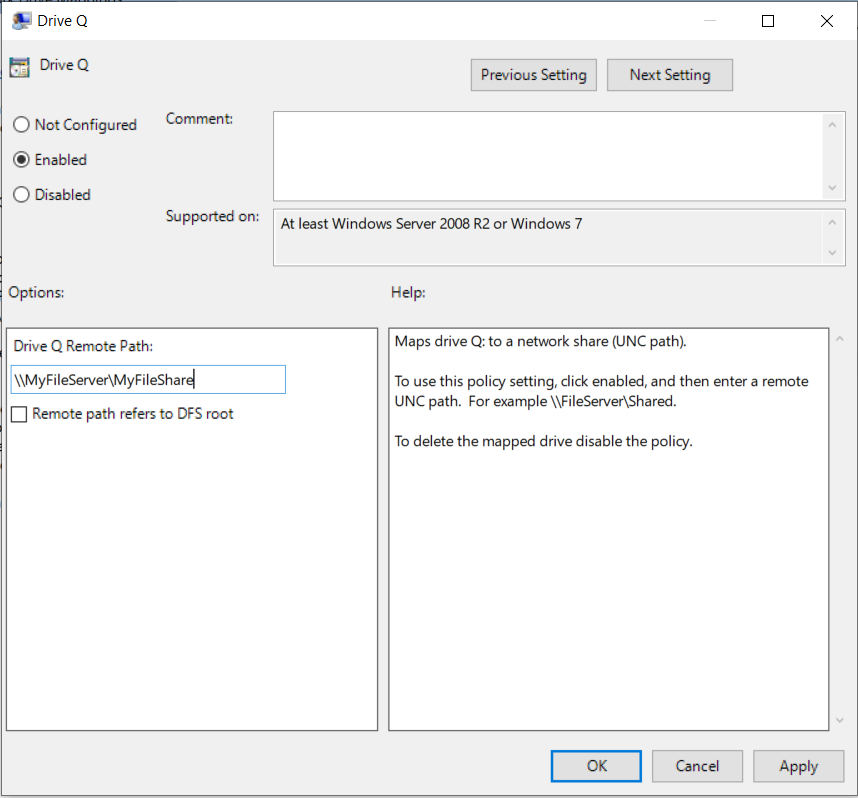
After saving the policy you will not see the drive in Windows Explorer immediately, you will need to sign out and back into Windows or restart the explorer.exe process via task manager.
After doing that you will see the mapped drive. If it is not a valid network path or the signed-in user cannot authenticate to it then you will see the drive in a disconnected state:
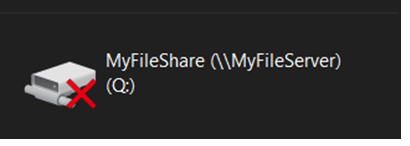
There is an additional setting at the bottom of the drive list called “Display a notification if a mapped drive fails to re-connect”. Setting this to “disabled” it prevents a pop-up notification from appearing when the user does not have network connectivity to the target remote path. I will detail more about this later in this post.
As we are writing registry keys outside of the \Software\Policies and Software\Microsoft\Windows\CurrentVersion\Policies registry hives, the settings are “tattooed” to the registry and will not be removed by simply changing the policy from “enabled” to “not configured”. The policy must be set to “disabled” to remove the mapped network drive from the client. Again, you can test this via gpedit.msc, changing the policy to “disabled” and restarting explorer.exe or signing out and back in will remove the mapped network drive.
How to manage network drive mappings via Intune configuration policy
Here is a step-by-step guide on configuring network drive mappings via Intune.
I recommend keeping your ADMX ingested templates in a separate profile to the associated settings, it just makes it easier to re-use the same template across multiple settings profiles.
- Download the ADMX template files from here.
- Extract the files somewhere onto your local drive (only the admx file is needed for ingesting via a custom profile).
- Create a custom configuration profile in Intune as detailed below:
| Configuration Profile |
|---|
| Platform: Windows 10 and later |
| Profile Type : Custom |
| Profile Name: ADMX Ingestion |
OMA-URI Setting
| OMA-URI Setting |
|---|
| Name : DriveMapping.admx |
| Description : ADMX template for Network Drive Mappings |
| OMA-URI: ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/DriveMapping/Policy/DriveMappingAdmx |
| Data Type: String |
| Value: {copy and paste the XML from DriveMapping.admx} |
- Save the profile and assign it to a device group containing your Windows 10 devices.
- Perform an MDM policy sync on a client to ensure the new ADMX template is correctly ingested.
- You can check this on the client in the registry:
HKLM\Software\Microsoft\PolicyManager\AdmxInstalled\{GUID}\DriveMapping\Policy\DriveMappingAdmx
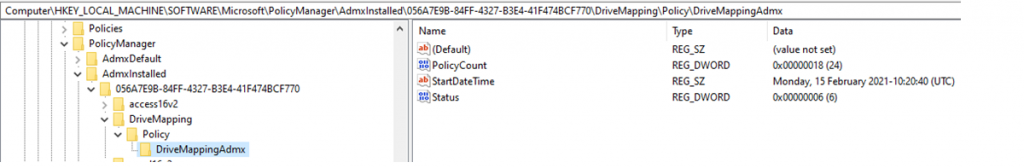
HKLM\Software\Microsoft\PolicyManager\AdmxDefault\{GUID}\DriveMapping~Policy~DriveMapping
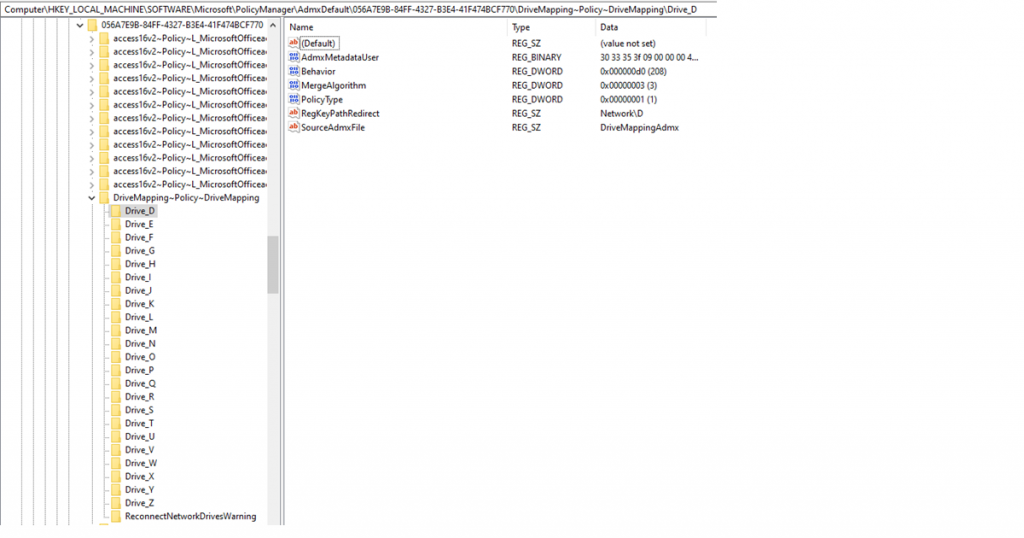
- Once the ADMX template is successfully ingested on the client, create another Intune custom profile to configure a network drive mapping. I have included an example below, just adjust the text in red to specify the drive letter and target remote path.
- If you wish to set the ProviderFlags registry value to 1 then also change the value for the Drive_Q_RemotePath_IsDFS” setting from “False” to “True“.
Configuration Profile
| Configuration Profile |
|---|
| Platform: Windows 10 and later |
| Profile Type: Custom |
| Profile Name: Network Drive Mappings |
| Name: Drive Q |
| Description: Maps Q Drive to a network share |
| OMA-URI: ./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/Drive_Q |
| Data Type: String |
| Value: <enabled/> <data id=”Drive_Q_RemotePath” value=”\\MyFileServer\MyFileShare“/> <data id=”Drive_Q_RemotePath_IsDFS” value=”False“/> |
Note: I have added support for the ProviderFlags registry value in a new version of the ADMX template uploaded on 13th November 2021. If you have downloaded a previous version and wish to test out this setting then please download the latest one and update your ADMX ingestion profile.
OMA-URI Setting
- You can add multiple OMA-URI settings to the same profile for additional drive mappings. For example, you could create all of the drive mappings for the Marketing department in a single profile and then assign that to a group containing the Marketing department users.
- Update 20/03/21 – Including an environment variable as a subfolder to the share in the remote path is possible. For example, \\MyFileServer\Users\%Username%. Thanks to Stuart Hoaen for fixing the ADMX template to make this work (see comments section below). I have updated the ADMX template linked to this post. Some reports setting the ProviderFlags value to 1 also helps resolve an issue where drive mappings using %username% revert to SYSTEM after a reboot. I have not been able to reproduce this issue myself; however, if you experience it, then please test with this setting.
- Assign the profile to a group of users requiring the network drive mappings.
- Again, perform an MDM policy sync on the client and monitor the registry to see if the settings are deployed successfully:
HKLM\SOFTWARE\Microsoft\PolicyManager\current\{SID}\DriveMapping~Policy~DriveMapping
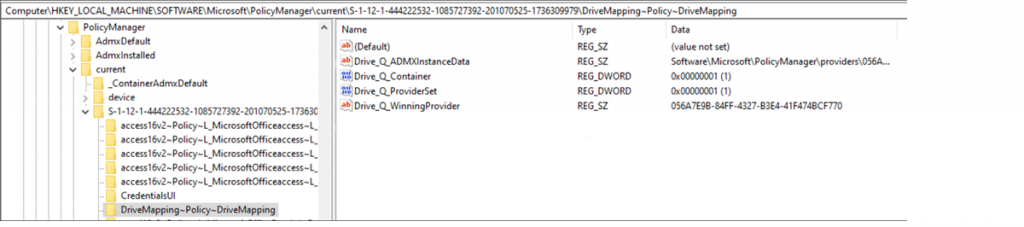
- Once the policy has been applied successfully, sign out and back in on the client (or restart the explorer.exe process), and the drive mapping will appear.
If the target remote path is not available immediately at the sign-in then the drive will appear in an offline state. However, simply double-clicking the drive to open it in Explorer will switch it to online as long as the network path is reachable and the user can authenticate to the remote file server.
Update 14/10/21: Thanks to Alex Durrant (@ADurrante) for pointing out that including special characters (e.g. &) in the remote path is possible. There are five special characters in XML, which are < > & ” ‘. As it turns out, both & and ‘ can be used as a shared name. You must encode the character correctly if you need to include either of those in the remote path.

For example, the path MyFileServerSales & Marketing should be entered into the OMA-URI value as MyFileServerSales & Marketing. Thanks, Alex!
Disabling the user notification for drive connection failures
If your users are remote and connecting over a VPN (that applies to many of us at the moment!), then by default, Windows will likely display a notification that the persistent mapped drive cannot be reconnected during sign-in. This can be annoying for end users but can be disabled using the additional setting I have included in the ADMX template. Just configure the following setting in a custom profile. I would recommend configuring this in a single profile that is assigned to all users rather than configuring it within each of your network drive mapping profiles:
| OMA-URI Setting |
|---|
| Name: ReconnectNetworkDrivesWarning |
| Description: Custom |
| OMA-URI: ./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/ReconnectNetworkDrivesWarning |
| Data Type: String |
| Value: <disabled/> |
In my experience of testing this I have seen the notification appear even when this setting is disabled, it does not appear to be that consistent. I have found that also setting the following system registry key seems to resolve the issue:
| Registry Key | HKLM\SYSTEM\CurrentControlSet\Control\NetworkProvider |
| Registry Value Type | DWORD |
| Registry Value Name | RestoreConnection |
| Registry Value | 0 |
As discussed earlier in this post, it is impossible to configure registry values within HKLM\System via ADMX-backed policy as Microsoft blocks it. Therefore, I usually configure this setting via PSH; you can deploy a single-line script to achieve this:
New-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\NetworkProvider -Name RestoreConnection -PropertyType DWord -Value 0 -ForceEditing and removing network drive mappings via ADMX-backed policy
You need to edit the UNC path in the OMA-URI setting to change the target remote path for a network drive mapping. The change will then apply to all clients whose profiles have been targeted.
However, as I mentioned earlier in this post, as the settings are “tattooed” to the registry, you must explicitly disable the policy setting for any network drive mappings you wish to delete. Simply unassigning the profile or deleting the OMA-URI settings will not remove the mapped drive from the client.
To delete a network drive mapping, change the value of the OMA-URI setting to <disabled/>.
| Name: Drive Q |
| Description:Maps Q Drive to a network share |
| OMA-URI: ./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/Drive_Q |
| Data Type: String |
| Value: <disabled/> |
You can delete the setting from your Intune profile once this has been applied to all existing clients.
I did discover some issues with deleting the registry keys/values when setting the policy to disabled. Whilst it worked perfectly via local group policy, it did not work via ADMX-backed policy. Therefore, the ADMX template sets the registry values to NULL strings or 0 rather than deleting them. The mapped drives will disappear from Windows Explorer, so the end-user experience isn’t impacted. Changing the policy back to enabled and specifying the remote path will re-apply the correct registry values, so there are no issues with deleting a mapped drive and then re-adding it later.
Happy network drive mapping
Resources
- Understanding ADMX-backed policies – Windows Client Management | Microsoft Docs
- Support Tip: Ingesting Office ADMX-Backed policies using Microsoft Intune – Microsoft Tech Community
- ADMX-backed policies in Policy CSP – Windows Client Management | Microsoft Docs
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here – HTMD WhatsApp.
Author
Mark is a Modern Workplace Solutions Architect based in the UK with more than 23 years of experience in IT. He has been working in enterprise desktop management since the start of his IT career, focusing on OS deployment with SCCM/MDT. Since 2015, he has worked on enterprise mobility and modern Windows management with EndPoint Manager/Intune. Twitter -> https://twitter.com/Mark_Thomas73.

OMA-URI Setting
Name Drive Q
Description Maps Q Drive to a network share
Data Type String
Value
Hello
There is no OMA-URI string in this part but there is in all the other examples. I cannot get this to work
Hi Adrian, thanks for testing this out and spotting the issue in the blog post. I have fixed that for you now :-).
Hi Mark,
It fails when mapping the drives as per the blog
ERROR CODE
0x87d1fde8
ERROR DETAILS
Remediation failed
Any ideas
Hi
I am new to this ADMX. can you please explain what do I need to put in the value {copy and paste the XML from DriveMapping.admx}?
from the Zip file, I get three files 1. drivemapping.adml 2. Drivemaaping.admx 3. example settings.txt
i copies Drivemaaping.admx and pasted in intune that work but i do not see any drive letters
Please Help
Hi Adrian
I think it might be the text formatting due to copying and pasting the setting value from the blog post. I will try to fix that but in the meantime just paste the value into Notepad and then overtype the double quote characters (“). Then copy that text from notepad into the setting in the MEM console.
Mark.
Amazing! Thanks so much for sharing this Mark!
Is it possible to set the drive display name using this?
Hi Anders,
Unfortunately no it’s not possible to do that via ADMX backed policy. The display name is stored in a different part of the registry (which is updatable via ADMX) but the reg key name is based on the UNC path. To the best of my knowledge it’s not possible to dynamically adjust the reg key the policy will write to based on the remote path value you entered.
I haven’t tried this but I believe it is possible to achieve the same thing by placing a desktop.ini file in the root of the file share. That will work if you are happy with all users connected to the same share having the same display name. The file needs to have either system or read-only attributes applied – I would use attrib +S +H +R to make it system, hidden and read-only.
I am not sure of the structure of the desktop.ini file, I will try and look into it a bit more and see if I can get it working. If you manage to do that yourself let me know :-).
Thanks, great suggestion!
I found the formating of the desktop.ini file. 🙂
[.ShellClassInfo]
LocalizedResourceName=Name
Thank you so much, Thomas! This is exactly what I have been looking for. I’ve tried numerous powershell solutions for this, but it’s been a nightmare to edit drives later.
You are very welcome! Thanks for the feedback 🙂
Thanks for this – worked brilliantly for me.
Follow up question (can’t find any answer anywhere) we have private areas for staff and these were traditionally mapped by “\\Server\%username%”. This works in the sense that the drive will appear mapped to the correct letter in File Explorer, but it throws back an error “Network resource or device is no longer available. This connection has not been restored”
Should the %username% work dynamically in this? Or am I on to a loser here..
Thanks
Thanks for the feedback Steven, great to hear it worked for you. I am not sure that variables such as %username% would work in this scenario, although I have never tried it. I assume that when mapping the drive through the normal windows process it resolves the variable to the value and then the drive is mapped using that e.g \\server\steven.
Hi. Thanks very much for this valuable resource. I had the same question as Steven McAuley above about using variables in paths. Like Steven I found it doesn’t work.
However, I’ve found this is possible by amending the ADMX file as follows….
Find the section within each and change the item to include an expandable=”true” flag. For example…..
After doing this, variables in drive map paths are resolved.
Hi. Thanks very much for this valuable resource. I had the same question as Steven McAuley above about using variables in paths. Like Steven I found it doesn’t work.
However, I’ve found this is possible by doing the following….
Find the element section within each policy section and change the text item to include an expandable=”true” flag. For example…..
text id=”Drive_Q_RemotePath” valueName=”RemotePath” expandable=”true”
After doing this, variables in drive map paths are resolved.
Thanks for the feedback Stuart! Yes that is correct it does seem that the expandable flag enables environment variables to be expanded to their real value. I will test this out and update the ADMX template and blog post. All kudos to you of course .
Hi Mark,
When we are testing this and using %username%, it shows up initially with the correct name (firstname.lastname). However, after a reboot, this particular user drive shows “SYSTEM” instead of firstname.lastname. We have the config profile assigned to a user group. Did your testing show something similar?
It appears this fixes it…my same response to another comment up above is below this. I did not add this item for every drive letter in my ADMX ingest, only the one where we are using a variable in the RemotePath. I didn’t know how that would otherwise behave since the other network drives are working normally without specifying it:
For those that are trying to use a variable like %username% it appears that adding the item for ProviderFlags = 1 inside the enabled tag within admx ingest for the drive letters that you need fixes this issue. This will ensure the ProviderFlags reg value exists for that drive letter.
Reference: it-admins.com/windows-10-build-2004-20h1-smbv1-network-drives-not-connecting/
Hi Greg,
I am doing some research on this and have seen the same articles re ProviderFlags, SMB v1 and Windows 10 2004. As far as I know (at least historically) ProviderFlags should only be set to 1 if the remote path is hosted by DFS. Whether this is somehow working around the issue with the use of %username% I am not sure (I have never been able to repro that issue myself).
I am going to do some testing and will likely update the ADMX to add support for ProviderFlags. It makes sense to include this and then it will be easier to control whether this is set to either 0 or 1 via Intune policy. The value could be set differently for each mapped drive.
I will update the blog post when I have done that, hopefully later this week.
Thanks for your feedback.
Mark.
Hi Greg,
I have updated the blog post and ADMX template today (13th November) to add support for the ProviderFlags registry value. You can now set this via Intune policy on a per drive mapping basis. Have a read of the blog post and let me know if anything isn’t clear.
Thanks
Mark.
Hi Mark,
Any ideas why after I push the “Configuration Profile” to enable the mapped drive of my choice the “HKLM\SOFTWARE\Microsoft\PolicyManager\current\{SID}\DriveMapping~Policy~DriveMapping” path does not appear? I was able to push the ADMX policy itself easily and confirm it’s entry in my registry.
Also when I load your ADMX file on my machine I receive the following error after opening the local GP editor, “Invalid value ‘True’ for attribute expandable. File C:\Windows\PolicyDefinitions\DriveMapping.admx, line 79, column 81.”
Thanks for the help.
Hi Calvin, I think there are two separate issues. I recently updated the ADMX template to add support for using variables and forgot to check that it worked via the local group policy editor :-). I have now fixed that issue so if you re-download the .zip file and use that .ADMX you will find that it does now load in GPEdit.msc. However even with the previous version your configuration profile should have still worked. Did you spot the comment above regarding the double quote characters? If you have copied the text from the blog post and pasted that directly into Intune then that might be the issue. Paste the text into Notepad first and overtype the double quote (“) characters – then copy that text from Notepad into the Intune console. It’s just a formatting issue from the blog post. Let me know if that helps.
Hi Mark,
Great post, although I’m also getting the Remediation failed error. Can I just confirm, should these be double quotes (which mine are) or not?
Hi Jan, yes they should be double quotes. The issue is caused by copying and pasting the text from the blog post. I have just added a .txt file to the .zip file which includes the correct settings. If you download the .zip again and check the “example settings.txt” file you can copy and paste the values directly from there (changing the drive letter as necessary). That will avoid the formatting issue when copying from the blog post. Clear your cached images and files from your browser cache before re-downloading the .zip just to make sure you get the latest one.
Very helpful.
After seeing the item:
Find the element section within each policy section and change the text item to include an expandable=”true” flag.
I wondered why it worked, then I remembered that in the registry there is data type of
REG_EXPAND_SZ which was engineered expressly to resolve %variables%, I suspect that changing expandable=”true” changes the reg data type written to the registry to REG_EXPAND_SZ
RegKey data types
[ REG_SZ | REG_MULTI_SZ | REG_EXPAND_SZ |
REG_DWORD | REG_QWORD | REG_BINARY | REG_NONE ]
Hi John,
Thanks for the feedback. Yes that is correct, setting the expandable property switches the registry value from REG_SZ to REG_EXPAND_SZ.
Mark.
Hi Mark,
Thank for your work.
Probably i found a problem with the username variables
First login after deploy the policy with your step by step it works fine.
But the second login the mapped drives with uservariables not work anymore.
In the network registry node there is: \\share\%username%\ but in the explorer appears \\share\SYSTEM
My idea is, that the policy is running with the system user and not with the login user. Then it will remap the mapped drive.
Have you an idea to solve this?
Hi Daniel,
Oh… that’s not good! I can’t be 100% sure how many times I logged on / rebooted when I tested this out but I don’t recall seeing that issue. I will test this scenario again and see if I can reproduce the problem. It might take me a few days due to other work commitments but I will get back to you.
Mark.
Hi Daniel,
Sorry for the delay in getting back to you. I have now re-tested this and the use of %username% as detailed in the blog post does work OK, it does not seem to revert to SYSTEM. I have rebooted several times, sync’d with Intune etc and all seems OK. However I notice you are using \\Server\%UserName%. I did not have that much success with that in my own testing and recommend using the variable as a subfolder of the share. For example \\Server\Users\%UserName%. Also are you assigning the ADMX ingestion profile to a group containing devices and the drive mapping profile to a group containing users? The drive mapping policy is per-user and I would recommend assigning that to a user group.
Hope that helps.
Mark.
Firstly, thank you for this great solution! I can confirm that first time it maps fine to \\server\share\%username%, but second reboot it is mounted as SYSTEM. Is there a solution to this?
This was reported by someone else but I have been unable to re-produce the issue in my own testing. I have rebooted several times and the mapping remains as %username%. How have you targeted the profile containing the mapping? Is it only targeted to a group containing users (and not devices)?
Yes its targeted to user group
I have the same Problem with %username% after reboot it is mapped to System. I assigned it to a User Group. Is there a Solution? Should I assign it to a User or DeviceGroup?
I recommend assigning the profile to users. As I have mentioned in previous comments I have not been able to reproduce the issue myself but as a few people are having the same issue there is clearly an issue somewhere. To be honest this isn’t a scenario I use in production myself and was not part of the blog post when I originally wrote it.
I added the support for environment variables based on feedback and my own testing but this does now appear to be unreliable. Unfortunately I don’t currently have a solution to this as I cannot reproduce the same error myself. What version of Windows 10 are you using?
Thank you for your Answer, we use Windows 10 Enterprise 20H2
OK… I have only tested the solution with 1903, 1909 and 2004 so far. I don’t believe 20H2 should make any difference but that is something I can try.
We have also 20H2 in use
OK, thanks for also confirming. I will test 20H2 in the next few days and see if I can repro the same issue.
Thank you for your testing.
Yes, we have assigned to a user group and we have also Windows 20H2 too.
the path was an example, but i belive it make not any difference.
Our plan is: Map a local synchronized sharepoint path like \\localhost\c$\users\%username%\Onedrive\Documents
But i have no idea why when the gpo first apply it works and after the second login system is the username.
I tested the investigation with a clean system but the same effect in a education environment.
Maybe there exists some special default settings in a education environment.
Hi Daniel,
I still cannot reproduce this issue on 20H2. I have just tested the example you gave of mapping to the local OneDrive folder and it works fine and persists as the user after several reboots. I am not sure what is happening for you and the other people that have reported this but there must be something else going on. It might be another policy you have set or maybe the drive mapping profile is somehow failing remediation.
Are there are errors in your MDM logs (Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin)? Does the drive mapping profile show as successful for the device/user in Intune?
Mark.
Hi Mark
I found no information in the logs or in the Intune Webinterface. Every second login the uservariable is changing to system user.
Now, i have programmed a c# console program which works with parameters in the webinterface. converted to a intunewin format. I can publish drive mappings from the apps site.
The program is writing the values in the user context like your investigations. This solved all my problems.
Thank you, for inspring me, do realize this solution.
Hi all,
I’ve the same issue after the second reboot.
Try to change the value for the DeferFlags reg to 1.
It worked for me.
Thibaut
Hi Thibaut,
I still need to try and repro this and understand the difference between 20H1 and H2 as the behaviour seems to be different. DeferFlags should be set to 4 if the current logged in user credentials are used (as far as I know). Would be interesting to know if this fixes it for other people but I will need to do some more investigation before changing the ADMX template. You can do this yourselves in your own ADMX ingestion profile if you want to do some testing.
Mark.
Hi Mark,
a very basic question by a newbie:
I would like to use your method connecting a folder on a server as a network drive. The server is not part of a domain, so I have simply created a local user account with a password, which has the rights to access the folder.
My question is: how is it possible to add username and password with your method? Can I somehow add it with the UNC?
Thanks for your help.
Markus
Hi Markus,
Whilst it is possible to specify a username in the registry settings my current ADMX template doesn’t allow you to configure that (it’s hardcoded to a null value). However it’s not possible to specify the password via the registry, users would have to enter the password and this is then stored in the Windows Credential Manager. So even if I updated the ADMX to cater for the username you would have to tell all of the users the password and they would need to enter it.
To be honest what you are looking to do isn’t a very secure solution and best avoided. If you are setting up something new and don’t currently have any on-premises AD infrastructure I would suggest using a cloud based storage solution such as Azure Files.
Mark.
Thanks, Mark. I will probably go with Azure Files.
Thank you for all the work you put into it. Once I resolved the self-induced syntax error (dammit UTF-8), it worked flawlessly.
That’s great to hear, thanks for your feedback David!
Hi Mark,
Thanks a lot !!
For anyone wishing to change drive label, an option is;
In intune, create a win32 (xxx.bat) app to call the xxx.vbs file
xxx.bat – cscript.exe xxx.vbs
xxx.vbs (see below)
Option Explicit
Dim objNetwork, objShell, objUNC
on error resume next
‘ Section which actually (re)names the Mapped Drive
Set objShell = CreateObject(“Shell.Application”)
objShell.NameSpace(“H:”).Self.Name = “Drive name”
Hope it helps
Hi Chudi,
I’d like to rename all our drives. Can you go into a bit more detail how to do it?
Thank you.
Any ideas why the ReconnectNetworkDrivesWarning does not work as you intended, though? While it indeed seems to apply correctly as per Intune, local group policy editor still show it as “Not configured”.
It does work, you won’t see the setting show as configured via local group policy (that’s normal). If you are still seeing the warning pop-up have you also set the HKLM setting via PowerShell (as per the blog post)?
I have not (yet), but is then the OMA-URI setting still needed in addition?
I usually configure both just to be sure but feel free to test it with just the PowerShell configuration.
I am getting issues mapping a user drive. It works find when I import the admx locally to a pc and configure through gpedit but when I push it out through Intune it gives me a Remediation failed.
This is what I am putting in the policy:
./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/Drive_N
But I am getting no luck.
Any Ideas?
Looks Like it filtered what I pasted
”
“
data id=”Drive_M_RemotePath” value=”\\kes-store-001\%Username%$
Hi Adam,
I am not sure if you saw this in the comments above but if you copied the example OMA-URI setting from the blog post and pasted that directly into the MEM console then there is a bit of a formatting issue with the ” character. Just delete/replace the ” characters directly in the MEM console. That might fix the remediation failed issue for you.
Mark.
Looks Like it filtered what I pasted
”
“
Hi Mark,
I am all of a sudden getting this error message at a customer;
“An error occured while reconnecting to
Microsoft Windows Network: The local device name is already in use
The connection has not been restored”
Any idea why this is happening? I’ve deployed this for a couple customers, and it has been working really great so far, but all of a sudden, this one user keeps getting this error. I’ve tried deleting everything and re-deploying the policy with no luck. The first time I connect to the drive, it works. But after a reboot, it the problem reoccurs 🙁
/Morten
Morten, I ran into the same thing, and in my case it was a problem with Windows Hello for Business, and specifically a misconfiguration of my Certificate Authority publishing its revocation list.
Once I resolved the revocation publishing issue, the drives mapped without error. I don’t know how well URL posting works in these comments, but check out AnubhavinIT’s YouTube channel, and specifically his “How to enable on-premise resources access from Azure AD joined Windows 10 using Hello for Business” video, that is a fantastic resource.
Hi Morten, apologies for the delay in replying. I am just catching up with some of the comments that have been posted here. I agree with Jon’s reply and have seen the same when WHFB SSO isn’t working correctly. Hopefully you have managed to sort it out.
Hi Mark
Thanks for the article. i am new to this ADMX policy. i have followed your first step to do it via Gpedit.msc and it works fine. When i try to do it on intune it only gives me
drivemappingadmx folder. It does not give me letter for the drive.
What do i need to put in this {copy and paste the XML from DriveMapping.admx}
Hi Mark,
Thanks for the details steps for Network Drive Mapping.
Both ADMX policy and network Map profile working as expected from Intune ,but when network drive profile is applied on device, it is showing as Red cross mark, after opening the drive it is showing online and cross mark gone. Please help on this. and how to disable the notification when it is not connected.
Can you please give some example’s to add multiple Drives into single profile.
Hi Bharath, apologies for the delay in replying. I have seen the issue with the red cross when the device does not have direct line of sight to the file server when the policy applies (e.g before VPN is connected).
If you want to add multiple drive mappings in a single profile you just add multiple OMA-URI settings into a single custom profile in Intune. Just click the “add” button to add an additional setting into the same custom profile before saving it.
Hi Mark,
Thank you for this write up, it’s been so valuable. I have experienced the same issue with the %username% variable mapping with System account after the device is reboot as described by others above. My system is running 21H1 and wondering if you had been able to reproduce it
Hi Jerry,
Thanks for raising this, it seems that we also have the same issue at our environment as well that the %username% variable maps it with System account after the reboot. We are also running with 21H1 and was wondering if we were able to find a fix for the same.
Best
Shwetank
For those that are trying to use a variable like %username% it appears that adding the item for ProviderFlags = 1 inside the enabled tag within admx ingest for the drive letters that you need fixes this issue. This will ensure the ProviderFlags reg value exists for that drive letter.
Reference: it-admins.com/windows-10-build-2004-20h1-smbv1-network-drives-not-connecting/
Hi Jerry, I have not managed to repro this yet (on 21H1 or 21H2). There was a suggestion by Thibault above that changing DeferFlags to 1 might fix the issue. You can do this in your own ADMX ingestion profile. If you can do that and then provide some feedback as to whether it helped that would be great. Thanks.
Hi,
We have a user’s profile drive that map to each user and is set up in AD under profile of each user’s account. If we go with Intune is there a way to do it like \\server\share\%username% so each user can see his own drive. Any powershell script or with intune? Advise please.
Hi
I would like to ask if i have to add the domain on the %username%. i have this AD user but when we access the mapped drive I logged in with this \\server\share\domain\%username%.Is those kay?like for example
user credentials is
testdomain\Name.Username
password
this is the format. is it possible?
thanks
Hi Darren, %username% is just a way of including the users’ login ID as part of the remote path. So for example if each user has their own personal share which uses their login ID as the share name then you can configure a single policy which will work for all users. For example you have the shares \\MyFileServer\Users\Darren and \\MyFileServer\Users\Mark then using the value \\MyFileServer\Users\%UserName% will work for both Darren and Mark as the path will dynamically adjust based on their login ID.
It’s not possible to include credentials such as their password in the setting. The solution assumes that the logged in user has access to the file share.
Anyone used this in a shared device like a lab environment? I found that if the setting profile was assigned to user groups, it only target devices with primary user assigned or user driven enrolled, and devices without primary user or self deployed would stuck on pending. If I assign it to device groups, only the user logged in gets the mapping after the profile is applied, any subsequent users won’t get the mapping.
Hi Mark,
If a user disconnect the drive by mistake then its not remapping after reboot or rerunning the policy from system.
Thanks,
HI Mark,
I have same situation.
Thanks
R.Mohan
Yes so I think this is probably going to be a limitation of the solution. If you manually disconnect the drive Intune will still think the policy is enforced on the client and won’t re-apply it. I will test this out myself but I don’t think there is a solution to it right now.
Hello, I’m receiving the following errors when attempting to push one of the network drives:
MDM PolicyManager: Set policy string, Policy: (Drive_L), Area: (DriveMapping~Policy~DriveMapping), EnrollmentID requesting set: (F2F701D4-1918-4E9D-B938-9533B66FA8FC), Current User: (S-1-12-1-577647526-1220497481-901012619-1763064298), String: (
<data id=”Drive_L_RemotePath” value=”“/>), Enrollment Type: (0x6), Scope: (0x1), Result:(0x80004005) Unspecified error.
MDM ConfigurationManager: Command failure status. Configuration Source ID: (F2F701D4-1918-4E9D-B938-9533B66FA8FC), Enrollment Name: (MDMDeviceWithAAD), Provider Name: (Policy), Command Type: (Add: from Replace or Add), CSP URI: (./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/Drive_L), Result: (Unspecified error).
The drive path is correct.
Same issue here, have you found any resolution?
Hi Neil, as per some other comments above have you just copied and pasted the sample OMA-URI values directly from the blog post? This won’t work due to double quotes characters. Just overtype the double quotes to make sure they are formatted correctly. I also included a .txt file in the .zip file with the sample OMA-URI values – you can also copy them from there instead.
However the error does not look right as the remote path value is empty. It is hard for me to tell without seeing your policy settings.
Mark.
How to manage them Windows Hello. As we have pin enabled for autopilot devices we are facing challenge to mapping. Although it get mapped successfully if we use user name and password
Hi RJ, this isn’t an issue with the network drive mapping via MDM – that is working for you. You would have the same issue if you mapped the drive manually. If you have a “cloud only” deployment of WHFB then users will not get SSO to on-premises resources when signed in with the WHFB provider (PIN/Bio). However it will work when signed in with their password.
Take a look at the MS WHFB docs – what you need to do varies depending on whether you are hybrid domain joined or Azure AD joined and what version of Windows Server is used on your domain controllers.
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-planning-guide
Unfortunately the implementation can be complex and the MS docs don’t cover all of the potential issues. However you will find plenty of other resources to help you – just search the web for “Intune WHFB SSO” :-). I can confirm that when you have this in place then this solution for mapping the drive will work with WHFB, just as it does when signed in with a password.
I’m curious why you have the ProviderType locked to 0x2000 (8192) while ProviderName is Microsoft Windows Network which is actually 0x20000 (131072)
Hi Ryan, I am just looking into this and it could be an error in the ADMX. 0x20000 (131072) is for the Microsoft LanMan provider and should be the value that is used, although the solution seems to work as it is. I will do some testing and update the ADMX if needed.
Hi Ryan,
I have updated the ADMX template (13th Nov) to fix this issue. Thanks for spotting this!
Mark.
Hi, thank you very much for this article. It helped me a lot and thankfully works perfectly. I am inspired.
I still have a question… does someone know, how I can pin those drives to the quick access in the Windows explorer?
Hi Joyce,
Thanks for your feedback. I am able to just right-click the drive in Windows Explorer and select “Pin to Quick Access”. Does that not work for you?
Mark.
Hi MarK,
At first, thanks for your work!
I start today with your guide for mapping the drives
Actually, i only have deployed successfully the ADMX
But i’m getting an ERROR CODE 0x87d1fde8 with drive profile:
– I have Assigned to a USER group ( I have also tried with a device Group, and with i have the same error)
– I have tried changing the IsDFS value from False to True, and with both value i have an error.
The details of my drive are:
– Name: O
– \\domain.local\Depart
The details of the OMA-URI Settings that i have used:
– Name: Drive O
– Description: Maps O Drive to a network share
– OMA-URI: ./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/Drive_O
– Data Type: String
– Value:
Any suggestions of things to try to solve the error?
Thanks in advance
Hi,
I’m also having issues mapping the drive.
I used the string value out of the txt file but no luck.
Anyone has a solution for this ?
Thanks in advance.
MDM ConfigurationManager: Command failure status. Configuration Source ID: (2C3B054D-8140-40B7-ABB7-2B02906D270D), Enrollment Name: (MDMDeviceWithAAD), Provider Name: (Policy), Command Type: (Add: from Replace or Add), CSP URI: (./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/Drive_M), Result: (Unspecified error).
MDM PolicyManager: Set policy string, Policy: (Drive_M), Area: (DriveMapping~Policy~DriveMapping), EnrollmentID requesting set: (2C3B054D-8140-40B7-ABB7-2B02906D270D), Current User: (S-1-12-1-1428649110-1202822877-2883627167-330870591), String: (
), Enrollment Type: (0x6), Scope: (0x1), Result:(0x80004005) Unspecified error.
Hey,
Just letting everyone know the issue I had was solved over night.
I adjusted the ” ” yesterday but it did not work right away. This morning all good!
Thank you Mark for this blog post 😉
Great news Glenn! Glad it’s working for you and thanks for the feedback.
What do you mean by adjusted the ” “? I’m having the same issue.
Just to make it more clear, you need to remove all spaces and returns before
Also note that it can take 5 minutes before Azure actually pushes the new saved version of your OMA-URI, as I experienced. Even after pushing the Sync button in Windows. Then restarted explorer.exe and got my network drive Q.
HI Mark,
i have test this and not works.
The firts step work fine, and i can check adminsalled and admxdefault shows like you told. But in policymanager\current i dont have any SSID, only shows “device”
In Intune the firs admx is deployed fine, but the secon, with the letter Q for instance, fail. I don’t know why. Have you any idea?
And, when you says that “copy XML of form Drivemapping.admx is open this lastone in notepad and copy exactly, no?
i hope help plis. Is very important for me.
Good morning,
I cant seem to get this to work at all.
I think I have tried everything in here 🙁
String:
Drive_W [./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/Drive_W]
Error -2016281112 (Remediation failed)
The setting i applied is as follows:
anyone got any ideas?
Hi Mark,
Can this also be used for mapping an Sharepoint DocLib as network drive?
Many thanks and best regards,
Ruediger
I’m experiencing bizarre behavior where Microsoft Edge is launched on sign in. Any reason this would happen?
Hi Matt, I have read something about this on Twitter recently. It’s nothing to do with the drive mappings it seems to be a bug in Edge and will be fixed by an update. Some more info here – https://www.reddit.com/r/MicrosoftEdge/comments/s06vuy/edge_starts_as_soon_as_i_power_on_the_pc/
Hi Mark,
Thanks for your time and efforts putting this together – has proven a nice tool to have in the back pocket when customers need to support legacy solutions such as mapping network drives 😉
We’re seeing an issue where upon wiping an Azure AD Joined (cloud only) device via Intune device wipe, the mapped drives never come back.
They are successful first time but they disappear on reprovision and looking in EventViewer I can see the generic unspecified error when the policy tries to apply. There are no reg keys with the configuration and looking through ProcMon wasn’t much help.
Still looking but wondering if there is something we’ve missed?
First run through of a brand new device works OK but subsequent wipes just show the generic error in Intune and no drive mappings appear in ‘This PC’.