Here’s a step-by-step guide on how to block Windows Registry Access using Intune. You can Prevent access to the Windows registry editor Regedit.exe. This setting also determines whether the registry can run on the device silently.
The Windows Registry is used by Windows to store configuration settings and options. It plays a critical role in the proper functioning of the operating system and various applications. However, if not properly secured, it can be exploited by malicious actors to compromise system stability and data security.
Preventing access to the registry is a security measure frequently implemented in organizations to enhance overall security. By default, standard user accounts run with limited privileges and require the administrator consent to modify the Registry. This helps prevent unauthorized changes.
Admins can configure the Policy to disable registry access for specific user accounts or groups. This policy effectively blocks users from opening the registry editor, helping prevent unintended or unauthorized use of the Windows editor.
However, planning and implementing this policy carefully is important, as legitimate system administration tasks often require registry access. Administrators should ensure that necessary exceptions are made for IT persons or users who require such access for their roles.
Block Windows Registry Access using Intune
By following these steps, you can effectively disable Windows Registry Access on Intune-managed devices. This allows you to control the registry execution process by preventing user access.
- Sign in to the Microsoft Intune Admin portal https://intune.microsoft.com/.
- Select Devices > Configuration profiles > Create profile.
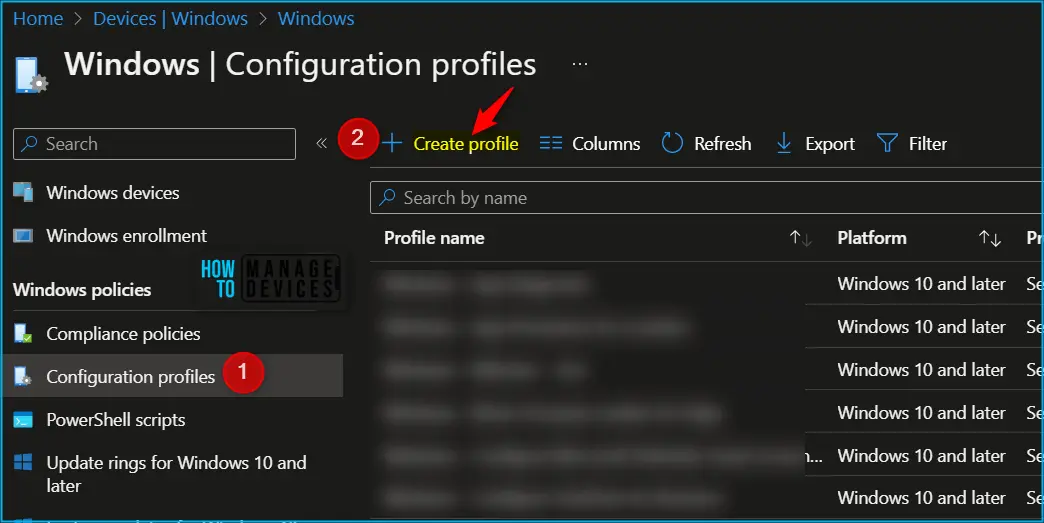
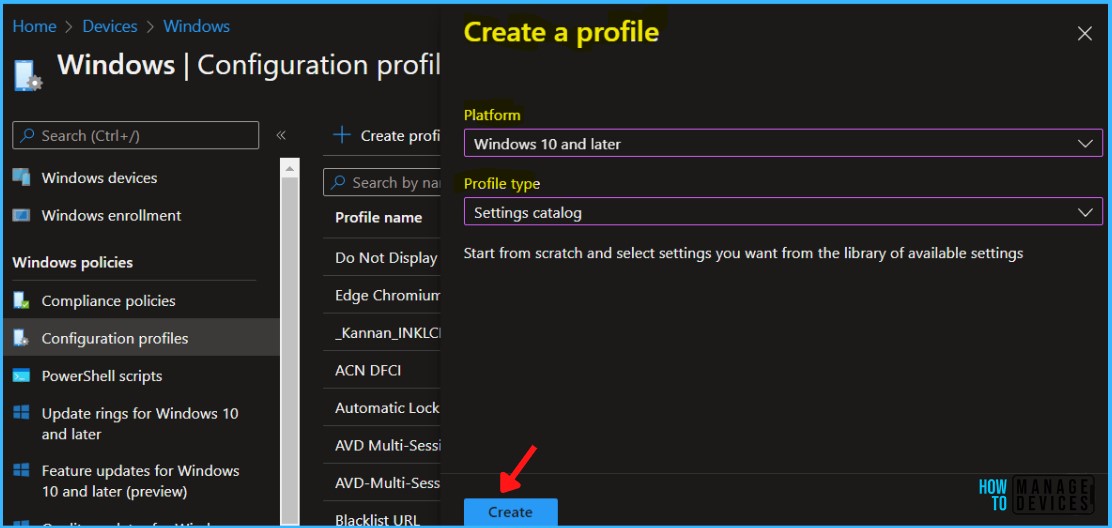
In Create Profile, Select Windows 10 and later in Platform, Select Profile Type as Settings Catalog. Click on Create button.
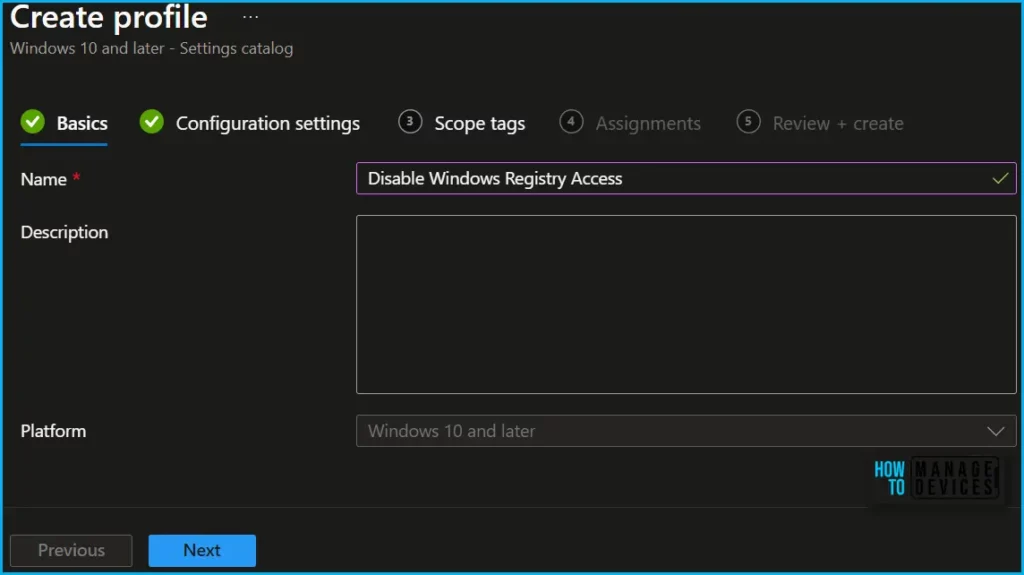
In Basics, enter the descriptive name for the new profile. For example, Disable Windows Registry Access or Prevent users access to registry editor, and add a description for the profile to understand the policy usage and Select Next.
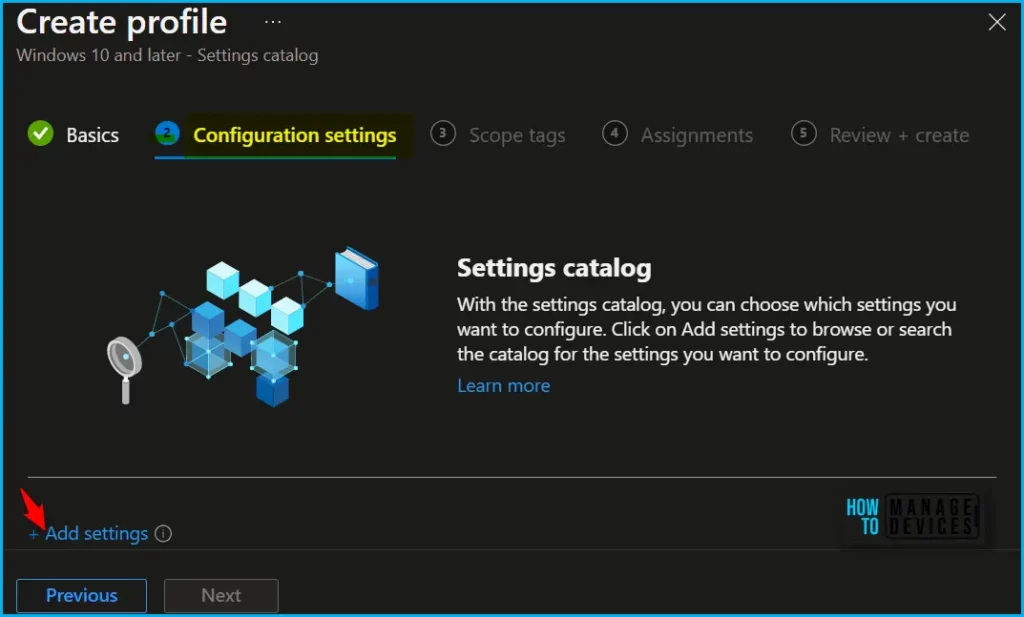
On the Configuration settings tab, With the settings catalog, you can choose which settings you want to configure. Click on Add Settings to browse or search the catalog for the settings you want to configure.
Search for “Registry editing tools” or “Prevent access to the registry”. Select the “Administrative Templates\ System” from the search result. Select “Prevent access to the registry editing tools (User)” and close the pane.
If you enable this policy setting and the user tries to start Regedit.exe, a message appears explaining that a policy setting prevents the action.
If you disable this policy setting or do not configure it, users can run Regedit.exe normally. To prevent users from using other administrative tools, use the “Run only specified Windows applications” policy setting.
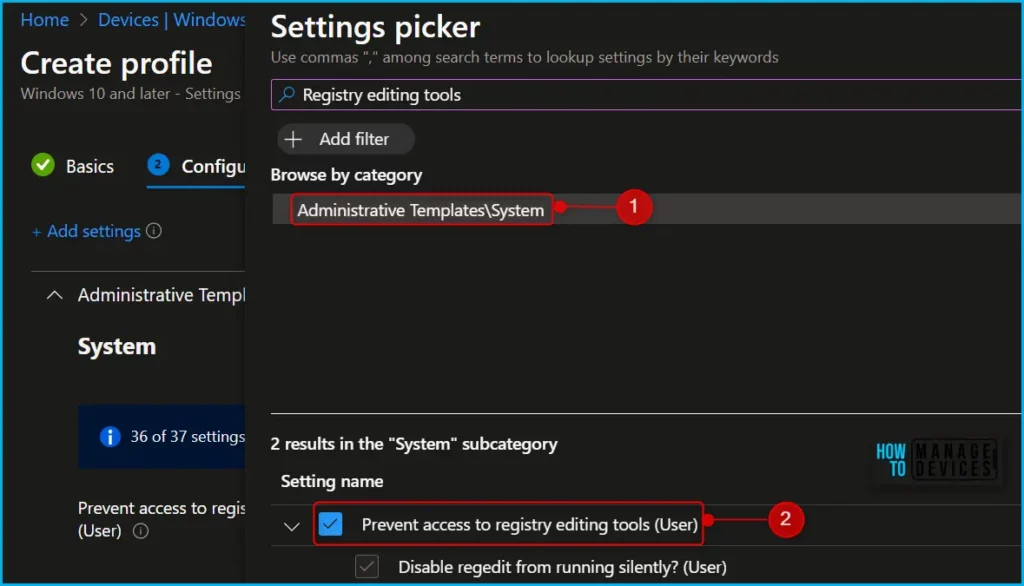
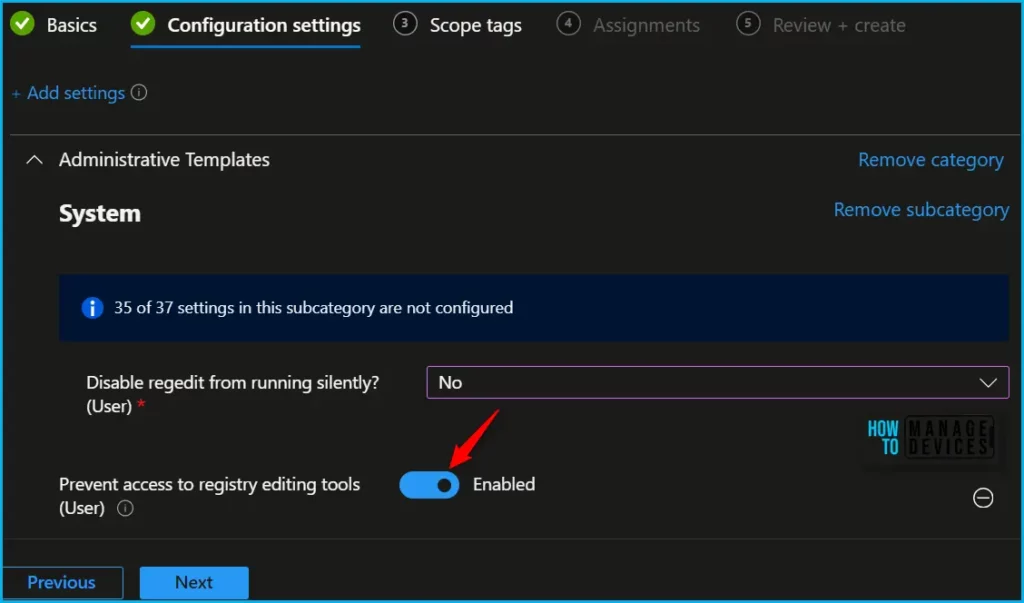
The next step is to toggle “Prevent access to registry editing tools” to Enabled. Once you enable the option, the selected setting will appear, and click on Next.
This policy setting prevents users from running the registry editor, regedit.exe. This policy setting also determines whether regedit can run silently on the computer. Here we have configured the Disable regedit from running silently, to No.
Using Scope tags, you can assign a tag to filter the profile to specific IT groups. One can add scope tags (if required) and click Next to continue.
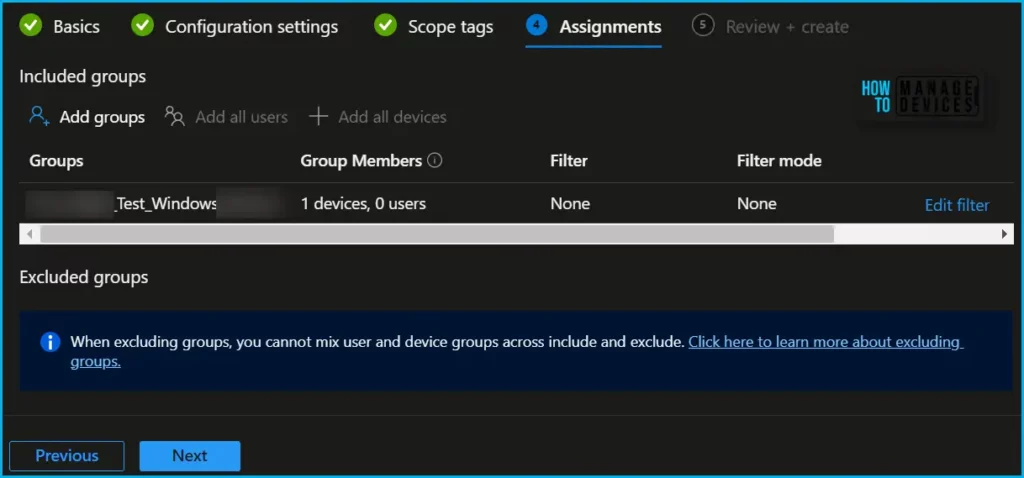
Now in Assignments, in Included Groups, you need to click on Add Groups, choose Select Groups to include one or more groups, and click Next to continue.
In the Review + Create tab, you need to review your settings. After clicking Create, your changes are saved, and the profile will be assigned to the added devices group.
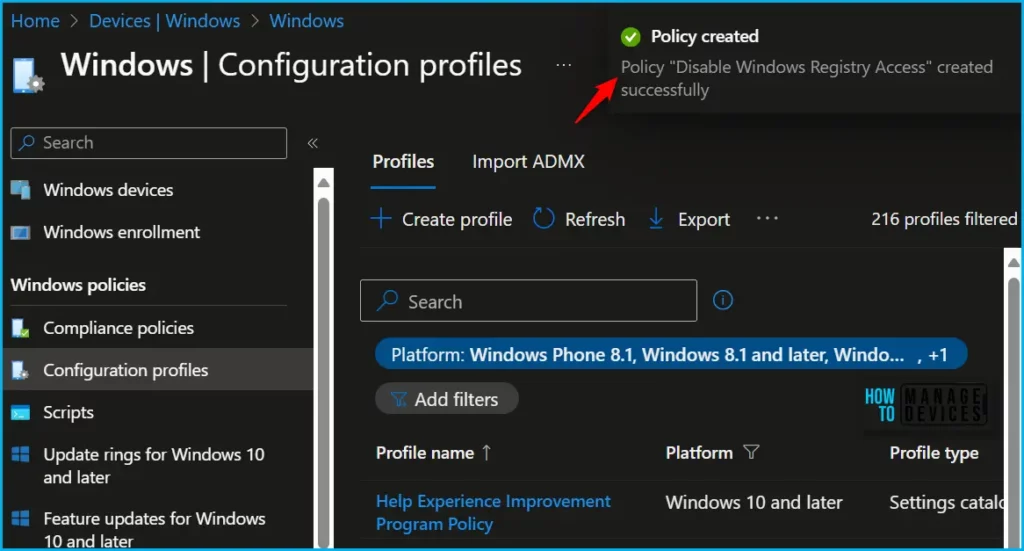
A notification will appear automatically if you see it in the top right-hand corner. You can easily see that the Policy “Disable Windows Registry Access” was created successfully. Also, if you check the Configuration Profiles list, the Policy is visible there with the tag NEW.
To restrict Windows Registry access on Windows devices, especially in a business or organization setting, you typically rely on Group Policy or other centralized management tools like Microsoft Intune. This centralized approach to prevent registry editor access through Intune simplifies the administrative process.
| Intune CSP | On-premises GPO |
|---|---|
| ./User/Vendor/MSFT/Policy/Config/ADMX_ShellCommandPromptRegEditTools/DisableRegedit | Administrative Templates (Users) > System > Prevent access to the registry editing tools |
Monitor Windows Registry Access Policy Deployment
Intune provides several features to monitor and manage device configuration profiles. Once the configuration profile is applied, Registry access should be disabled on the targeted devices.
Note! The device groups will receive your profile settings when the devices check in with the Intune service. The Policy applies to the device.
To monitor Intune policy assignment, from the list of Configuration Profiles, select the policy you targeted, and here you can check the device and user check-in status. If you click View Report, additional details are displayed. Additionally, you can quickly check the update as devices/users check-in status reports:
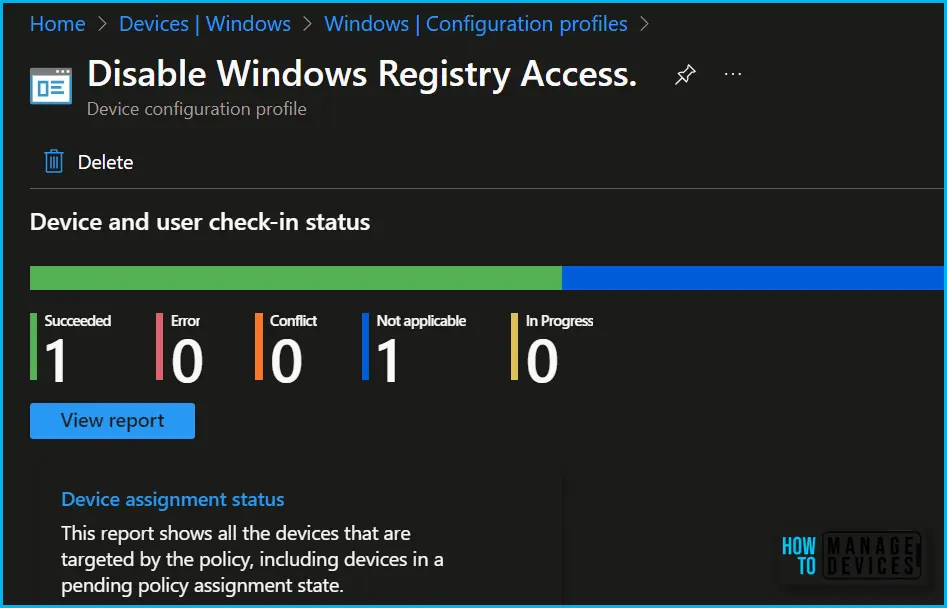
Monitor Event Log for Windows Registry Access Policy Deployment
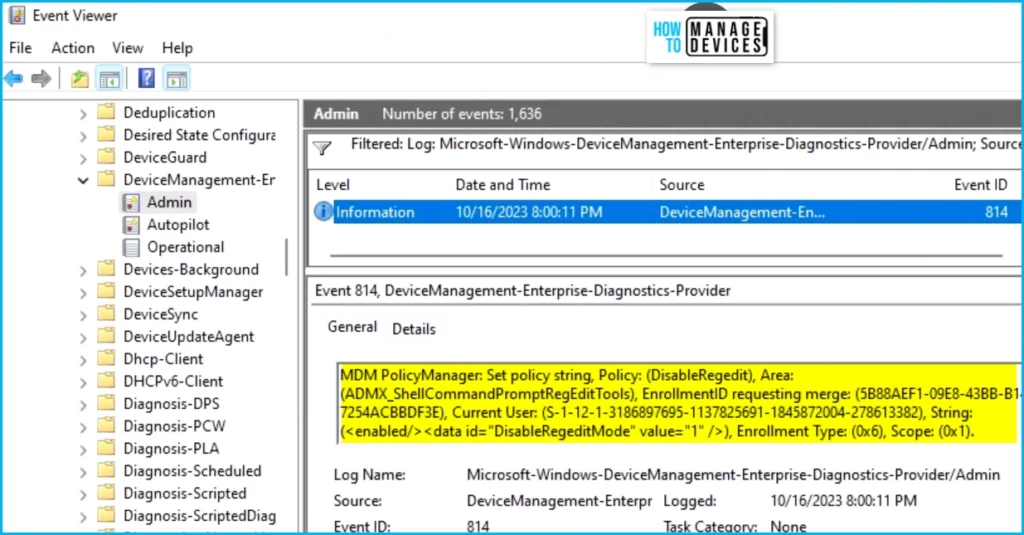
Intune event IDs 813 or 814 can indicate that a string policy has been applied to Windows 10 or 11 devices. These event IDs can provide valuable information about the policy that has been applied, including the exact value of the policy enforced on those devices.
In the case of the policy mentioned earlier, which prevents access to the Windows registry, event ID 814 would be used to indicate that the string policy has been applied, and you can view the specific value of the policy.
To confirm this, check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
MDM PolicyManager: Set policy string, Policy: (DisableRegedit), Area: (ADMX_ShellCommandPromptRegEditTools), EnrollmentID requesting merge: (5B88AEF1-09E8-43BB-B144-7254ACBBDF3E), Current User: (S-1-12-1-3186897695-1137825691-1845872004-278613382), String: (), Enrollment Type: (0x6), Scope: (0x1).
Registry Settings Details
To check the policy deployment, You can validate the registry details for disabling Windows registry access at the below location. Of course, Once you disable the access, you won’t have control to validate registry changes, You can use the registry for controlling the registry editor.
| Registry Hive | HKEY_CURRENT_USER |
| Registry Path | Software\Policies\Microsoft\Windows\System |
| Value Name | DisableRegedit |
| Value Type | REG_DWORD |
| Enabled Value | 0 |
| Disabled Value | 1 |
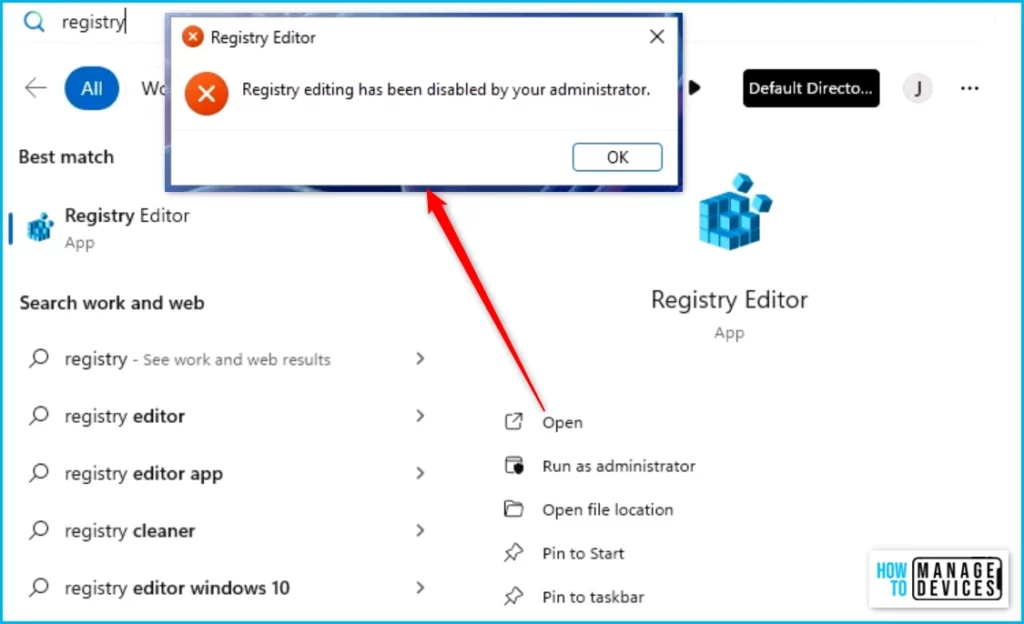
End Users Experience
If you enable the policy and the user tries to open a registry, the system displays a message explaining that a setting prevents the action. A popup will appear with the message, Registry editing has been disabled by your administrator.
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
About Author – Jitesh, Microsoft MVP, has over six years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus is Windows 10/11 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.
