Exciting News! How to enable Token Protection in Entra Conditional Access for Windows App to Secure AVD and Windows 365. This preview lets you easily require stronger login key protection for Outlook and SharePoint apps on Windows.
Token protection, also known as token binding, enhances security by ensuring stolen tokens can only be used on the intended device. Login key theft is uncommon, but if it occurs, the attackers can pretend to be you online until the key stops working or is cancelled.
Token protection connects a login key to a specific device using a secret code. Without this code, a stolen key won’t work. When you register a new Windows device with Microsoft Entra ID, your main login links to that device. This setup ensures that only these protected login keys, called Primary Refresh Tokens, can be used by apps to access resources.
Token Protection has been updated significantly since its initial preview. It now includes support for the Windows App, which extends its security benefits to both Windows 365 and Azure Virtual Desktop environments.

Table of Contents
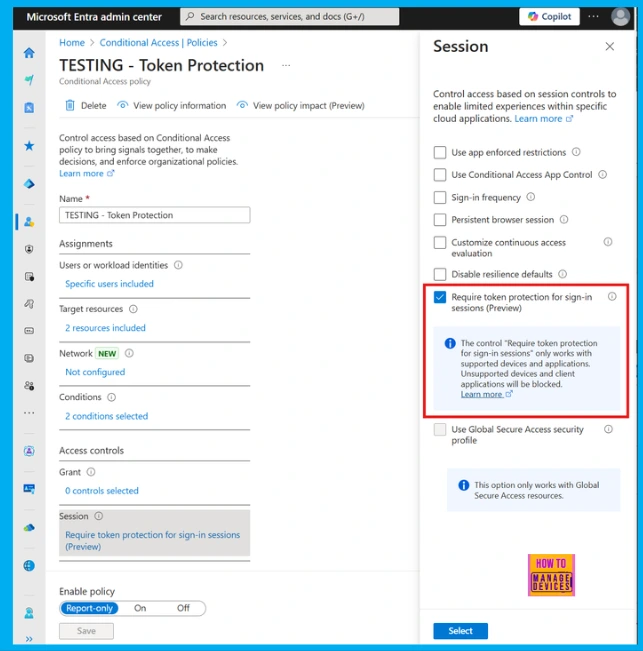
Enable Token Protection in Entra Conditional Access for Windows App
Token protection stops token theft by ensuring login keys only work on the original device. It creates a secure, encrypted connection between the key and the device using a unique secret code. When a modern Windows device joins Microsoft Entra ID, your login is linked to it.
This allows security rules to enforce that only these protected keys (Primary Refresh Tokens) can be used by apps for access. Although rare, token theft can cause serious security problems.
- How To Use Entra Require App Protection Policy In Conditional Access For Secure Access
- Microsoft Entra ID Logs Now Support Linkable Identifiers SID And UTI
- Entra ID Select Multiple Users And Bulk Update User Properties
Token Protection now Supports the Windows App Extending Protection to Windows 365 and Azure Virtual Desktop
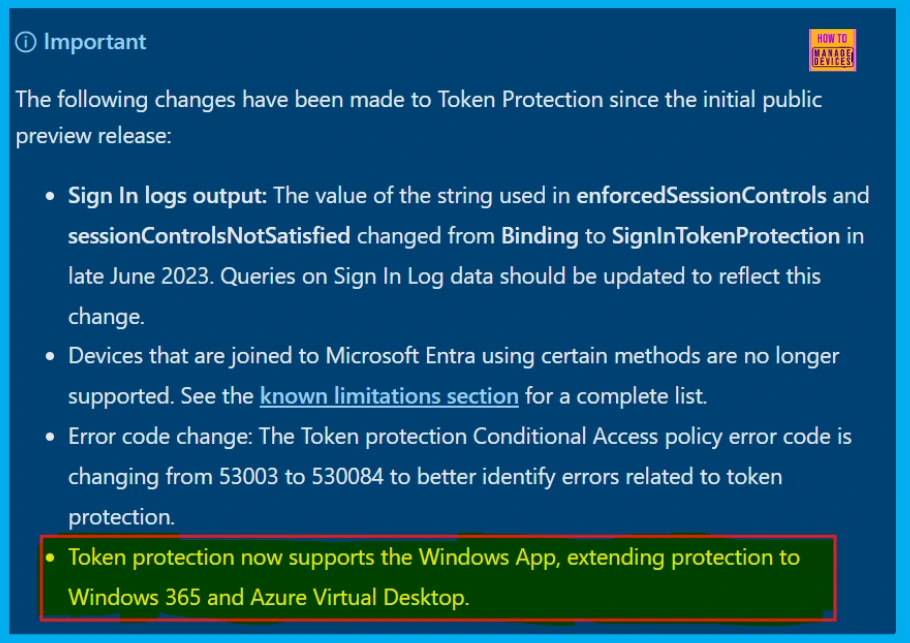
Token Protection has been updated since its initial public preview with the following changes.
| Updations | Features |
|---|---|
| Sign-in Logs Updated | The sign-in logs now use SignInTokenProtection instead of Binding to indicate token protection status in the enforcedSessionControls and sessionControlsNotSatisfied fields. If you’re looking at these logs, make sure to update your searches to use the new term, SignInTokenProtection, which was introduced in late June 2023. |
| Device Join Support Limitations | Support has been removed for devices that join Microsoft Entra ID using specific methods. |
| Error Code Updated | To make it easier to understand problems specifically related to token protection, the error code for the Token protection Conditional Access policy is being updated from 53003 to the new code 530084. |
| More Secure Access | Token protection now works with the Windows App, which means your Windows 365 and Azure Virtual Desktop sessions are also getting this extra security. |
Known Limitations
Microsoft Entra Conditional Access Token Protection has some limitations. There are certain situations where this security feature might not work as expected or could cause issues. This can affect how you log in, which apps are protected, and which devices can use token protection.
| Limitations | Impact |
|---|---|
| Unsupported Clients | Perpetual Office licenses and specific applications like PowerShell modules for SharePoint, PowerQuery in Excel, VS Code extensions for Exchange/SharePoint, and the Windows App. |
| Windows Client Devices | Surface Hub and Windows-based Microsoft Teams Rooms (MTR) are not supported. |
| External Users | External users meeting the requirements in their own organization are fine. Others might get unclear error messages. |
| Devices registered with Microsoft Entra ID | Several Microsoft Entra ID join methods are not supported, including Microsoft Entra joined Azure Virtual Desktop session hosts, devices enrolled in bulk, Microsoft Entra joined Cloud PCs from Windows 365, Microsoft Entra joined Power Automate hosted machine groups, Windows Autopilot self-deploying mode, and Azure VMs enabled for Microsoft Entra ID authentication via VM extension. |
| New Microsoft Entra Registered Devices | New Microsoft Entra registered devices on Windows versions before 24H2 might get blocked if users don’t sign in again after registration. Re-registration is needed if this happens. |
Requirements Supported Devices and Supported Applications
Using this feature requires Microsoft Entra ID P2 licenses. To find the right license for your requirements, see Entra Conditional Access is Central to Secure Microsoft 365 – A Brief Analysis.
Note: Token protection enforcement is part of Microsoft Entra ID Protection and requires Microsoft Entra ID P2 licenses at general availability.
| Supported Devices | Supported Applications |
|---|---|
| Windows 10 or newer devices that are Microsoft Entra joined, Microsoft Entra hybrid joined, or Microsoft Entra registered. See the known limitations section for unsupported device types. | OneDrive sync client version 22.217 or newer |
| Windows Server 2019 or newer that are hybrid Microsoft Entra joined. | Teams native client version 1.6.00.1331 or newer |
| Power BI desktop version | |
| 2.117.841.0 (May 2023) or newer | |
| Exchange PowerShell module version 3.7.0 or newer | |
| Microsoft Graph PowerShell version 2.0.0 or newer with EnableLoginByWAM option | |
| Visual Studio 2022 or newer when using the ‘Windows authentication broker’ Sign-in option | |
| Windows App version 2.0.379.0 or newer |
Deployment
When users access compatible applications on their registered devices using compliant platforms, the Conditional Access policy enforcing token protection should operate seamlessly in the background.
To avoid disrupting users due to app or device issues with token protection, first test with a small group, then gradually roll out to everyone. Before enforcing, set up a policy to just monitor (report-only mode) and track both regular and background logins for a while to understand normal use. Finally, apply the protection to users known to be compatible first. This helps check if everyone’s apps and devices will work with the new security.
Capture Logs and Analyze
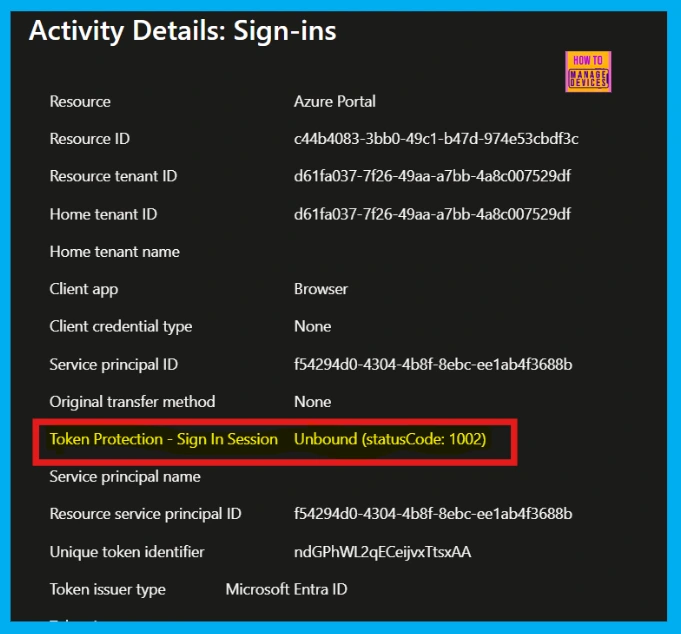
You can track and analyze the enforcement of Conditional Access token protection policies both before and after deployment using Policy Impact (Preview), Sign-in Logs, or Log Analytics.
| Sign-in logs | Log Analytics |
|---|---|
| To understand the impact of your token protection enforcement policy, examine the Microsoft Entra sign-in logs, which detail outcomes in both report-only and enabled scenarios. | Log Analytics allows you to query sign-in logs (both interactive and non-interactive) to find blocked requests caused by token protection enforcement failures. |
End User Experience
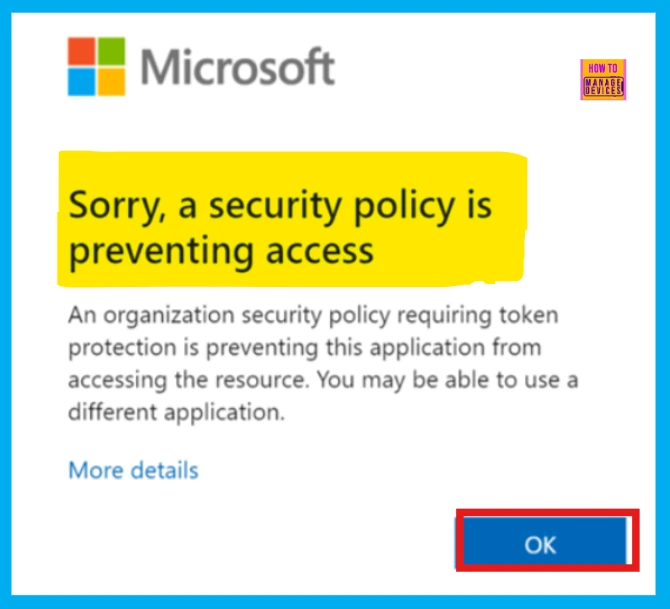
If your device is registered or enrolled and the app supports token protection, you would not see any difference when signing in. Otherwise, you will see a specific screen after you log in.
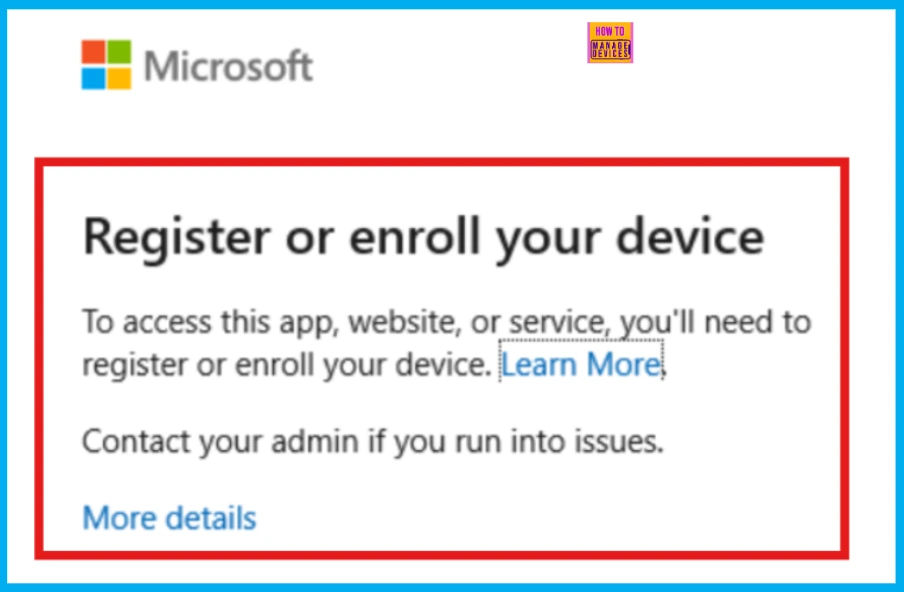
Using an unsupported app with token protection enabled will result in a specific screenshot after authentication.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Resources
- Microsoft Entra Conditional Access token protection explained – Microsoft Entra ID | Microsoft Learn
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and leader of the Local User Group Community. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.

I get the Unsupported App notification for all my Windows 24H2 machines.