Let’s discuss how to Assign Custom Intune Role Based Access to Azure AD Groups using Microsoft Entra PIMThis post will help you assign and activate Intune custom roles to Entra AD groups using Azure AD PIM. Let’s see how you can assign an Intune RBAC Role to an Azure AD group and configure Privileged Identity Management PIM for the groups to activate the RBAC role for users.
Privileged Identity Management (PIM) is a service in Microsoft Entra that enables you to control, monitor, and manage access to the organization’s resources. These resources can be in Microsoft Entra ID, Microsoft Azure, Microsoft 365, or Microsoft Intune.
Privileged Identity Management provides us with the flexibility to assign Roles explicitly. Let’s assume we want to provide Intune Role access to users only for a specific time period and make sure they specifically elevate access when needed. In that case, PIM can assign the role as an Active assignment.
PIM can inform you of important events in Microsoft Entra, like the roles assigned or activated. You can do Role Assignation, Activation, Approval, Auditing and create alerts of the assignments using Microsoft PIM.

Table of Contents
Before You Get Started
Before we get started, there are a few license details that we should consider before configuring the Microsoft Entra ID PIM in our environment. These licenses are generally a pre-requisite for PIM and are not specific to Entra ID Group-based PIM access.
- Assign Azure AD Inbuilt Roles using PIM
- Create Custom Intune Role
- Intune Support for Endpoint Privilege Management
- Download Intune Configuration Spreadsheet Excel List of Policies Configurations
Below are the Microsoft Entra ID Governance licenses required to use Microsoft Entra ID PIM. For more on licensing details for using Entra ID PIM, refer to Microsoft Entra ID governance licensing fundamentals.
| Microsoft Entra ID Governance license required for using PIM |
|---|
| Microsoft Entra ID P2 – Users assigned to an access review |
| Microsoft Entra ID P2 – Users who perform access reviews |
| Microsoft Entra ID P2 – Users able to approve or reject activation requests in PIM |
| Microsoft Entra ID P2 – Users with eligible and/or time-bound assignments as members or owners of PIM for Groups |
Configure the Microsoft Entra ID Group for using PIM
Let’s create a test group in Microsoft Entra ID, which we are going to use for the Intune Custom role assignment. We will configure the same group for PIM so that users can get access to the Intune role as per the assignment. When assigned, the user will authenticate for this group using PIM and become part of the group for a specific time.
Navigate to Portal.azure.com >> Microsoft Entra ID >> Groups and click on New Group, where we must provide group details. For testing, we are giving the group name “Test Intune RBAC using PIM” and keeping the membership as assigned. If you want, you can add a description for the group for better understanding.
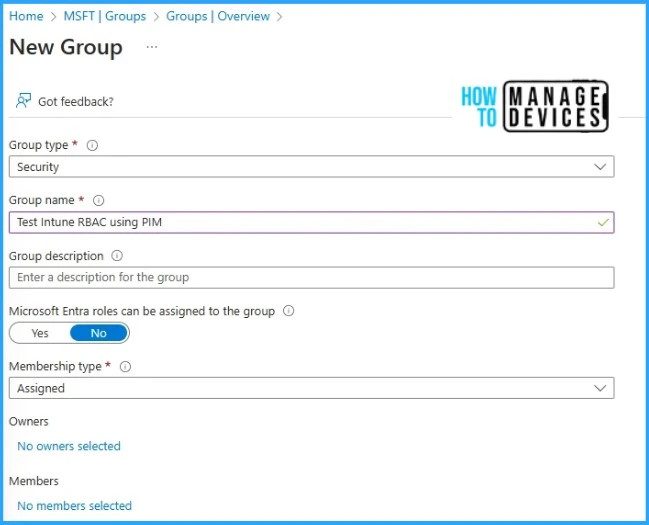
Once the group is created, Go to the activity tab in group properties and click on the Privileged Identity Management option. From there, we will have to enable PIM for the group, which will enable access to the group’s ownership or membership using PIM.
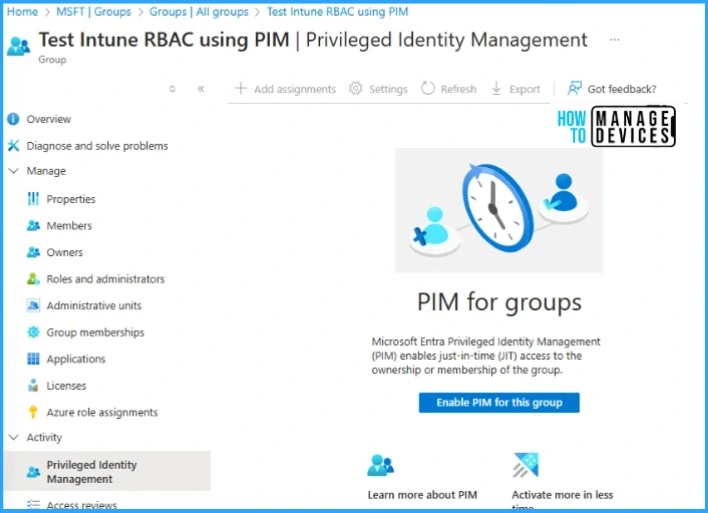
Once the PIM is enabled for the group, we can add assignments. This is the same as assigning Microsoft Entra ID roles using PIM, where we can add the assignments as eligible or active. For more details on assigning Entra ID roles via PIM, please check Assign Azure AD Roles Using Privileged Identity Management PIM.
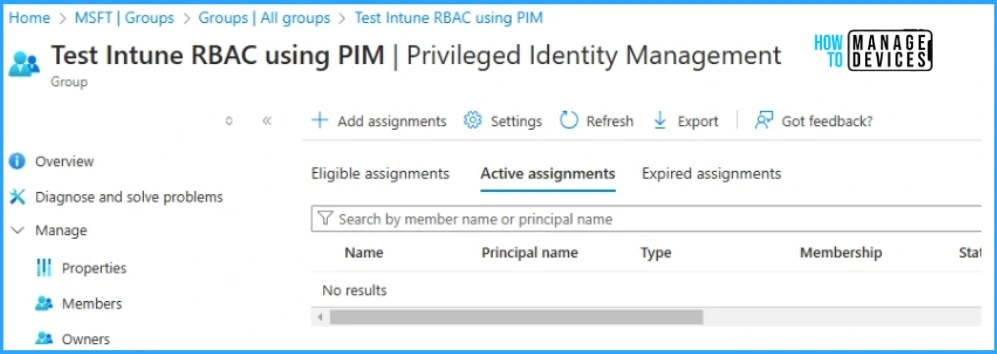
In short, Eligible assignments require the user to authenticate to elevate or activate the membership access, while active assignments give the user permanent access without any elevation or activation. In this post, we are going to add an Eligible assignment for testing purposes.
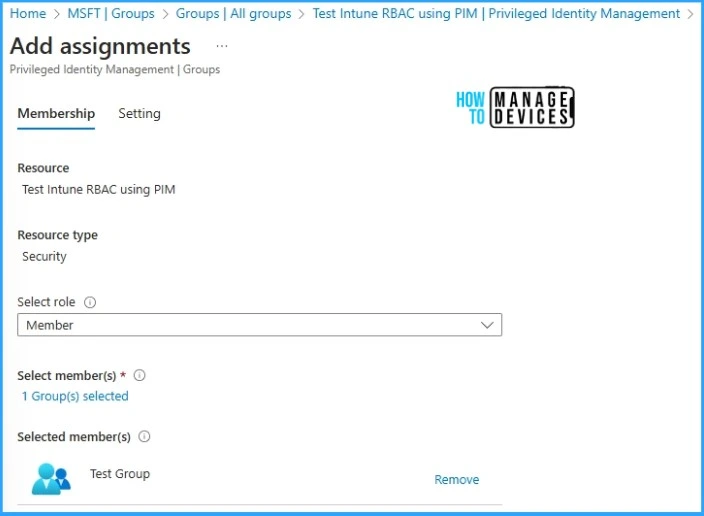
Here, we are adding the role of member because we want to manage the Intune Custom Role assignation/activation for specific users or User groups. So this means that any user who is part of our “Test Group” can activate the membership to this “Test Intune RBAC Using PIM” Entra ID group using PIM.
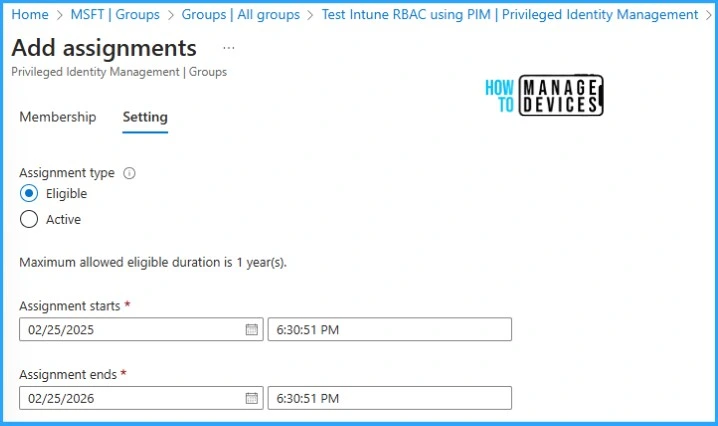
Under the settings tab, we can change the assignment type to Eligible or active. As mentioned, we are keeping it Eligible for just-in-time assignment testing. You can also change the assignment window. By default, it’s one year, but you can customize it as per the requirement.
Our Microsoft Entra ID group is ready with PIM. Let’s add some users to the selected test group. We have just added one test user to the group for now, but we can keep using this group in the future for role assignments as per the requirement.
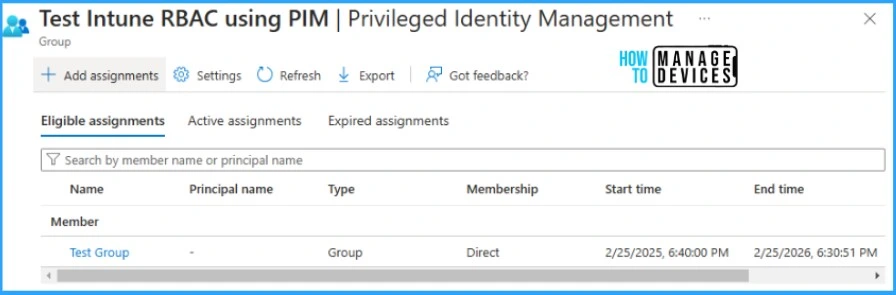
Assign Intune Custom Role to Entra ID PIM enabled Group
Before proceeding, make sure you have a custom Intune role created as per the requirement. You can also use inbuilt Intune admin roles using this assignation method. In this post, we are going to assign a custom Intune Application admin role to our test group. For more details on custom Intune role creation and assignation, check out how to create Custom Intune Role access.
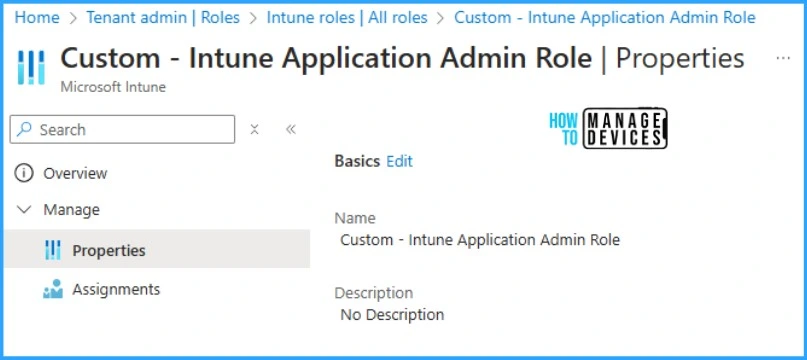
Let’s navigate to Intune portal >> Tenant Administration >> Roles >> Select the role you want to assign to the PIM-enabled Entra ID group >> Assignments >> Assign.
Provide the basic details required for the assignment, such as the Assignment name and description. In the admin group section, select the newly created PIM-enabled Entra ID group. In the scope group, you can add a parent group of the PIM-enabled group or the same test group. We have added the same group in both the Admin and scope groups options.
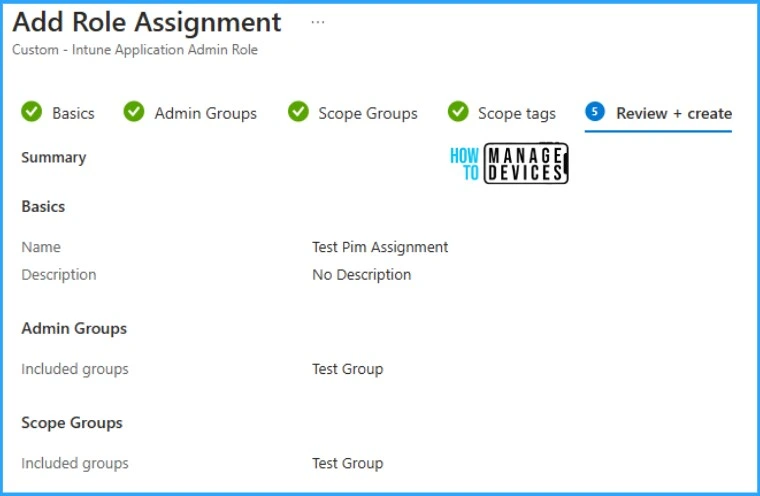
Activate User Assignment via Entra ID PIM
The next step is for the users of the PIM-enabled group to activate the assignment from the Microsoft Entra ID PIM portal. This is how it works: When the user activates the assignment for the group from Microsoft Entra PIM, the PIM service adds the user to the Entra ID group for the time being as per the assignment type. Once the user is part of the Entra ID group, the Intune Role assignation will take place.
Let’s log in tothe Intune portal using Test User 1 and navigate to Tenant Administration >> Microsoft Entra PIM >> My Roles >> Groups >> Activate required Role.
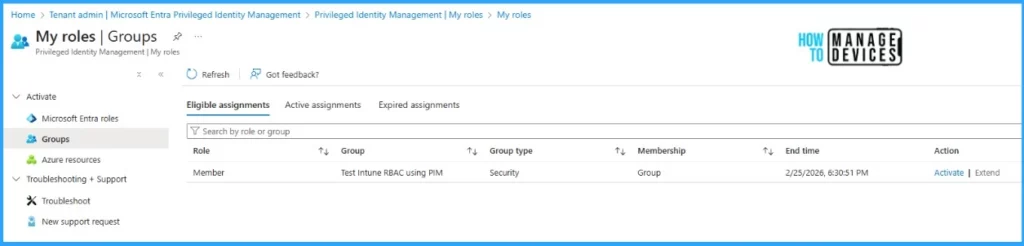
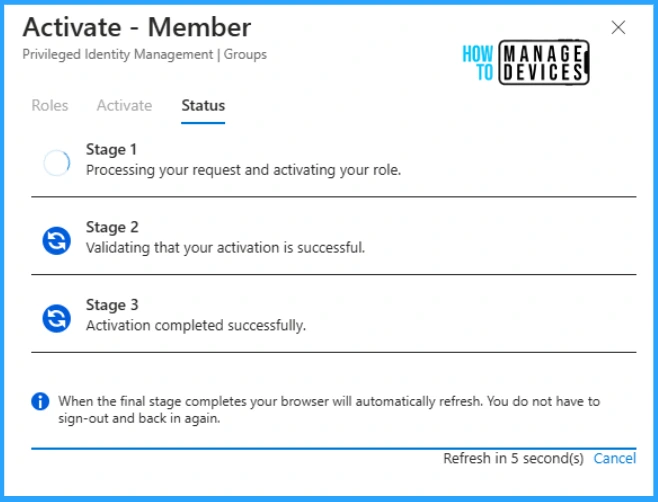
Provide comments to justify the activation of the role and time window, which can be 0.5 hours to 8 hours. These comments will be saved in PIM logs for monitoring purposes. The activation process may require you to authenticate again with your credentials and MFA per the organization’s policy.
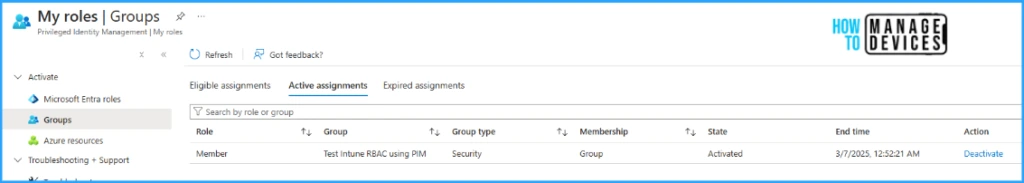
Once the group-based role is activated for the user, we will be able to see the active assignments in the PIM >> Groups >> Active assignments tab, along with their end time. From this tab, we can also deactivate the role if required.
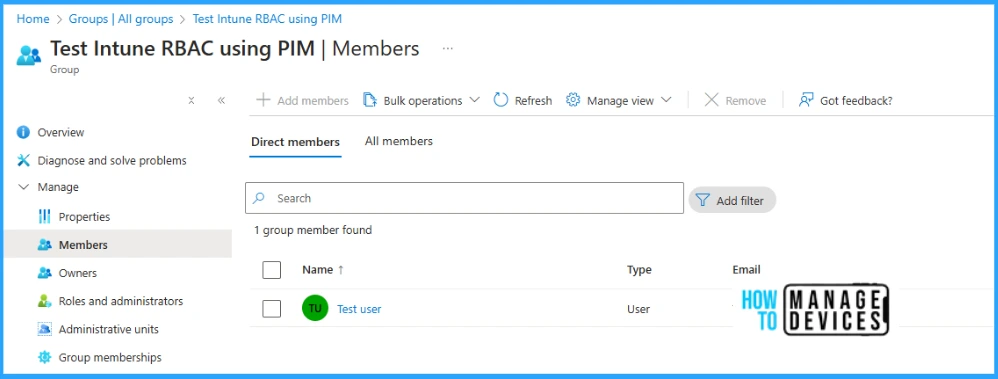
After successfully activating the group-based PIM role, we can see the test user is now automatically added as a member of the “Test Intune RBAC using PIM” Entra ID group, where we assigned Intune Custome role-based access. So now, the test user inherits the Intune Custome Role-based permissions.
This is how we can assign Entra ID inbuilt or Custom roles to groups, which is very beneficial while working in a complex or process-oriented infrastructure. I hope this post was beneficial for you. I appreciate your patience in reading it.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Sachin Chauhan is a Microsoft-certified professional and Modern Device Management Consultant with over 10 years of experience in Microsoft technologies like MECM, Intune, Windows OS, Autopilot, Operating system deployments and management, Azure, and PowerShell Automation.
