Let’s discuss how to Block Users Personal Devices to Join Entra ID using Intune. By default, Microsoft Entra ID allows all users to join their devices. Anyone with an Entra ID can link their personal computers to the system.
Users adding their private computers to Entra ID opens up potential vulnerabilities. These private devices often don’t meet the same security standards as company-managed devices. They might lack essential security updates, antivirus software, or other measures to safeguard sensitive data.
As a result, they can become entry points for security breaches, putting the organization’s data at risk of compromise. The situation gets even riskier when a user’s account is compromised.
If an attacker gains access to a user’s account, they could add their computer to Entra ID. This is particularly dangerous because the malicious actor’s computer could become compliant within the system.
When a compromised user adds their computer, it looks legit. The attacker might then access internal stuff meant only for trusted devices. Also, compliant devices often skip security checks like MFA, so the attacker gets in quickly.

- What is Microsoft Entra ID?
- Security Enhancement with Named Locations in Entra ID
- Enterprise Applications Security Settings in Entra ID
- Modernize MFA Authentication Policies in Entra ID
- List of Entra ID Ignite 2023 Sessions
- Free Entra Training Videos | Start Learning Entra ID Azure AD
Block Users Personal Devices in Microsoft Entra
Microsoft Entra’s join and registration settings stop regular users from adding Windows devices to Microsoft Entra ID. However, this doesn’t affect hybrid join or devices in AutoPilot self-deployment mode because they don’t join through regular user actions.
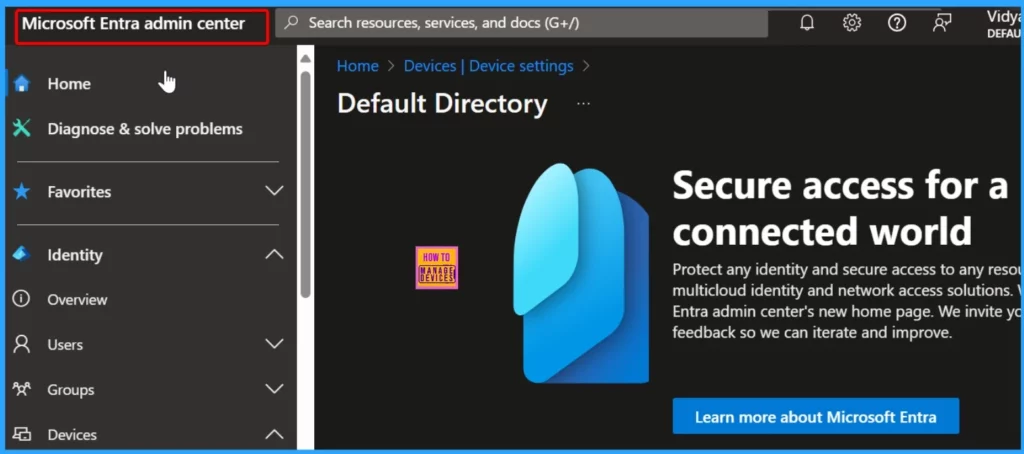
The first part of the settings can be found by going to Microsoft Entra ID and opening Devices > Device Settings. The top setting is “Users may join their personal devices to Microsoft Entra.” It’s best to set this to “Selected” so that you can limit it to specific users who want to enrol on their corporate device, not their personal device. If the option is selected “None, ” none of the devices will join Microsoft Entra.
Disabling End User Devices Enrollment to Microsoft Intune
In addition to managing device join in Microsoft Entra ID, I think turning off end-user device enrollment to Microsoft Intune is crucial. While not directly related to Entra ID, this step is essential for overall security.
Users can enrol their devices into Microsoft Intune’s Mobile Device Management (MDM) mode. This is common in Bring Your Own Device (BYOD) scenarios, where employees use their personal devices for work. However, due to security concerns, this practice should be disabled. Employees should only use corporate devices provided by their IT department.
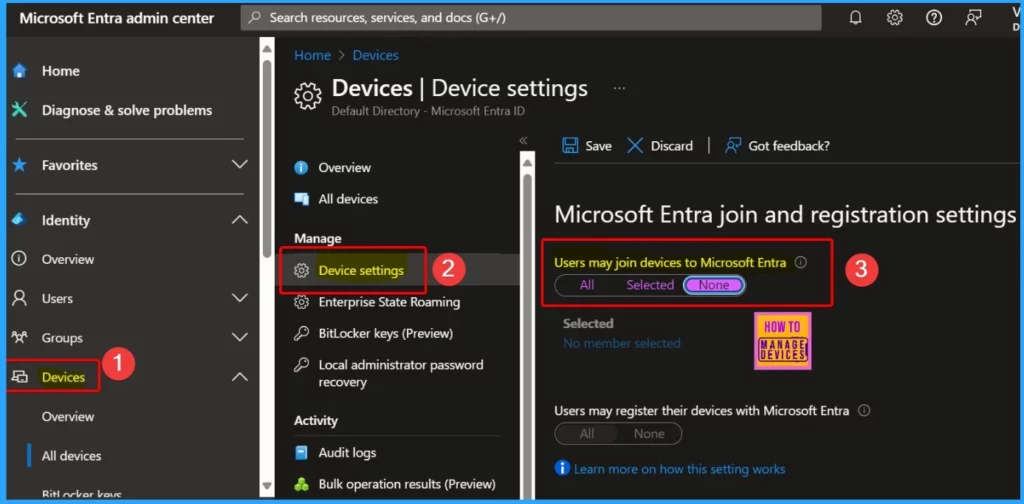
To turn off end-user device enrollment to Microsoft Intune MDM, follow these steps in the Intune Admin Center:
| Steps |
|---|
| Go to Devices. |
| Click on Enrollment. |
| Navigate to Device platform restrictions. |
- Renew SCIM Token in Apple Business Manager to Sync Microsoft Entra ID
- Microsoft Entra ID Company Branding Now Generally Available
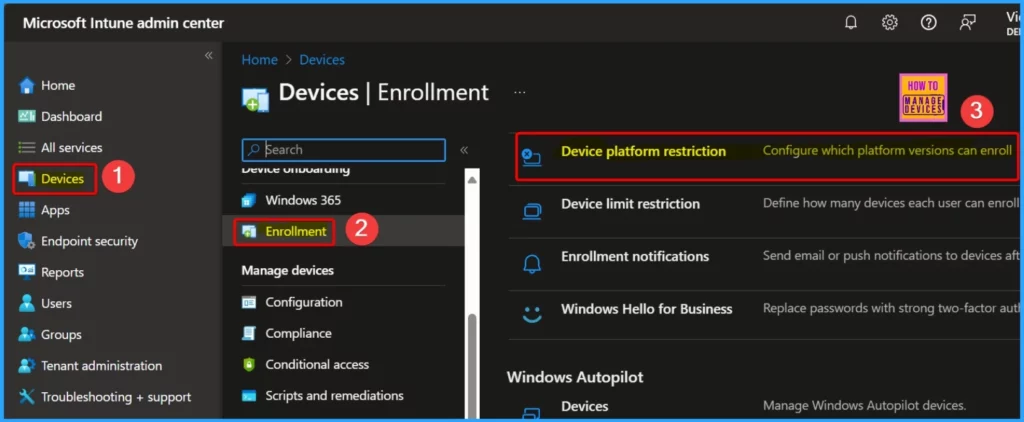
Open Windows platform restrictions (or other relevant platforms). Under Windows restrictions, select the Create restriction option. The screenshot below will guide you.
The Basic tab is like the starting point for showing important info. It’s the first tab you’ll see, and it’s all about the basics. Here, you can find the name of whatever you’re looking at, a description to explain what it is, and details about its platform.
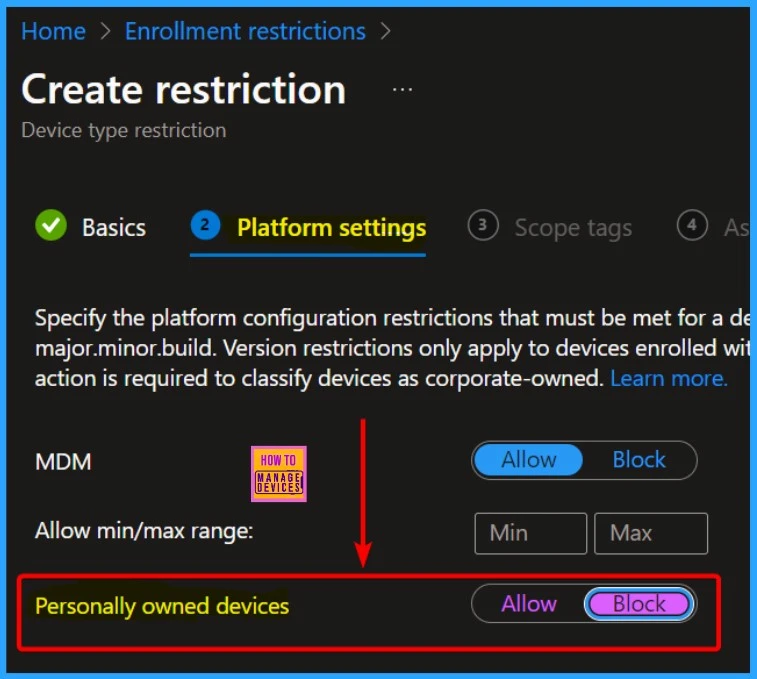
You can see Platform Settings settings such as the MDM, Allow min/max range, and Personally Owned Devices. In the Personally Owned Device settings, you can control whether people can use their devices with the platform.
- Right now, it’s set to “Allow,” which means they can. But if you change it to “Block,” they won’t be able to anymore.
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
About the Author: Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing about Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.

Thanks for the article, but, how does Intune or Entra ID knows if a computer is personal or corporate? I was expecting some way to distinguish between these two types os devices.
Says right on the ‘Create restriction page’ –> “…Intune classifies devices as personally-owned by default. Additional action is required to classify devices as corporate-owned…”