Let’s learn the 11 Most Common DNS Attacks and Preventions in this post. Firstly, DNS stands for Domain Name Server, and it is a basic form of communication. DNS takes the user input domain and matches them with an IP address. DNS attacks perform the malicious activity by using the said mechanism.
A DNS mechanism was developed to convert alphabetical names into IP addresses, allowing users to access websites. The organizational infrastructure of a DSN is like a tree where starting level contains the ranked-up (top) domains as .com and .org.
DNS tunneling enables threat activities to compromise connectivity to the network and also advance toward remote access to the targeted server. Many DNS attacks can enable hackers to take down servers, steal data, lead users to fraudulent sites, and execute the Distributed Denial of Service attacks.
DNS is one of the most critical internet services and the key component that allows your computer to show you the content right before you. This post will describe all the DNS attack types and their prevention.

- Azure Outage because of DNS Issues Ubuntu? Aug 2022
- How to Add Custom Domain to Office 365 | Add DNS Record
What is DNS?
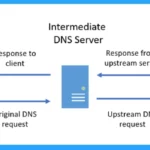
Domain Name System (DNS) is a protocol that translates a domain name into an IP address. On the other hand, when any user types any domain name (website.com) into a browser, a program in the operating system called DNS resolver search for the numerical IP address or website.com.
Common DNS Attacks
An attack that targets the Domain Name System (DNS). It is an essential service of the IP network and the internet. DNS is required in most exchanges. Using a DNS resolution, most of the communication begins. If the resolution service becomes unavailable, most applications can no longer function.
It works similarly to a database accessed by many computers trying to find the address, which solves the user query. In DNS attacks, hackers will sometimes target the servers containing domain names. The attackers will try to determine defenselessness within the system and make it good.
Types of Common DNS Attacks
There are many types of DNS attacks present, in the following the most common DNS attacks are listed below for further detailing.
- DNS Amplification
- DNS Flood Attack
- DNS Spoofing / Cache Poisoning
- DNS Tunnelling
- Domain Lock-up Attack
- DNS Hijacking
- Phantom Domain Attack
- Botnet-Based CPE Attack
- NXDOMAIN Attack
- Random Subdomain Attack
- Distributed Reflection Denial of Service (DRDoS)
Let’s look into the details of all Common DNS Attacks listed above. And also describe and discuss the what are the prevention methods.
1. DNS Amplification
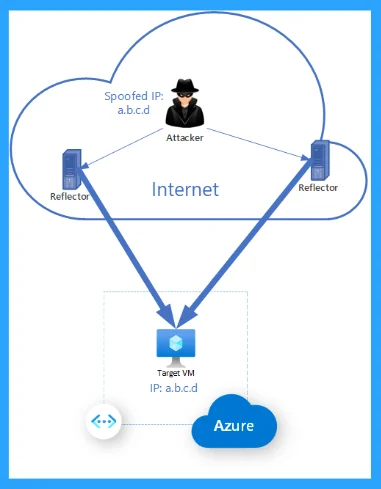
DNS amplification attacks start Distributed Denial of Service (DDoS) on a target server. It includes the open DNS servers that are publically available. Using the public DNS, they sweep over a targeted DNS response traffic.
The attackers send a DNS lookup request to an open DNS server, where the source address is spoofed to become the target address. When the DNS server returns the DNS record response, it is relayed to the new target, controlled by the attacker.
2. DNS Flood Attack
DNS flood attacks involve using the DNS protocol to carry out a User Datagram Protocol (UDP) flood. Threatening people deploy valid, which spoofed, DNS request packets at an extremely high package rate and create a huge group of source IP addresses.
Since the requests seem valid, the DNS servers of the target start responding to all the requests. After that, the DNS server can be overstepped by the many requests. A DNS attack requires a great amount of network resources, and then it targets DNS infrastructure until it is taken offline. Then the result is the target’s internet access becomes slow.
3. DNS Spoofing / Cache Poisoning
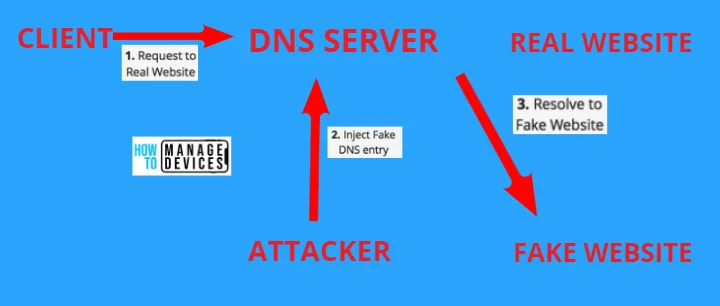
DNS spoofing or DNS Cache poisoning involves duplicating DNS records to redirect online traffic to fraudulent sites that emulate the intended destination. Once users reach the fraudulent destination, it directs them to login into their account.
When the user enters information, they essentially allow the attackers to steal access credentials and any sensitive information typed into the scammer login form. These types of malicious websites are used to install viruses end user’s system, which helps attackers to access the user’s system for a long time.
And also, it is a trick to attack your DNS resolver cache. This attack technique is used to redirect the victims to another remote server. Once the cache poisoning is live and working, attackers will receive all the legitimate traffic in their servers and show phishing-based pages to steal personal information from new users.
4. DNS Tunneling
DNS tunneling involves encoding the data of other programs or protocols within DNS queries and responses. It usually features data that can take over DNS servers, allowing attackers to manage the remote server and applications.
It relies on the external network connectivity of a compromised system, which provides a way into an internal DNS server network with network access. It also requires controlling a server and a domain, an authoritative server carrying out executable data programs and tunneling.
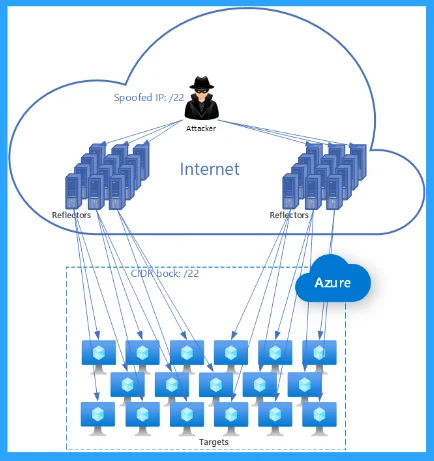
5. Domain Lock-up Attack
Domain lock-up attacks, attacks on a DNS resolver. Attackers perform domain lock-up attacks by creating TCP connections with any resolver; the domains send random junk packets that occupy and oversweep the resolver.
6. DNS Hijacking
DNS hijacking allows an individual to divert to the doubtful DNS (Domain Name System). But, it may be achieved by using viruses or unauthorized modifications of a server. At the same time, the individual has the authority of the DNS.
The authorized DNS can guide others to a web page that seems identical but carries extra content like advertisements, which also guide users to some pages which carry malware or install third-party software.
7. Phantom Domain Attack
Phantom domain attacks are kinds of attacks that compare to normal subdomain attacks. In this kind of attack, the attackers attack your DNS resolver and overpower it to use up supplies called phantom domains, as these phantom domains will never respond to the queries.
The motivation behind this attack is to let the DNS revolver wait for the response for a long time, ultimately leading to the failure of deteriorated DNS performance problems.
8. Botnet-Based CPE Attack
The botnets can be counted as attacks and prepare programs for future attacks; with this as the foundational prospect, this study explores how a botnet is described and organized with our growing dependence on digital devices, the internet, and new future technologies.
Let me clarify that it is several internet-connected devices, and it can be practiced to implement a distributed denial-of-service attack (DDoS attack), which steals data, transmit spam, and enables the attacker to obtain access to the device and its connection.
9. NXDOMAIN Attack
A DNS NXDOMAIN flood DDoS attack attempts to oversweep the DNS server using many requests for invalid records. These attacks are often handled by a DNS proxy server that uses all its resources to query the DNS authoritative server.
This causes both the DNS Authoritative server and the DNS proxy server to use up all their time handling bad requests. The response time for legitimate requests slows down until it eventually stops altogether as a result.
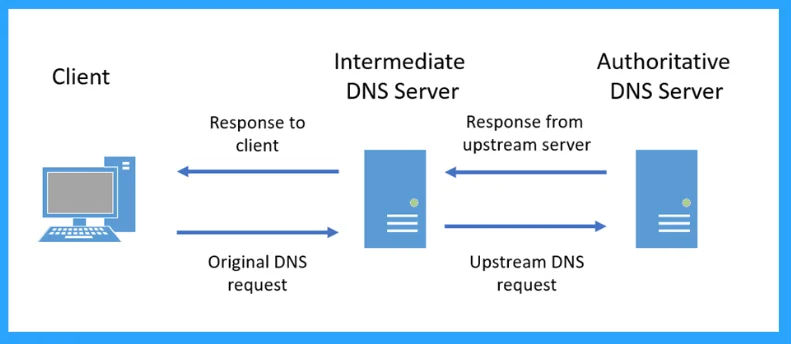
10. Random Subdomain Attack
The Random Subdomain attack can happen from time to time on several networks. Hence, the random subdomain attacks can be identified as DoS attacks that adhere to the same goal as simple DoS. Spoilers send a lot of DNS inquiries against a healthy and active domain name.
However, it harms many non-existing subdomains. It builds a DoS that immerse the authorized DNS server that receives the primary domain name and finally lets interruption of all DNS record lookups. It’s an attack that’s hard to identify.
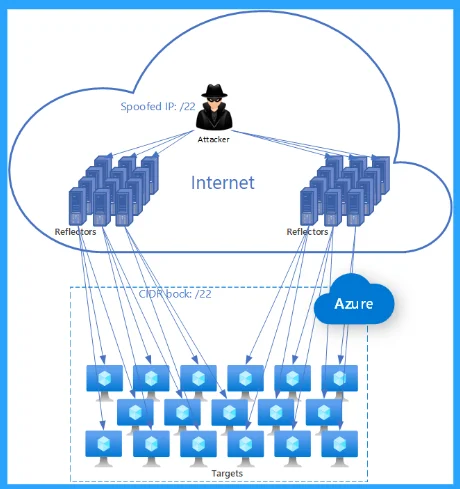
11. Distributed Reflection Denial of Service (DRDoS)
Distributed reflective denial of service (DRDoS) attacks concentrate on bringing down the availability of an asset within the volume of UDP acknowledgments. Sometimes, the attacker would transfer a DNS, NTP, etc., and demand a copied source IP to transfer a more vast acknowledgment to the host.
UDP is the protocol of different choices for this variety of attacks, as it does not build an association state. Once these response packs appear, there is a loss of availability.
This practice makes reflection possible by regulating these attacks at the proper scale; the shared reflection becomes clear, and various endpoints. Dispatch spoofed UDP offers, generating acknowledgments focused on a target.
Preventions for DNS Attacks
DNS attacks can harm end-user by collecting their personal information, harm organizations by malpractice in their organizational data, etc. So several ways can help to protect your organization/ an end-user against DNS attacks, shown in the table below:
| Preventions | Description |
|---|---|
| Up-to-date DNS Software | It’s very important to update your DNS software from time to time and install the security patches. |
| Multi-Factor Authentication | It’s also important to implement Multi-Factor Authentication for all available accounts with access to the DNS infrastructure. |
| DNS Security Extensions | This ensures the safety of DNS by using Digital Signature. DNS security extensions add an extra layer of security to DNS. Digital signatures and certificates authorize access, so it protect private data. |
| Reliable DNS infrastructure | It’s a foundation of a safe and protected environment for an end-user or organization. This will balance a load of incoming threats while an online presence receives many DNS requests. |
| DDoS protected DNS | This was developed specifically to prevent cyber threats like DDoS attacks. |
| Constant Monitoring | Monitoring the inbound and outbound DNS queries and response data can help in detecting any malicious behavior in DNS. |
| Private DNS Resolver | Restrict the DNS resolver to only users on your network, and minimize the risk of malicious external usage, which is used to prevent the DNS cache from being poisoned by attackers. |
Intention Behind DNS Attack
The common reason behind the DNS attack is the competition to show powerful among other hackers. This attacking competition is fully illegal and suffers downtime. But there are many more reasons behind DNS attacks, shown in the table below:
| Reasons for attack | Description |
|---|---|
| Extortion | There is also DNS attack ransomware, and cybercriminals use DDoS attacks to target a server. The server is can respond to regular connections, where attackers furnish their demand for a ransom to stop attacking. |
| Revenge | There is a personal revenge situation against a company, a supplier, or an individual who tries to affect the system. |
| Cover Attack | This type of attack is used as a distraction. It is caught on fixing the DNS traffic while another attack is being conducted or malicious software is installed in the background. |
| Notoriety | People who want to be famous do bad stuff and seek attention by performing some attacks. |
| Personal Challenge | Some of them just want to test their knowledge and attend an attack to get an idea about their success rate. |
| Cyberwarfare | This happens between one country to another country of other important stages, which is used for dis-organized the details. |
Conclusion
As discussed above, DNS service is essential for preserving an organization’s website and online assistance working daily. If you are looking for methods to avoid these kinds of DNS attacks, then this post will be helpful for you.
I hope the 11 Most Common DNS Attacks and Preventions information is helpful. Please follow us on HTMD Community and visit our website HTMD Forum if you like our content. Suggest improvements, if any, and we love to know which topic you want us to explore next.
Author
Alok is a Master of Computer Applications (MCA) graduate. He loves writing on Windows 11 and related technologies. He likes to share his knowledge, quick tips, and tricks with Windows 11 or Windows 10 with the community.
