Hey, let’s discuss how to Enable Autopilot Reset Credential Provider Visibility Policy in Windows to Manage Device Refresh using Intune. This policy is about controlling the visibility of the option that lets a PC refresh itself. It does not actually trigger the refresh, but it hides or shows the option for users. The admin must still sign in to start the refresh process on the device.
The importance of this policy is that it gives organisations more control over their devices. It prevents normal users from accidentally trying to reset or refresh a PC. This helps reduce mistakes and ensures that only admins handle sensitive reset tasks.
For users and organisations, this policy makes things safer and easier. Admins can reset devices to a clean and managed state without losing the device’s enrollment in management tools. This is useful for schools, companies, and other groups where many devices are shared.
An example of this policy in use is in a school where students borrow laptops. The IT admin can reset a laptop quickly to get it ready for the next student. In an office, it helps IT prepare devices for new employees while keeping the company’s settings and apps intact.
Table of Contents
What are the Advantages of Disabling this Policy using Intune?
Disabling this policy means that the refresh option remains visible to users on their devices. This can be helpful in situations where trusted users or staff may need quick access to reset or refresh a PC without always relying on IT admins. It also gives more flexibility in troubleshooting and device recovery.
1. Users can easily see and access the refresh option.
2. Saves time by allowing trusted users to start a reset quickly.
3. Helpful in environments where IT support is limited.
4. Allows faster recovery during technical issues.
5. Provides flexibility in managing shared or personal devices.
Enable Autopilot Reset Credential Provider Visibility Policy in Windows to Manage Device Refresh using Intune
The Autopilot Reset Credential Provider Visibility Policy can be easily configured on Windows devices using either Microsoft Intune or by setting a custom OMA-URI (Open Mobile Alliance Uniform Resource Identifier).
- Config Refresh Minimize Security Policy Drift on Windows 11 Managed Devices by MDM Intune
- Best way Intune to Stop Sending New Policy Updates to Windows Devices Pause Config Refresh Feature
- Force the Re-Applying of Intune Policies using the Config Refresh Feature Improves Security of Windows Devices
Create a Profile
To start deploying a policy in Intune, sign in to the Microsoft Intune Admin Center. Then, go to Devices > Configuration profiles > Create New Policy. Select Platform as Windows 10 and later, and profile is Settings catalog.
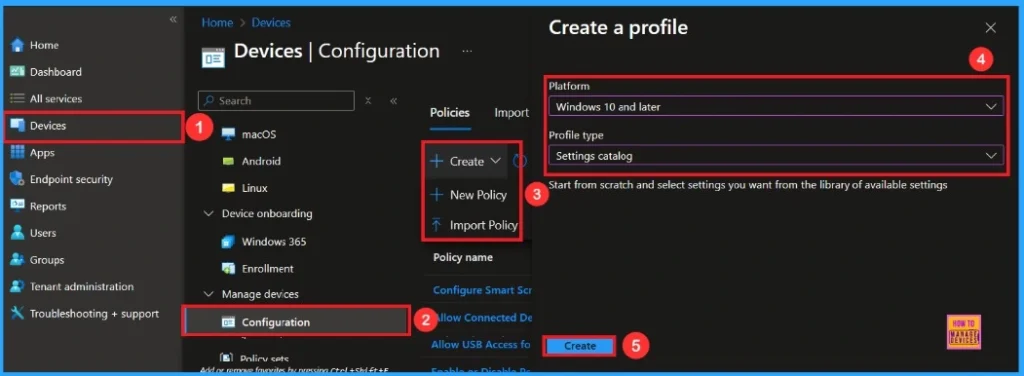
Basic Step
To begin configuring a policy in Intune, start with the Basics step. Here, we can add the name(Disable Automatic Re Deployment Credentials) of the policy and give a brief description(To Disable Automatic Re Deployment Credentials).
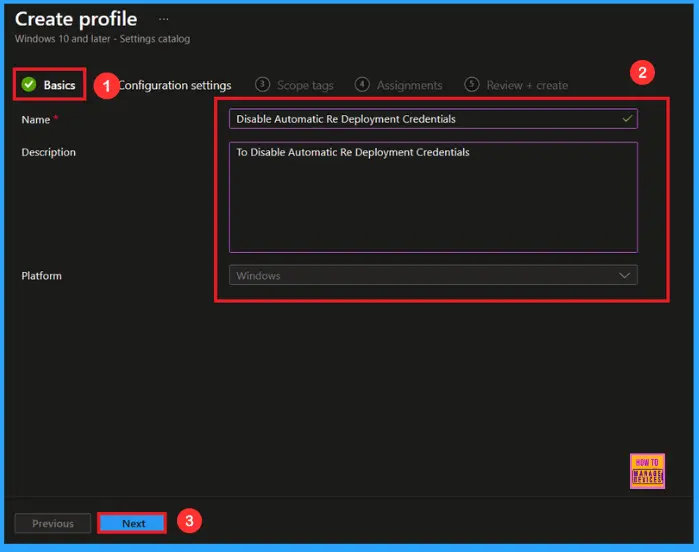
Configuration Settings
In the Configuration settings tab, click the Add settings button to open the Settings picker. Search the settings for Credentials Providers, then select the Disable Automatic Re Deployment Credentials.
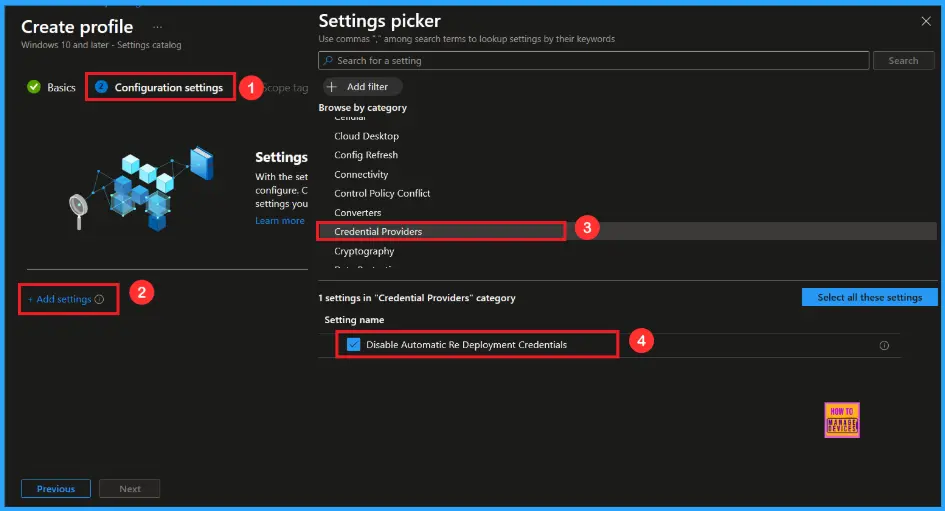
After closing the Settings Picker, you will see that setting on the Configuration Settings page. Here we have only two settings: Enable or Disable. By default, Disable Automatic Re Deployment Credentials Policy is Enable.
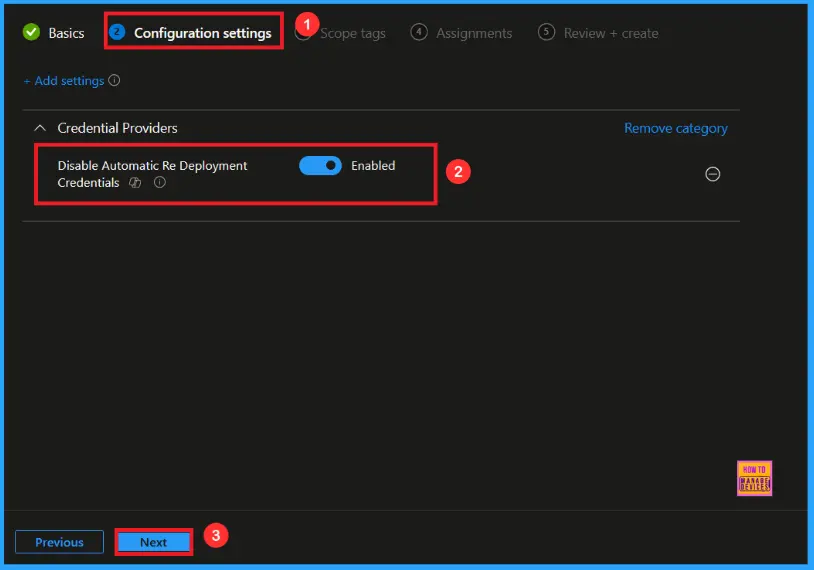
Disable Automatic Re Deployment Credentials Policy
If we disable or not configure this policy, you can disable Automatic Re Deployment Credentials Policy by toggling the switch right to left. After reviewing or adding more settings, you can click the Next button to continue.
Scope Tags
A Scope Tag in Intune is used to control visibility and access to Intune resources based on administrative roles. Scope tags are not mandatory. You can add the scope tag using the Select scope tags button.
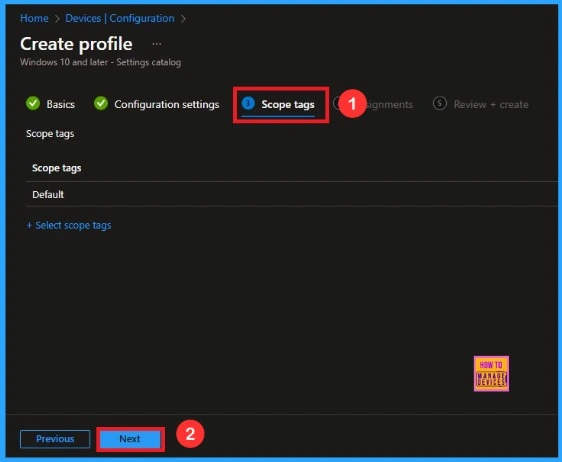
Assignments
On the Assignments tab, we can select which users or devices get this policy. Under Include Groups, click Add Groups. From the list, select the group that we want to target (e.g., Test_HTMD_Policy). Then click the Next button.
Final Step
At the final Review + Create step, we see a summary of all configured settings for the new profile; after reviewing the details and making any necessary changes by clicking Previous. We click Create to finish, and a notification confirms that the “Disable Automatic Re Deployment Credentials created successfully”
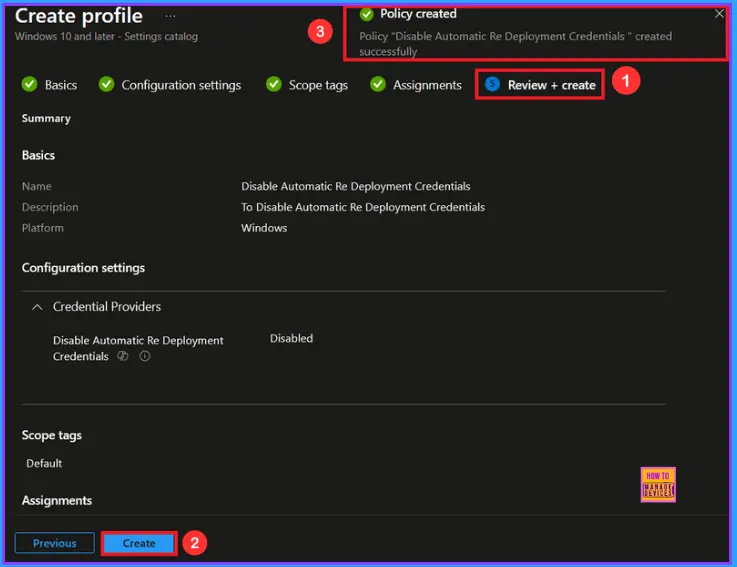
Device and User Check-in Status
We can check a policy’s status in the Intune Portal. Generally, it takes about 8 hours for policies to be created. Use the manual sync option to reduce the configuration delay in the Company Portal app on the device, then check the status again. Navigate to Devices> Configuration. Click on the specific policy (Disable Automatic Re Deployment Credentials) to see its details.
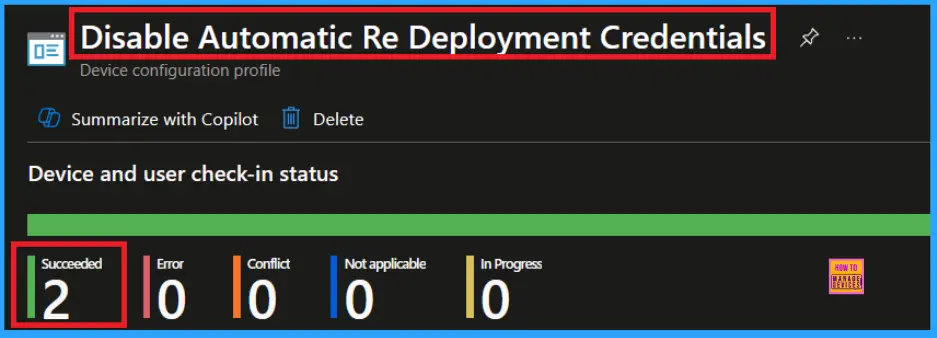
Client Side Verification
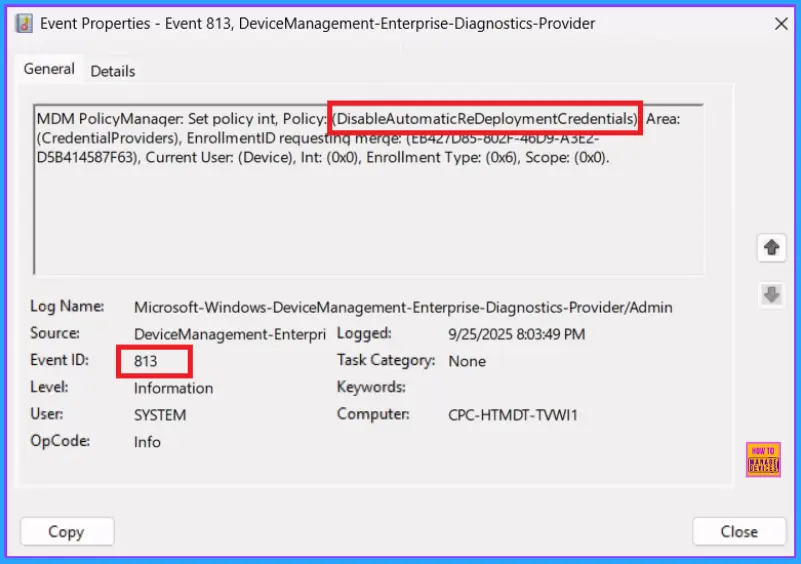
To confirm if a policy has been applied, use the Event Viewer on the client device. Go to Applications and Services Logs > Microsoft > Windows > Device Management > Enterprise Diagnostic Provider > Admin. Use the Filter Current Log option and search for Intune event 813.
MDM PolicyManager: Set policy int, Policy: (DisableAutomaticReDeploymentCredentials)Area:
(CredentialProviders), EnrollmentID requestinq merqe: (EB42/D85-80ZF-4009-A5EZ-
D5B414587F63), Current User: (Device), Int: (0x0), Enrollment Type: (0x6), Scope: (0x0).
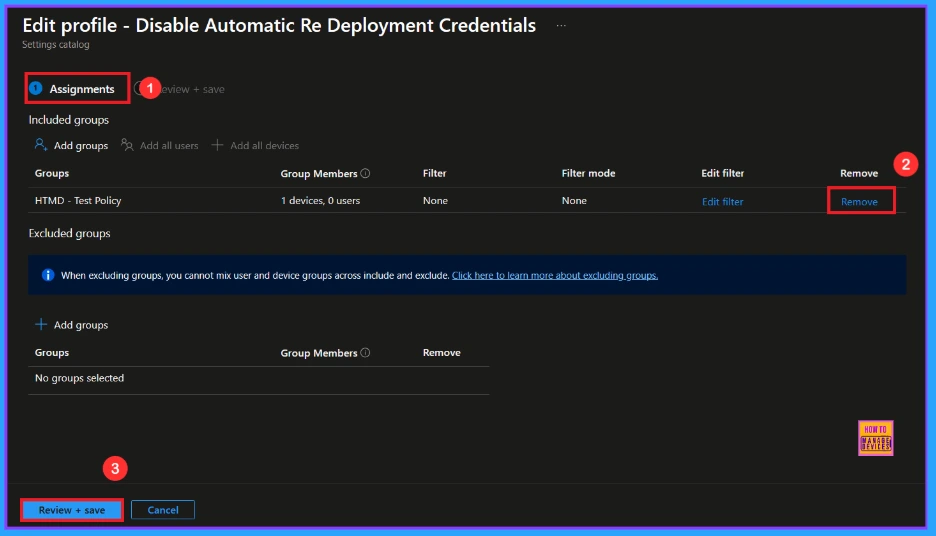
How to Remove Assigned Group from Automatic Re Deployment Credentials Policy
Sometimes, we need to remove a group from a policy assignment for security updates. Open the policy from the Configuration tab and click on the Edit button on the Assignment tab. Click on the Remove button on this section to remove the policy. Click Review + Save after making the change.
For detailed information, you can refer to our previous post – Learn How to Delete or Remove App Assignment from Intune using by Step-by-Step Guide.
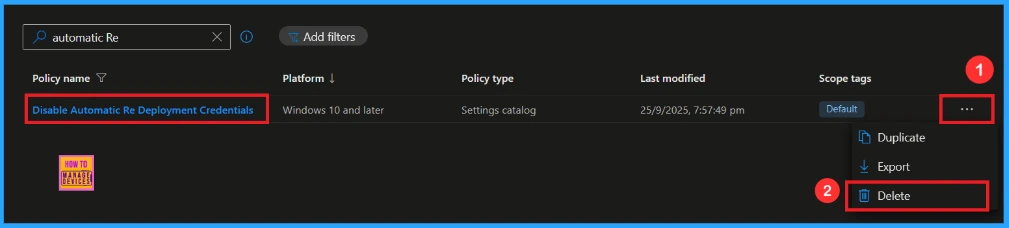
How to Delete Automatic Re Deployment Credentials Policy from Intune
To delete an Intune policy for security or operational reasons. It is simple to do. Search the Policy(Disable Automatic Re Deployment Credentials). Click the three dots, then click the Delete option.
For detailed information, you can refer to our previous post – How to Delete Allow Clipboard History Policy in Intune Step by Step Guide.
Windows Configuration Service Provider (CSP)
The policy Configuration Service Provider (CSP) is a tool for businesses to manage settings on Windows 10 and 11 devices. It details each policy’s function (Description Framework Properties) and available choices (Allowed Values).
Description Framework Properties
| Property Name | property Value |
|---|---|
| Format | Int |
| Access Type | Add, Delete, Get, Replace |
| Default Value | 1 |
Assigned Values
- 0 – Enable the visibility of the credentials for Autopilot Reset.
- 1(Default) – Disable visibility of the credentials for Autopilot Reset.
./Device/Vendor/MSFT/Policy/Config/CredentialProviders/DisableAutomaticReDeploymentCredentials
OMA-URI Settings to Power Sleep Policy
An OMA-URI is a unique string used to configure specific settings on Windows 10 or 11 devices through a Configuration Service Provider (CSP). Its format is determined by the CSP and is used to apply custom device configurations.
To create a new policy in Microsoft Intune, sign in and navigate to Devices > Configuration. Click on Create to start a new policy. Choose the platform as Windows 10 or later. For the Profile type, select Templates, then choose Custom. Provide a name for the policy, such as Allow Search Engine Customization and add a description if needed.
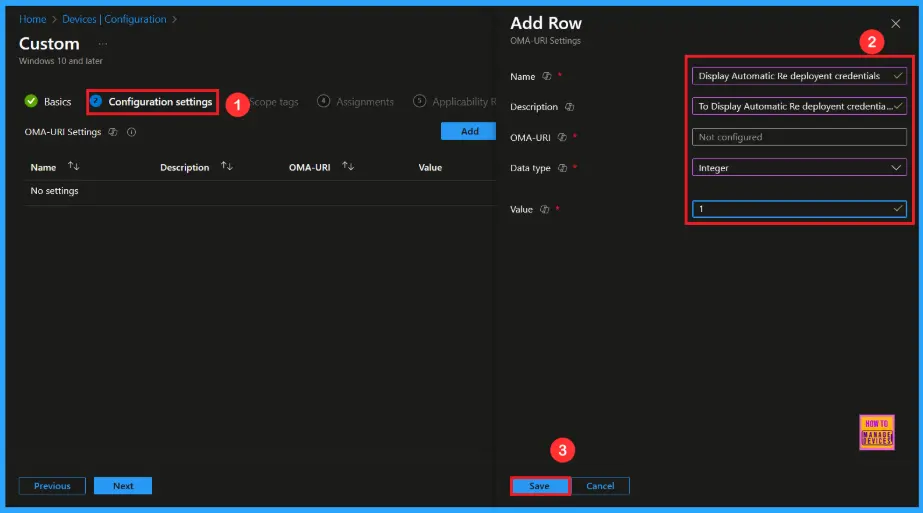
- Click on + Add under OMA-URI Settings to configure the specific setting.
- To Configure the OMA-URI Setting, do the following
- Enter a name for this setting, such as Disable Automatic Re Deployment Credentials
- Description of the setting: To Disable Automatic Re Deployment Credentials
- Enter the following OMA-URI path: ./Device/Vendor/MSFT/Policy/Config/CredentialProviders/DisableAutomaticReDeploymentCredentials
- Set the Data type to Integer.
- Enter the value
- 1 to Disable visibility of the credentials for Autopilot Reset.
- 0 to Enable the visibility of the credentials for Autopilot Reset
- After entering the above details, click the Save button.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


