Let’s learn how you can create an Azure AD Dynamic Device Group Managed by MDE Defender for Endpoint using the MicrosoftSense attribute. The Defender for Endpoint service is constantly being updated to include new feature enhancements and capabilities.
With the upcoming MDE enrollment improvements, new device enrollments will no longer support the MDEManaged and MDEJoined system labels. However, existing Windows devices managed by Defender for Endpoint can continue to utilize these labels to target policies without any impact.
To ensure that all devices enrolled in security settings management for Microsoft Defender for Endpoint receive policies, It is recommended creating a dynamic Azure AD group based on the managementType attribute MicrosoftSense.
For new enrollments, including those that no longer require hybrid Azure AD join, the MDEManaged or MDEJoined system labels cannot be used to target policies. Instead, utilize one of the other available methods for targeting policies with these new enrollments.
It is recommended to review your group policy and targeting settings for Windows devices managed by Defender for Endpoint, specifically if you are using the security settings management functionality.
- Azure AD Dynamic Groups Based On Domain Join Type Hybrid Azure AD And Azure AD
- Get Microsoft Defender For Endpoint Product Comparison And License Assignment Options
What’s New Changes to System Label Attributes for Grouping and Targeting
As part of the upcoming enrollment improvements for this capability, the MDEManaged and MDEJoined system labels will no longer be applicable for new device enrollments. It’s important to note that this change only affects you if you have opted into the public preview features in Defender for Endpoint.

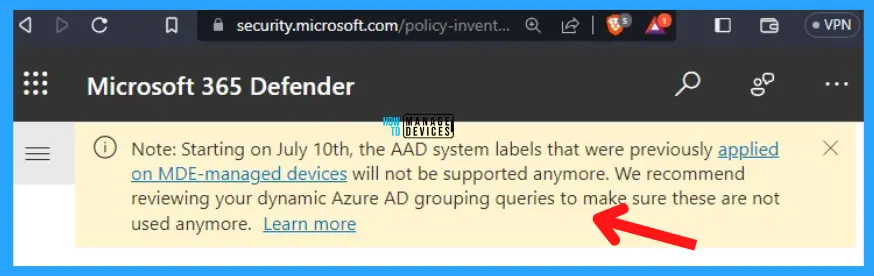
NOTE from Microsoft: Starting on July 10th, the AAD system labels that were previously applied on MDE-managed devices will not be supported anymore. We recommend reviewing your dynamic Azure AD grouping queries to make sure these are not used anymore.
If you currently rely on the MDEManaged or MDEJoined system labels for Azure AD groups to target policies, recommend transitioning to one of the alternative methods listed below:
- Target policy based on the platform by using the deviceType attribute (Windows, WindowsServer, macOS, Linux) – Recommended.
- Target policy by using the managementType attribute MicrosoftSense. This will target all devices managed by Defender for Endpoint that are using the security settings management functionality.
Azure AD Dynamic Device Group Managed by Defender for Endpoint
Here are the steps to create an Azure AD Dynamic Device Group managed by Defender for Endpoint, This will automatically add devices managed by Defender for Endpoint to the group, without requiring admins to perform any additional tasks, such as creating a new policy.
Note – Microsoft reveals a major announcement that Microsoft Azure Active Directory (Azure AD) is becoming Microsoft Entra ID. Here I will be using Azure AD, being known to all of you.
- Sign in to the Entra Portal https://entra.microsoft.com/ with a Global administrator, Intune administrator, or User administrator role in the Azure AD organization.
- Azure AD is now Entra ID – More details – What is Microsoft Entra ID?
- Select All groups, and select New Group.
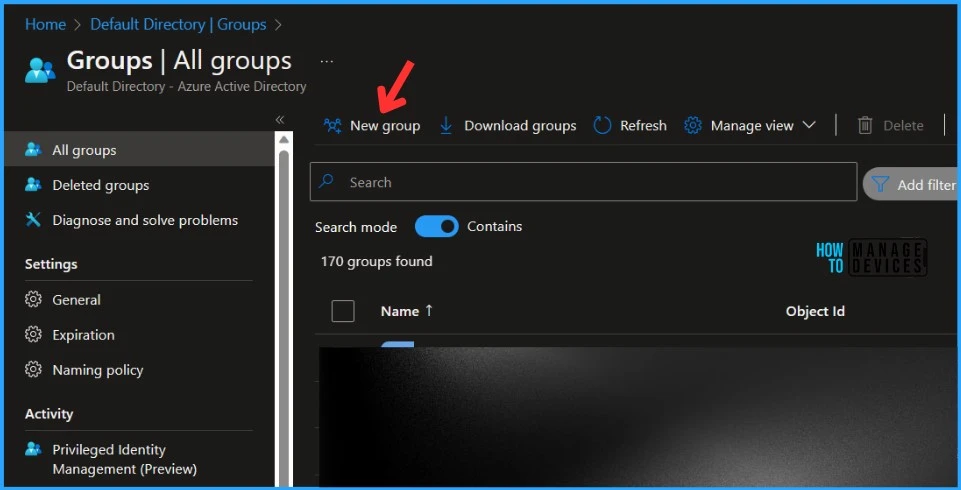
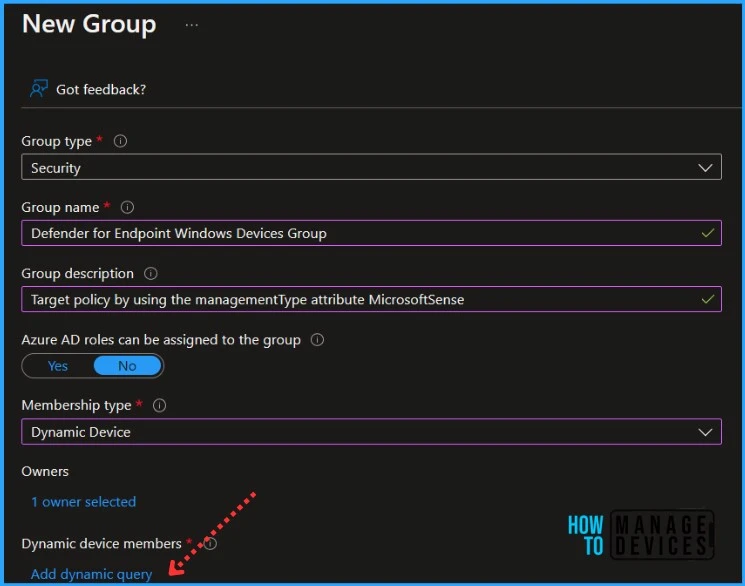
On the New Group, Add the required information to proceed for Dynamic Group. Click on Add Dynamic Query under Dynamic Device Members.
- Select Security – Group Type from the drop-down option.
- Enter Group Name “Defender for Endpoint Windows Devices Group” (Provide a suitable name).
- Enter Group Description, For Example, Target policy by using the managementType attribute MicrosoftSense.
- Select Dynamic Device as Membership type.
Note – You need to select Membership type as Dynamic Device or User to have Add dynamic query in this blade to appear.
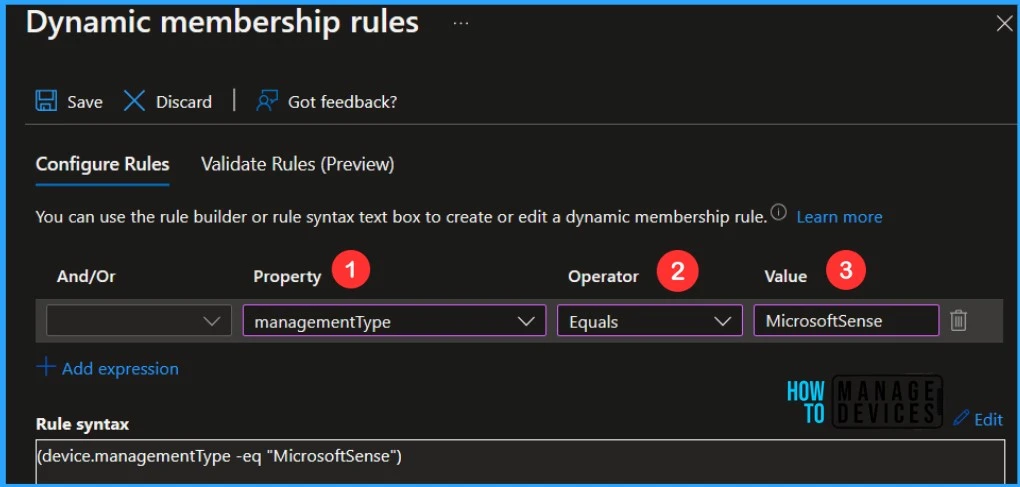
There are two options to build the Azure AD dynamic group query. You can use the rule builder or rule syntax text box to create or edit an AAD device group dynamic membership rule.
- Rule Builder – Graphical Interface, easy to create the dynamic query.
- Rule Syntax – Advanced technical users for complex queries.
You need to follow the steps mentioned below to use Azure AD dynamic group Rule Builder to create dynamic query rules.
- Under Configure Rules – Choose Property drop-down list.
- Select managementType as the property from the drop-down list.
It’s time to choose an Operator now for the managementType. I have selected Equals from the operator drop-down menu, and the Value should be MicrosoftSense.
| Device attribute | Values | Rules [For Example] |
|---|---|---|
| managementType | MicrosoftSense | (device.managementType -eq “MicrosoftSense”) |
On Validate Rules tab, Click on Add devices or Add users based on group selection to validate configured rules for the group.
- Validation results will appear and show whether a device or user is a member of the group or not. The result will show the Status as follows.
In group (✅Green Tick) - If a user or device satisfies a rule on a group, the result will show as In group.
Not in group (❌Red Cross).- If a user or device no longer satisfies the rule, the result will show as Not in group.
Unknown - If the rule is not valid or there is a network issue, the result will show as Unknown. 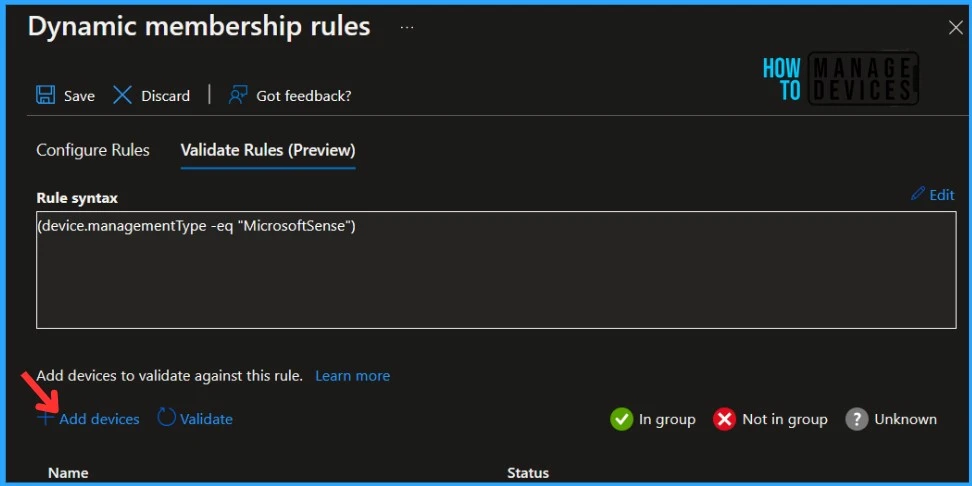
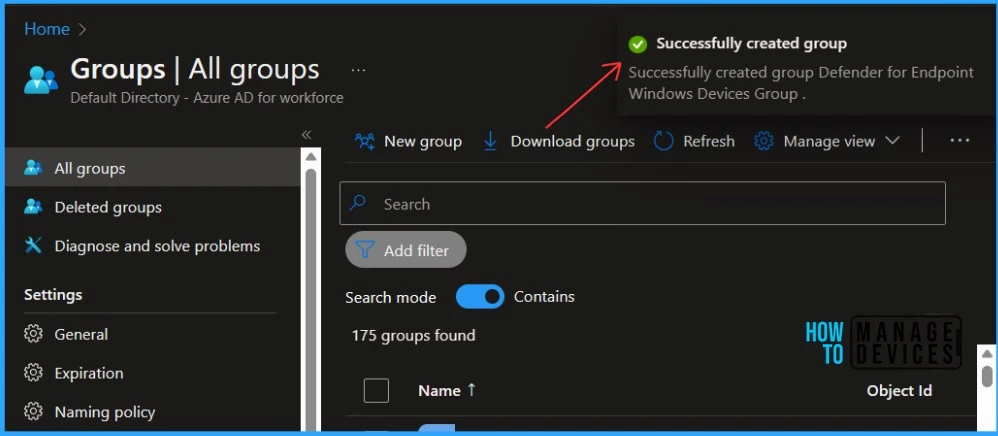
Click on SAVE and CREATE buttons to complete the process of building Azure AD dynamic device group creation. A notification will appear with a message, Successfully created group Defender for Endpoint Windows Devices Group.
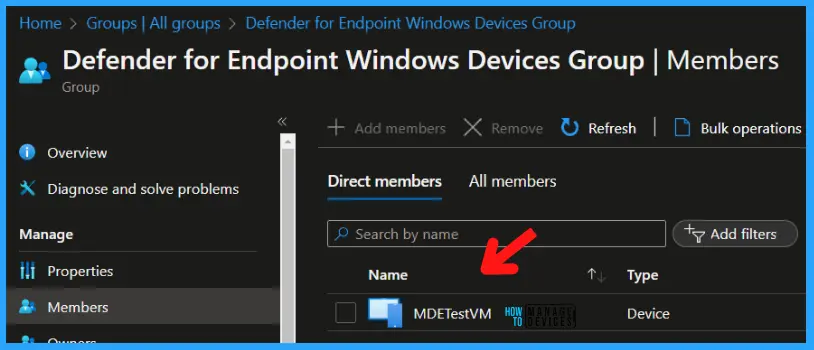
Now, the Azure AD Dynamic Device Group is created and managed by Defender for Endpoint. The devices meeting the defined criteria in the dynamic query will automatically be included in the group, and the associated device tag will indicate their management status within Defender for Endpoint.
Author
About Author – Jitesh, Microsoft MVP, has over six years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus is Windows 10/11 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.
