Let’s learn how you can create Turn off the Store application policy in Intune. You can use the Turn off Store application setting to disable end user access to Store apps, and allow managed Intune Store apps.
The enhanced app management experience within Intune, utilizing the powerful capabilities of the Windows Package Manager. These improvements aim to provide users with a seamless way to manage applications within the Microsoft Store, In Intune, you can use the new Store app type to deploy Store apps to your devices.
Now, you can use the Turn off the Store application policy to disable end users’ direct access to Store apps. When it’s disabled, end users can still access and install Store apps from the Company Portal app and through Intune app management. Don’t configure this policy if you want to allow random store app installs outside of Intune.
The previous Only display the private store within the Microsoft Store app policy doesn’t prevent end users from directly accessing the store using the Windows Package Manager winget APIs. There is no need to install WinGet separately, as the essential WinGet functionality required for the new Store integration in Intune is already included as part of the Intune Management Extension.
So, if your goal is to block random unmanaged Store application installs on client devices, then it’s recommended to use the Turn off the Store application policy. Don’t use the Only display the private store within the Microsoft Store app policy.
- Why Is Software Inventory Missing From Intune Portal?
- Intune Remote Help Available For OOBE Screen During Windows Autopilot Scenario
Turn Off Store Applications using Intune
To disable end users direct access to Store apps, You can leverage the policy to turn off store application from Microsoft Intune. Turning off the policy does not affect the installation of store apps from Intune. Here are the steps you can follow:
- Sign in to the Microsoft Intune Admin portal https://intune.microsoft.com/.
- Select Devices > Configuration profiles > Create profile.
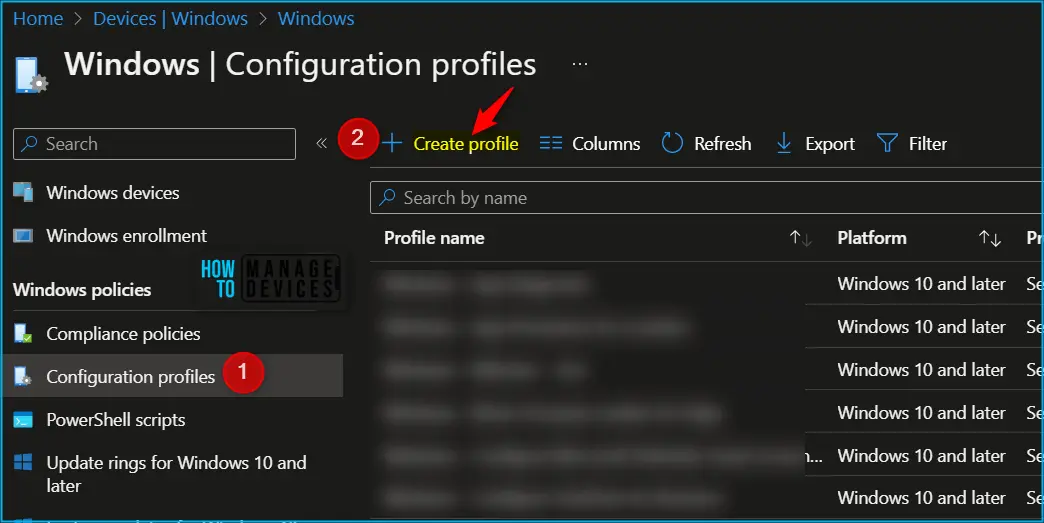
In Create Profile, Select Windows 10 and later in Platform, Select Profile Type as Settings Catalog. Click on Create button.
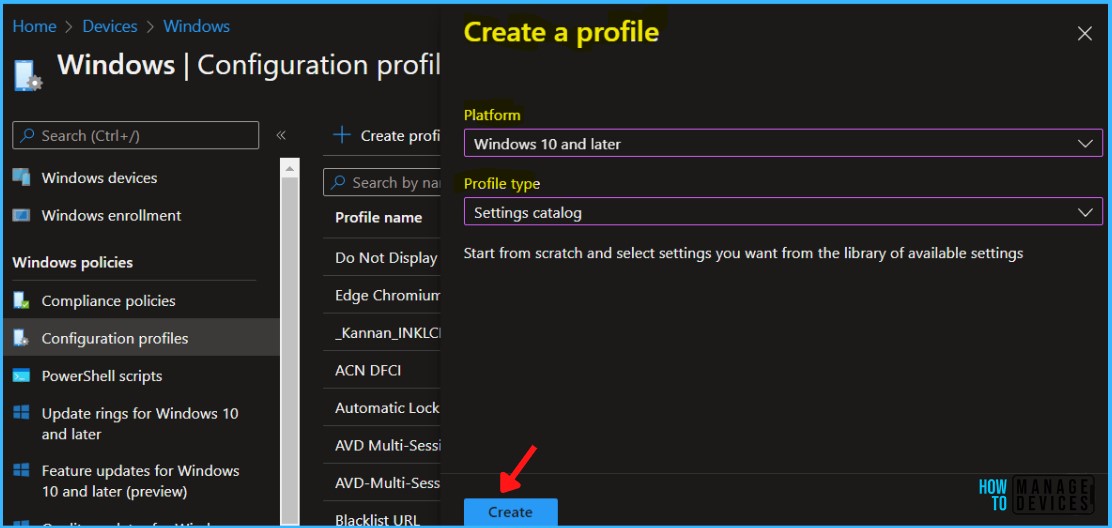
In Basics, enter the descriptive name for the new profile. For example, Turn off Store Applications, Description, and add a description for the profile to understand the policy usage and Select Next.
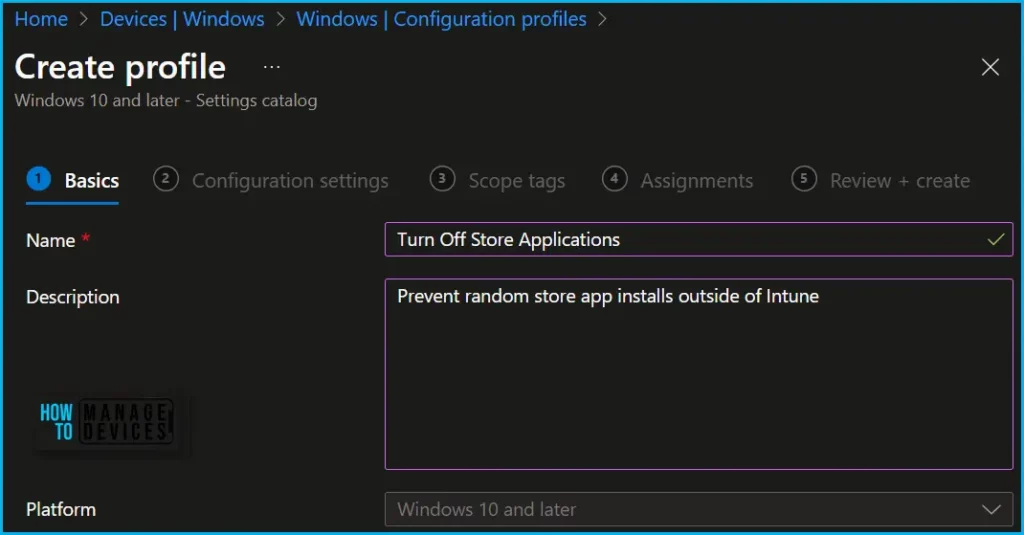
On the Configuration settings tab, With the settings catalog, you can choose which settings you want to configure. Click on Add Settings to browse or search the catalog for the settings you want to configure.
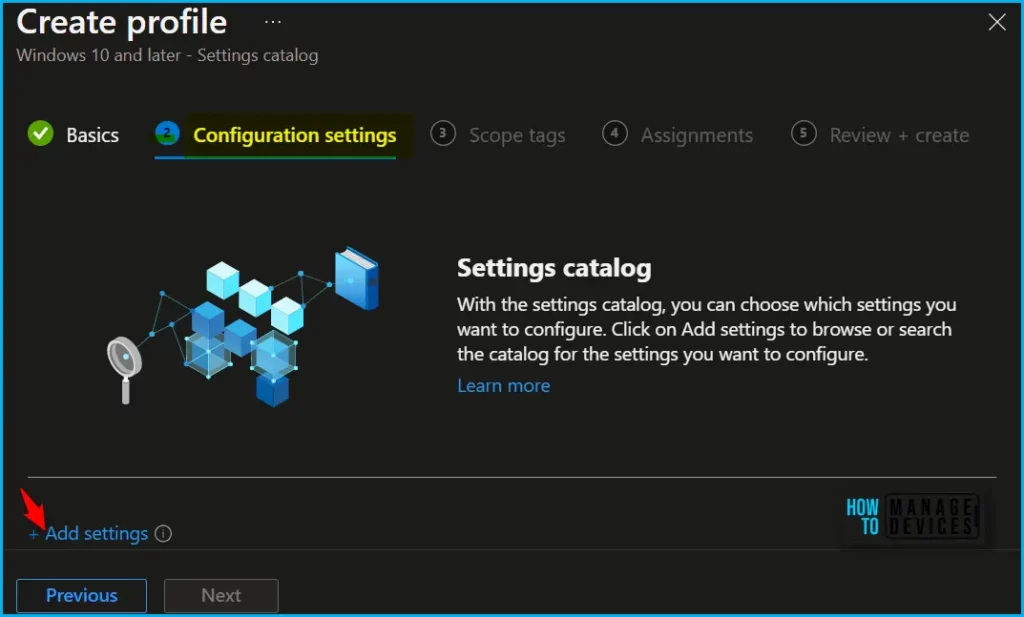
Search for “Store App or “Store Application”. Select the search result for “Adminstrative Templates\Windows Components\Store” You may find similar settings, device or user. Select the search results for Store, Select “Turn off Store application” and close the pane.
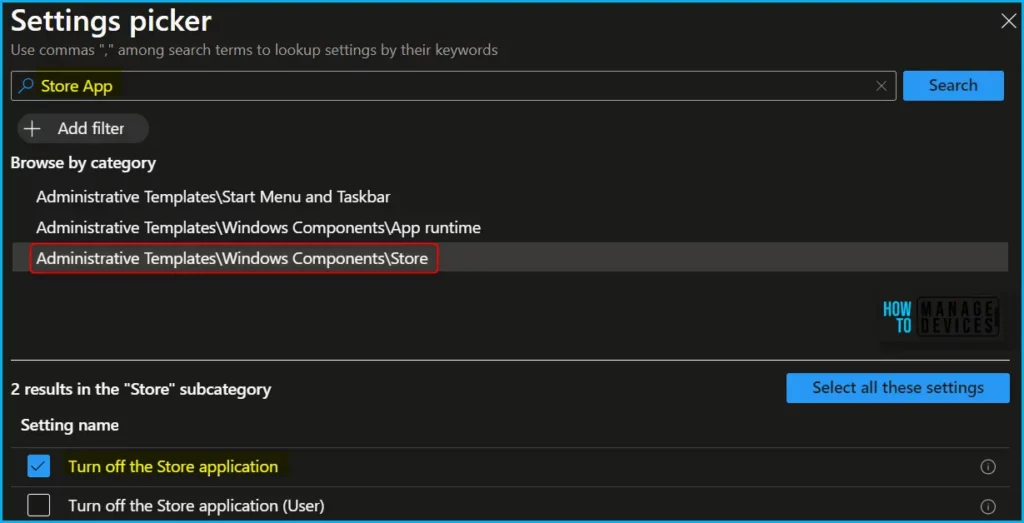
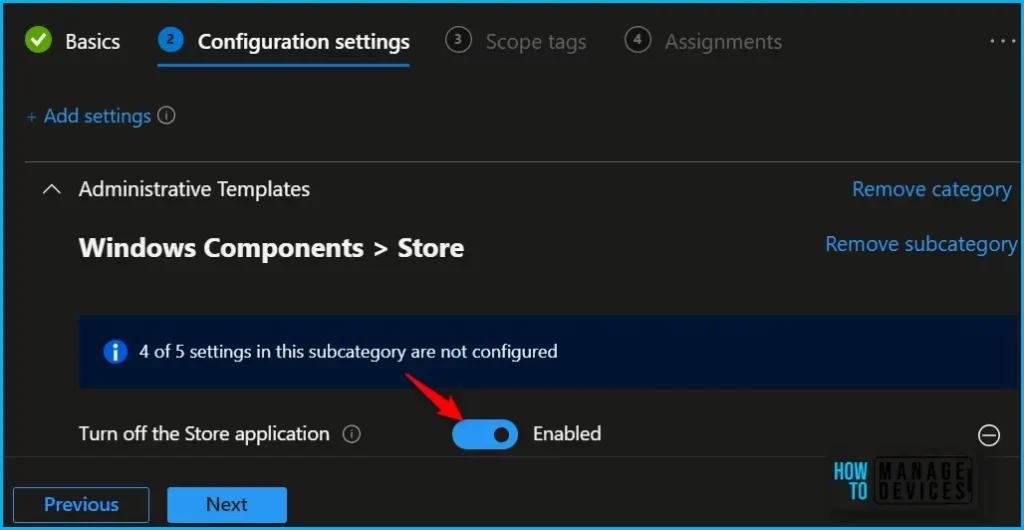
The next step is to expand the Store and toggle “Turn off the Store application” to Enabled. Once you enable the option, the selected setting (Device) will appear and click on Next.
Denies or allows access to the Store application. If you enable this setting, access to the Store application is denied. Access to the Store is required for installing app updates. If you disable or don’t configure this setting, access to the Store application is allowed.
Using Scope tags, you can assign a tag to filter the profile to specific IT groups. One can add scope tags (if required) and click Next to continue.
Now in Assignments, in Included Groups, you need to click on Add Groups, choose Select Groups to include one or more groups, and click Next to continue.
In the Review + Create tab, you need to review your settings. After clicking Create, your changes are saved, and the profile will be assigned to the added devices group.
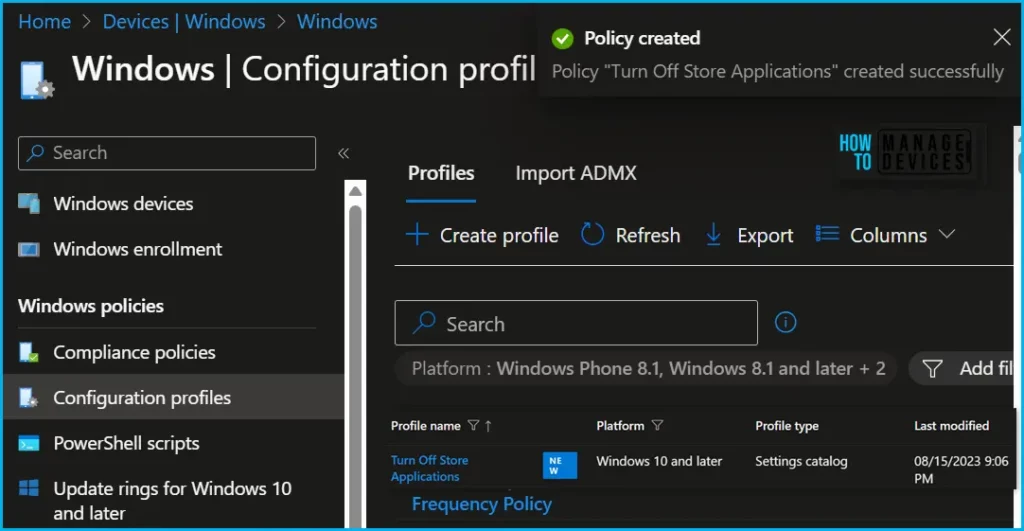
A notification will appear automatically if you see it in the top right-hand corner. One can easily see that the Policy “Turn Off Store Applications” was created successfully. Also, if you check the Configuration Profiles list, the Policy is visible there.
Note! The device groups will receive your profile settings when the devices check in with the Intune service. The Policy applies to the device.
This centralized approach to managing store applications through Intune simplifies the administrative process and enhances the overall user experience on managed devices.
| CSP | Intune | On-premises GPO |
|---|---|---|
| – ADMX_WindowsStore/RemoveWindowsStore_1 – ADMX_WindowsStore/RemoveWindowsStore_2 | – Settings Catalog – Administrative templates | Administrative Templates > Windows Components > Store |
Monitor Store Application Policy Deployment
Intune provides several features to monitor and manage device configuration profiles. By monitoring the status of your profiles, you can ensure that your devices are configured correctly and that any issues are addressed promptly.
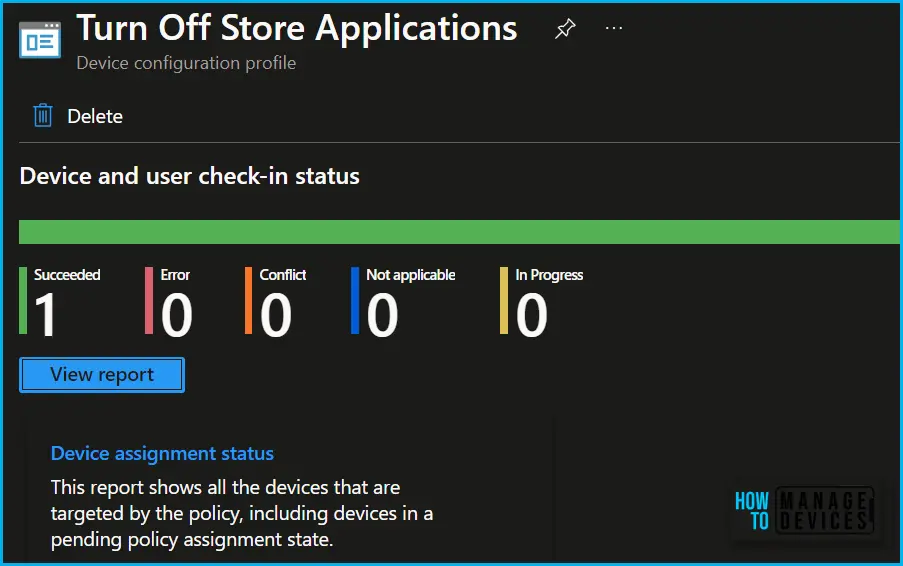
To monitor Intune policy assignment, from the list of Configuration Profiles, select the policy you targeted, and here you can check the device and user check-in status. If you click View Report, additional details are displayed. Additionally, you can quickly check the update as devices/users check-in status reports:
Track Event Log for Intune Policy Deployment
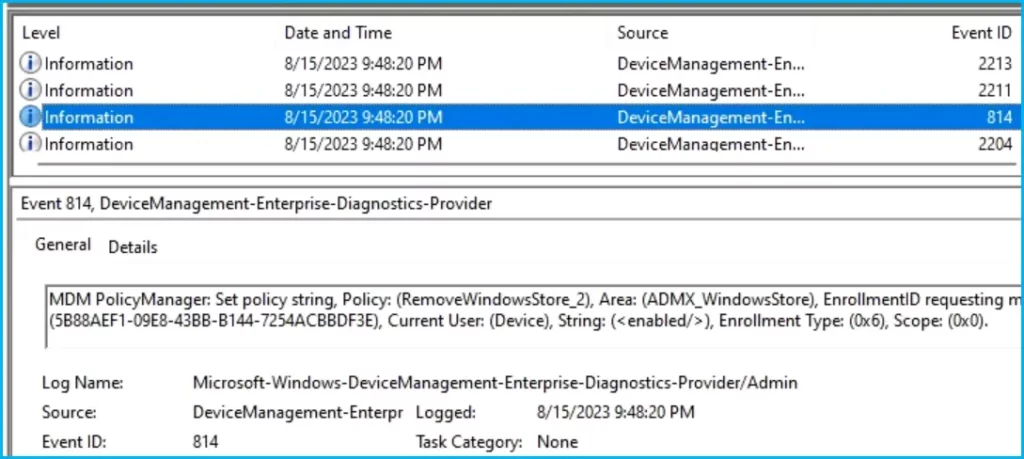
Intune event IDs 813 or 814 can indicate that a string policy has been applied to Windows 10 or 11 devices. These event IDs can provide valuable information about the policy that has been applied, including the exact value of the policy enforced on those devices.
In the case of the policy mentioned earlier, which enforces idle session time limits, event ID 814 would be used to indicate that the string policy has been applied, and you can view the specific value of the policy.
To confirm this, check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
MDM PolicyManager: Set policy string, Policy: (RemoveWindowsStore_2), Area: (ADMX_WindowsStore), EnrollmentID requesting merge: (5B88AEF1-09E8-43BB-B144-7254ACBBDF3E), Current User: (Device), String: (<enabled/>), Enrollment Type: (0x6), Scope: (0x0).
Author
About Author – Jitesh, Microsoft MVP, has over six years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus is Windows 10/11 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.

Hi, I did use this setting in Intune, and it works perfectly.
But, then I had a machine that installed through Intune and the Company Portal failed with error code 0x8024001E.
Now i could not install the company portal as I have no access to MS Store. Not even with Winget.
How do I push out a new install of Company Portal to the device without access to MS Store.?
Hi,
I have a question I can’t find an answer to regarding blocking the Store and still getting the updates for New Store Apps (both UWP & Win32).
You say that: “If you enable this setting, access to the Store application is denied. Access to the Store is required for installing app updates”
While Microsoft say that: ”
“Microsoft Store Win32 apps are kept up to date by Intune, therefore in order for the app to be updated it must be assigned in Intune. App updates are not affected by the Store’s update policies.”
https://learn.microsoft.com/en-us/mem/intune/apps/store-apps-microsoft#intune-management-of-microsoft-store-win32-apps
https://learn.microsoft.com/en-us/mem/intune/fundamentals/whats-new#week-of-august-14-2023
My goal is of course to replace some older Win32-apps with the New Store version in order to keep these up to date but I can’t find much information about it really? Any idea? Thanks!
For some reason, this failed for me. I got an “App uninstallation failed” notice with Error code 0x87D103E8 (Unknown error, of course)
Testing on a machine with Windows 10.0.22621.2283
The downloaded Teams was version 23231.411.2342.9597
Any assistance would be appreciated.