Ten New Indicators Skills can now leverage MDTI Indicator Data. Yes! This is excellent news for Security Copilot customers. Using Threat Intelligence (TI) sources, they can develop a full view of risks and increase their awareness of attacker tools and methods and how they affect the organisation.
Microsoft’s Security Copilot has improved in detecting threats. At Microsoft Ignite 2024, they announced new features that are generally available to Security Copilot users. They can now access more threat intelligence sources to understand how attackers work and how they target their organization.
Microsoft Defender Threat Intelligence (MDTI) is a powerful platform for storing threat intelligence, including incident response, threat hunting, vulnerability management, and threat intelligence analyst workflows. It helps professionals analyze and respond to security signals.
MDTI Indicator Data is now in Public preview. You can now use ten new indicators skills to control threat intelligence. In this post, I will briefly explain the ten new indicators skills that can leverage MDTI Indicator Data.

Table of Contents
What are Indicators of Compromise (IoC)?
An indicator of compromise (IoC) indicates that someone might have violated the organization’s network or computer. It shows that something crucial like malware, compromised credentials, or data exfiltration has already happened. Security experts search for the event logs and security tools to stop the attack and fix the damage. After everything is fixed, they research how the attack happened so that the organization’s security can strengthen and reduce the risk.
Ten New Indicators Skills Can Now Leverage MDTI Indicator Data
Ten new indicators skills to control threat intelligence. These indicators can link any indicator of compromise (IoC) to related data, which can help signal the attacks. This allows security experts to investigate attacks more efficiently and defend against threats. These new skills use two main types of threat information.
| Two Main Types of Threat Information |
|---|
| In-depth Indicators data |
| Indicators Metadata |
- What Is The Security Compute Unit In MS Copilot For Security Context
- Turn On Or Off Microsoft Defender SmartScreen For Microsoft Edge In Windows 11
- Manage Microsoft Defender Antivirus Updates Using Intune
In-depth Indicators Data
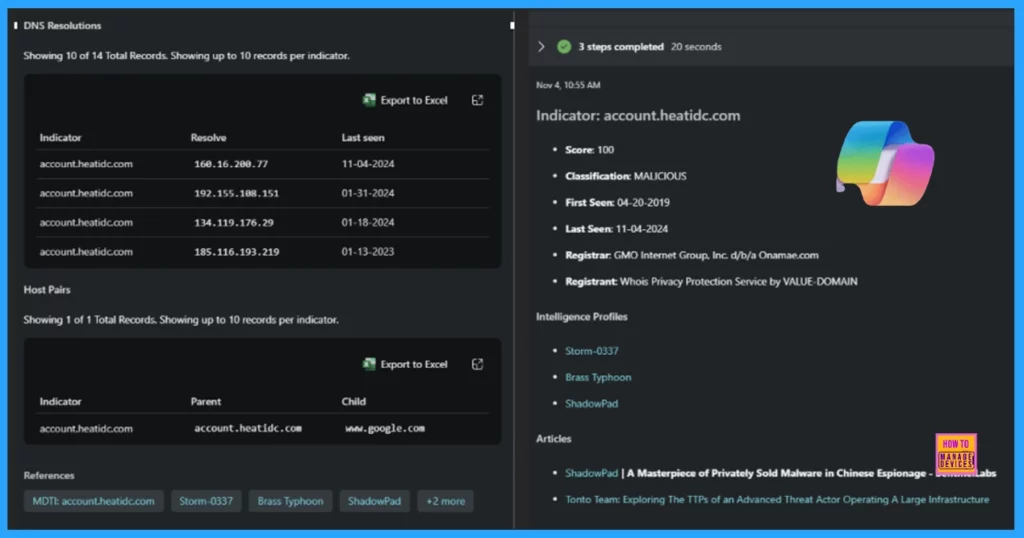
Security Copilot can link any indicator of compromise (IoC) with all threat intelligence related to it in MDTI. It includes articles, Intel profiles, and summary data from Microsoft’s file and URL analysis. Sometimes, a critical situation requires a quick response, such as current information on the attacker and the nature of the attack. This data can also level up experts by preparing the needed next steps charted in MDTI to help them agree with the incident quickly and efficiently.
The following image is an example of an indicator linked to several IP addresses, two articles, and three Intel profiles.
Indicators Metadata
MDTI has advanced Internet data sets. These data sets help Security Copilot link any IoC to the associated infrastructure. Core and derived data sets are made from Internet data collected and examined worldwide. Linking IoC to the associated infrastructure can help analysts find new threat tools and defend the threat activity before it affects the organisation.
- Core Data Sets: It includes Resolutions, WHOIS information, SSL Certificates, Subdomains, DNS, Reverse DNS, and Services
- Derived Data Sets: Trackers, Components, Host Pairs, and Cookies.
Resources
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


