Let’s check how to create AppLocker Policies to Secure Windows Environments. These Applocker policies can help to build appropriate Windows Information Protection (WIP) using Intune.
Applocker was introduced with the Windows 7 operating system and Windows Server 2008 R2. It helps you determine which applications and settings users can run.
If you need to prevent an application from running, AppLocker provides a simple interface. This includes executable files, scripts, Windows Installer files, dynamic-link libraries (DLLs), packaged apps, and packaged app installers.
AppLocker helps reduce administrative overhead and the organization’s cost of managing computing resources by decreasing the number of help desk calls that result from users running unapproved apps.
Table of Contents
It requires no additional licensing.
Overview– Create AppLocker Policies
AppLocker is included with enterprise-level Windows editions. You can enforce the rules on a single computer using the Local Security Policy editor (secpol.msc). For a group of computers, you can use the Group Policy Management Console or MDT, SCCM, or MECM.
Requirements
- AppLocker does not have any specific hardware requirements.
- Operating system requirements Refer to Microsoft Blog.
Note – You can configure AppLocker policies on any edition of Windows 10, but you can only enforce AppLocker on devices running Windows 10 Enterprise, Education, or Windows Server 2016 later..
Why does AppLocker exist?
AppLocker can help you in the following ways to control applications within your organization:-
AppLocker helps reduce administrative overhead and the organization’s cost of managing computing resources by decreasing the number of Help Desk calls that result from users running unapproved apps. AppLocker addresses the following app security scenarios:
• Application inventory: It has the ability to enforce its policy in an audit-only mode where all app access activity is registered in event logs. These events can be collected for further analysis. Windows PowerShell cmdlets also help you analyze this data programmatically.
• Protection against unwanted software: AppLocker can block apps from running when they are excluded from the list of allowed apps. When AppLocker rules are enforced in the production environment, any apps not included in the allowed rules are blocked from running.
• Licensing: AppLocker can help you create rules preventing unlicensed software from running and restrict licensed software to authorized users.
• Standardization: AppLocker policies can be configured to allow only supported or approved apps to run on computers within a business group. This permits a more uniform app deployment.
• Manageability: AppLocker includes several improvements in manageability compared to its predecessor, Software Restriction Policies. These include importing and exporting policies, automatic rule generation from multiple files, audit-only mode deployment, and Windows PowerShell cmdlets.
How does it work?
An AppLocker rule is a control placed on a file to govern whether it can run for a specific user or group. Rules apply to different types of conditions, collections, and files.
Architecture and components
AppLocker relies on the Application Identity Service to provide attributes for a file and to evaluate the AppLocker policy for the file. AppLocker policies are conditional access control entries (ACEs), and policies are evaluated by using the attribute-based access control SeAccessCheckWithSecurityAttributes or AuthzAccessCheck functions.
AppLocker provides three ways to intercept and validate if a file can execute.
- A new process is created
- A script is run
- A DLL is loaded
Process Overview for Deploying AppLocker
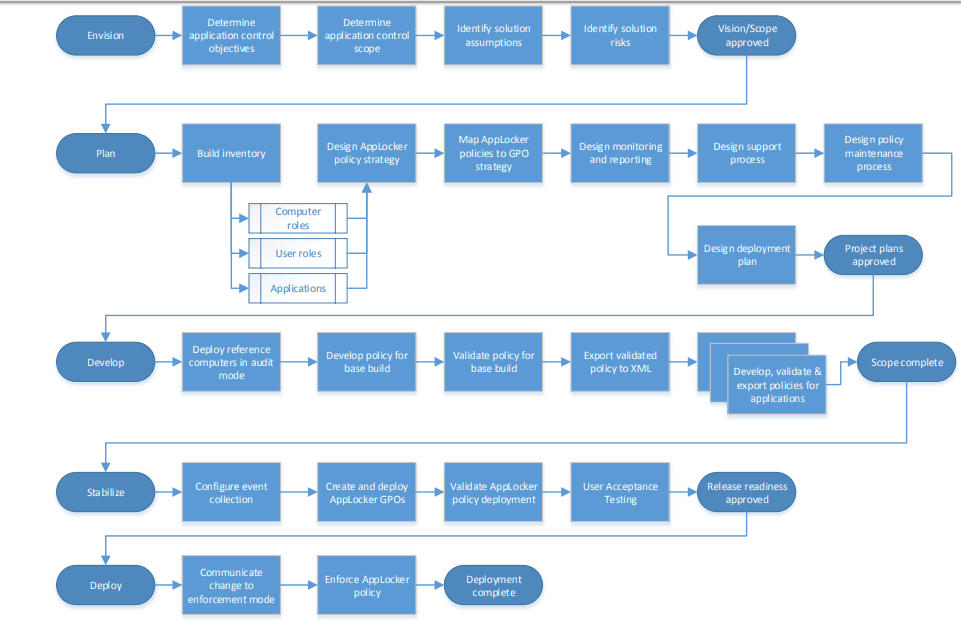
The phases are summarized as follows –
- Envision – Determine the objectives and scope and identify assumptions and risks.
- Plan – Perform a detailed environment analysis with computers, users’ roles, and applications to be controlled.
- Develop – Create AppLocker rules on reference computers for the operating system and all applications. Test and refine the rules until they are ready for formal testing, and then
export the rule sets to XML. - Stabilize – Configure centralized monitoring of AppLocker events by Performing detailed
validation. - Deploy – Change AppLocker to “Enforce rules” mode to complete the deployment of
AppLocker.
AppLocker Rule Collections
AppLocker enforces rules by grouping enforcement for different types of files. AppLocker includes five different types of rules collections:
- Executable files: .exe and .com
- Windows Installer files: .msi, mst, and .msp
- Scripts: .ps1, .bat, .cmd, .vbs, and .js
- DLLs: .dll and .ocx
- Packaged apps and packaged app installers: .appx
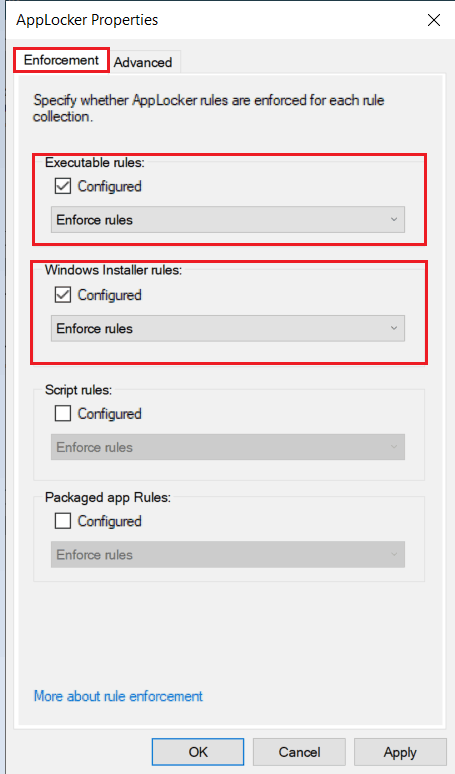
Configure Enforcement Rule
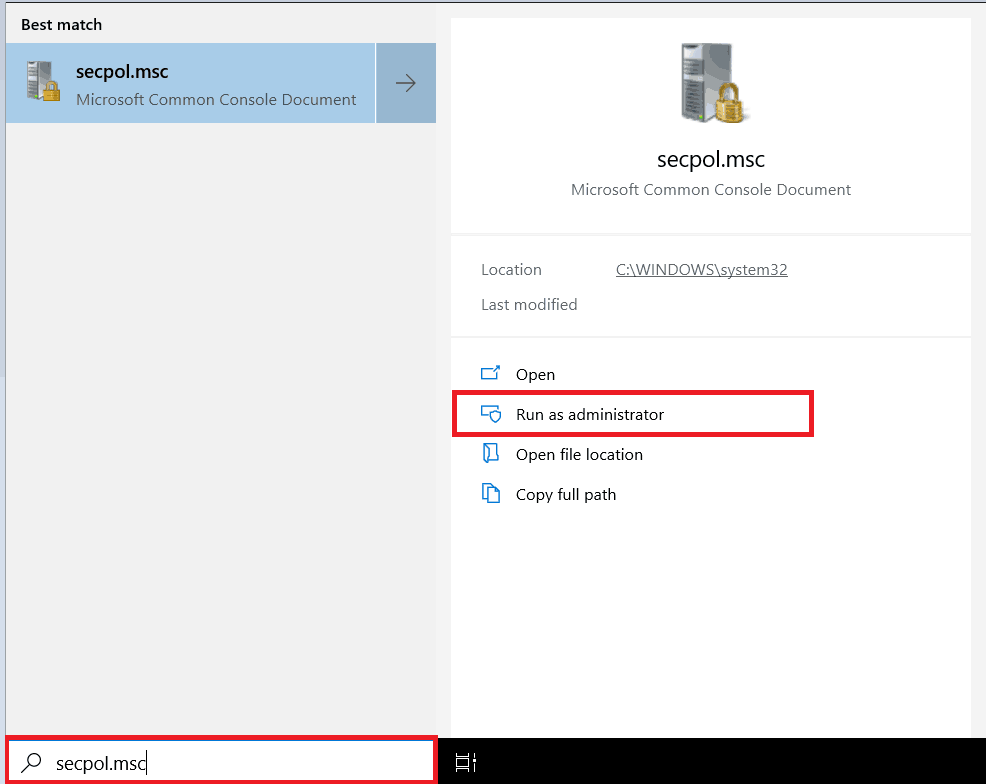
- Open Local Security Policy Editor. Type secpol.msc, and click Run as administrator.
- Expand Application Control Policies, click on AppLocker, and click on the Configure rule enforcement on the right side
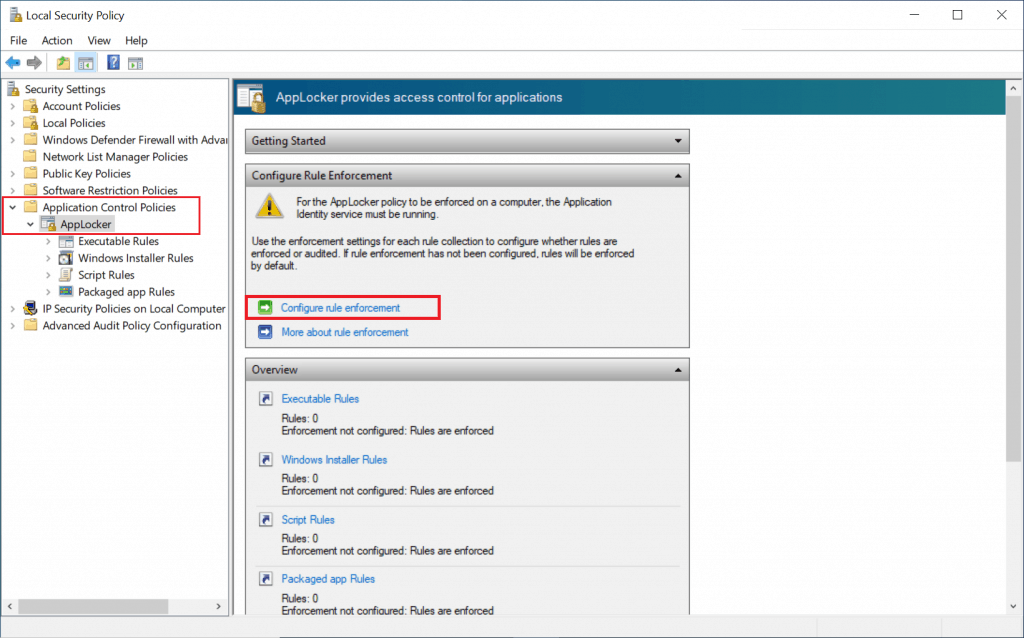
- You can configure the enforcement setting to Enforce rules or Audit only the rule collection.
- Enforce rules: rules are enforced for the rule collection, and all events are audited.
- Audit only, rules are only evaluated but all events generated from that evaluation are written to the AppLocker log.
- Check the Configured box under file types, click Apply, then OK.
Rule Conditions
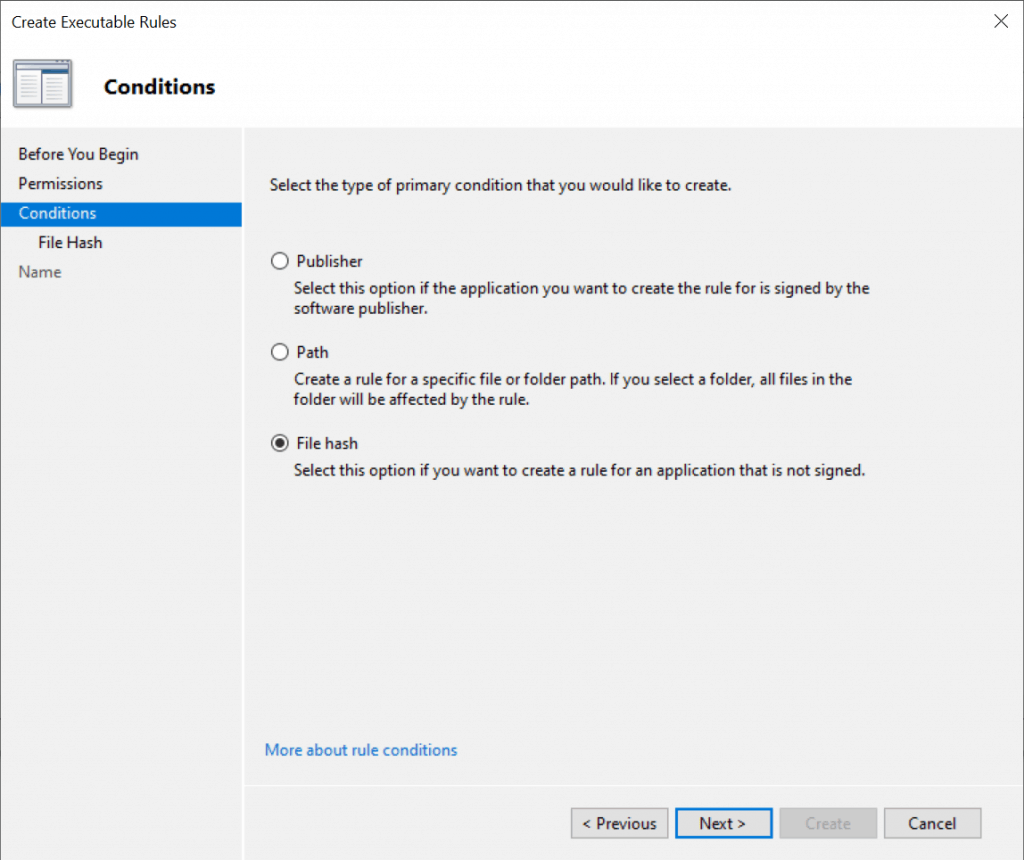
The three primary rule conditions are publisher, path, and file hash.
This helps you to determine on which the AppLocker rule is based. what condition, controls are available, and how it is applied.
Publisher – Publisher conditions can only identify digitally signed applications. It is easier to maintain compared to the file hash rule as doesn’t need to update frequently and a single rule can be implemented for the entire product suite.
Path – Path conditions are best for known paths such as program files and windows. It provides less security compared to other rules as if a rule that is configured to use a folder path holds subfolders that are writable by the local users.
File hash – File hash rules use a cryptographic hash system of the identified file for files that are not digitally signed. It is more secure compared to path rules.
Create AppLocker Rules
Open Local Security Policy Editor. Type secpol.msc, click Run as administrator.
AppLocker includes default rules for each rule collection. These rules are intended to help ensure that important system files will be allowed to run applocker.
- Expand Application Control Policies under AppLocker. right-click on Executable Rules Rules and click on Create Default Rules.
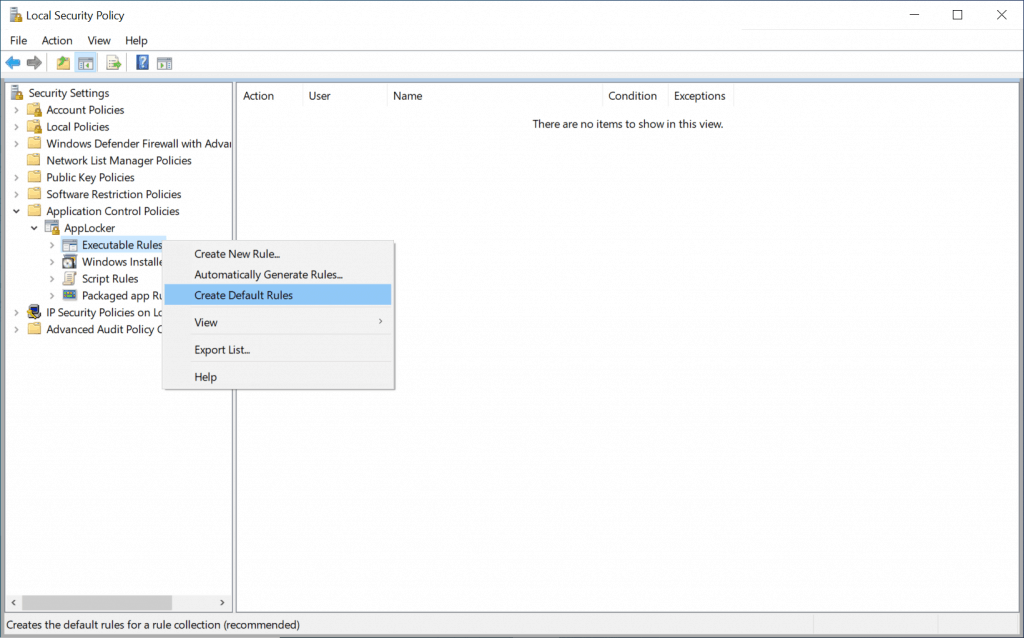
Important – You can use the default rules as a template when creating your own rules to allow files within the Windows folders to run. However, these rules are only meant to function as a starter policy when you are first testing AppLocker rules. The default rules can be modified in the same way as other AppLocker rule types.
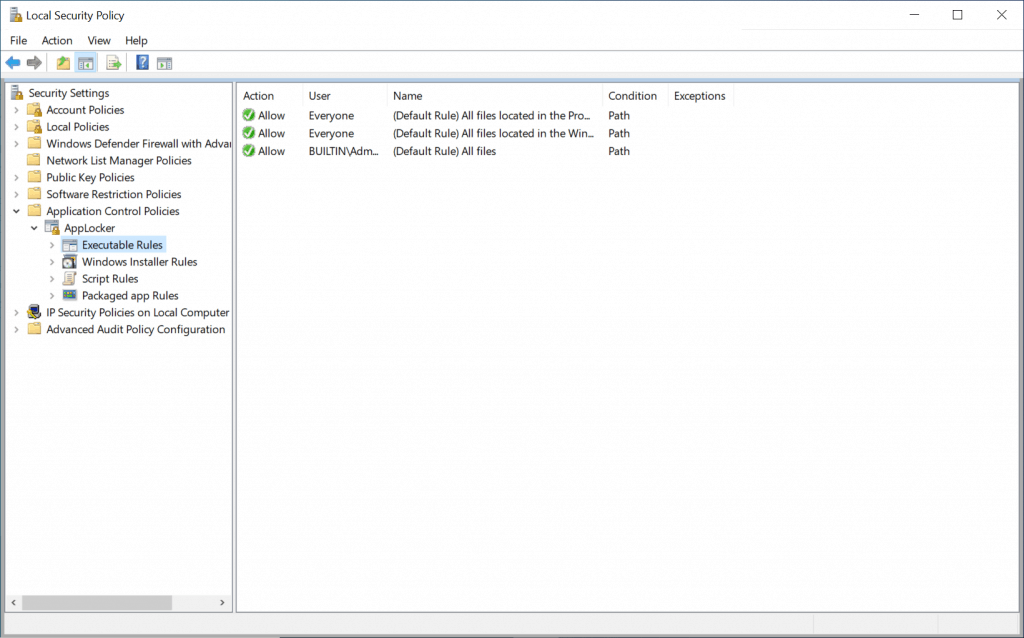
- Default rules have been created successfully, as shown below.
In this post, I’ll walk you through an example to create a new Executable file rule to restrict Mozilla Firefox execution for everyone.
In the left pane under AppLocker, right-click on Executable Rules, then select Create New Rule.
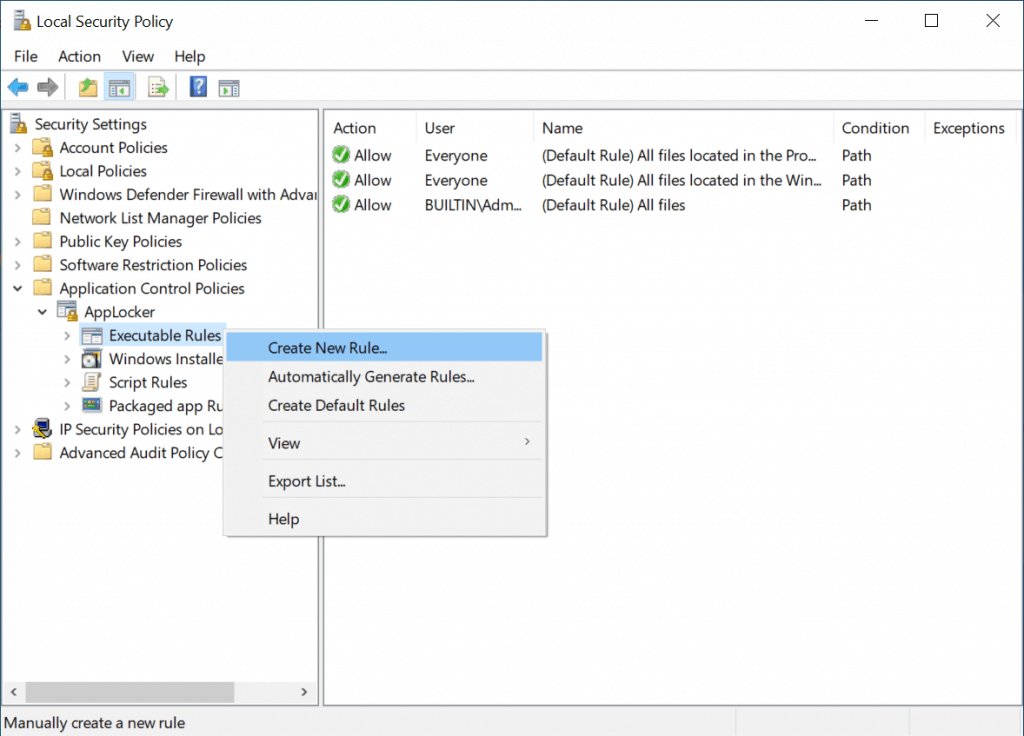
- Click on Next.
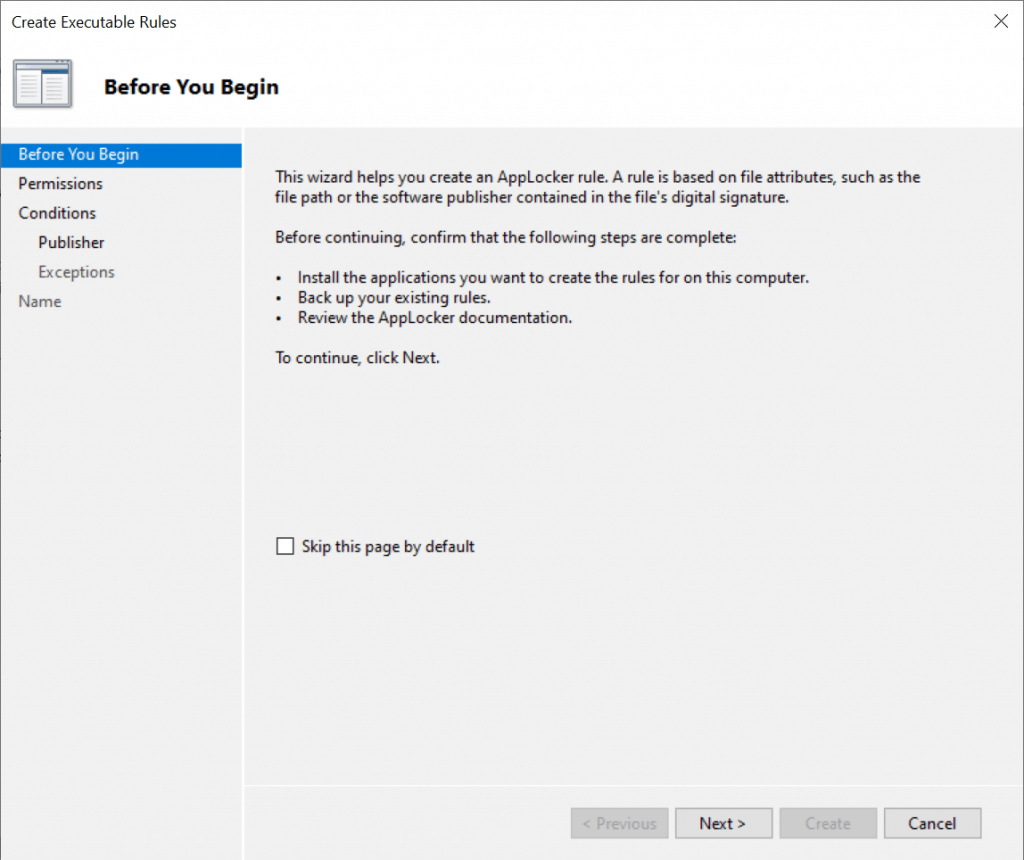
- If you want to specify a user or group to apply this rule on, click Select.
Note – By default setting is Everyone for all users and groups.
A rule can be configured to use allow or deny actions:
- Allow: You can specify which files are allowed to run for which particular user or groups of users in your environment.
- Deny: You can specify which files are not allowed to run for which particular user or groups of users in your environment.
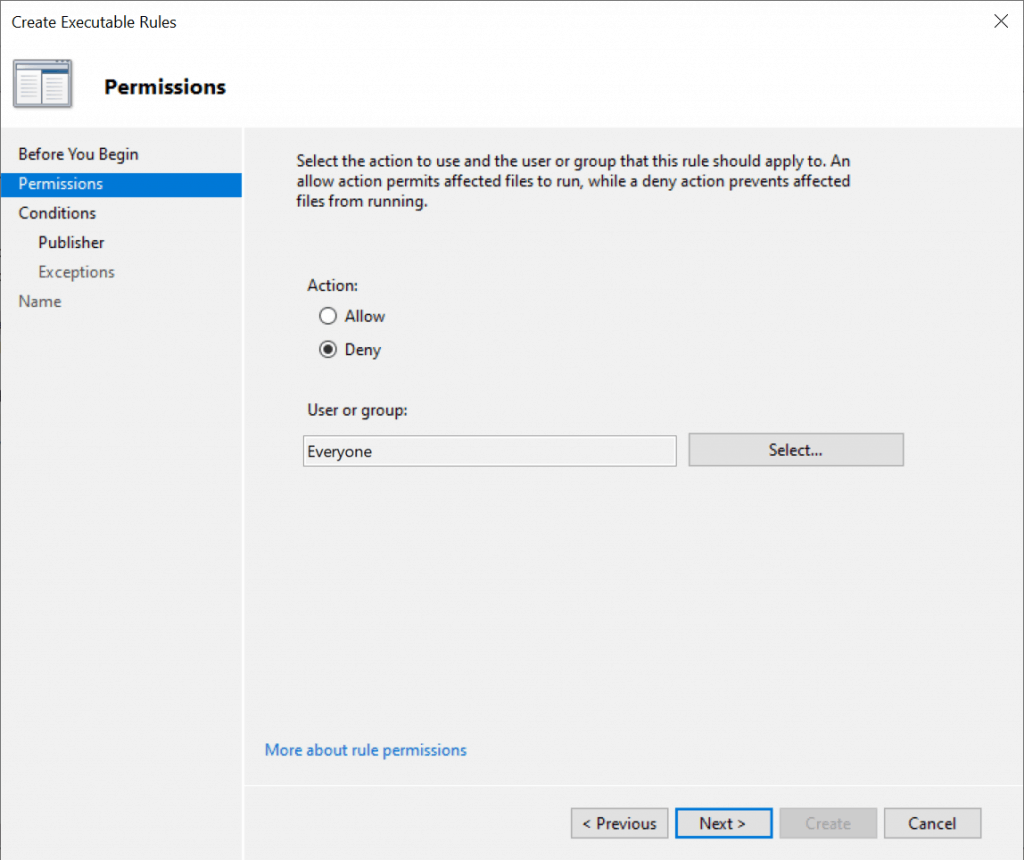
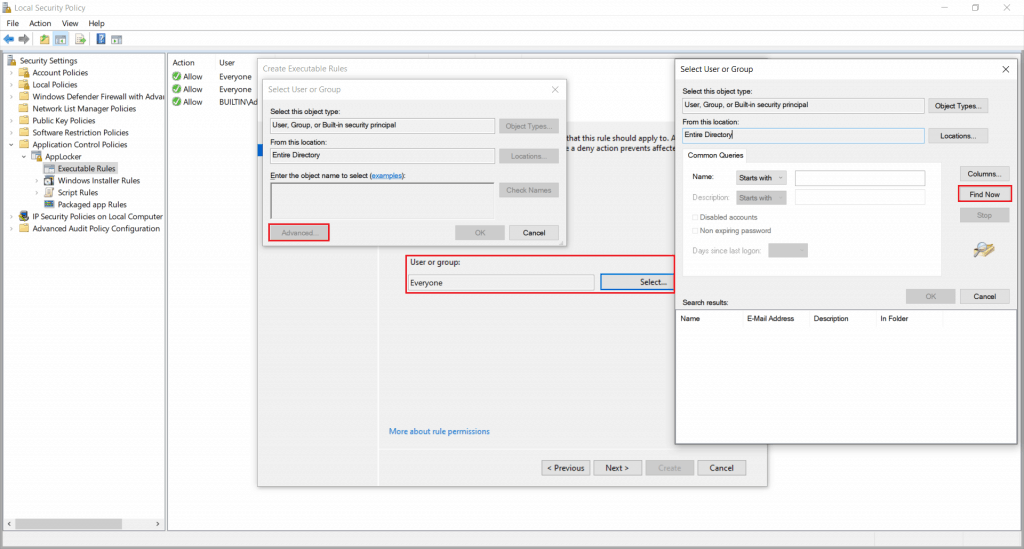
Click on the Advanced button, then click Find Now to Select a user or group you want to allow or deny.
- Then click OK.
I will select File hash condition on the Conditions page and then click Next.
File hash rules use a system-computed cryptographic hash of the identified file. For files that are not digitally signed, file hash rules are more secure than path rules.
Keep hash rules to a minimum – The rule must be updated each time a new file version is released.
Click Browse Folders and select the path for the apps that you want to allow or deny access. For this example, use “C:\Program Files”.
Note – If you want to block the application installation, you need to provide the executable files by Browse Files…
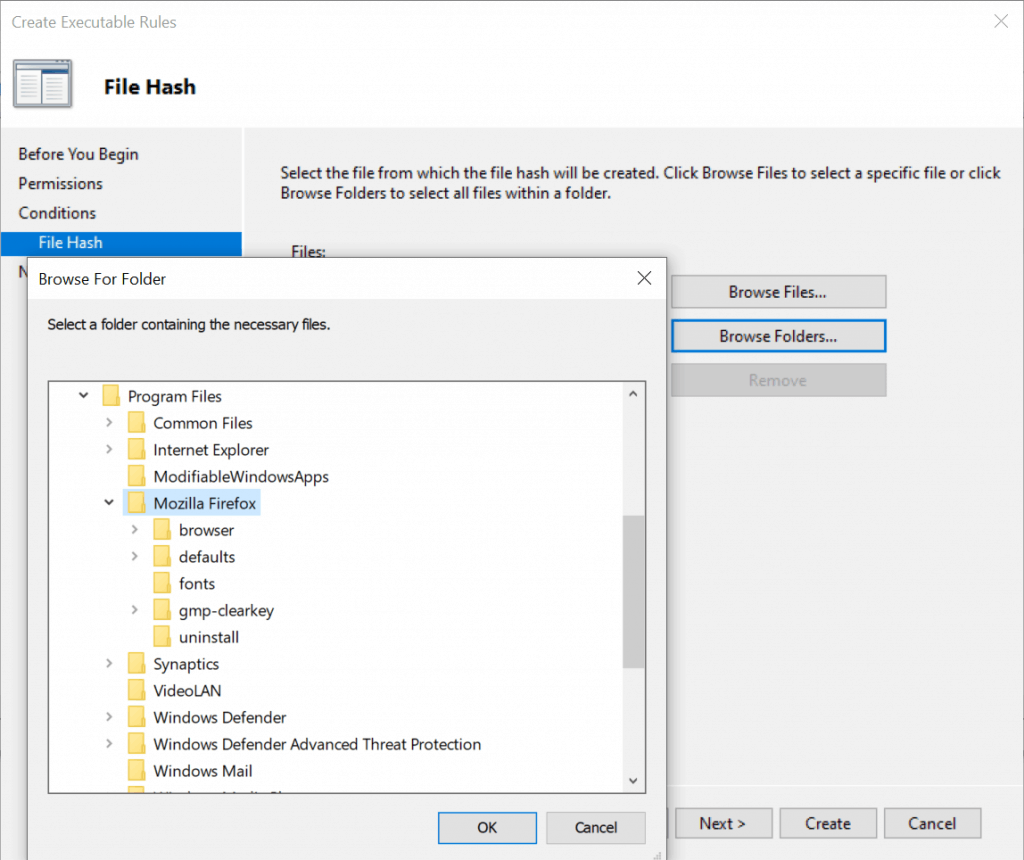
Select the file from which the file harsh will be created.
- The files in the folder have been added, then click Next.
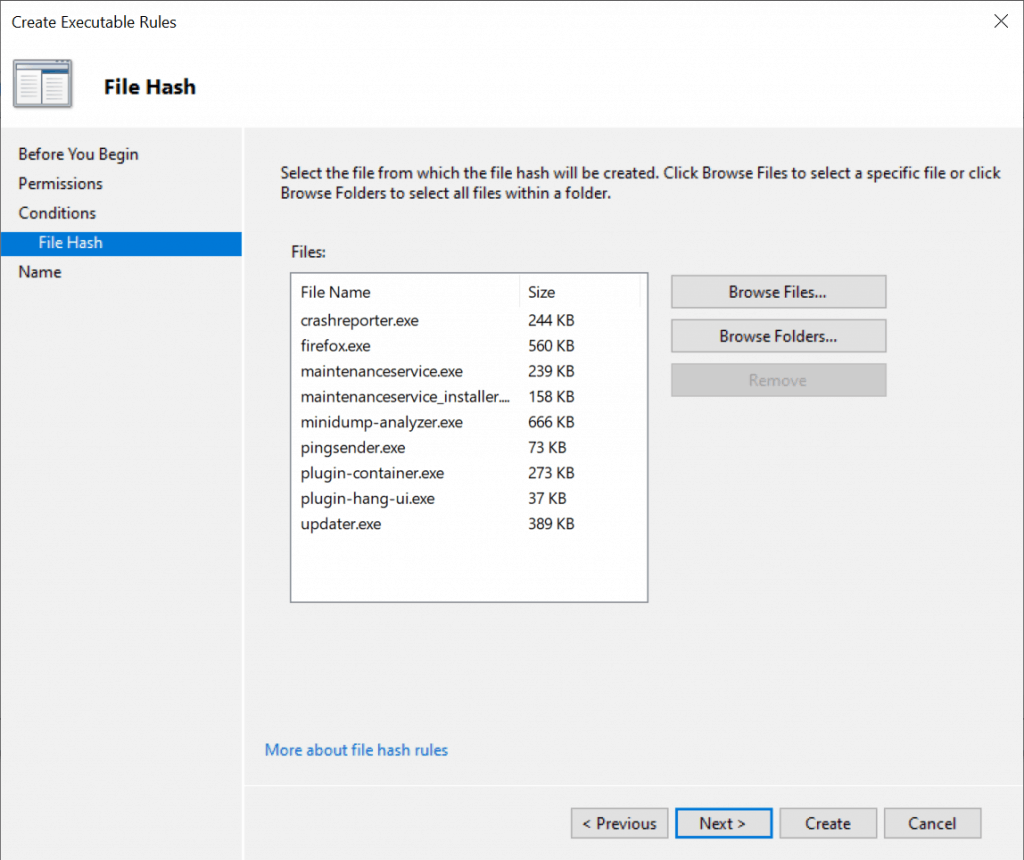
On the Name page, type a name and description for the rule, and then click Create.
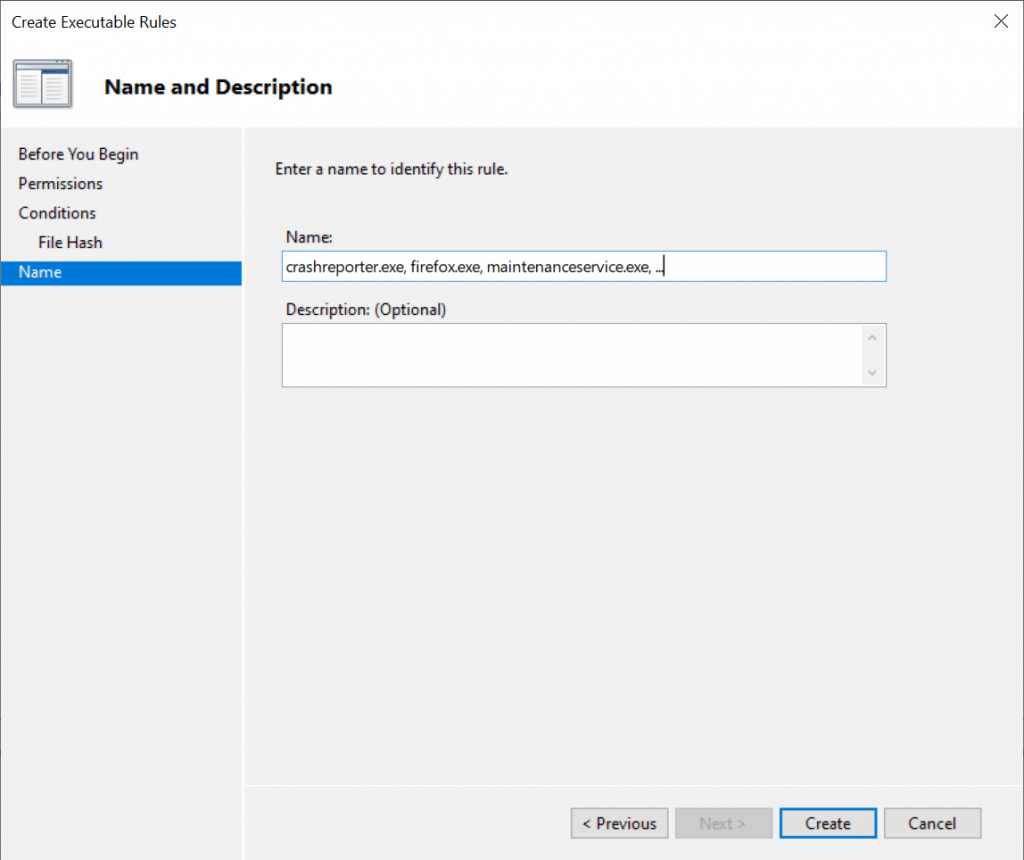
The rule restricting Mozilla firefox will now be created under “Executable Rules” as shown below.
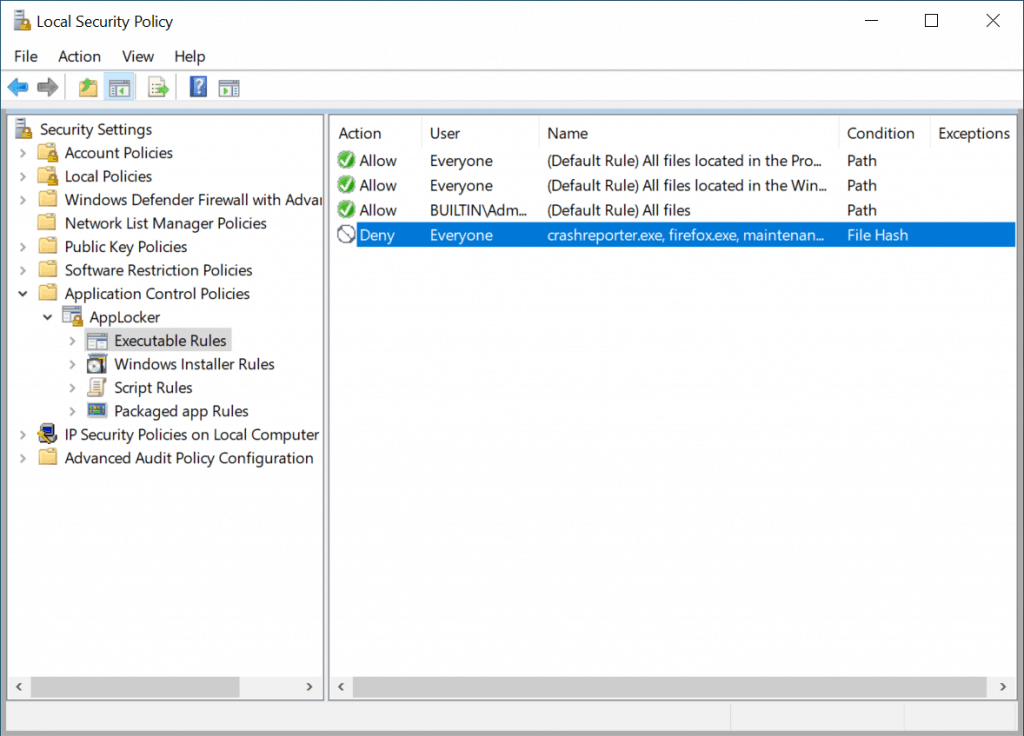
- Once done, close the Local Security Policy editor.
Repeat this by changing the—FileType parameter for each of the file types that rules will be created for (Exe, Script, WindowsInstaller, and Dll).
Export AppLocker Rules
To export an AppLocker policy to an XML file, simply right-click AppLocker in the console and select Export Policy.
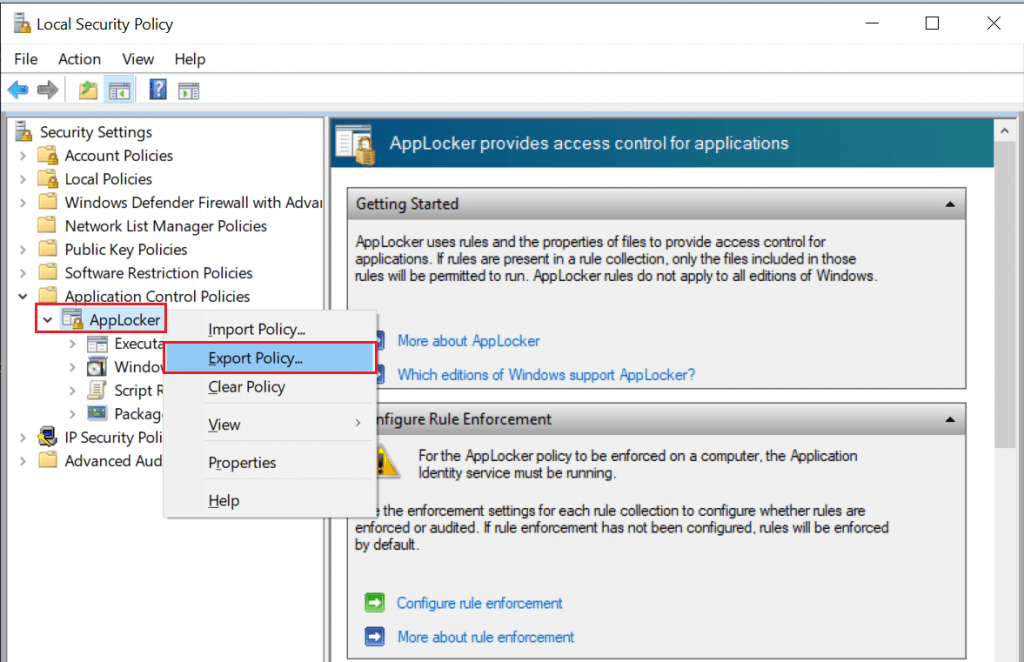
- Browse to the location where you want to save the XML file.
- In the File name box, type a file name for the XML file, and then click Save.
Clearing – Deleting AppLocker Rule
Once all of the AppLocker policies have been created and exported to XML, the local security policy of the reference computers should be cleared.
This will ensure that policy can be deployed and managed centrally and that the effective policy on the reference computers does not contain rules from the local policy.
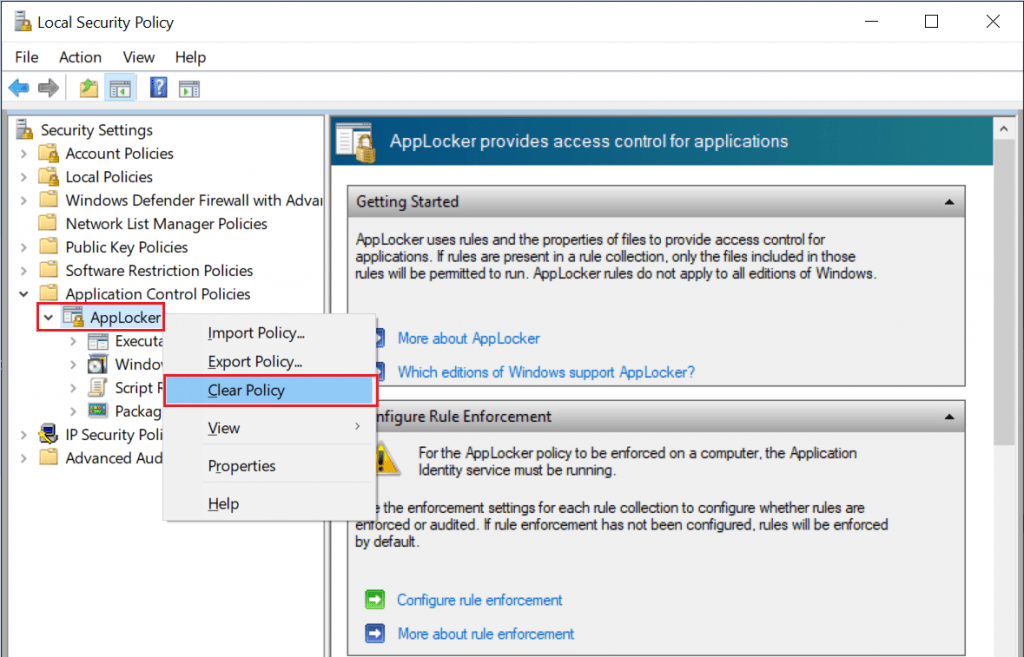
To clear AppLocker policy
From the AppLocker console, right-click AppLocker, and then click Clear Policy.
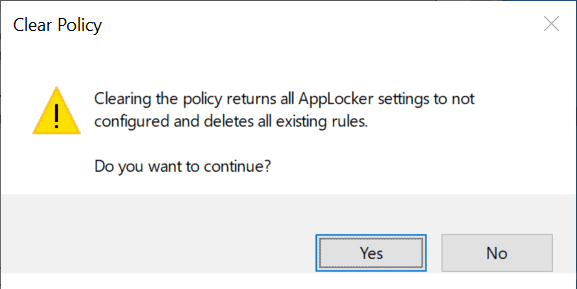
On the Clear Policy prompt, Click on Yes to confirm.
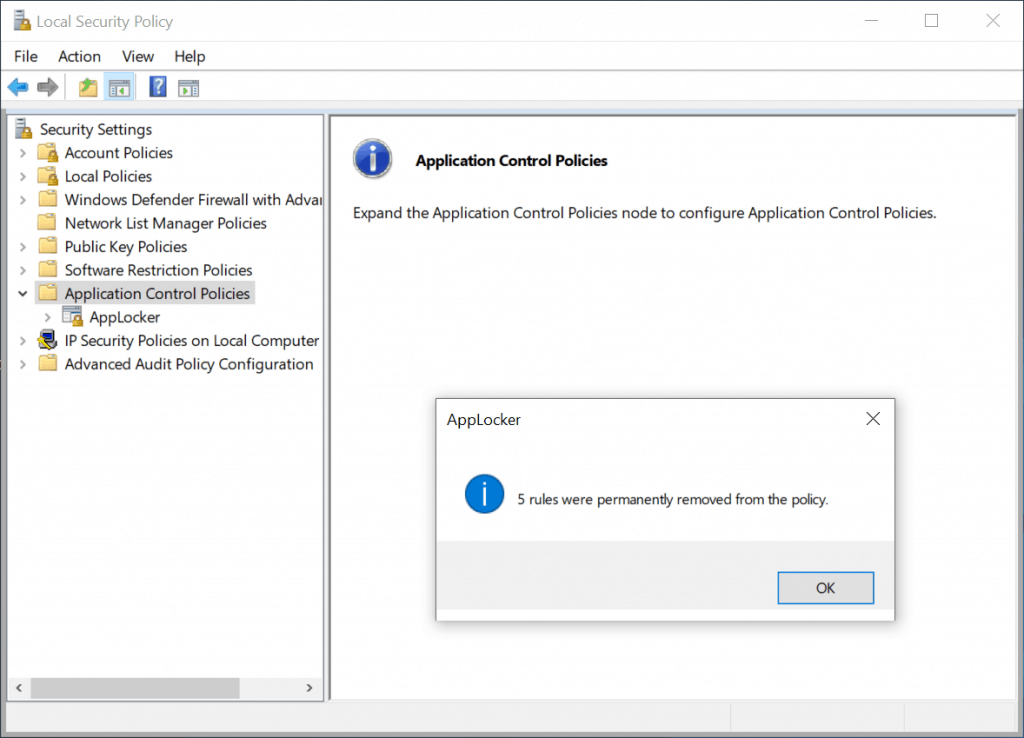
The AppLocker dialog box will notify you of how many rules were permanently removed. Click on OK.
- Reboot the machine.
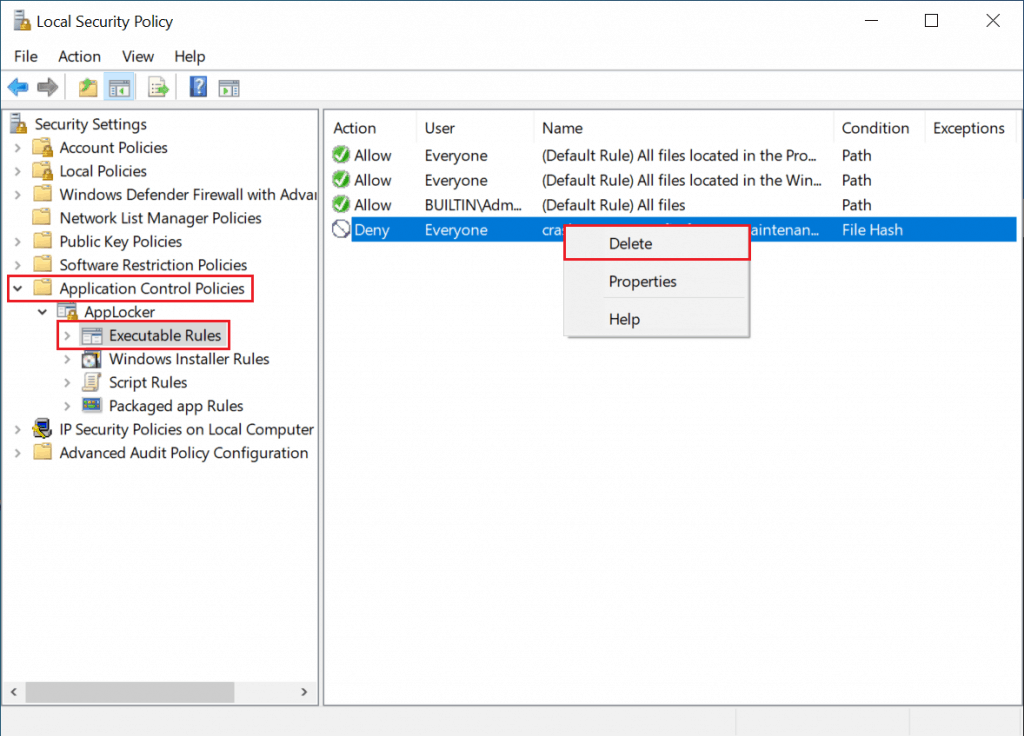
To delete a rule in an AppLocker policy
- Open the AppLocker console.
- Click the appropriate rule collection for which you want to delete the rule, then click Yes.
Develop Phase
Points to consider to test AppLocker validation.
- Deploy a reference computer that will be used for authoring of AppLocker rules.
- Configure the Application Identity service set to Automatic and running.
- Put AppLocker into “Audit only” mode so the rules created don’t block execution.
- Auto-generate AppLocker rules for each file category that will be used and manually edit them to meet exact requirements.
- Performed testing for all end-user and administrative usage cases and reviewed audit entries in the Event Log.
- Export AppLocker policies into individual XML files for later import.
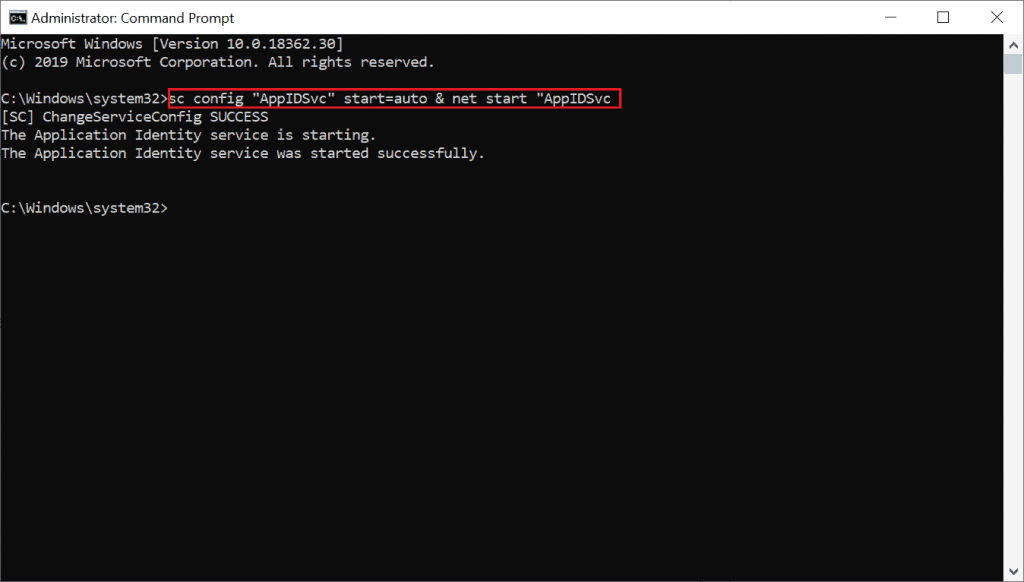
On Target Devices Make sure the Application Identity service is enabled, set to Automatic, and running. AppLocker cannot enforce rules if this service is not running.
- The Application Identity service determines and verifies an application’s identity. Stopping this service will prevent AppLocker policies from being enforced.
- Start to command prompt Run as administrator.
- Run the below command to ensure the Application Identity service is enabled and set to Automatic and running.
sc config "AppIDSvc" start=auto & net start "AppIDSvc"
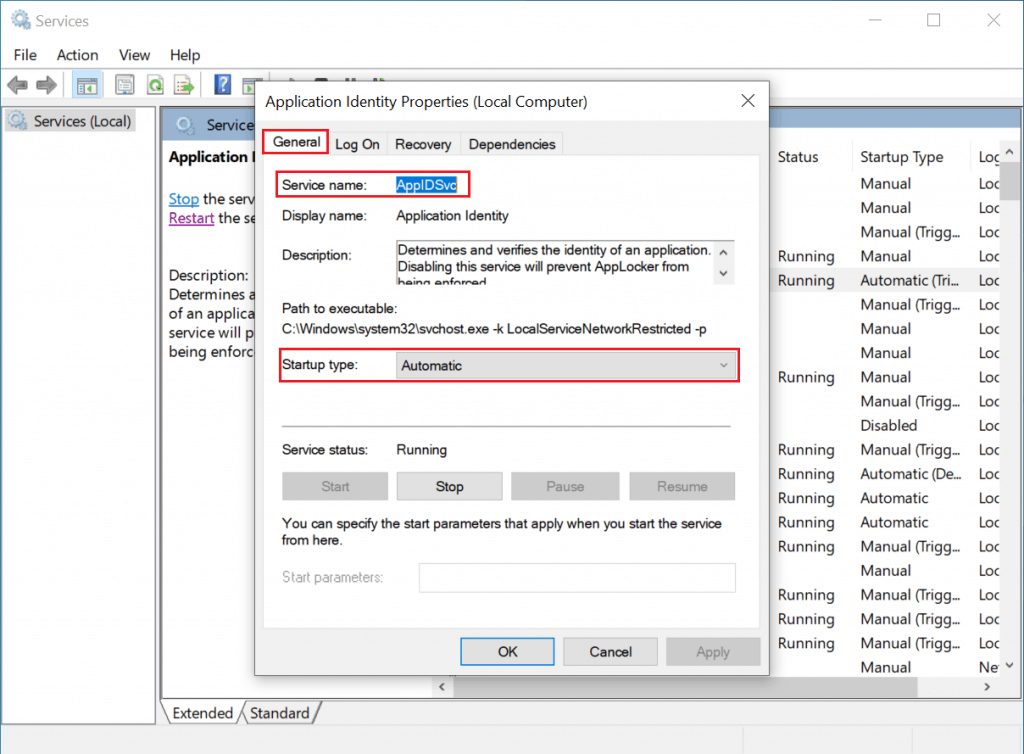
- To start the Application Identity service manually.
- Type services.msc in the start menu search box.
- Click the Services Run as an administrator, find Display Name “Application Identity”, and then click Start Service.
- Verify that the status for the Application Identity service is running.
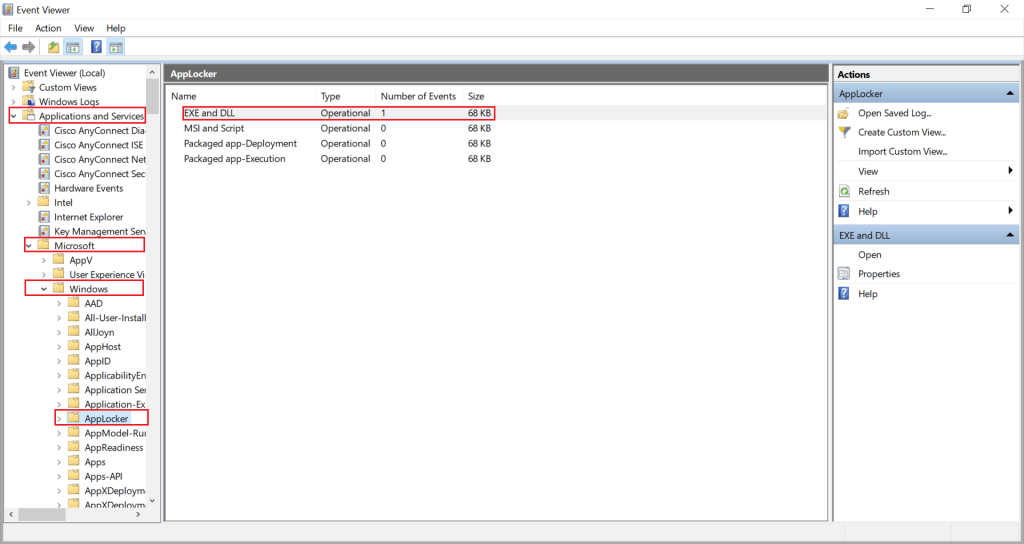
Analyze AppLocker Events
This gives you a fair understanding of how an AppLocker policy is delivered to and implemented on devices.
All AppLocker events are logged to Applications and Services event logs under the path Microsoft\Windows\AppLocker
- Microsoft-Windows-AppLocker/EXE and DLL
- Microsoft-Windows-AppLocker/MSI and Script
- Microsoft-Windows-AppLocker/Packaged app-Deployment
- Microsoft-Windows-AppLocker/Packaged app-Execution
A list of relevant AppLocker event IDs can be found in Microsoft Blog.
- Event ID – 8001, Indicates that the AppLocker policy was successfully applied to the computer.
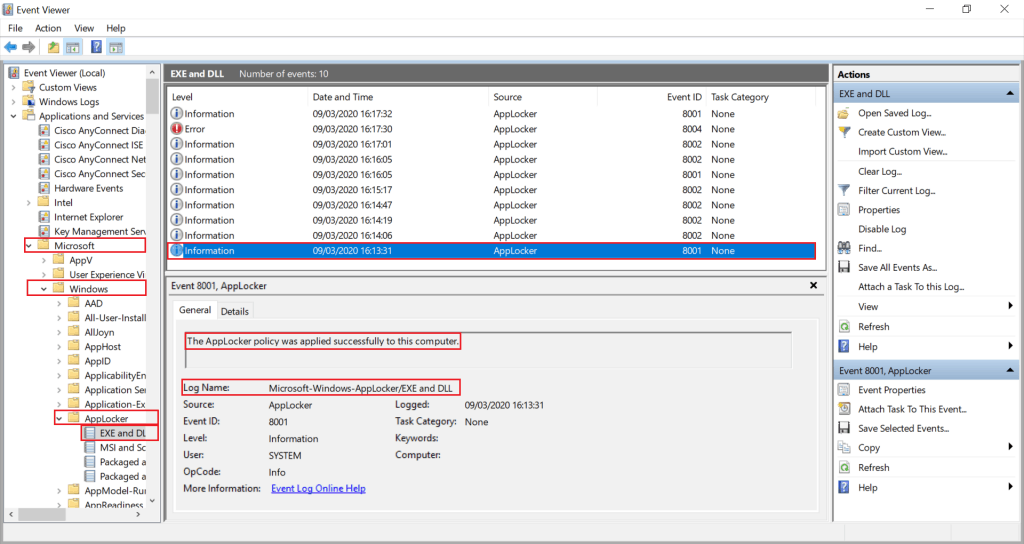
- Event ID – 8004, Indicated The .exe or .dll file cannot run.
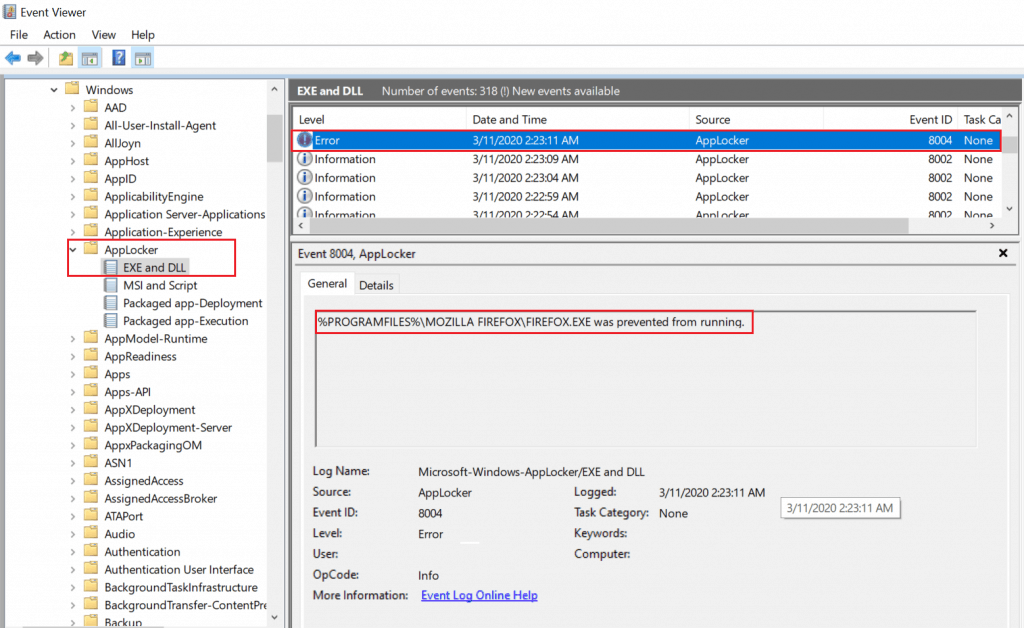
Results
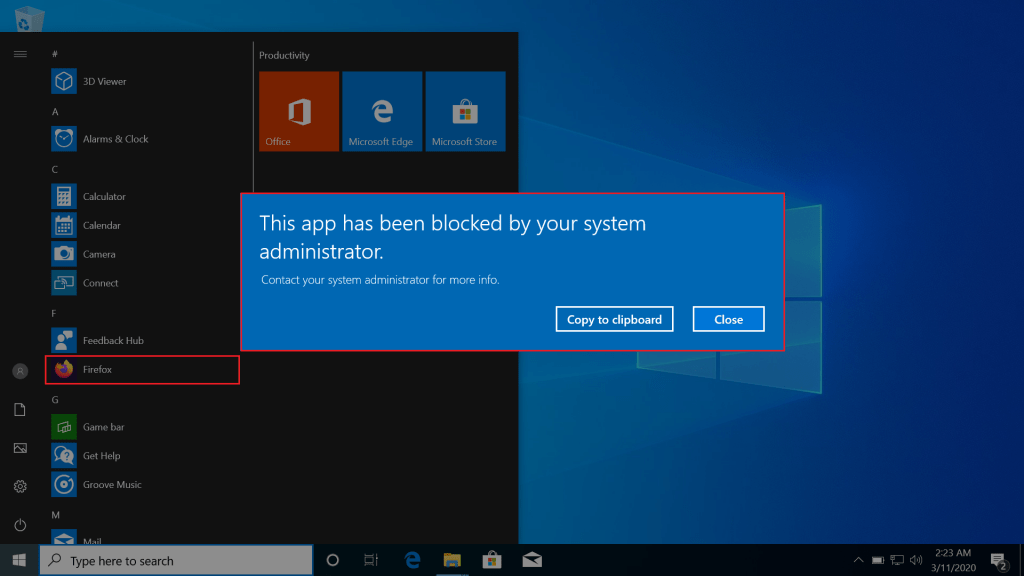
Once policies are successfully applied, users will get a prompt when trying to open a blocked executable (Mozilla Firefox).
“This app has been blocked by your system administrator”
Later, I will try to cover how we can apply the applocker policies based on path or publisher rules using SCCM or MECM. For that time, Stay Tuned!!
Resources
- AppLocker design guide
- How AppLocker works
- AppLocker deployment guide
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Jitesh has over five years of experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus area is the Windows 10 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.

Great explanation on this topic. Can you do one for Applocker with MS Intune? Looking forward to see the Intune post.
Thank you!
Hello Andy, Glad to know you liked it. Much appreciated your input. Surely we’ll try to cover for Intune as well. If we already have will share with you.
Is there explanation on Applocker for azure/intune
Hello Justin, you can go through below post by Joy.
+ Windows Information Protection | WIP Learn with Joy Part #1 | Intune https://www.anoopcnair.com/windows-information-protection-the-concepts-1/
+ https://www.anoopcnair.com/windows-information-protection-the-internals-2/
If you have any queries please reach us Via HTMDForum – htmdforum.com
*Note – You can configure AppLocker policies on any edition of Windows 10, but you can only enforce AppLocker on devices running Windows 10 Enterprise, Education or Windows Server 2016 later..*
Does the above sentence mean on the Windows Information Protection policy / Applocker policies with respect to WIP, will not get enforced on the Windows 10 Pro and Windows 10 Home devices?