Let’s learn how to set up SCCM Azure AD User Discovery ConfigMgr. The Azure Active Directory user discovery feature was added to SCCM in 1706 and later versions.
Azure AD user discovery helps deploy applications to Azure AD users. It enables the deployment of apps to AAD users in a co-management scenario.
Azure AD User Discovery can be configured from the Administration workspace – Cloud Management. This post will see “Video Tutorial on How to Setup SCCM Azure AD User Discovery.”
SCCM Azure AD user discovery involves discovering specific users from Azure AD. The details of these users will be stored in SCCM DB.
Table of Contents
- Overview Windows 10 Co-Management with Intune and SCCM
- Custom Report to Identify Machines Connected via SCCM CMG
- How to Setup Co-Management – Introduction – Prerequisites Part 1
- How to Setup Co-Management – Firewall Ports Proxy Requirements Part 2
- Setup Co-Management – AAD Connect UPN Suffix Part 3 (This Post)
- Setup Co-Management – CA PKI & Certificates Part 4
- Setup Co-Management Cloud DP Azure Blob Storage Part 5
- Setup Co-Management Azure Cloud Services CMG Part 6
- SCCM Configure Settings for Client PKI certificates Part 7
- How to Setup SCCM Co-Management to Offload Workloads to Intune – Part 8
- How to Deploy SCCM Client from Intune – Co-Management – Part 9
- End User Experience of Windows 10 Co-Management – Part 10
Video – How to Setup SCCM Azure AD User Discovery ConfigMgr
Let’s review the video walkthrough of the Azure AD user discovery setup in SCCM. How to Configure Azure Active Directory User Discovery with SCCM – YouTube.
What is SCCM Azure AD User Discovery?
This provides deeper visibility of Azure AD user properties, which SCCM could use to target Azure AD users’ applications.
Where are Azure AD User Discovery Configurations?
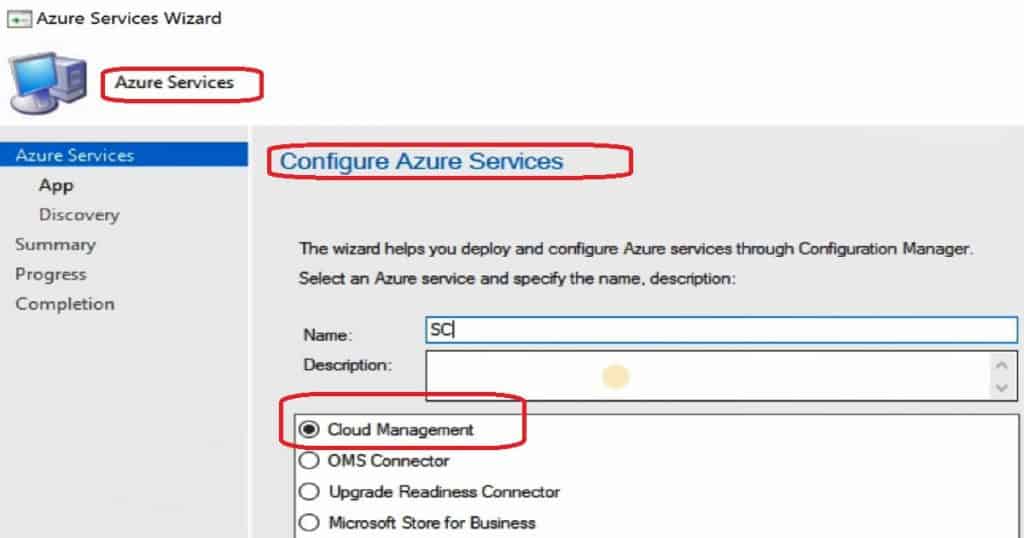
In the SCCM console, navigate through Administration- Cloud Services – Azure Services – Cloud Management. You don’t have to use the Azure portal to create server and client applications.
Instead, the following SCCM Azure service Wizard helps create apps in Azure and schedule the Azure AD User Discovery configurations.
How Do You Create Azure Server and Client Apps from the SCCM Console?
As part of the Azure AD user discovery process, we must create connectivity between the on-prem SCCM CB server and Azure AD. This is done through Azure server-side and client-side applications (more details in the section below). We can create these apps using the Azure Services Wizard in the SCCM console.
We need to create Azure Apps using Azure AD admin credentials. Once successfully authenticated with Azure AD, SCCM helps you create the two apps mentioned in the screenshot below.
Creating applications is straightforward, as seen in the video tutorial. Enter the Application Name, Home Page URL, and APP ID URI—any URL is OK. You don’t want a proper working URL; any URL will be OK. The secret critical Validity period is one year, and the Azure AD admin account signs in.
Azure AD tenant names will automatically populate when you authenticate with Azure AD. It would help to have an internet connection on the SCCM console’s server.
How Do You Configure Azure AD User Discovery Settings?
Unlike SCCM Active Directory discovery, configuring SCCM Azure AD user discovery does not allow you to select a particular OU. Instead, the discovery runs for the entire tenant.
The Azure Services Wizard offers the option to Enable Azure AD discovery settings. Configure the settings to discover resources in Azure AD. When the resources are discovered, SCCM CB creates records in its Database. The SCCM Azure AD user discovery Schedule has two options.
The default settings for complete Azure AD user discovery occur every 7 days. The delta discovery interval is 5 minutes. Delta discovery finds resources in Azure AD that have been new or modified since the last discovery cycle.
- Full Azure AD User Discovery
- Delta Azure AD User Discovery
Permission Required for SCCM Azure AD User Discovery
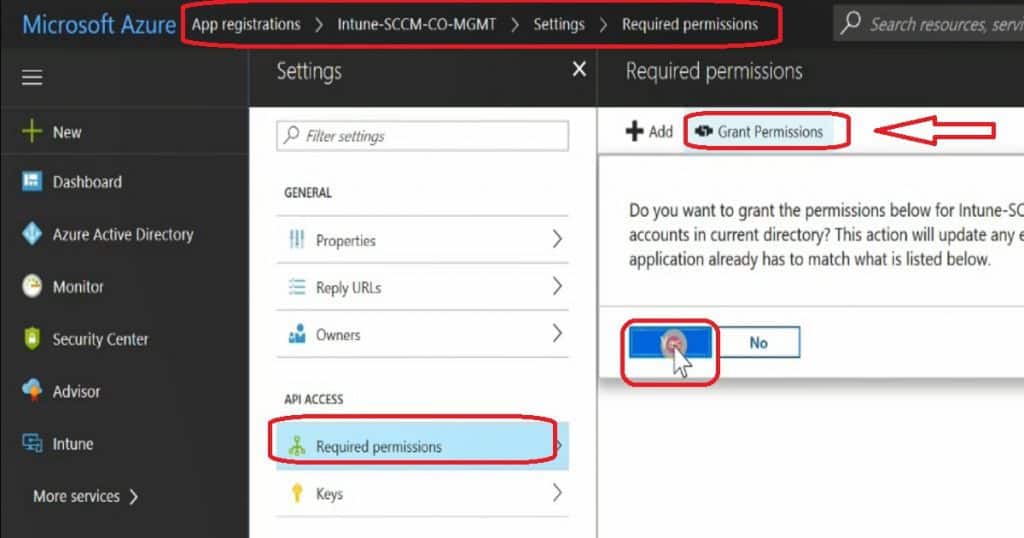
We have created two Azure apps (Server and Client) in the Azure App Registration blade. Select the server application and client application – click on Settings and select the Required Permission button.
Click on Grant Permissions to provide SCCM access to discover the Azure AD users. Repeat the same steps for the Client application.
Watch the video tutorial to learn more details about SCCM Azure AD User Discovery.
Troubleshooting – SCCM Azure AD User Discovery – Issues
SMS_AZUREAD_DISCOVERY_AGENT.log is where you can trace the details of Azure AD User Discovery.
Full Azure AD User Discovery Sync – Details
Full discovery sync details of Azure AD user discovery are recorded in the log file called SMS_AZUREAD_DISCOVERY_AGENT.log.
Initializing Task Execution Manager instance as SMS_AZUREAD_DISCOVERY_AGENT. $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:22.056-330><thread=4184 (0x1058)>
Starting component SMS_AZUREAD_DISCOVERY_AGENT~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:22.165-330><thread=4184 (0x1058)>
Component SMS_AZUREAD_DISCOVERY_AGENT started successfully.~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:22.712-330><thread=4184 (0x1058)>
Azure AD Discovery Worker starts.~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:27.353-330><thread=4204 (0x106C)>
Subscribing to Registry Hive: LocalMachine, KeyPath: SOFTWARE\Microsoft\SMS\COMPONENTS\SMS_AZUREAD_DISCOVERY_AGENT, FilterType: ValueChange, WatchSubTree: False~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:27.369-330><thread=4204 (0x106C)>
Registry Watcher started~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:27.385-330><thread=4204 (0x106C)>
Successfully subscribed listener to registry key.~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:27.385-330><thread=4204 (0x106C)>
AAD sync manager for cloud service ID=16777217 started. ~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:44.541-330><thread=4204 (0x106C)>
Full sync for cloud service ID=16777217 will start immediately. ~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:44.604-330><thread=4204 (0x106C)>
Graph API version changed to 1.6~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:45.510-330><thread=4204 (0x106C)>
Query batch size changed to 100~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:45.526-330><thread=4204 (0x106C)>
Max Json length changed to 33554432~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:45.572-330><thread=4204 (0x106C)>
AAD full sync initialized for tenant 67bb8c6d-7266-4faa-a290-5edd572c2210, with server app 7f81b297-e94e-4767-b44a-b0a191f32989.~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-13-2017 10:24:46.416-330><thread=4204 (0x106C)>
ERROR: Sync request failed. Error: Microsoft.IdentityModel.Clients.ActiveDirectory.AdalServiceException: Service returned error. Check
Delta Azure AD User Discovery sync – Details
Let’s find out more details from the log files SMS_AZUREAD_DISCOVERY_AGENT.log.
INFO: UDX was written for user TESTSyc@anoopc.onmicrosoft.com - C:\Program Files\Microsoft Configuration Manager\inboxes\auth\ddm.box\userddrsonly\___mrxm4stp.UDX at 06-11-2017 16:10:11.~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-06-2017 16:10:11.412-330><thread=2552 (0x9F8)> Successfully published UDX for Azure Active Directory users.~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-06-2017 16:10:11.453-330><thread=2552 (0x9F8)> Total AAD Users Found: 1. Total AAD User Record Created: 1~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-06-2017 16:10:11.536-330><thread=2552 (0x9F8)> AAD delta sync completed successfully at 16:10:11. ~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-06-2017 16:10:11.612-330><thread=2552 (0x9F8)> Next DELTA sync for cloud service 16777217 will start at 11/06/2017 16:15:11.~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-06-2017 16:10:11.665-330><thread=2552 (0x9F8)> AAD delta sync initialized for tenant 67bb8c6d-7266-4faa-a290-5edd572c2210, with server app 7f81b297-e94e-4767-b44a-b0a191f32989.~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-06-2017 16:15:11.763-330><thread=2552 (0x9F8)> Successfully acquired access token for server app. ~~ $<SMS_AZUREAD_DISCOVERY_AGENT><11-06-2017 16:15:11.866-330><thread=2552 (0x9F8)>
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.



Appreciate your helpful video and instructions but the friendly names and the names of the services/urls you use are not very good. I realize it doesn’t matter what you put in for those details but the names should reflect something a little more specific about what you are setting up.