Hello everyone, today, let’s learn how to create Intune App Protection Policies for iOS iPadOS. In this article, we will discuss the overview of App Protection policies and the steps to create them for iOS/iPadOS devices.
To apply APP protection policies, the applications should support. Most M365 applications, like Outlook, Word, OneDrive, etc., support Aprotection Policies. Please refer to the list of M365 apps that support App Protection Policies. In addition to M365 apps, many productivity apps are available in the Google Play Store, and the Apple App store support App Protection Policies.
App Protection Policies can be applied to both enrolled and non-enrolled devices. APP can be used for third-party MDM solutions. By implementing Aprotection Policies, we can ensure the data within managed apps are protected and can be controlled by the IT team. Let us discuss the App Protection Policies below.
What are App Protection Policies
App protection policies are part of Mobile Application Management (MAM) in Intune. In every organization, employees use their mobile devices for both personal as well as official tasks. This will provide chances of data leakage and data loss.
App protection policies (APP) in Intune are a set of policies that are used to protect corporate data on managed applications on both managed and non-managed devices. These policies can control access to corporate data and prevent data leakage within managed applications (managed apps that have app protection policies applied to them) on mobile devices.
Suppose any organization has LOB(Linne of business) apps and requires controlling the data with APP; in that case, the applications should either integrate Intune App SDK or wrap the application with Intune app wrapping tool. Intune SDK provides full features of App protection policies, whereas the app wrapping tool offers limited support for App protection policies.
NOTE: Intune app wrapping tool is a command line tool that creates a wrapper around the application and lets us manage the application with application protection policies. Intune App SDK requires code-level changes to your application. Integrating Intune app SDK does not change the app behavior. Intune AppSDK and Intune app wrapping tool are available for iOS and Android applications.
App protection policies can be deployed to 3 types of devices
- Devices enrolled in Intune
- Devices not enrolled in any MDM solution(neither Intune nor third-party MDM)
- Devices enrolled to third-party MDM
Why do we need App Protection Policies
App Protection policies provide various restrictions that can be applied to Managed apps. The following are the features of App Protections Policies that can be applied to any managed application.
- Data Protection by restriction copy and paste of data from the work profile to the personal profile
- Restricting the saving of documents/files only to OneDrive or SharePoint
- Enforcing application-level PIN
- Application-level data wipe
- Limiting access to applications based on OS versions
NOTE: The users must have an account in the Azure active directory and Intune license assigned to the account to use app protection policies. These app protection policies apply only when users sign in to the app.
We can create App protection policies for both Android and iOS/iPadOS. In this article, let’s see how we can create an App protection policy for iOS/iPadOS
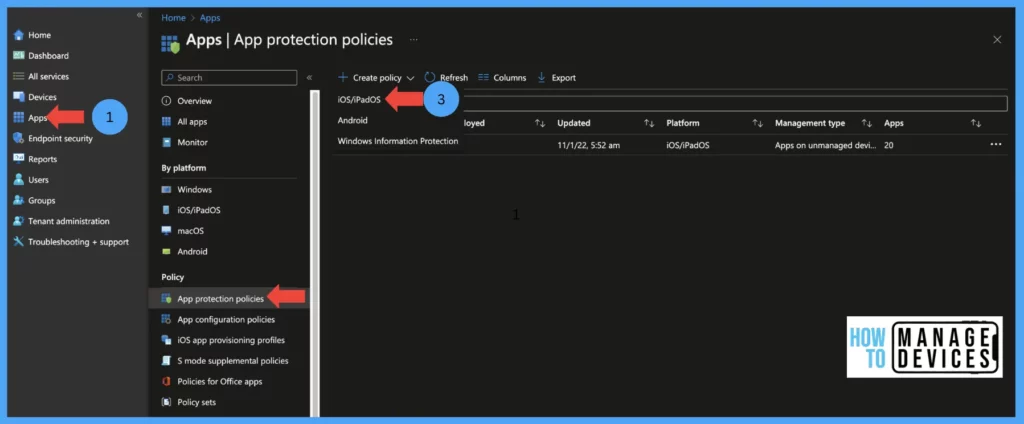
- Sign in to Microsoft Intune Admin Center.
- Click on app> App Protection policies.
- Click on create policy > select iOS/iPadOS.
Provide the Name of the policy and provide a description of the policy and click on Next. Now we target the devices and applications as per our requirement
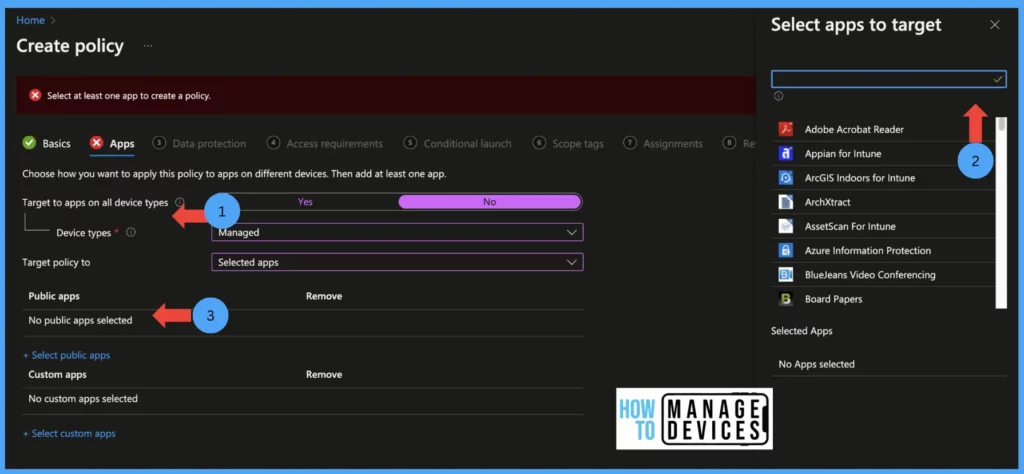
- Target to apps on all device types: Select yes if you want to target both Managed and unmanaged devices (enrolled or not enrolled devices). If you want to target only either managed devices or unmanaged devices, select No and select your requirement.
NOTE: When you select managed devices, the App Protection policies apply to apps on devices that are enrolled devices only. If you select an unmanaged device the App Protection policies will apply to apps on devices, that are not enrolled in Intune (mam without enrollment). If you wish to apply App Protection policies for managed or unmanaged devices select both options.
- Now select the apps to which the policy targets, here we have 4 options as below. Once decided
- Target to Selected apps: This will allow us to select public apps that support Intune App SDK, and we can also target custom apps that support Intune APP SDK.
- All Apps: This will target all Microsoft apps and third-party apps integrated with Intue App SDK
- All Microsoft apps: This will target all Microsoft apps which have integrated with Intune App SDK
- Core Microsoft Apps: The core Microsoft apps include Microsoft Edge, PowerPoint, Excel, Word, Office, OneDrive, OneNote, Outlook, SharePoint, Teams, and Microsoft To Do.
After selecting the targeted applications and devices, click on Next, and let’s configure data protection restrictions which define how users interact with the data in the apps.
Data Transfer
These are the policies to manage the Data Transfer between the managed and unmanaged applications. These types of policies help with Data Loss Prevention (DLP).
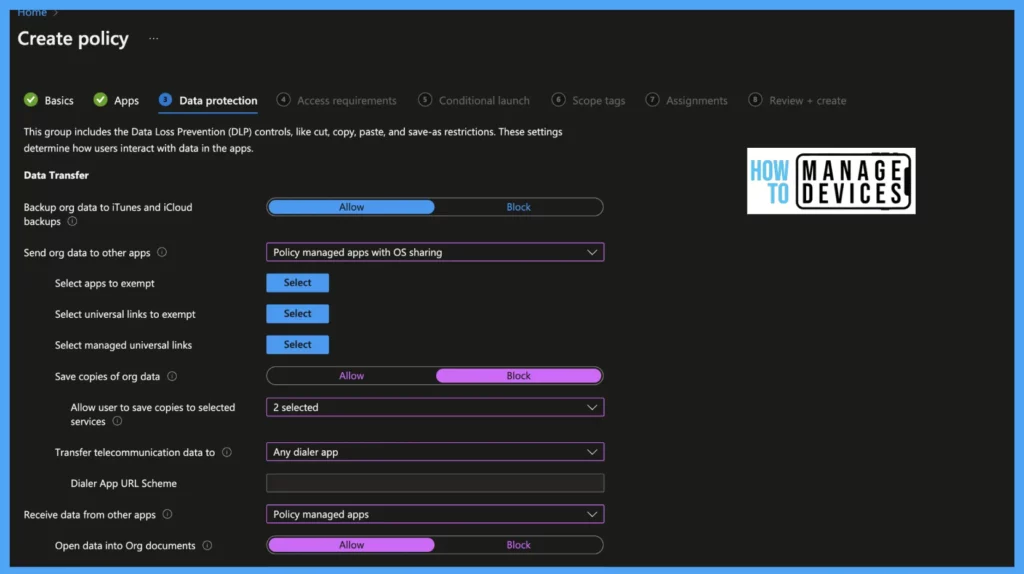
Backup org data to iTunes and iCloud backups: Enable it to Block if you want to block the organization’s data backup to iCloud and Select Allow if you want to allow to backup data.
Send org data to other apps: These settings define how the organization’s data is transferred between apps.
- All Apps: This will allow apps to send org data across all apps, least restrictions
- Policy-managed apps: When selected, this sends org data between policy-managed apps, no other apps receive data from managed apps
- Policy-managed apps with OS sharing: This setting will allow apps to send org data between policy-managed apps and allow them to send org data to other MDM-managed apps on enrolled devices. This setting applies only to enrolled devices.
- Policy-managed apps with Open-In/Share filtering: This setting will allow app transfer of data between policy-managed apps only. The sharing dialogue displays only policy-managed apps when selecting the documents/files open-in/share option.
- None: This doesn’t allow data transfer between any apps, even between policy-managed apps
Now, you need to select the applications that you want to exempt from data transfer policies. You need to understand that this might weaken your Intune App Protection policies.
- Select apps to exempt: Define apps to allow data transfer from managed to non-managed apps.
- Select universal links to exempt: Specify the universal links which can be opened in specified unmanaged applications from managed applications instead of the managed browsers.
- Select managed universal links: Specisfy the universal links which should be opened in the specified managed application instead of the protected browser determined by the Restrict web content transfer with other apps setting.
- Save copies of org data: Select Allow toggle to make a copy of the org data on the device. Block, this block saving of org data on the device storage but can allow saving to OneDrive, SharePoint, Box, local storage, and Photo library( select OneDrive and SharePoint to save your copies of your org data)
- Transfer telecommunication data: This will define how phone numbers are handled from managed applications
- None, do not transfer this data between apps: This will not transfer the phone number to any dialer.
- A specific dialer app: This will allow a particular dialer app to initiate calls when the phone number is detected. We need to specify the dialer app name(ex. Google dialer app)
- Any dialer app: Allow any dialer app to initiate calls
Is it allowed to receive data from other unmanaged apps as per your security policies? If so, let’s look at the following policies and configure them as per your organization’s standards.
- Receive data from other apps: This is the exact opposite of Send org data to different apps settings, i.e., this will allow data to receive from other/unmanaged apps
- None: When selected, managed apps do not allow data transfer from any apps, including policy-managed apps
- All Apps: Allow data transfer from all apps (including managed and unmanaged apps)
- Policy-managed apps: Allow data transfer within policy-managed apps
- All apps with incoming org data: Allow data transfer from all apps and treat app data without user identity as from your org data. This setting will be applicable only for enrolled devices.
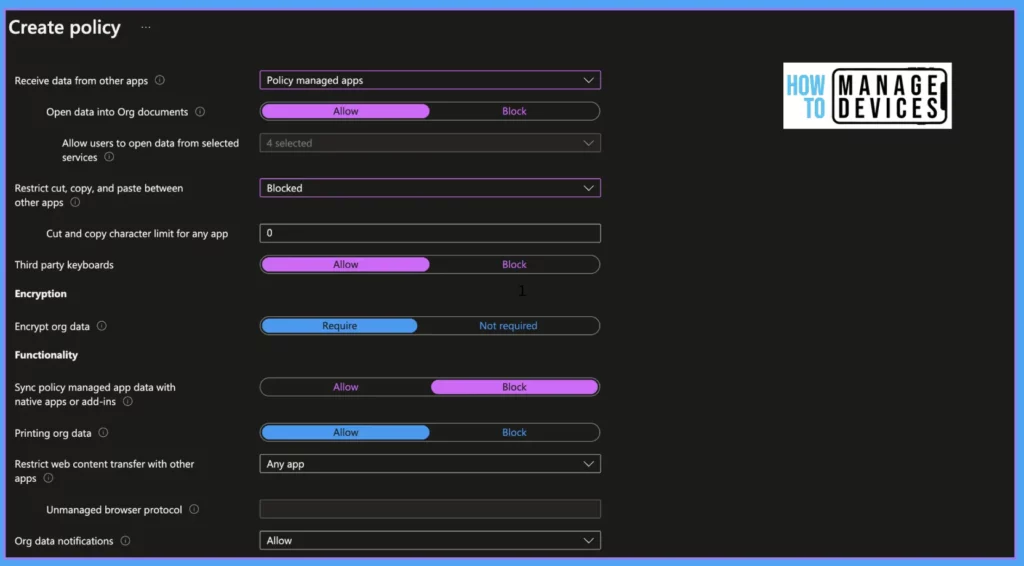
Open data into Org documents: This setting will be enabled only to receive data from other apps and is set to policy-managed apps. Set to Block if you want to block the open options. This will allow admins to allow users to open desired apps like OneDrive, SharePoint, Camera, and PhoLibrary.
- Restrict cut, copy, and paste between other apps: If you want to restrict users from copying, cut, and pasting the organizational data from managed apps, Use these conditions.
- Block: Blocks copy, cut and paste data across all apps, even in managed apps
- Policy Managed apps: Allow copy, cut, and paste data across policy-managed apps
- Policy Managed apps with paste in: Allow copy, cut, and paste data across policy-managed apps and allow paste from other apps to managed apps.
- Any apps: Allow copying, cut, and pasting data on any apps with no restrictions.
Cut and copy character limit for any app: Define the number of characters allowed to copy and cut from managed apps to other apps. When we define, this will allow users to copy ad cut specified characters irrespective above restriction i.e, Restrict cut, copy, and paste between other apps restrictions.
Third-party keyboards: If you want Block third-party keyboards, set the value to Block else, and set the value as Allow. When set block, users will receive a message that Third-party keyboards are blocked for the first time use of managed apps.
Encryption
Encrypt org data: When set Require, Intune will enforce device-level iOS/iPadOS encryption for managed apps when the device is locked. When enabled, users are forced to set a device-level PIN if the device does not have a one
Functionality
The following are the granular controls that you can set using Intune App protection policies. This is again going to help organizations to manage their data and protect it.
Sync policy managed app data with native apps or add-ins: Set Block to not allow saving data of managed apps to native apps like contacts calendar and widgets. This setting is applied only to the Outlook app. When Allowed, the policy-managed apps sync the data to a native app.
- Printing org data: If you want to block users from printing org data, set the value to Block, else set it to Allow
- Restrict web content transfer with other apps: This restriction will define how web content i.e, hyperlinks opened from managed apps
- Any apps: Open web URLs on any browser
- Microsoft Edge: When set to Microsoft Edge, web URLs are opened in Microsoft Edge.
- Unmanaged browser: This will allow web URLs to open in an unmanaged browser defined in the Unmanaged browser protocol. (like https:// or HTTP)
- Org data notifications: This value allows or blocks the notifications of org data(notifications for Outlook apps)
- Blocked: Do not share notifications
- Block org data: Do not share org data in notifications.
- Allow: Shares org data in all notifications
After selecting data protection restrictions as above, click on next to select Application access requirement restrictions. In this section, we will define how user access policy-managed apps. Let’s see what restrictions are available for us.
Access Requirements
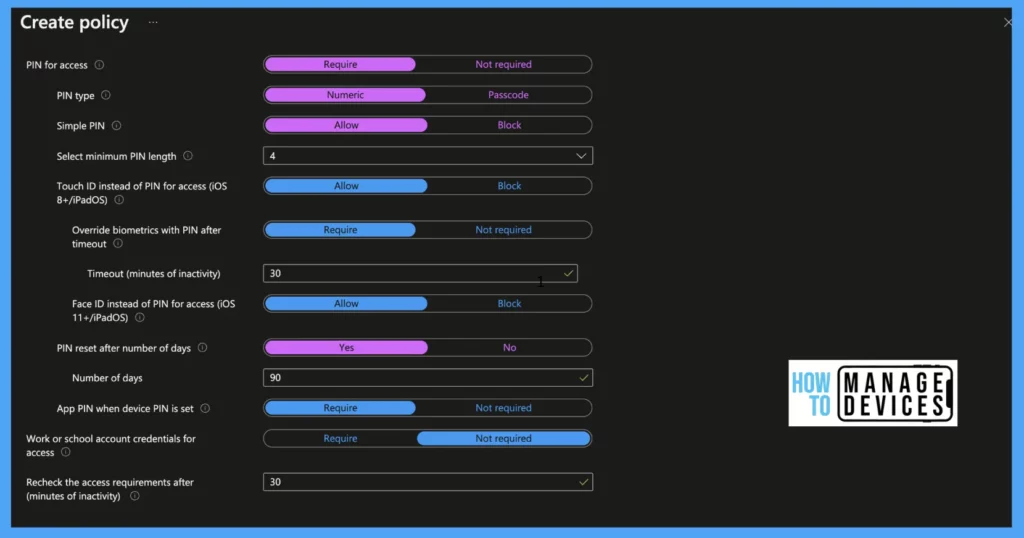
These are the PIN requirements that you can set up for personal iOS or iPadOS devices using Intune App protection policies. You need to consider the end-user experience when you set up a PIN policy for mobile devices.
- PIN for access: When set to Required, it enforces the app to have a PIN. Users will be prompted to set a PIN for an app on its first launch.
- PIN Type: When PIN access is set to Required, we need to decide what type of PIN is required for accessing the app, either Numeric or Password. When set to Numeric, it is all numbers. Chose password if you require alphanumeric passcode for the app
- Simple PIN: When set to Allow, simple PIN allows users to have PINs like 1234 and 0000. Set the value to Block if you require to complex PIN for accessing the app
- Select Minimum PIN length: Define a numeric value to have a minimum length of PIN.
- Touch ID instead of PIN for access (iOS 8+): Set value to Allow, to allow users to unlock the app with Touch ID instead of PIN
- Override biometrics with PIN after timeout: When the value is set to Required, users will be prompted to enter the PIN for accessing, after the defined timeout. Users will continue to unlock the app using Touch ID till the timeout
- Timeout (minutes of inactivity): When the above value is set to Required, define a timeout(in mins) for TouchID
- Face ID instead of PIN for access (iOS 11+/iPadOS): As Apple introduced face ID, set this value to Allow if you want to allow users to unlock apps using FaceID. Else set the value to Block
- PIN reset after a number of days: Set Allow to change App PIN after a few days.
- Number of days: Set a numeric value to reset the PIN after these days(ideal case 90 days).
- App PIN when device PIN is set: Set the value to Require if you want users to have App PIN even when the device PIN is set on the enrolled device.
- Work or school account credentials for access: Set the value to Require if you want to allow access to the app. When set to require user is prompted to enter their work or school credentials to unlock the app. If PIN access is also set to require, the user is prompted to enter work or school credentials and PIN to access the app.
- Recheck the access requirements after (minutes of inactivity): Set value in minutes till then, the user will not be prompted to PIN
After defining the access requirements as pre your org requirement, click Next to proceed to Conditional Launch. In conditional launch, we will define conditions like min OS, Grace period to use the managed app. Let’s see the options available in the Conditional launch. Many of these settings will be filled with default values, and we can modify them as per our requirements.
Conditional Launch
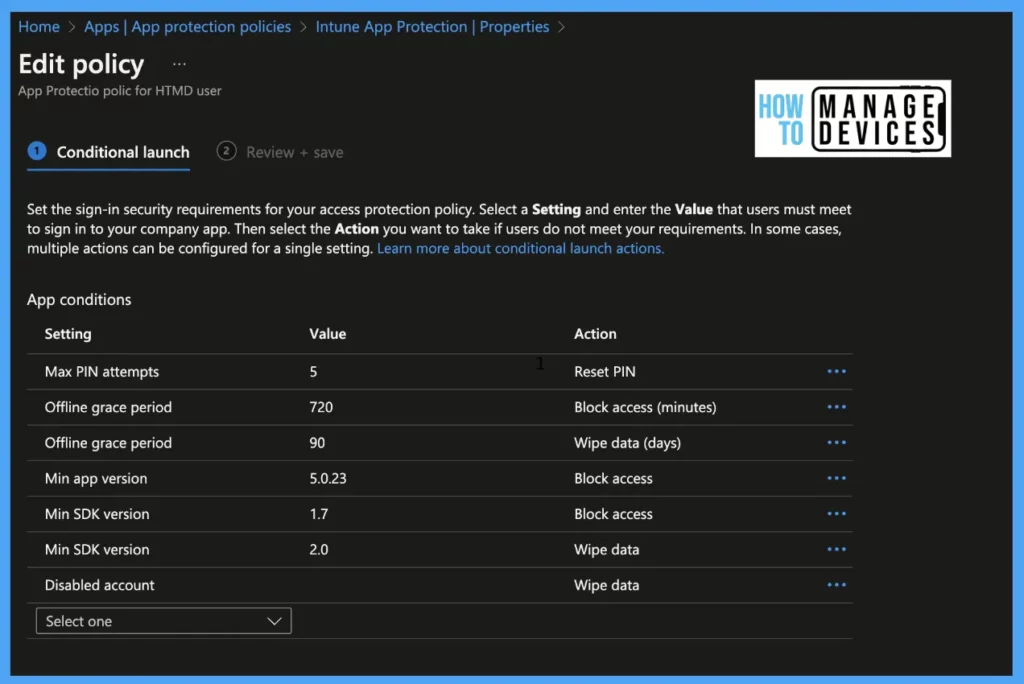
App Conditions are going to help to protect organization data when there is a situation such as a device being stolen, and someone is trying to steal the data by trying out different PIN combinations, etc.
- Max PIN attempts: Set a numeric value till when the user can enter the wrong PIN for accessing the app. Once the max attempts are reached, configure the value either to wipe data or reset the app PIN
- Offline Grace Period: Define the number of minutes the apps can run offline. After the defined time exceeds, access to the applications will be blocked. Similarly, we can set the value to the number of days to wipe data.
- Min App Version: Define the minimum version of the app to launch.
- Warn: if the app version falls below the defined value user gets a notification.
- Block access: The user will be blocked from accessing the app if the app version is below the defined value.
- Wipe Data: The user data associated with the app will be removed if the app is running on below defined app version
- Min SDK Version: Define the minimum Intune app protection policy SDK version to use the app.
- Block access: blocks access to the app if an application has below defined Intune app protection policy SDK
- Wipe data: The user data associated with the app will be removed if the app has Intune app protection policy SDK below version than defined
- Disable account: If the user account is disabled, we can block access to the app or wipe the data associated
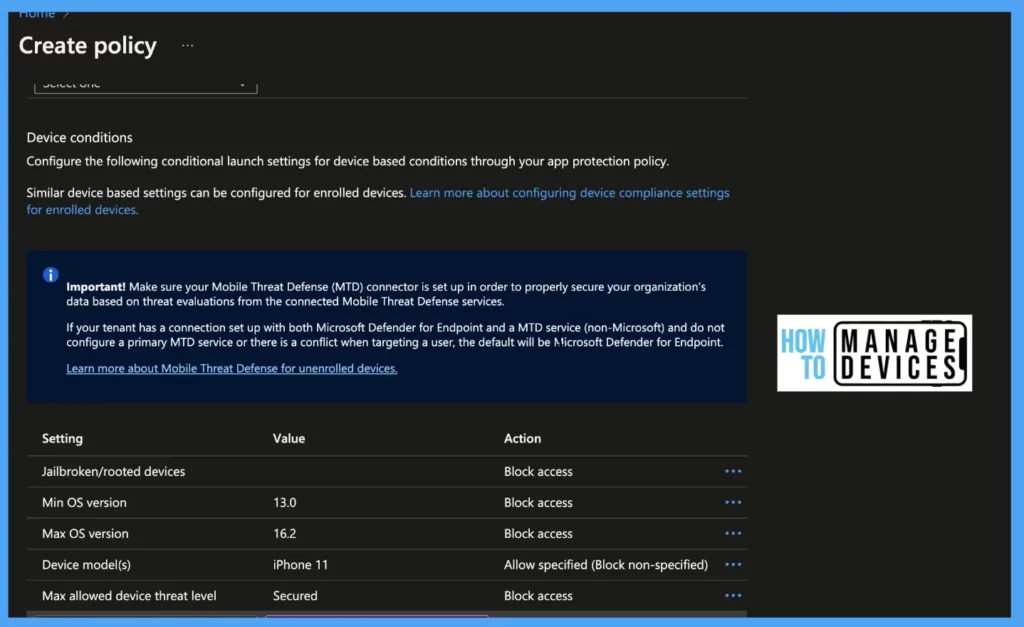
Intune Device conditions for Intune App Protection Policies
Device conditions for Intune App Protection Policies are again going to help with stronger protection with several checks such as Jailbroken, minimum version, maximum allowed thread level, etc.
- Jailbroken/Rooted Devices: When the device detects that device is jailbroken or rooted, we can Block the access and Wipe the data associated
- Min OS Version: Set Min OS required for accessing the app.
- Block access: If the device is running on below min OS user will be blocked from accessing the app
- Warn: The user will get a notification that the device is not meeting the required Min OS, and the notification can be dismissed
- Wipe data: If the device is below defied OS the user data will be wiped out
- Max OS Version: Set Max OS required for accessing the app
- Block access: If the device is running on below min OS user will be blocked from accessing the app
- Warn: The user will get a notification that the device is not meeting the required OS, and the notification can be dismissed
- Wipe data: If the device is running on higher defined OS, the user data will be wiped out
Device Model: If your org decides to allow specified device models to access managed apps, define the device models separated by a semicolon, and the values are not case sensitive.
- Allow specified (Block non-specified): This will allow specified devices only to access data on managed apps, the rest of the devices will be blocked access
- Allow specified (Wipe non-specified): This will allow specified devices only to access data on managed apps, the data on the rest of the devices will be wiped.
Max allowed device threat level: Intune will provide access to managed apps based on the threat level defined by MTD. This requires the integration of Intune with MTD. We can define secure level as Secured, High, Low, or Medium.
- Block access: If the device does not fulfill the required threat level, access to the app will be blocked
- Wipe Data: The data associated with the app will be wiped if the device doesn’t fulfill the required threat level.
Now we have configured Data protection, Access Requirements, and Conditional Launch, click on Next and select the scope tags, if any, then click on groups, select the group you want to assign to, and then click on Review, review the configurations once again, and click create.
NOTE: In Conditional Launch, we can select the same restriction multiple times with the same or different action items. For the min app restriction version, create a separate policy for each app, as the app has different versions.
Conclusion
So, in this article, we learned what are App Protection Policies and what restrictions can be configured for protecting organizational data. Let’s discuss how these policies will be applied to users and how these policies can be managed in another article.
The following is some of the content from the HTMD team, and I’m sure this will help you with Intune App protection policy decision-making (Intune Design Decisions) and creation. An old video (the audio music is a bit annoying – make sure to mute the audio) to get some end-user experience with Intune app protection policies is given below.
Author
About Author – Narendra Kumar Malepati (Naren) has 11+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.

#Hello Anoop, I have been working on IOS-BYOD device enrollment and pushed the Apps for company portal and installed successfully. But I have stucked certain point i.e configuring App protection policy (IOS) platform (Access requirements – PIN Setup for managed Apps)..If any one idea about this policy and configuration please #help me on this..
Hi Brahma,
Could you please explain more about the issue you are facing
Hi Naren,
Thank you for your response.
The App protection policy creation Pin setup is working fine as expected.
We followed the same article and created the app protection, but we are experiencing the following issue.
We have configured the App protection policy for BYOD(Android/IOS) devices but when we are trying to download the any file from Microsoft Teams we are getting the error Like–These actions have been turned off for your organization. You can still preview files. Though.
Note : We are able to download the files from MS-Outlook to OneDrive/SharePoint.
Please #help on the above issue. Thanks in Advance for your support.
Do you have a guide on how to make an IOS device be seen as “managed” I am finding mixed things around app configuration policies, and when i try to push app configuration policies to IOS devices they are marked as not applicable, thus my devices from the eyes of App protection policies, are still showing as unmanaged.
Hi, is there a way using Edge under “Restrict web content transfer with other apps” where some URLs from a managed app, a link inside email for example, can be in exception so it is opened directly on any other browser, unmanaged?