Let’s discuss Complete Checklist to Enforce Microsoft’s 14 Non-Negotiable Intune Security Controls. Microsoft provide security configuration guidance for Microsoft Intune that helps organizations strengthen their overall security posture.
These security posture helps IT admins to implement Zero Trust-aligned security controls across tenants using Microsoft Intune. Secure Tenant is the foundational layer of security for your entire mobile device and endpoint management environment.
The Security Tenant session establishes the baseline standards for governance, identity, and compliance within your Microsoft Intune environment. Its main goal is to eliminate risk from unmanaged or non-compliant devices and ensure that administrative access follows the principle of least-privilege.
On the Secure Tenant Session you can see 14 specific checks, grouped into four core pillars. They are Governance and Least-Privilege Access, Device Enrollment and Onboarding, Cross-Platform Device Compliance, and Advanced Security Integration and Insights.
Table of Contents
Complete Checklist to Enforce Microsoft’s 14 Non-Negotiable Intune Security Controls
As mentined, 4 core pillers with 14 specific checks. The Governance and Least-Privilege Access piller ensures that your administrative structure is secure and follows Zero Trust principles, particularly concerning who can manage what.
- Device Enrollment and Onboarding pillar secures the process by which a device enters and is recognized by your environment.
- Cross-Platform Device Compliance is the most critical pillar, defining the baseline security posture a device must meet to be trusted.
- Advanced Security Integration and Insights pillar integrates specialized security services for a higher level of protection and visibility.
| 14 Pillers | Minimum License Requirements |
|---|---|
| Scope tag configuration is enforced to support delegated administration and least-privilege access | Microsoft Intune Plan 1 |
| Device enrollment notifications are enforced to ensure user awareness and secure onboarding | Microsoft Intune Plan 1 |
| Windows automatic device enrollment is enforced to eliminate risks from unmanaged endpoints | Microsoft Intune Plan 1 Microsoft Entra ID P1 (for Conditional Access) |
| Compliance policies protect Windows devices | Microsoft Intune Plan 1 |
| Compliance policies protect macOS devices | Microsoft Intune Plan 1 |
| Compliance policies protect fully managed and corporate-owned Android devices | Microsoft Intune Plan 1 |
| Compliance policies protect personally owned Android devices | Microsoft Intune Plan 1 |
| Compliance policies protect iOS/iPadOS devices | Microsoft Intune Plan 1 |
| Platform SSO is configured to strengthen authentication on macOS devices | Microsoft Entra ID P1 (for Conditional Access) |
| Defender for Endpoint automatic enrollment is enforced to reduce risk from unmanaged Android threats | Microsoft Intune Plan 1 |
| Device cleanup rules maintain tenant hygiene by hiding inactive devices | Microsoft Intune Plan 1 |
| Terms and Conditions policies protect access to sensitive data | Microsoft Intune Plan 1 |
| Company Portal branding and support settings enhance user experience and trust | Microsoft Intune Plan 1 |
| Endpoint Analytics is enabled to help identify risks on Windows devices | Microsoft Intune Plan 1 |
- Intune Zero Trust Implementation using EPM and MAA
- How to Find Windows Devices without Compliance Policy using Intune Copilot Explorer
- How to Detect Android Enterprise Rooted Devices using Intune Compliance Policy
Scope Tag Configuration
Enforce scope tags and role-based access control to limit admin access by role, geography, or business unit. If Intune scope tags aren’t properly configured for delegated administration, attackers who gain privileged access to Intune or Microsoft Entra ID can escalate privileges and access sensitive device configurations across the tenant.
Remediation Action
Use Intune scope tags and RBAC roles to limit admin access based on role, geography, or business unit
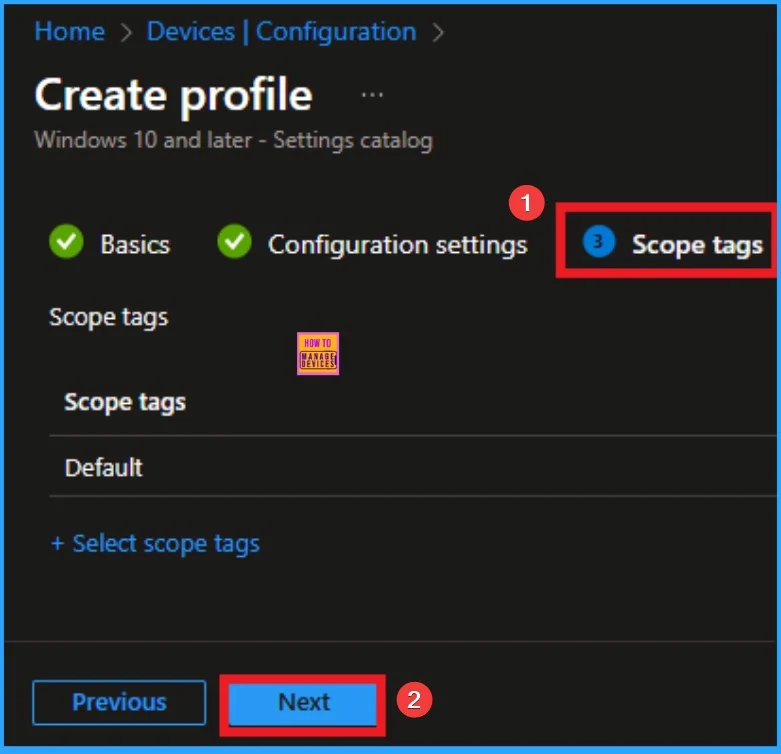
Device Enrollment Notifications
Device enrollment notifications helps to Notify users when devices are enrolled to detect unauthorized onboarding and reinforce secure provisioning. Attackers who obtain user credentials or exploit self-enrollment flows can silently onboard devices, bypassing user scrutiny and enabling data exposure or lateral movement.
Remediation Action
Configure Intune enrollment notifications to alert users when their device is enrolled and reinforce secure onboarding practices.
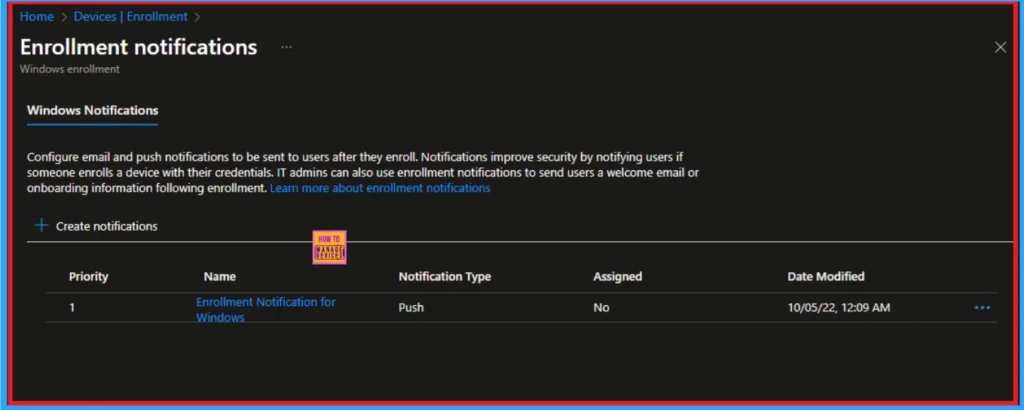
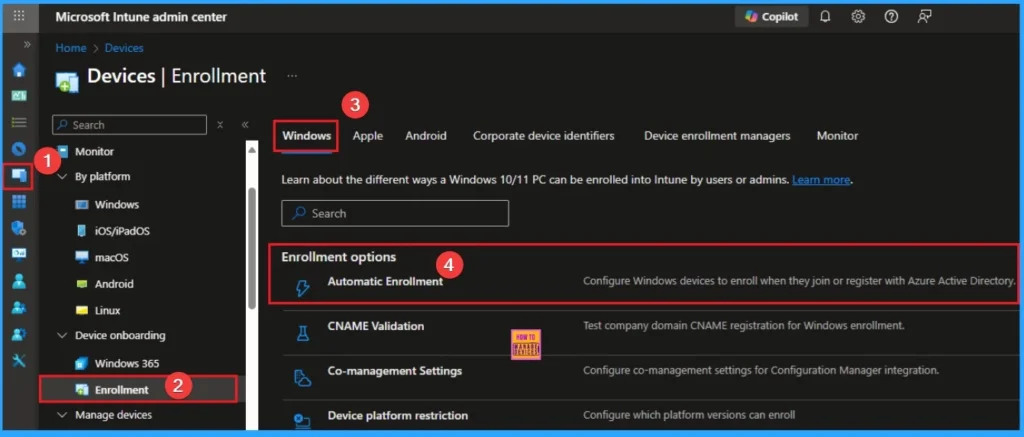
Windows Automatic Device Enrollment
By enforcing Windows automatic device enrollment, admins can prevent the accessing of corporate data, bypass compliance policies, and introduce vulnerabilities into the environment by attackers in unmanaged devices.
Remediation Action
Enable automatic enrollment for Windows devices using Intune and Microsoft Entra to ensure all domain-joined or Entra-joined devices are managed.
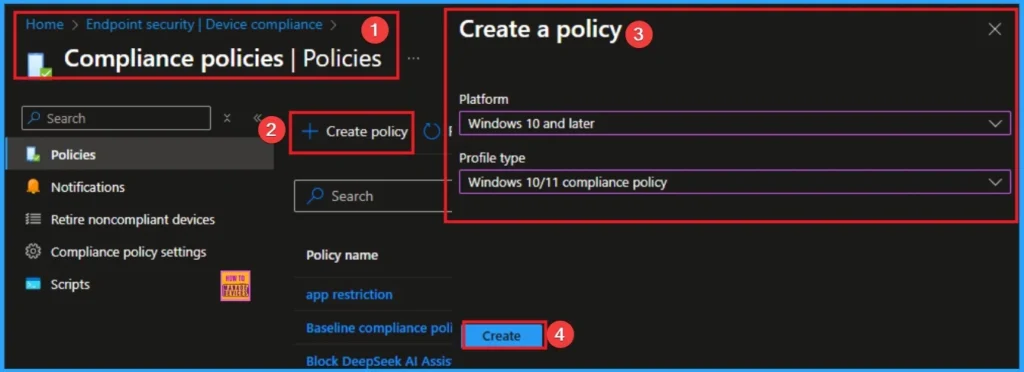
Compliance Policies Protect Windows Devices
By assigning Compliance policies protect Windows devices, admins can prevent the exploitation on unmanaged or noncompliant endpoints to gain unauthorized access to corporate resources, bypass security controls, and persist within the environment. Also it ensures Windows devices meet core security requirements and supports Zero Trust by validating device health and reducing exposure to misconfigured endpoints.
Remediation Actions
Create and assign Intune compliance policies to macOS devices to enforce organizational standards for secure access and management.
Compliance Policies Protect macOS Devices
Enforcing Platform SSO policies on macOS devices ensures consistent, secure authentication across apps and services. This strengthens identity protection, supports Conditional Access enforcement, and aligns with Zero Trust by reducing reliance on local credentials and improving posture assessments.
Remediation Action
Use Intune to configure and assign Platform SSO policies for macOS devices to enforce secure authentication and strengthen identity protection.
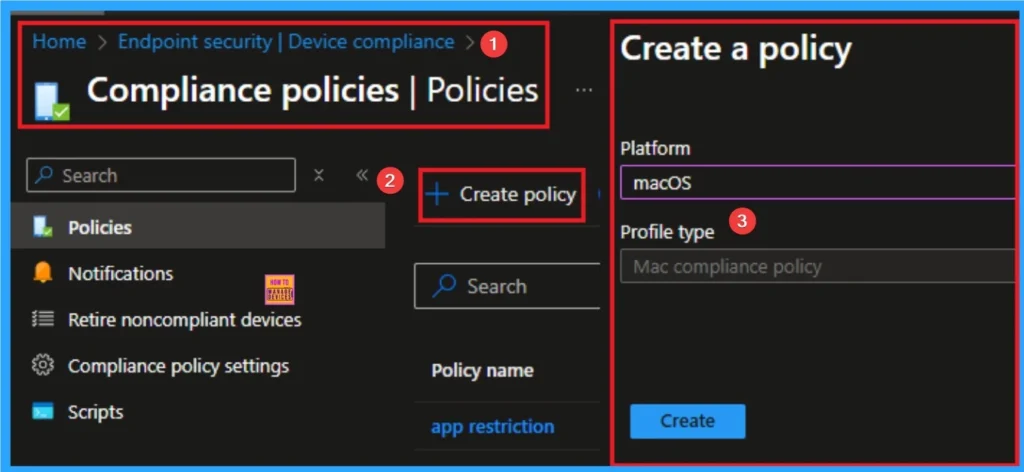
Compliance Policies Protect Personally Owned Android Devices
Enforcing compliance policies ensures Android Enterprise devices meet core security requirements and supports Zero Trust by validating device health and reducing exposure to misconfigured or unmanaged endpoints.
Remediation action
Create and assign Intune compliance policies to fully managed and corporate-owned Android Enterprise devices to enforce organizational standards for secure access and management.
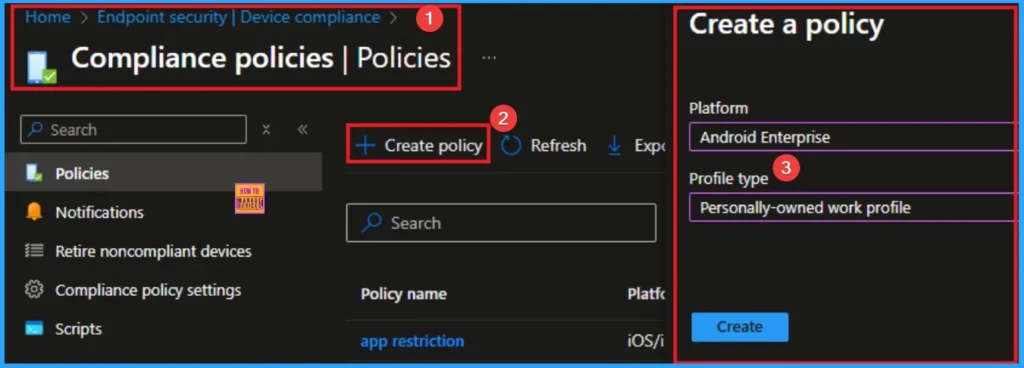
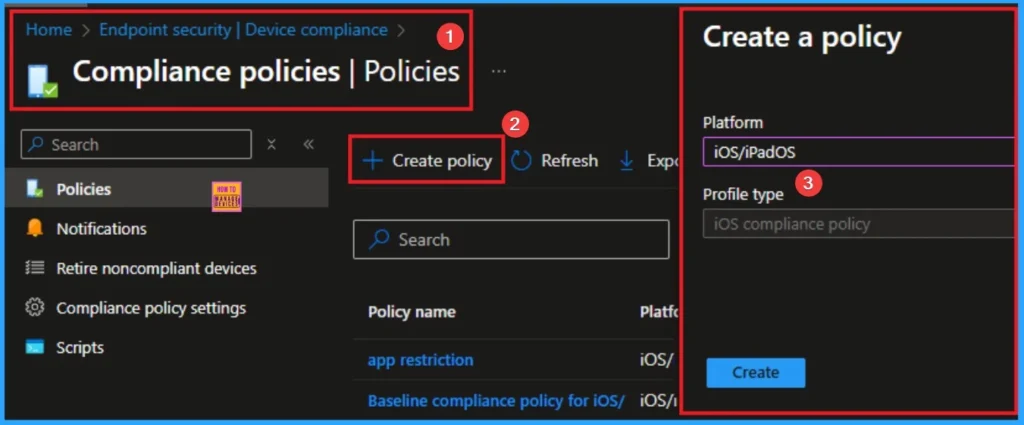
Compliance Policies Protect iOS/iPadOS Devices
Enforcing compliance policies ensures iOS/iPadOS devices meet core security requirements and supports Zero Trust by validating device health and reducing exposure to misconfigured or unmanaged endpoints.
Remediation Action
Create and assign Intune compliance policies to iOS/iPadOS devices to enforce organizational standards for secure access and management.
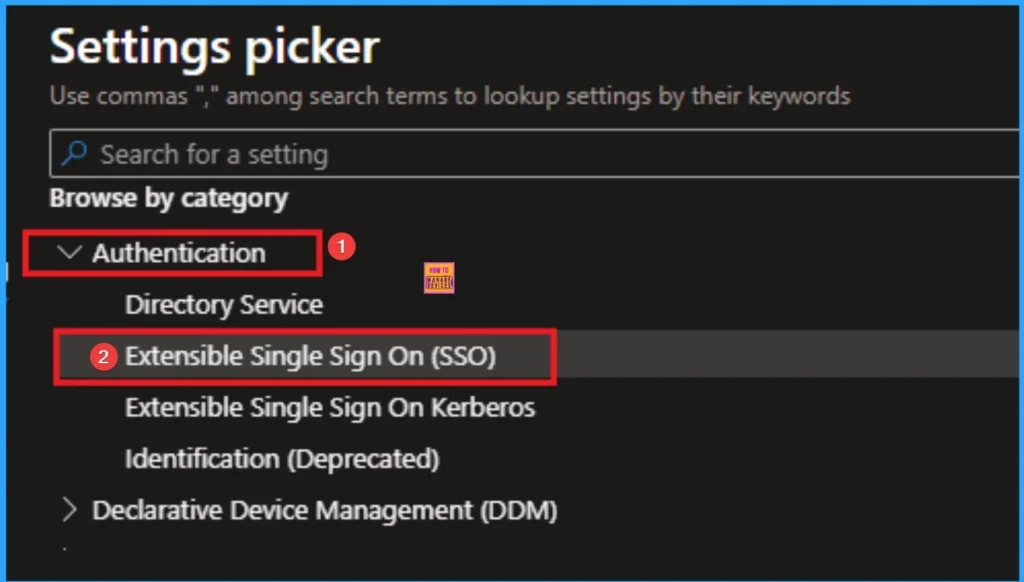
Platform SSO for macOS
Enforcing Platform SSO policies on macOS devices ensures consistent, secure authentication across apps and services. This strengthens identity protection, supports Conditional Access enforcement, and aligns with Zero Trust by reducing reliance on local credentials and improving posture assessments.
Remediation Action
Use Intune to configure and assign Platform SSO policies for macOS devices to enforce secure authentication and strengthen identity protection.
Defender for Endpoint (Android)
Enabling automatic Defender enrollment ensures Android devices are protected by advanced threat detection and response capabilities. This supports Zero Trust by enforcing mobile threat protection, improving visibility, and reducing exposure to unmanaged or compromised endpoints.
Remediation action
Use Intune to configure automatic enrollment into Microsoft Defender for Endpoint for Android devices to enforce mobile threat protection.
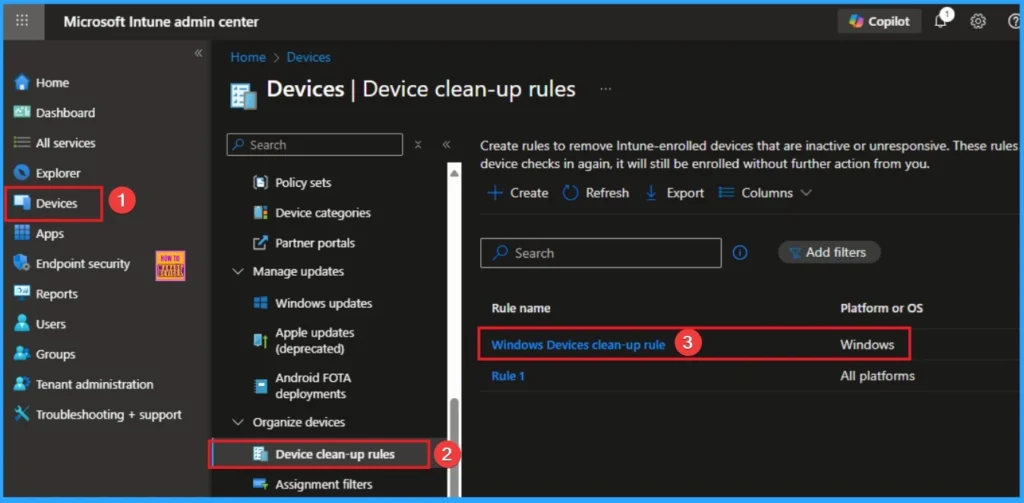
Device Cleanup Rules
Device cleanup rules automatically hide inactive devices from admin views and reports, improving tenant hygiene and reducing administrative burden. This supports Zero Trust by maintaining an accurate and trustworthy device inventory while preserving historical data for audit or investigation.
Remediation Action
Configure Intune device cleanup rules to automatically hide inactive devices from the tenant
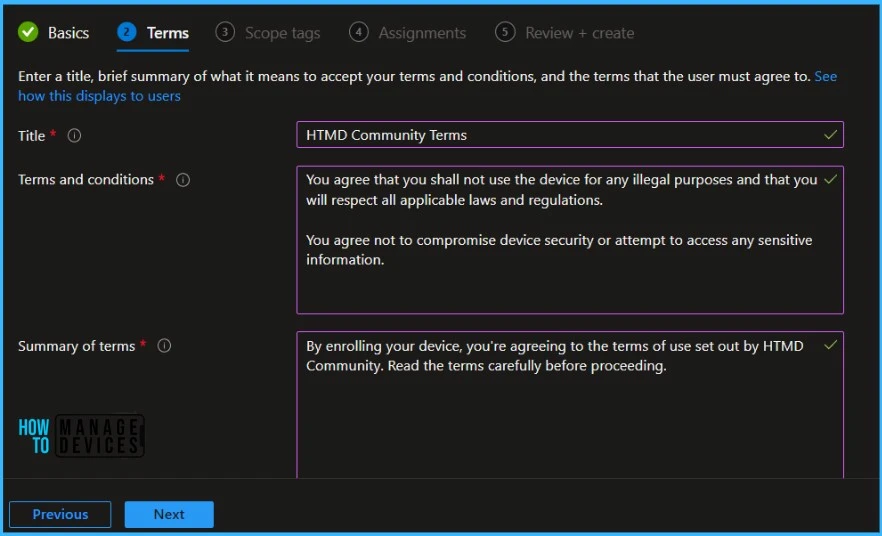
Terms and Conditions Policies
Enforcing Terms and Conditions ensures users acknowledge and accept company policies before accessing sensitive data or systems, supporting regulatory compliance and responsible resource use.
Remediation Action
Create and assign Terms and Conditions policies in Intune to require user acceptance before granting access to corporate resources.
Company Portal Branding
Intune Company Portal branding isn’t configured to represent your organization’s details, users can encounter a generic interface and lack direct support information. Customize branding and support info to improve user trust and reduce support overhead.
Remediation Action
Configure the Intune Company Portal with your organization’s branding and support contact information to enhance user experience and reduce support overhead.

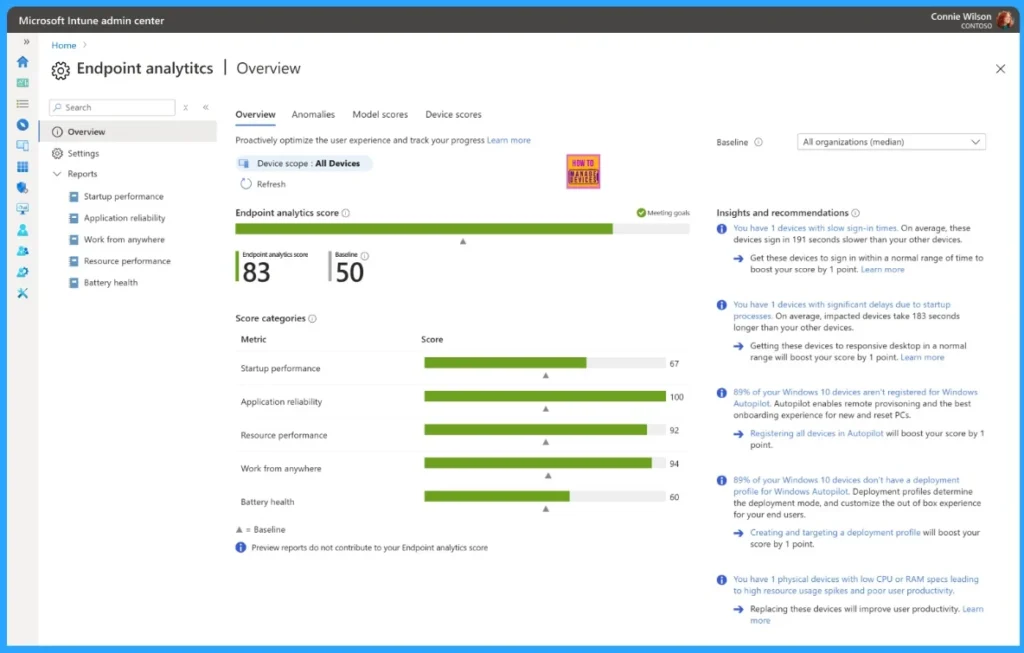
Endpoint Analytics
By enabling Endpoint Analytics provides visibility into device health and behavior, helping organizations detect risks, respond quickly to threats, and maintain a strong Zero Trust posture.
Remediation Action
Enroll Windows devices into Endpoint Analytics in Intune to monitor device health and identify risks
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Entra, Microsoft Security, Career, etc.


