SCCM Configure Settings for Client PKI certificates ConfigMgr.Setting up Client PKI certificates is one of the essential steps for HTTPS communication from CMG to MP/SUP.
This post will see how to complete the Client PKI setup tasks for Co-management scenarios. Once you have Root CA, Client PKI certificates configuration is pretty straightforward.
Read More on SCCM Client PKI – FIX SCCM PKI Client Registration Issue Hotfix and Fix SCCM Sites That Don’t Have Proper HTTPS Configuration Issue
Content of this post
- Decision Making – Client PKI
- Co-Management Related Posts
- Video Tutorial – Configure Client PKI Certs
- Configure Settings for Client PKI certificates
- Step by Step Process to Configure Client PKI Certs
- Bonus Tips about Client PKI Certificates
Decision Making – Client PKI
This is a critical decision point for your device management strategy. AAD identity is a better alternative for Client PKI. Even though you have AAD joined machines, you should have public certs for CMG and CDP. So, you need to decide whether you are going with internal PKI or Public PKI.
Deploying Client PKI Certs to Internet Connected Devices is another important point. Another checkpoint before implementing Client PKI is whether you need to enable Client Check the certificate revocation list (CRL) for site systems or not. I have NOT helped CRL for my lab environment to reduce the overhead.
Co-Management Related Posts
All Co Management Video Tutorial
Overview Windows 10 Co-Management with Intune and SCCM Custom Report to Identify Machines Connected via SCCM CMG How to Setup Co-Management - Introduction - Prerequisites Part 1 How to Setup Co-Management - Firewall Ports Proxy Requirements Part 2 Setup Co-Management - AAD Connect UPN Suffix Part 3 Setup Co-Management - CA PKI & Certificates Part 4 Setup Co-Management Cloud DP Azure Blob Storage Part 5 Setup Co-Management Azure Cloud Services CMG Part 6 SCCM Configure Settings for Client PKI certificates Part 7 (This Post) How to Setup SCCM Co-Management to Offload Workloads to Intune - Part 8 How to Deploy SCCM Client from Intune - Co-Management - Part 9 End User Experience of Windows 10 Co-Management - Part 10
Video Tutorial – Configure Client PKI Certs
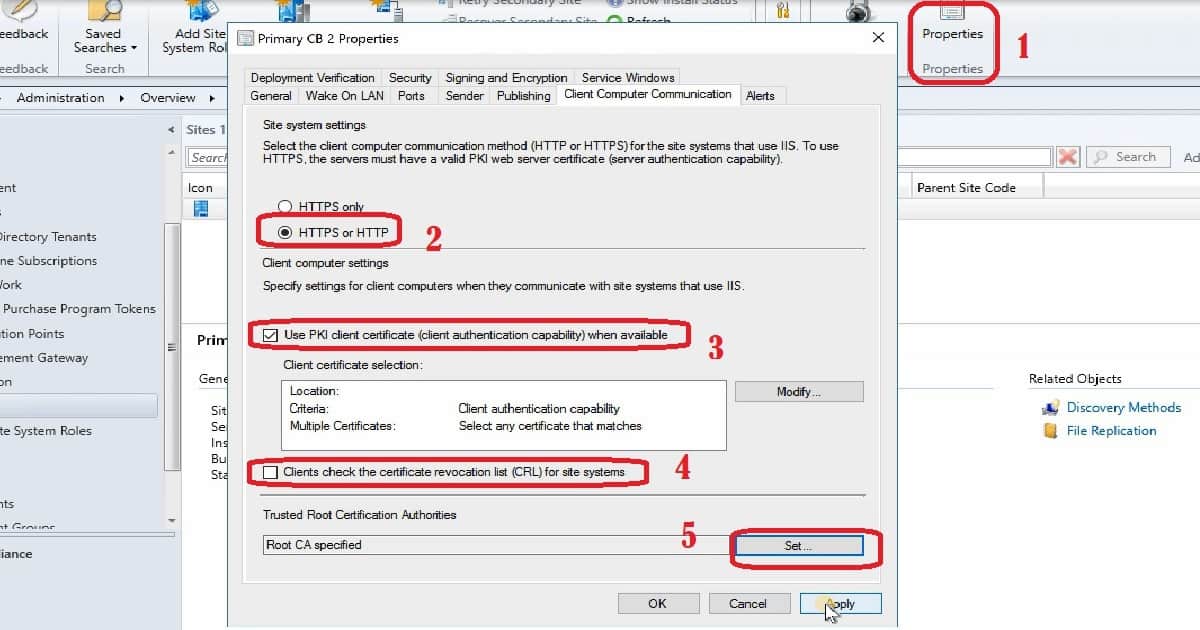
Configure Settings for Client PKI certificates
There are two sections in Client Computer communication. One is to get the server-side (site system Settings) ready for the secured (HTTPS), and the other is to configure client computer settings. Site System Settings
Select the client computer communication method (HTTP or HTTPS) for the site systems (MP/SUP) that use IIS. The server must have a valid PKI web server certificate (server authentication capability) to use HTTPS.
Client Computer Settings
Specify settings for client computers when the clients communicate with site systems that use IIS. Use PKI client certificate (client authentication capability) when available. Public Cert and AAD authentication are other options instead of using Client PKI certificates (as I mentioned in the above section).
Step by Step Process to Configure Client PKI Certs
- In the SCCM CB console, choose Administration.
2. In the Administration workspace, expand Site Configuration, choose Sites, and then choose the primary site server
3. Right-click on the Primary site server, choose Properties and choose the Client Computer Communication tab.
The client Computer Communication tab is available on a primary site only. If you do not see the Client Computer Communication tab, check that you are not connected to a CAS or an SCCM secondary site.
4. Choose the HTTPS or HTTP option when you do not require your existing SCCM clients to use PKI certificates. This will also help to implement client PKI for co-management scenarios.
If you chose HTTPS or HTTP, choose Use client PKI certificate (client authentication capability) when available when you want to use a client PKI certificate for HTTP connections. The client uses this certificate instead of a self-signed certificate to authenticate to site systems. This option is automatically chosen if you choose HTTPS only.
When clients are detected on the Internet or configured for Internet-only client management, they always use a client PKI certificate.
5. Choose Use PKI client certificate (client authentication capability) when available
6. Choose Modify to configure your chosen client selection method for when more than one valid PKI client certificate is available on a client, and then select OK. I don’t have more than one client PKI certificate; hence I didn’t modify this in my lab environment.
7. Select or Clear the check box for clients to check the Certificate Revocation List (CRL). As mentioned in the above section of this post, I cleared the check box for CRL to reduce the overhead.
9. Browse and Select your Root & Intermediate CA certs from Set Root Certificates windows. I don’t have an intermediate CA cert; hence I uploaded only Root CA.
Specify trusted root certification authority (CA) certificates for clients, choose Set, import the root CA certificate files, and select OK.
When you don’t upload Trusted Root CAs in the Trusted Root CA setting on the Client Computer Communication tab, SCCM trusted check but assumes that Trusted Root certificates are otherwise properly implemented on clients and servers in the environment.
I have not tested this in the latest version of the SCCM CB environment.
10. Choose OK to close the properties dialog box for the site
Bonus Tips about Client PKI Certificates
Following are some of the thought points I have in mind and implemented in my lab environment.
Intune to deploy Root CA certs to Internet-connected client devices, or If you have domain-joined machines, then you can use group policy to deploy root CA cert.
Use ARM wherever possible to avoid Azure management certs (otherwise, use self-signed certs)
Server PKI Cert for MP/SUP – IIS HTTPS communication (Or else we can use SCCM generated cert as you can see in the post)
Server PKI Cert for CDP/CMG – Client communication
Root and Intermediate CA certs uploaded to CMG


Do you need the PKI cert (SCCM Client Cert) to be added to a secondary site if it’s interforest, two-way, transitive trust? Domain A has my primary, but Domain B has my secondary site. Primary uses HTTPS, but secondary is just HTTP. Computers are being assigned the primary site, but the sccm client is not installing, and I think it’s because of the cert. I wonder if I can put that cert into IIS of Domain B – secondary site – will that work? I have separate CAs, and the Domain A admins don’t want me to put the sccm client cert into the CA.
I would like to know your scenario. What are you trying to implement? Co-Management?
Thank you
We have 1 Primary Site with 3 Distribution Points. Is there a easy way to work out which servers will need the Web Server cert ( IIS ) and which will require the Workstation Authentication cert ?
Hi Annop
Good day
When i’m trying to register the new ISV certificate i’m getting the following message Failed to submit certificate to site system i tried both CAS and Primary server.
Which ISV ? And you might not have access on the servers ? Have you tried to check the certs node in SCcm console …
hi anoop,
i have installed PKI to internet based client. the installation is completed. the client is taking MP point. but the certificate information in congratulation manager is none . and am getting below error
[RegTask] – Client is not registered. Sending registration request for GUID:69F2AF5E-35CD-4DB3-BFB0-C4AAE8B567C3 … ClientIDManagerStartup 9/20/2019 10:47:55 AM 7068 (0x1B9C)
WPJ Certificate not found ClientIDManagerStartup 9/20/2019 10:47:55 AM 7068 (0x1B9C)
RegTask: Failed to send registration request message. Error: 0x87d00231 ClientIDManagerStartup 9/20/2019 10:48:01 AM 7068 (0x1B9C)
RegTask: Failed to send registration request. Error: 0x87d00231 ClientIDManagerStartup 9/20/2019 10:48:01 AM 7068 (0x1B9C)
Hello, If you are looking pki for cmg. I would recommend using this guide https://www.anoopcnair.com/new-sccm-cmg-setup-guide-ehttp/#Enable_the_MP_for_CMG
Hi Anoop
I have Configured the Settings for Client PKI certificates as per your excellent instructions.
SCCM 2012 is installed in a number of our environments.
In one of our environments, every computer/server has multiple (in excess of 100) certificates issued using the ConfigMgrClientCertificate template.
I have tracked down that a scheduled task entitled “SystemTask” under “CertificateServicesClient” generates a new certificate each time it is run, the trigger is on every GPUpdate. This schedule task is the same in all the other environments that only have one certificate per computer/server (this as expected).
My suspision is that the Scheduled Task checks that the certificate matches a criteria (Inside SCCM this set to “DC = “), in this case the check determines that there is not a certificate that matches and therefore requests a new certificate.
Can you give me some pointers on what could be causing this issue and hopefully suggestions on how to resolve.
Regards
Pete
Hello I’m not tried this with 2012. This post is more in-line with Co-management scenarios. Unfortunately, I’m afraid I don’t have much experience in your specific scenario.
Hi Anoop, thanks for putting out these SCCM resources!
I’ve setup SCCM 1910 in my lab successfully but run into issues after implementing HTTPS/PKI. My client computers stopped communicating with the SCCM server after I switch it to HTTPS.
Here’s the error I’m getting from the client’s CcmMessaging.log.
“Post to http://sccm-server.domain.com/ccm_system/request failed with 0x87d00231.”
mpcontrol.log seems to show that MP is working.
“Call to HttpSendRequestSync succeeded for port 443 with status code 200, text: OK”
Thanks!
Hello Anoop,
I have MECM 2203, where we are pushing client on machines, we are almost done however wanted to implement PKI certificate to use HTTPS. What are the steps to follow? can this be achieved without again pushing clients to the endpoints?
You can try 1. eHttp – https://www.anoopcnair.com/setting-up-https-mp-sup-sccm-site-systems/
2. https with internal PKI -> https://docs.microsoft.com/en-us/mem/configmgr/core/plan-design/network/example-deployment-of-pki-certificates
Hello Anoop,
Thanks for your help and your precious work.
I have a question of principle. How does a client knowns that the site has changed mode? from http to https. The client must receive a policy, right?
it’s a chicken and egg problem.
Mp is configured to https only.. and client ask for policy via http..
just asking myself..
Hello Anoop,
Is the “Specify trusted root certification authority” option on the site settings supposed to allow the SCCM servers to accept client certificates issued by root CAs that aren’t in the SCCM servers’ OSs’ Trusted Root stores?
We have a dev environment with a separate PKI hierarchy (DEVCA), which is not trusted by the (production) SCCM servers. As I read the docs, importing that CA cert (along with our main production CA cert) into the site settings *should* allow clients to present DEVCA-signed client certs to the DP and MP… without having to have our SCCM servers fully trust the DEVCA at the OS-level. Am I misunderstanding?
We can’t get this to work, though.. and we opened a case with Microsoft, who is telling us that despite the SCCM documentation, the MP *has* to have the DEVCA in its trusted root store for clients to be able to register…