Let’s see what new updates to BitLocker Recovery Key Process for Windows Autopilot, and how BitLocker resets occur for re-used Windows Autopilot devices. Intune provides insights into the status of BitLocker recovery key for the managed device encrypted with Bitlocker.
By the information provided in MC667125, Microsoft Intune has introduced a new Plan for Change for the updates to Intune on how BitLocker resets occur for re-used Windows Autopilot devices. These changes started rolling out, effective from the September update.
If the question comes to your mind, what would the impact of change be? There will be no major impact on the tenant or user. This change will only affect users who have been allowed self-service recovery of BitLocker keys during Autopilot, specifically in the case of a device restore or reset.
Microsoft recently released a new experience creating new BitLocker profiles for endpoint security Disk Encryption policy. The experience for editing your previously created BitLocker policy remains the same, and you can continue to use them, Let’s check New BitLocker Disk Encryption Policy For Intune Endpoint Security.
- New BitLocker Disk Encryption Policy For Intune Endpoint Security
- Turn Off Store Application Setting To Disable End User Access To Store Apps Using Intune Policy
Plan for Change: Update to BitLocker Recovery Key Process for Windows Autopilot
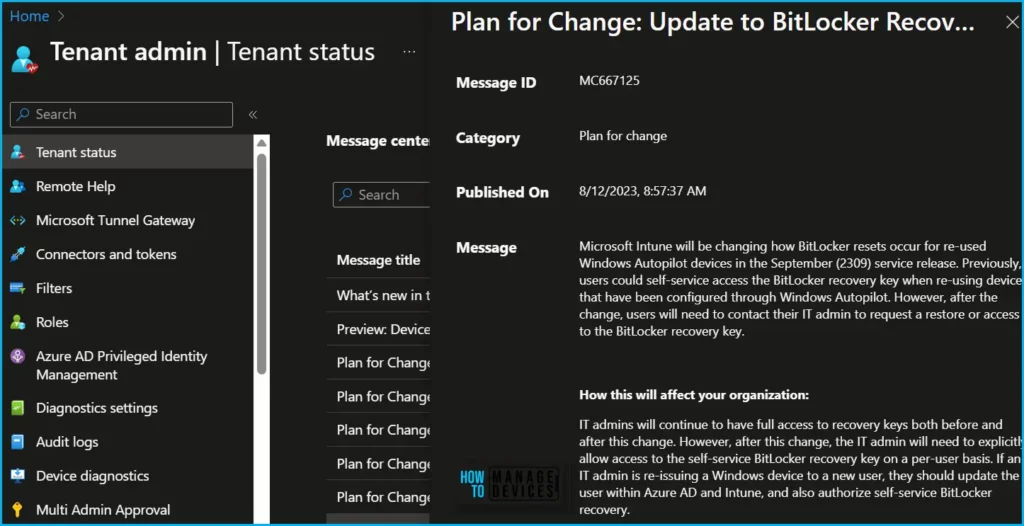
As mentioned in MC667125, Intune will be changing how BitLocker resets occur for re-used Windows Autopilot devices in the Intune September (2309) service release.
| Message | Service | Category | Published | Message ID |
|---|---|---|---|---|
| Plan for Change: Update to BitLocker Recovery Key Process for Windows Autopilot | Microsoft Intune | Plan for change | 8/12/2023 | MC667125 |
Microsoft Intune will be changing how BitLocker resets occur for re-used Windows Autopilot devices in the September (2309) service release. Previously, users could self-service access the BitLocker recovery key when re-using devices that have been configured through Windows Autopilot. However, after the change, users will need to contact their IT admin to request a restore or access to the BitLocker recovery key.

How this will affect your organization: IT admins will continue to have full access to recovery keys both before and after this change. However, after this change, the IT admin will need to explicitly allow access to the self-service BitLocker recovery key on a per-user basis. If an IT admin is re-issuing a Windows device to a new user, they should update the user within Azure AD and Intune, and also authorize self-service BitLocker recovery.
User impact: This change will only affect users who have been allowed self-service recovery of BitLocker keys during Autopilot, specifically in the case of a device restore or reset.
What you need to do to prepare: To ensure a smooth transition, please notify your helpdesk of this change. Additionally, update your documentation to one of the following options:
- Temporarily note the BitLocker recovery key prior to a restore as documented BitLocker recovery guide – Windows Security | Microsoft Learn.
- Contact the helpdesk or IT Admin to unlock self-service access.
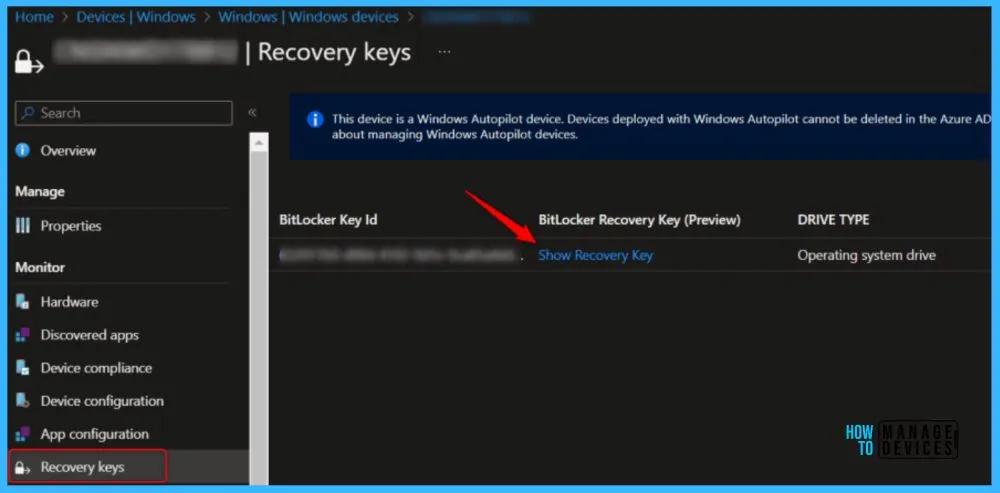
Find BitLocker Recovery Key in Intune
BitLocker Recovery Key Reader roles have required to help ensure that only an authorized person can unlock your Windows PC and restore access to your encrypted data. You need to create a custom role to read BitLocker Keys for managed devices.
Microsoft also added support to hide recovery keys from end users. This helps improve the devices’ security poster and prevents attackers from getting Bitlocker encryption keys from Windows devices.
Here’s how you can assign Azure AD Roles. The Azure AD PIM service also allows Privileged role administrators to make permanent admin role assignments, Assign Azure AD Roles Using Privileged Identity Management PIM
Author
About Author – Jitesh, Microsoft MVP, has over six years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus is Windows 10/11 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.
