In this article, I’ll explain how to provision Windows 365 Cloud PC for an external identity using Microsoft Intune. You can invite users to your Entra ID tenant and give them Cloud PCs with the use of external identity capability. Giving Cloud PCs to external identities comes with a number of restrictions and criteria.
In the GA of Windows 365 support for external identities, it is now possible to provision a Cloud PC for an external identity. The administrative process for provisioning this Cloud PC remains unchanged, as it adheres to the same provisioning procedures for both Enterprise and Frontline Cloud PCs.
Licenses allocated to an external collaborator within their own home tenant typically do not provide entitlements to Windows 365 or other products associated with your tenant. Consequently, Microsoft usually advises acquiring the same type of license that you would purchase for internal users and assigning it to the external collaborator’s identity within your tenant. For instance, if you are licensing Microsoft 365 Apps in conjunction with your Windows 365 Cloud PCs, and your external collaborators require the same entitlements, you should purchase a Microsoft 365 Apps license and assign it to the external collaborator in your tenant.
Similarly, licenses allocated to a user in one tenant of a multitenant organization typically do not grant entitlements to Windows 365 or other products in a different tenant of the same organization. Consequently, Microsoft usually advises acquiring a license for every user in each tenant where access rights are necessary. An exception to this rule is Entra ID; only a single Microsoft Entra ID P1 license is needed for each employee across the multitenant organization.

Table of Contents
Prerequisites and Requirements of External Identity
The table outlines the key prerequisites needed to enable Windows 365 External Identity for seamless access to Cloud PCs. It highlights the essential Entra ID configurations, licensing, and security requirements for external users.
| Prerequisites and Requirements | Description |
|---|---|
| Cloud PC Operating System | The Cloud PC must be running Windows 11 Enterprise, versions 24H2 or later with the 2025-09 Cumulative Updates for Windows 11 (KB5065789) or later installed. |
| Cloud PC Join Type | The Cloud PC must be Entra joined |
| Single Sign-On | Single sign-on must be configured for the Cloud PC |
| Windows App Client | The external identity must connect from the Windows App on Windows or a web browser. (https://windows.cloud.microsoft.com/ or https://windows365.microsoft.com/ (Old) |
| Licensing | Ensure that external identities have the proper entitlements for software and services on the Cloud PC. Before your users can gain access to a Cloud PC, you must purchase Windows 365 licenses. Customers can purchase Windows 365 as a separate license per user for a fixed monthly fee to access and use Cloud PCs. |
- Best Guide to Invite B2B Guest Users to Entra ID using Intune
- Cloud PC Zero to Hero Journey DaaS solution Windows 365
- How to Enhance Windows365 AI-Enabled Endpoint Management using Copilot in Intune
- Best Method to Enable and Disable Windows 365 Cloud PCs Redirections using Intune
Create a Windows 365 Cloud PC Provisioning Policy for External Identity
To create a Windows 365 Provisioning Policy for external users, log in to the Microsoft Intune Admin Center using your administrator credentials.
- Navigate to > Devices > Device onboarding > Windows 365
- Click on Provisioning policies > +Create policy
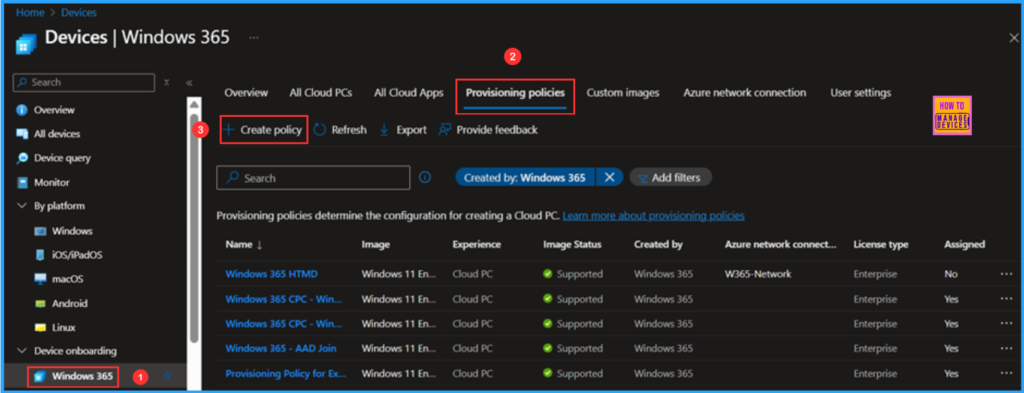
In the General tab, you can now add the following settings. A Cloud PC is a managed virtual computer that users can access to complete their work from any location and on any device. These steps will guide you in configuring the settings necessary to host Cloud PCs.
- Name: Provisioning Policy for External Users
- Description: Optional
- Experience: Access a full Cloud PC desktop
- License type: Enterprise (You can also opt for Frontline if you have a vaild license)
- Join type: Microsoft Entra Join
- Network: Microsoft hosted network
- Geography: India
- Region: Automatic (Recommended)
- Use Microsoft Entra single sign-on: Yes (Check the box)
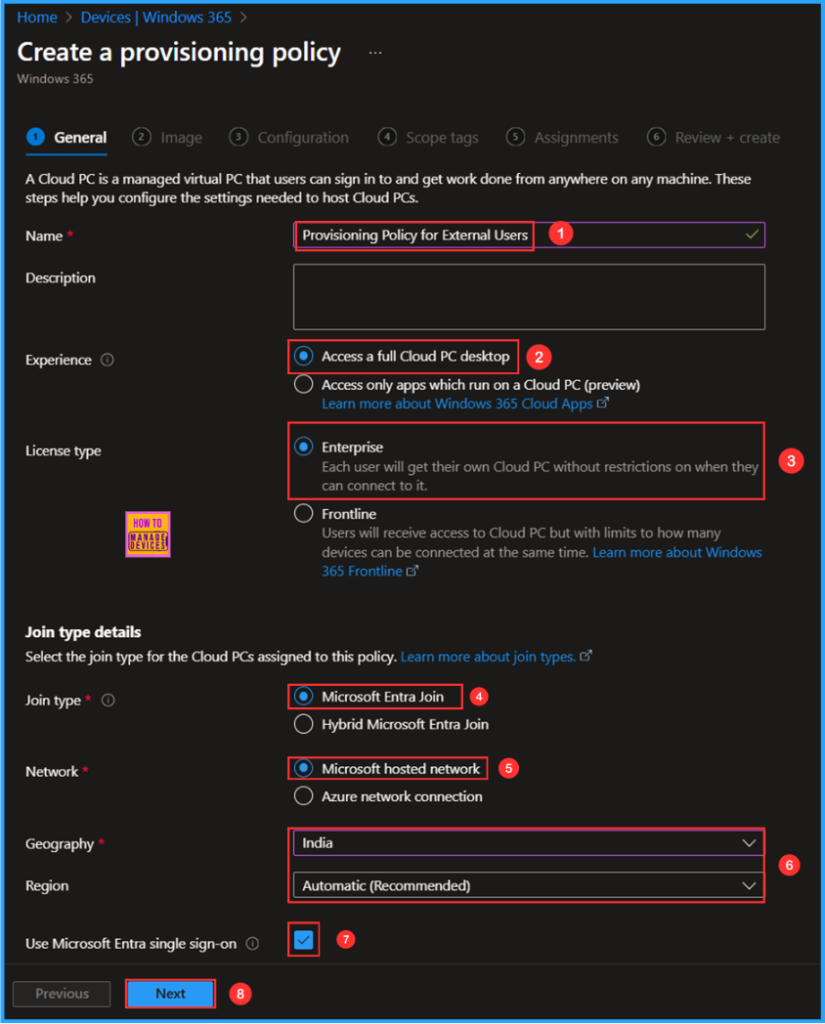
You can choose an existing image to create the session or create a new custom image. I will select the latest available Gallery image, which is Windows 11 Enterprise + Microsoft 365 Apps 25H2.
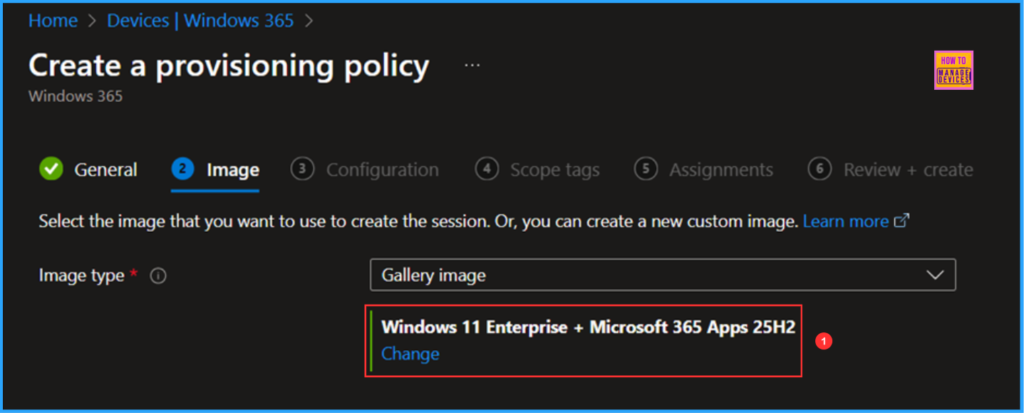
The next tab focuses on Windows settings, Cloud PC naming, and Additional Services configuration. Please select the options listed below.
- Language & Region: English (United States)
- Apply device name template: Yes (Check the box)
- Enter a name template: EXT-%USERNAME:5%-%RAND:5%
- Select a service: None (Manage and update Cloud PC’s manually)
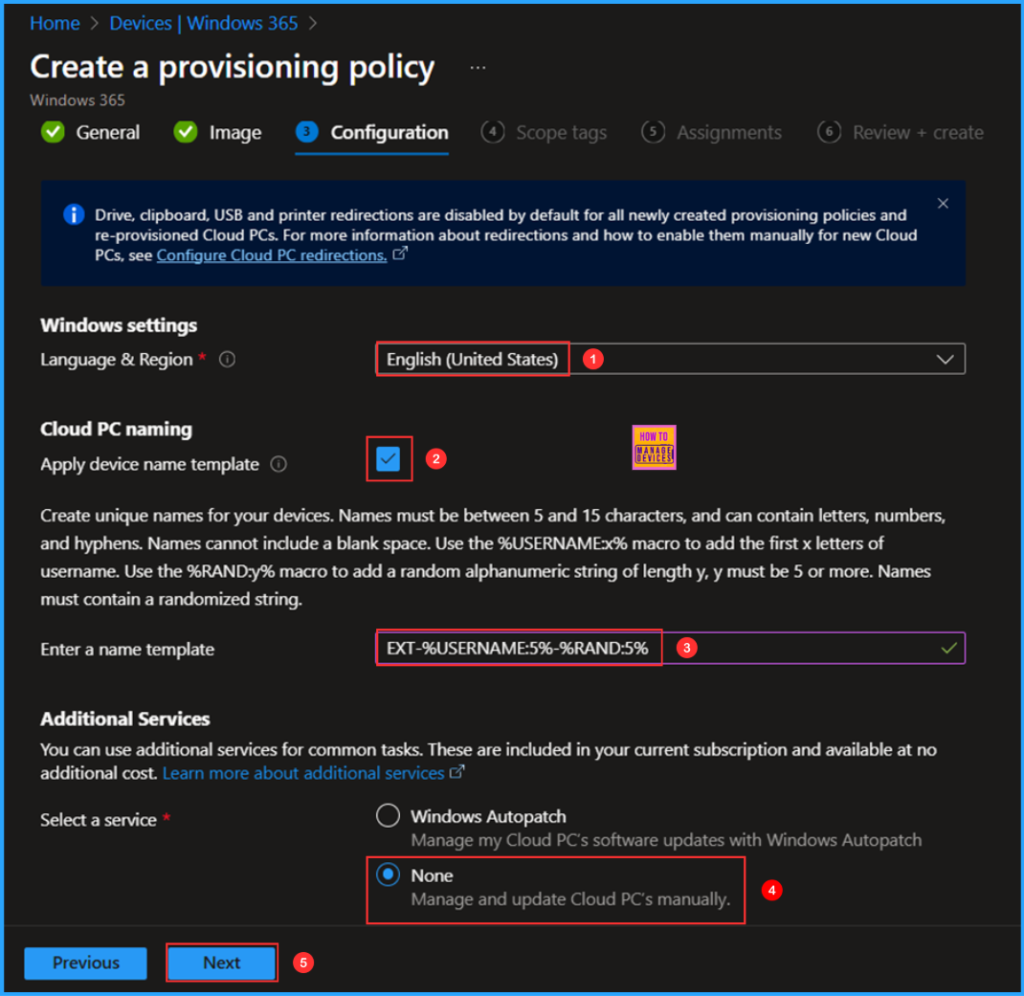
On the next page, keep the Scope tags set to Default. If your tenant has custom scope tags, select them based on your policy needs, and then click Next.
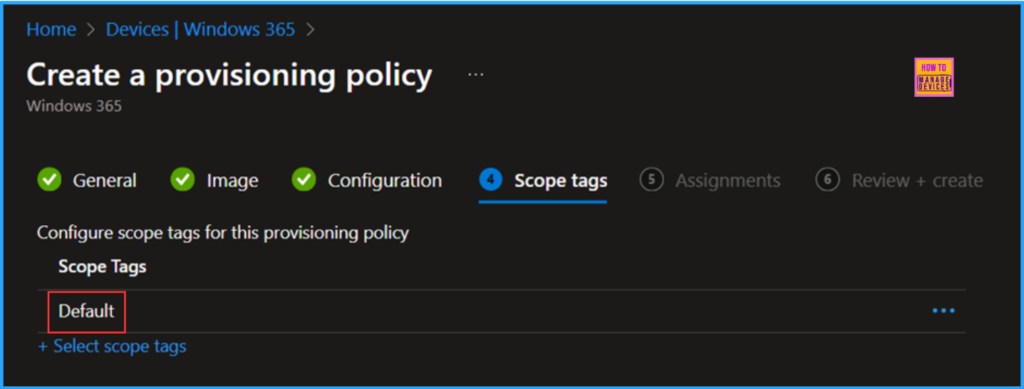
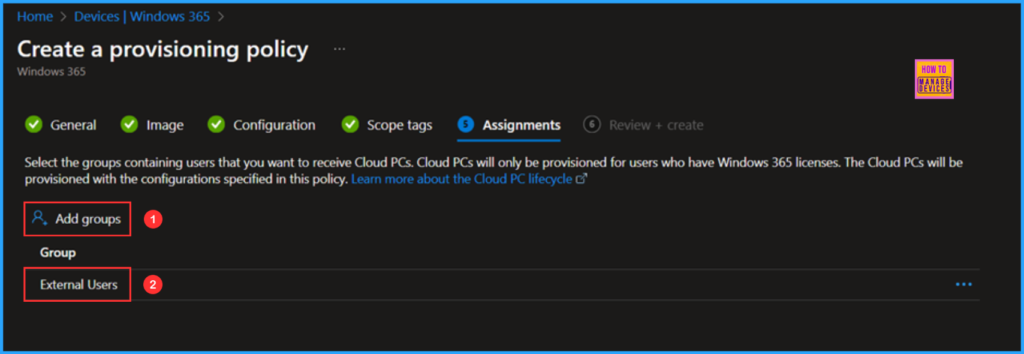
In this section, choose the group or groups of users who will receive Cloud PCs. I will assign the policy to the External Users group. To do this, click on Add groups and select the appropriate user group.
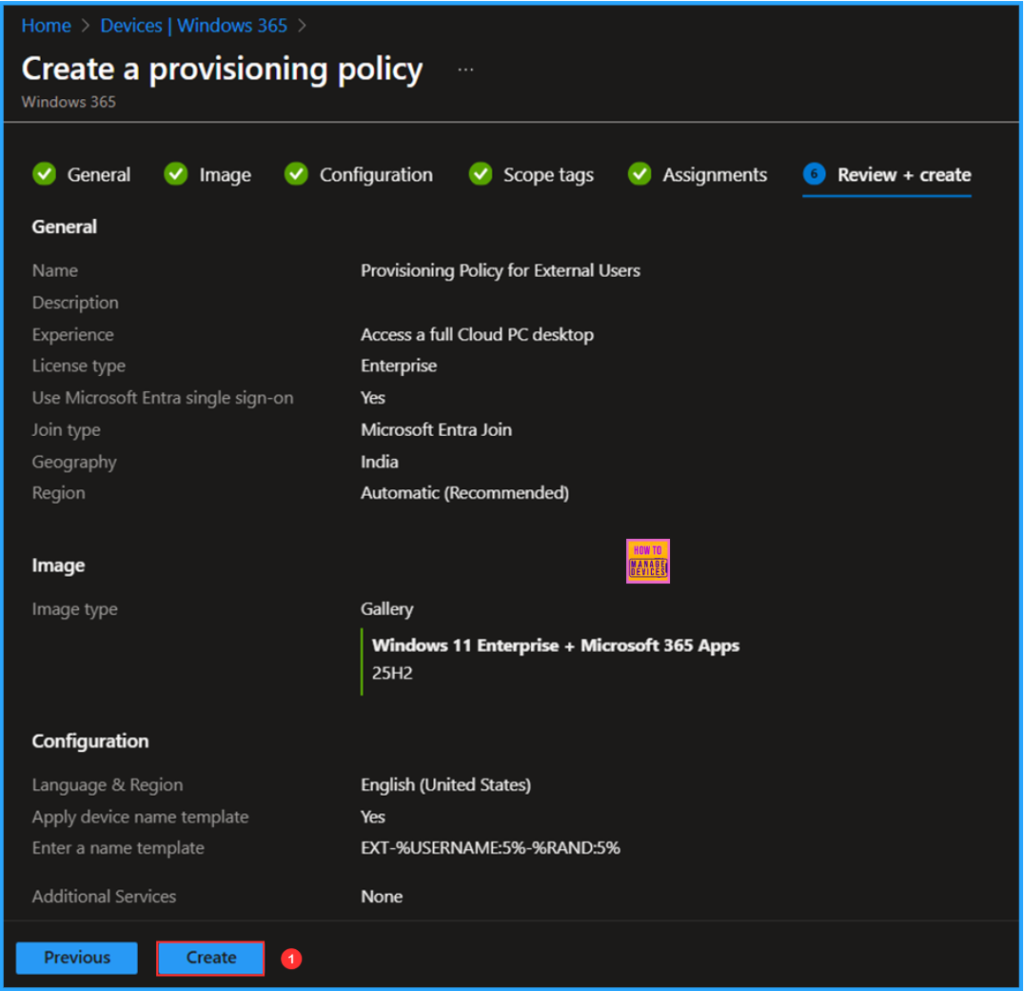
On the Review + create page, review all settings for the Provisioning Policy for External Users. After confirming, click Create to deploy the policy.
- How to Use Microsoft Entra External ID for Security Operations
- Entra External ID Now Supports SMS as an MFA Option
- How RDS AAD Auth Transforms SSO for Windows 365 CloudPC and Azure Virtual Desktop
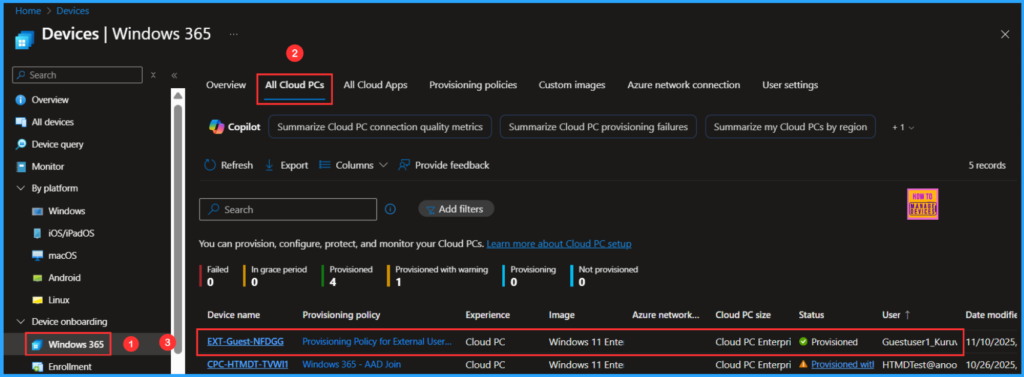
Monitor the New Provisioning Policy for External Users Deployment
The new Provisioning Policy for External Users has been deployed to the External User group, a Microsoft Entra ID for external identities. Please allow some time for the policy to take effect. To monitor the status of the policy deployment, follow the steps outlined below in the Intune Portal.
- Navigate to Devices > Windows 365 > All Cloud PCs > Search for the “Provisioning Policy for External Users”.
According to our configuration, the External Cloud PC with Hostname “EXT-Guest-NFDGG” has been successfully provisioned.
PowerShell Script to Add Windows App’s Sign-in options Registry Key
Now we can check how to connect the Windows 365 Cloud PC for an external user. If you are using the Windows app, make sure you add the registry value mentioned below using the method provided.
New-Item -Path "HKLM:\SOFTWARE\Microsoft\WindowsApp" -Name "Flights" -Force | Out-Null; Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\WindowsApp\Flights" -Name "EnableIdSignInUx" -Value 1 -Type DWordOnce the above-mentioned registry is added successfully, it will give you an extra option to sign in to an organization. Click on Sign-in options.
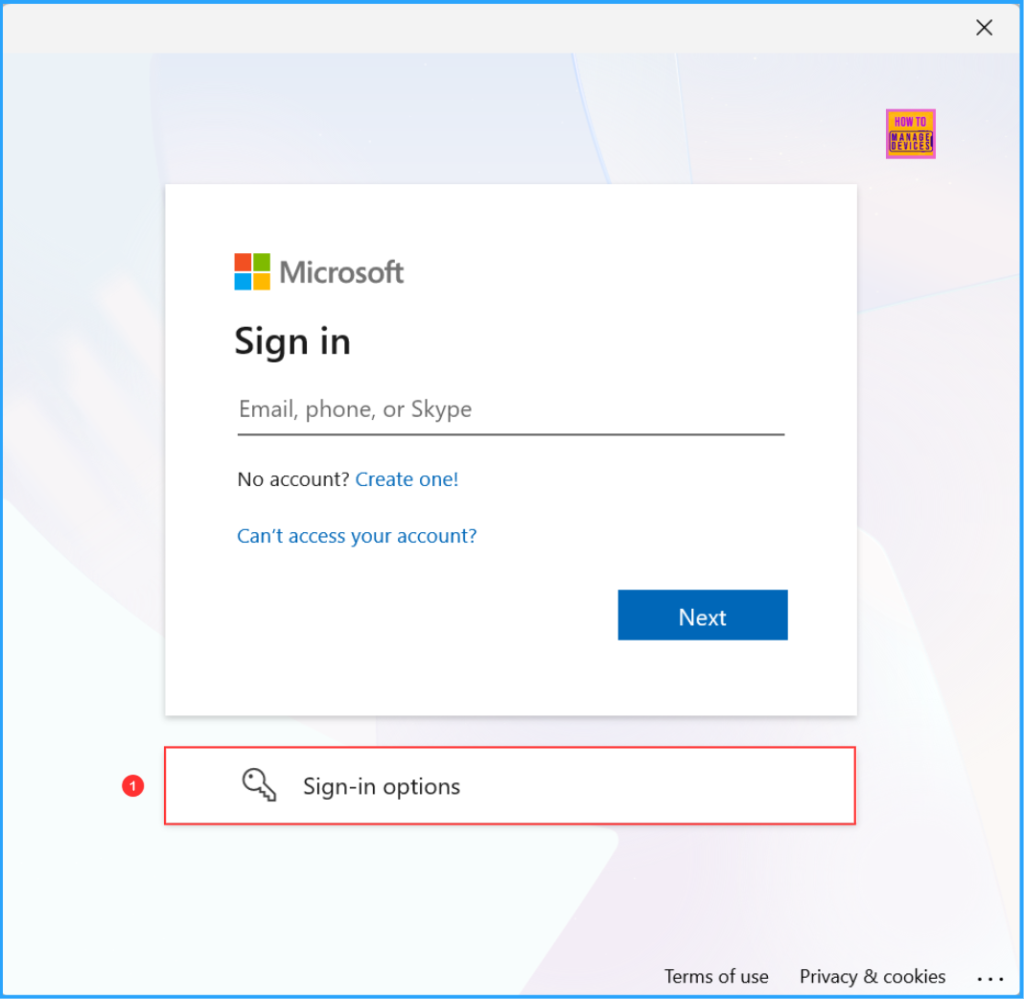
The next pane will provide sign-in options such as Face, fingerprint, PIN or a security key. You can also Sign in with GitHub or to an organization. Please select the Sign in to an organization option here.
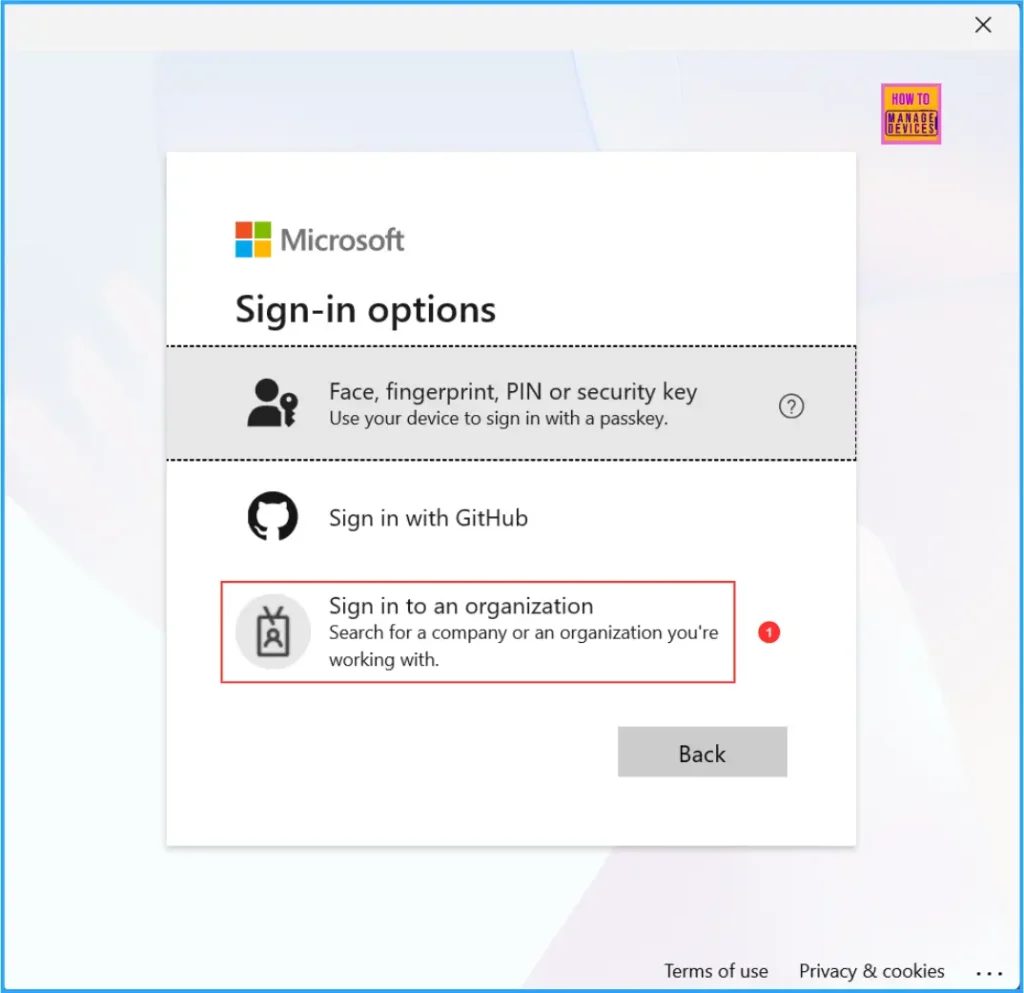
Enter the domain name of the organization you wish to sign in to. Here, you should enter the client domain name (the tenant name where the external identity was added), and then click Next.
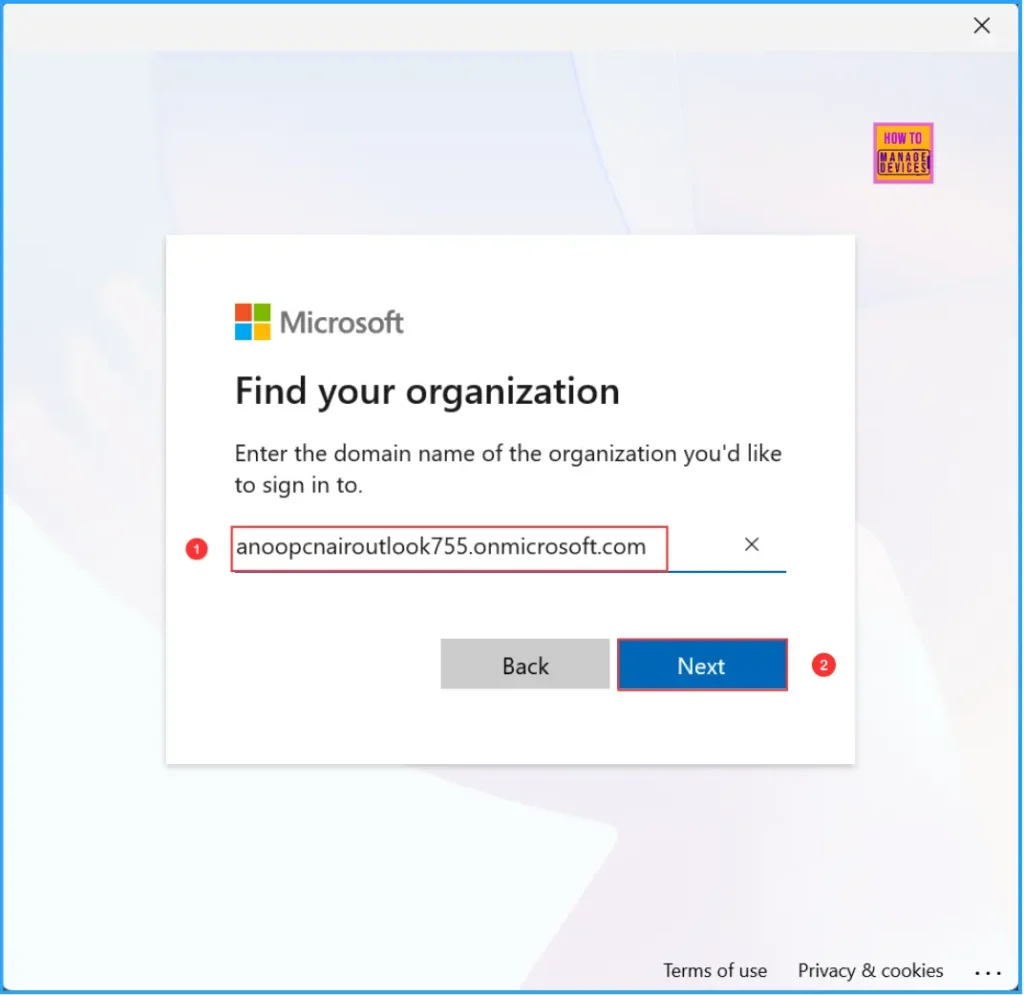
Enter your external user username, for example, Guestuser1@Kuruvaikandy.onmicrosoft.com. Then, click Next, enter your password, and select Sign in.
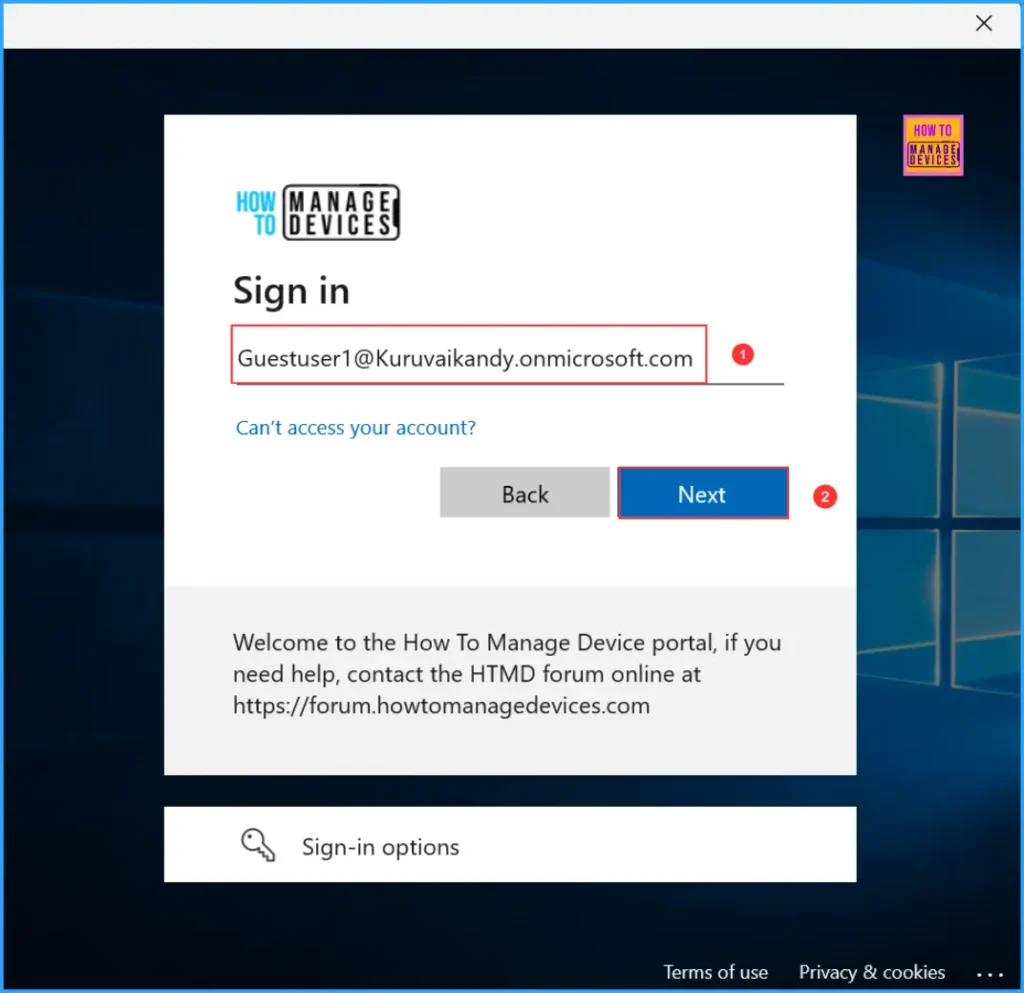
Windows 365 Cloud PC for an External Identity Experience
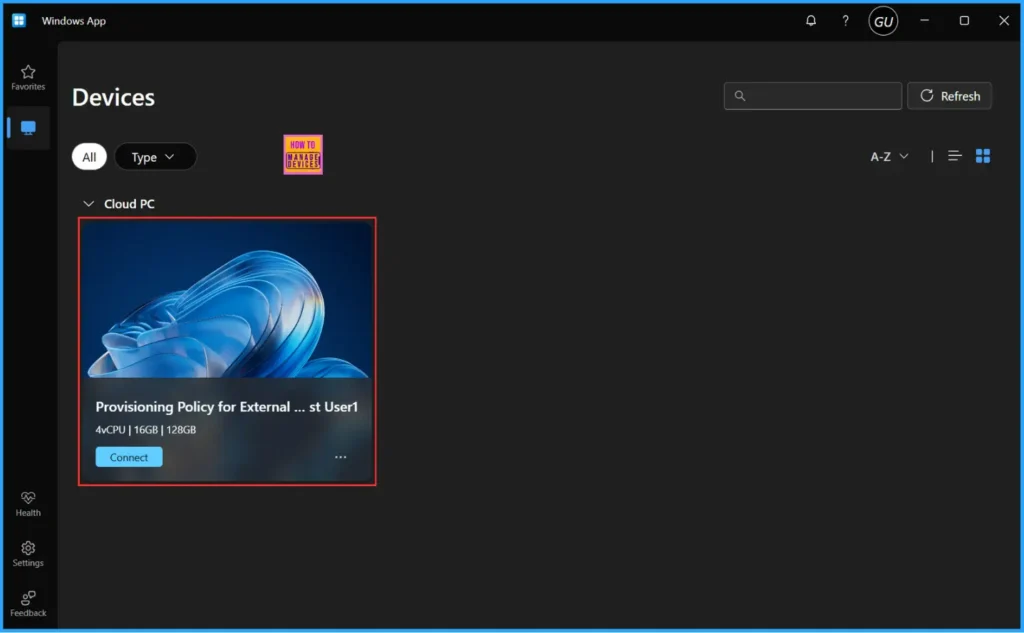
Under Devices tab in Windows App now you can see the newly provisioned Cloud PC assined to the external user Guestuser1@Kuruvaikandy.onmicrosoft.com.
After logging in, if you encounter an error message stating, “It looks like your system administrator hasn’t set up any resources for Guestuser1@Kuruvaikandy.onmicrosoft.com yet. Please choose a different account or try again. If you believe you have received this message in error, please contact your system administrator,” Don’t worry, follow these steps: Click on the user icon in the top right corner and switch the organization to Default Directory. This should make the assigned Cloud PC visible.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 12 years of experience in SCCM, Intune, Modern Device Management, and Automation Solutions. He writes and shares knowledge about Microsoft Intune, Windows 365, Azure, Entra, PowerShell Scripting, and Automation. Check out his profile on LinkedIn.


