Let’s learn how to create the SCCM Collection using AD Group. The SCCM Dynamic collection can be created using AD Group.
In previous posts, I explained how to create static and dynamic collections. In this post, I will help you learn how to create an AD Group-Based SCCM Collection.
You must enable Active Directory Group discovery to use device collections based on Active Directory groups.
We can create an AD security group-based collection using dynamic and direct member query rules. You can also use the following method to create a dynamic SCCM Collection based on Active Directory OU | The Easy Way.
Table of Contents
How to Enable AD Security Group Discovery
You must enable Active Directory (AD) group discovery to create an AD group-based SCCM collection. If you have not enabled AD group discovery in your SCCM environment, you won’t be able to develop SCCM collections based on AD security groups.
- What is Collection, How to Create SCCM Direct Membership Collections
- How to create dynamic collections?
I’ve explained this discovery process in the video tutorial.
When you specify an AD group to discover, SCCM discovers the members of that AD security group and any nested AD security groups.
SCCM Active Directory Group Discovery
SCCM generates a user group resource record for a specific group. This discovery happens when the selected group is an AD security group.
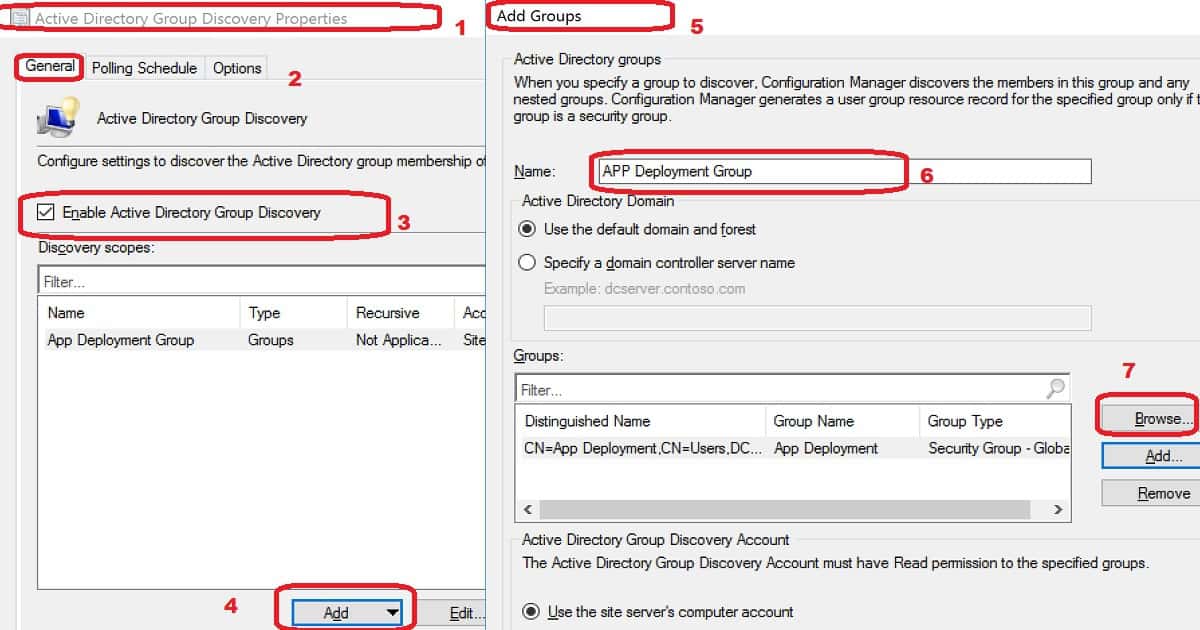
Open the SCCM Admin console and Navigate to \Administration\Overview\Hierarchy Configuration\Discovery Methods. Double-click or go to the properties of Active Directory Group Discovery.
In the Active Directory Group Discovery properties window, click on the checkmark near Enable Active Directory Group Discovery.
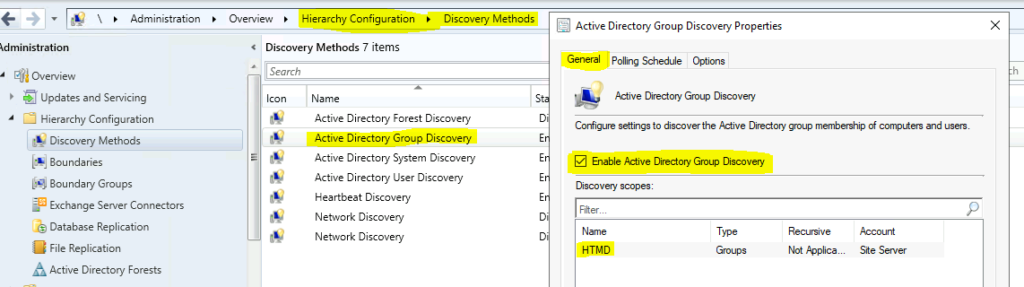
Click the ADD button at the bottom of the Active Directory Group Discovery properties window. Select either Groups or Location.
Select Groups, as I don’t want to discover all the AD security Groups in my AD environment. I will test this with one or two AD groups.
- Enter a Name for AD Security Group Discovery from the Add Group window
- Click on the Browse button to select an AD security group
- Select AD security Groups that you want to discover from the Select Groups windows
- Click OK and OK to close the Window
SCCM Active Directory Group Discovery Issue
Troubleshooting related to AD security group discovery can be started from the log file called adsgdis.log. Following is some of the extracts of important lines of the AD security group discovery log file.
!!!!Valid Search Scope Name: App Deployment Group Search Path: LDAP://CN=APP DEPLOYMENT,CN=USERS,DC=INTUNE,DC=COM IsValidPath: TRUE
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:25.151-330><thread=3804 (0xEDC)>
Starting the data discovery.~
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:25.153-330><thread=3804 (0xEDC)>
Connecting to site server’s (\\SCCM_Prod.Intune.com) registry~
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:25.157-330><thread=3804 (0xEDC)>
INFO: DDR was written for group ‘INTUNE\App Deployment’ – C:\Program Files\Microsoft Configuration Manager\inboxes\auth\ddm.box\userddrsonly\asg29mn6.DDR at 8/13/2018 9:53:24.~
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:25.511-330><thread=3804 (0xEDC)>
INFO: Successfully updated the Group membership tables for group ‘INTUNE\App Deployment’
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:26.030-330><thread=3804 (0xEDC)>
INFO: CADSource::fullSync returning 0x00000000~
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:26.108-330><thread=3804 (0xEDC)>
INFO: AD Discovery under container LDAP://CN=APP DEPLOYMENT,CN=USERS,DC=INTUNE,DC=COM found 1 objects
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:26.111-330><thread=3804 (0xEDC)>
INFO: Succeed to update immediate groups of search scope App Deployment Group into DB.
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:26.204-330><thread=3804 (0xEDC)>
INFO: Succeed to save all immediate search bases into DB.
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:26.250-330><thread=3804 (0xEDC)>
INFO: ——– Finished to process search scope (App Deployment Group) ——–
lt;SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT><08-13-2018 09:53:26.256-330><thread=3804 (0xEDC)>
Video Tutorial – AD Group-Based SCCM Collection
Create Direct Membership for User Collection Using AD Security Group
I would recommend following the steps to complete the creation of the SCCM User Collection using the Active Directory user group.
Please ensure you have completed the AD User discovery before creating this user collection. I explain this discovery process in the video tutorial.
AD Group Based SCCM Collection process is given below:-
Navigate to the SCCM console – Assets and Compliance – User Collections. Right-click and select “Create User Collection” from the Device Collections node.
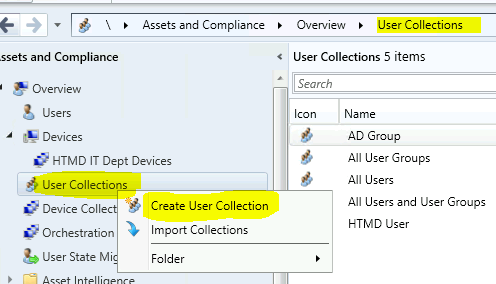
On the General page, provide a Name and a Comment. Then, in the Limiting collection, choose Browse to select a limiting collection. The collection will only contain members from that collection.
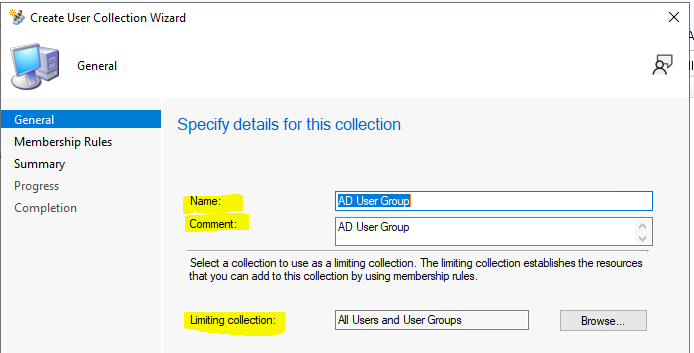
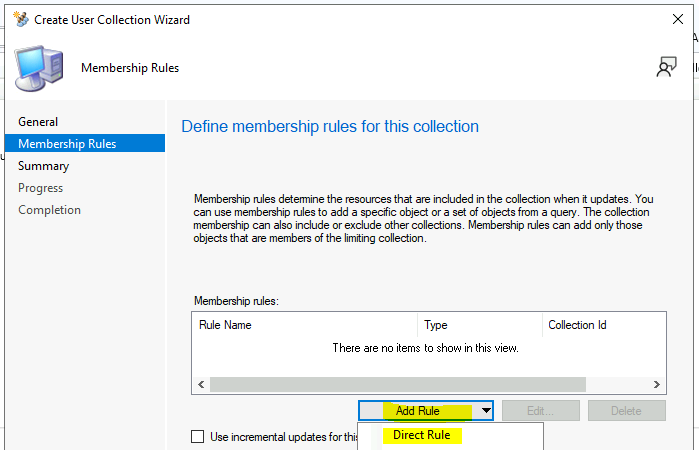
On the Membership Rules page of the Create User Collection Wizard, in the Add Rule list, select the type DIRECT membership rule for this collection. You can configure multiple rules for each collection.
Select Direct Rule in the Add Rule list on the Membership Rules page of the Create User Collection Wizard.
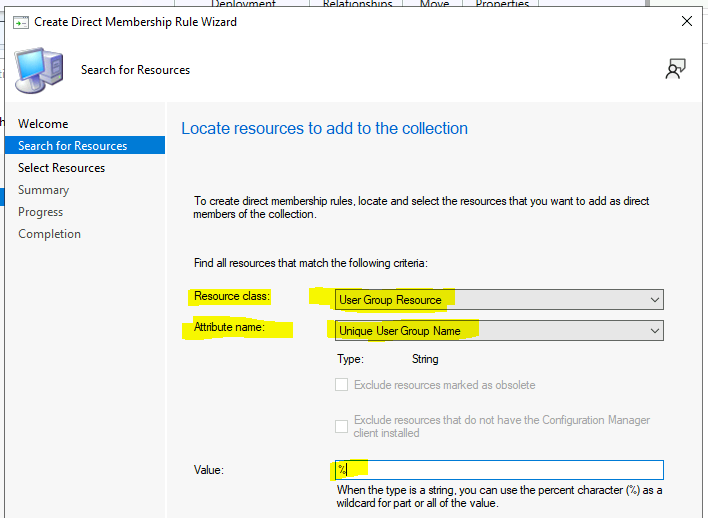
On the Search for Resources page of the Create Direct Membership Rule Wizard, specify the following information: 7-10 steps. By the end of the 11th step, you can create a static AD Group-Based SCCM Collection.
Check the drop-down options for the Resource class: Select the type of resource you want to search for and add to the collection. Select from User Group Resource values to search for inventory data returned from client computers.
Check the drop-down options for Attribute name: Select the attribute associated with the selected resource class that you want to search for. For example, if you choose computers by their NetBIOS name, select Group User Resource in the Resource class list and Unique User Group Name in the Attribute name list.
Enter the Value: Enter a value for which you want to search the selected attribute name. You can use the percent character % as a wildcard. Click the NEXT button. For example, to search for computers with a NetBIOS name beginning with “M,” enter M% in this field.
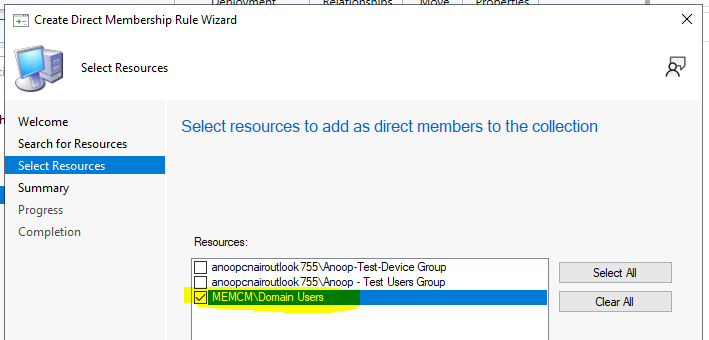
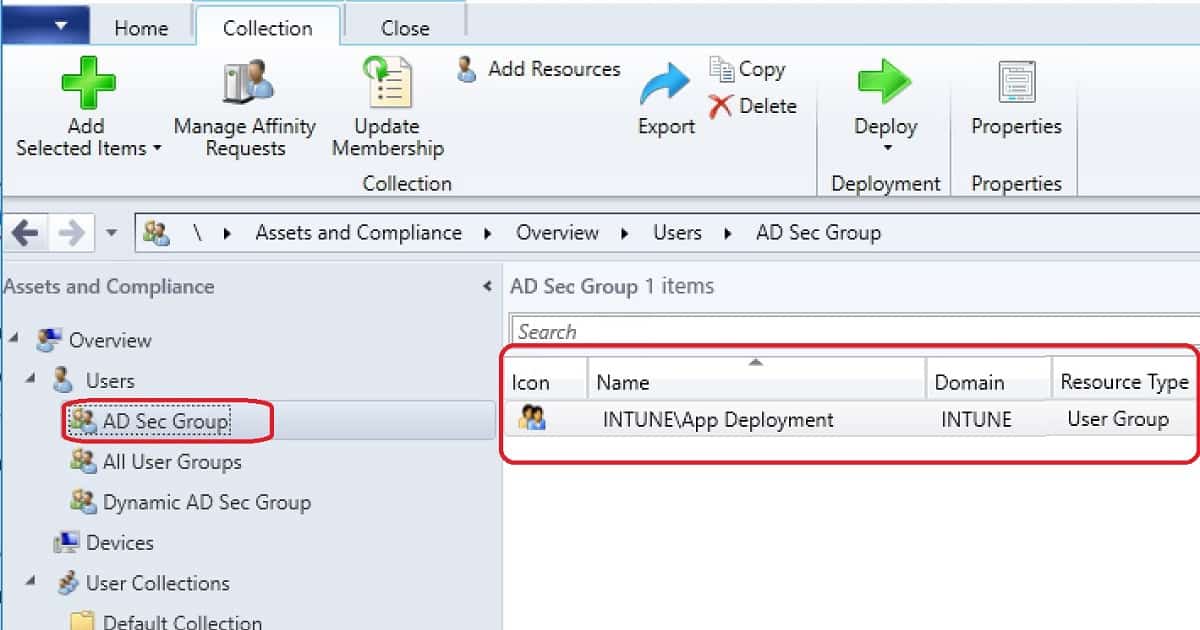
Select the AD Security Group you want to add as a member of the user collection on the Select Resources page. This group will be added to the Resources list collection, and then choose Next and NEXT to complete the wizard.
NOTE:– If AD Group Discovery is not completed, you won’t be able to see any groups on this page.
Click on Close and OK to complete the AD Security Group-based collection creation.
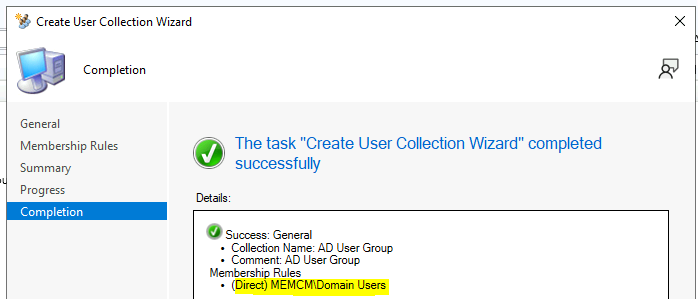
End Result of Static Membership Query – AD Security Group Based User Collection:-
AD Group Based SCCM Collection – Direct Membership Rule. I’ve explained this discovery process in the video tutorial.
[Related posts – What is Collection, How to Create SCCM Static Collections, and How to create dynamic collections?]
Create Dynamic Membership Query for User Collection Using AD Security Group
The second part of the AD Group-Based SCCM Collection creation is explained below. This user collection is created using a dynamic collection WQL query. You may need to keep the default update schedule for this type of use collection.
I’ve explained this discovery process in the video tutorial.
Navigate to the SCCM console – Assets and Compliance – User Collections. Right-click and select “Create User Collection” from the User Collections node.
On the General page, provide a Name and a Comment. Then, in the Limiting collection, choose Browse to select a limiting collection. The collection will only contain members from that collection.
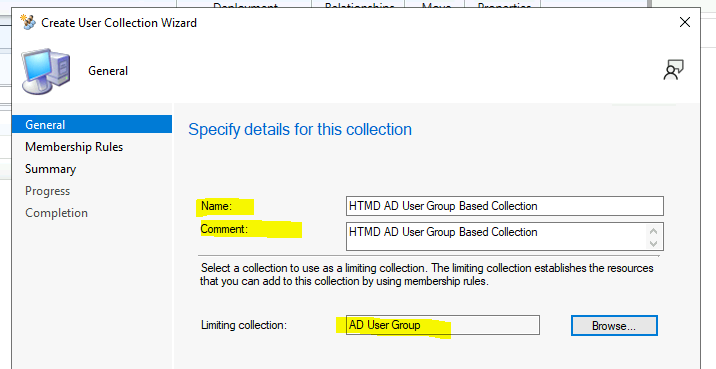
On the Membership Rules page of the Create User Collection Wizard, in the Add Rule list, select the Query Rule membership rule type for this collection. You can configure multiple rules for each collection.
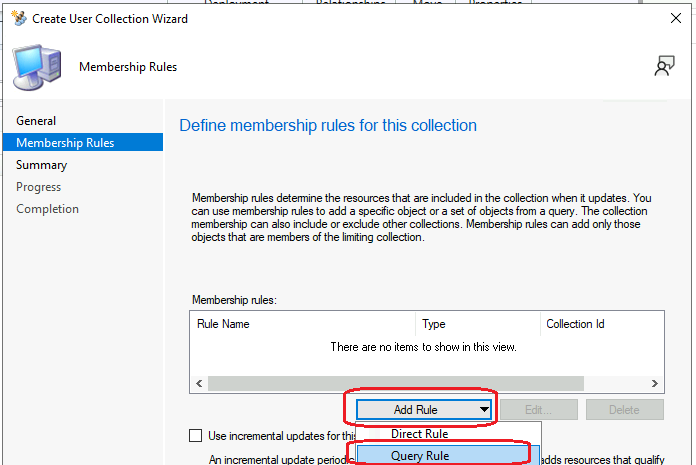
On the Membership Rules page of the Create User Collection Wizard, in the Add Rule list, select Query Rule.
On the Query Rule Properties windows, specify the following information. Name: Specify a unique name. By the end of the 11th step, you can create a dynamic AD Group Based SCCM Collection.
Resource class: Select the type of resource you want to search for and add to the collection. You must select User Resource to create a Dynamic User Collection in SCCM.
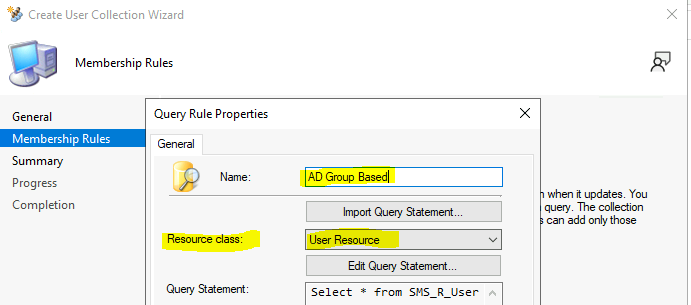
Click Edit Query Statement to open the Query Statement Properties dialog box, where you can create a query to use as the rule for the SCCM user dynamic collection.
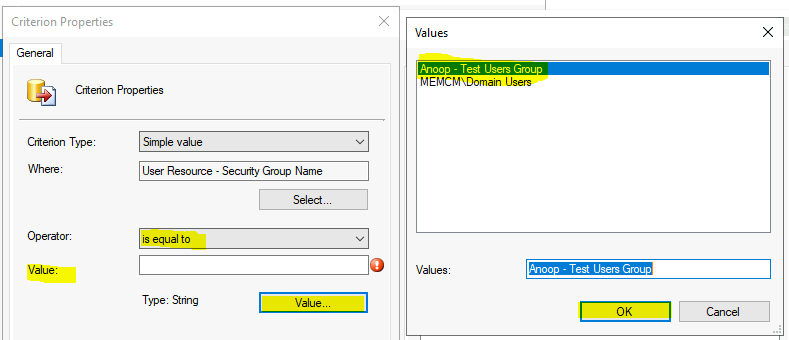
On Query Statement Properties, click on the Criteria tab. Click on the Criteria Properties dialog and click on the * button to start creating dynamic rules on the Criteria Properties dialog.
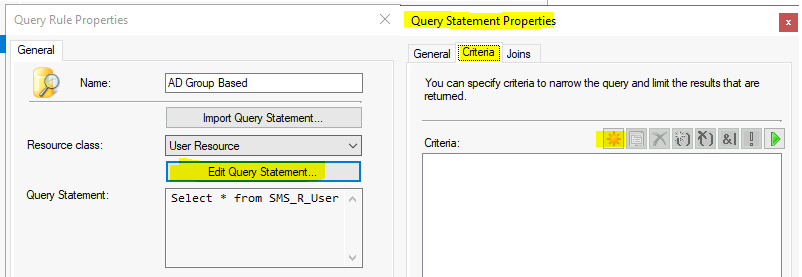
- Select Criteria Value as Simple Value.
- The dialog box clicks the Select button on the Criteria Properties to open the Attribute Dialog box.
- On the Attribute Dialog box, select the Attribute class as User Resource and Alias as = No Alias.
- Select Attribute as Security Group. Click OK to close the Select Attribute Dialog box.
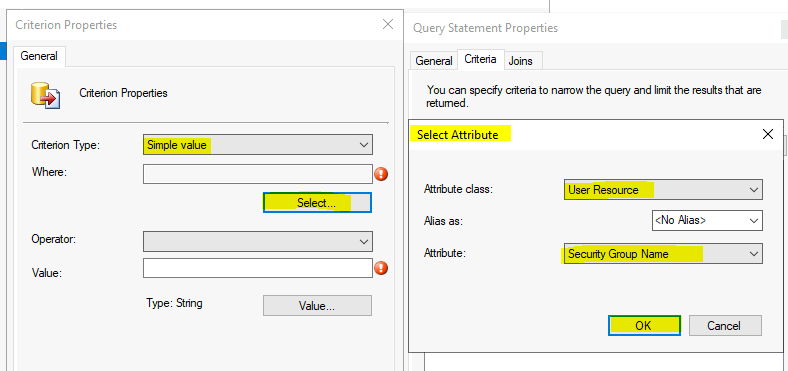
The dialog box selects Operator “is equal to ” on the Criteria Properties. “ Is Like is not the operator which gives you the best performance.
Click on the Value button and find out the available AD security groups. Select the AD security group for your collection creation.
WQL Query Based on AD Security Group Collection
Let’s find the details of the WQL query based on the AD security SCCM collection.
select * from SMS_R_User where SMS_R_User.SecurityGroupName = "Anoop - Test Users Group"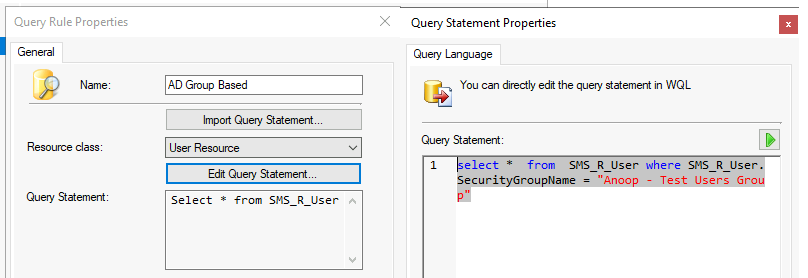
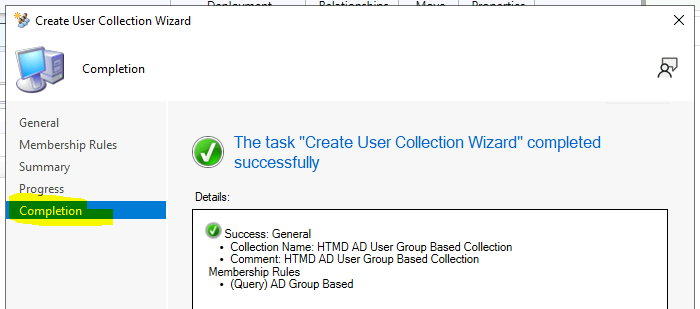
Complete – AD Group-based SCCM Collection
Let’s complete the Complete – AD Group-based SCCM Collection.
Click OK, OK, and OK to close all dialog boxes on the Membership Rule page and click on NEXT. Click NEXT, NEXT, and Close to finish the Create User Collection Wizard.
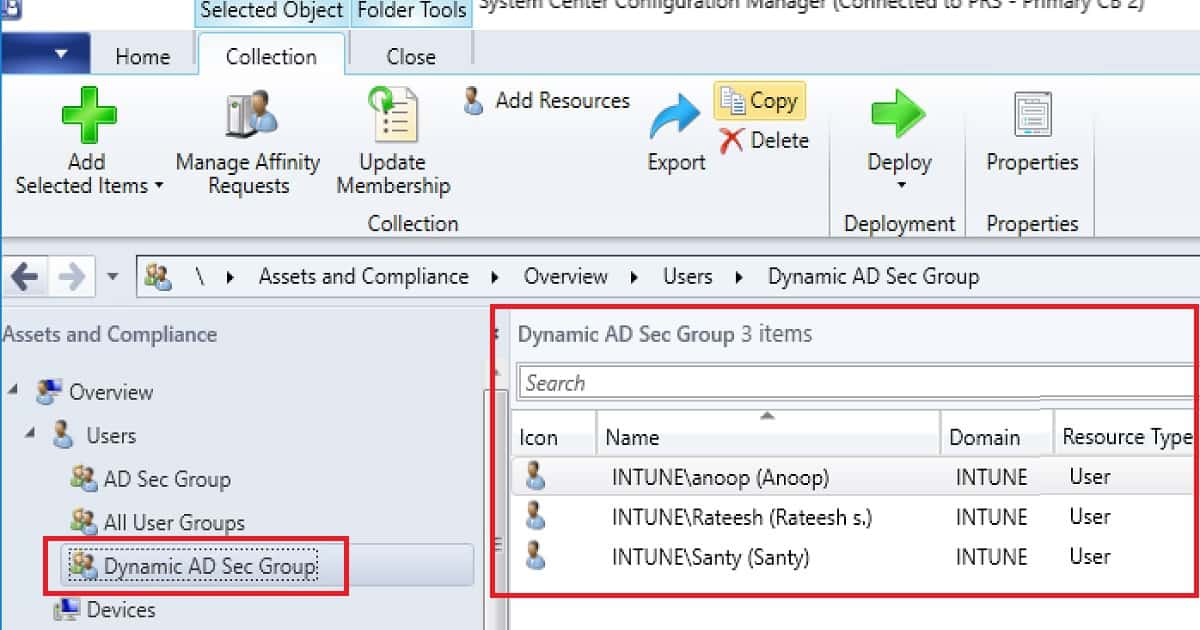
End Result of SCCM User Collection Based on Query Rule
The AD Group-Based SCCM Collection with query rule dynamic member rule results are below.
select * from SMS_R_User where SMS_R_User.SecurityGroupName = “INTUNE\\App Deployment”
Resources
- ConfigMgr–User collection and direct membership for Security Group
- Create SCCM Static Collections (Programmatically or using a script)
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His primary focus is Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.

Hey, another great article thank-you! This is very interesting.
The only reason I can think of not to use direct membership for AD groups is for uninstalls.
We use AD groups + query rule to populate, and an uninstall collection which populates if the software is installed but is not a member of the “install” collection (exclude rule).
So I guess my question is, is there a way you can think of to cater for automatically uninstalling applications if a user is removed from the AD group?
Great work thanks for the article.
Happy that you liked it. Can you tell me what is the next guide you want from me?
Hi Anoop,
Mate I am not able to locate ‘User Resource’
Raghu
Hi, great article. We use AD groups to populate patching device collections via a query. As such, a server must only be in one AD group to pick up an appropriate maintenance window. Do you know of a way to check if a server is in multiple device collections (so I can weed out my finger faults!)? Thanks
Hi Anoop! I tried this method and it works well in the AD security group, it also replicates the number of members in the collection vs the number in AD Security group. But my problem is when I remove or delete a member in the AD Security group, it does not replicated in the collection. Am I doing something wrong?
Ah ok … does this mean it doesn’t remove the members of collection if you change some membership changes in ad group. I don’t think there is any specific configuration you need to put in for this. I don’t remember whether I tested this scenario or not. Did you see some details in the log files ? Also did you try full sync ?
I see based on group type attribute, you are using global scope security groups…have you had success with Domain Local and Universal as well? and/or nested group membership?
I am having real troubles figuring out why this isn’t working for Domain local at the moment.
Arker, if you are using a device collection you won’t see resource = user.