The latest Defender Update KB2267602 (Version 1.381.2140.0) bug deletes shortcuts from the desktop, start menu, and taskbar. We noticed this issue in one of the HTMD Windows 10 Patch Tuesday post comments.
There are also reports that the latest def update KB2267602 (2089), causing ASR (Attack Surface Reduction) rule Block Win32 API Calls from Office Macro, is blocking Applications within Windows OS. I have included the details of restore options for removed shortcut links such as PowerShell Scripts.
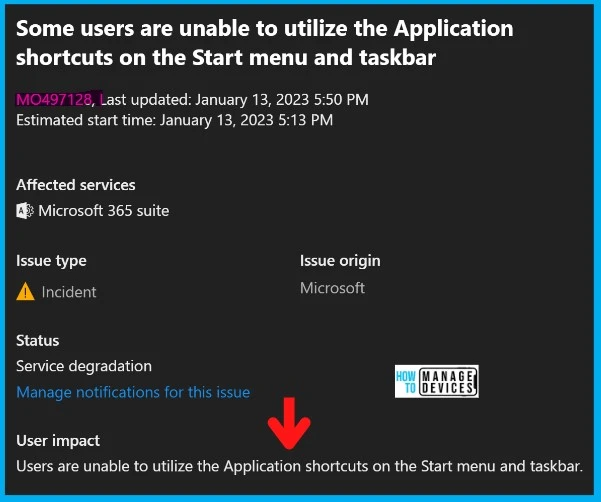
Microsoft has just published MO497128 details on this Microsoft 365 Suits category. Microsoft acknowledges that the issue is because of the defender def update issue. We will keep the post up to date with the latest information. Some users cannot utilize the Application shortcuts on the Start menu and taskbar.
Microsoft added a workaround solution to disable the ASR rule using Intune, Group Policy, PowerShell, etc. I have shared this in the below sections of this post. Microsoft Reverted the Offending ASR rule. More details are below.
Microsoft Recommendation – 13th Jan 2023 – 3:22 PM GMT – You take action to place the offending ASR rule into Audit Mode. Further information on how to perform these steps can be found in the More info about workaround actions given below.
The issue with Defender Update KB2267602 Bug – Deletes shortcuts
The shortcut icons may not appear or would not work. As per Microsoft, the Current status: Current status: MS reverted the offending ASR rule. However, this change is propagating throughout the environment and could take several hours to complete.
- Scope of impact: Impact is specific to some users served through the affected infrastructure.
More info: The shortcut icons may not appear or would not work. Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, as they have dependencies on the shortcut files.
More info from Microsoft: The shortcut icons may not appear or would not work. Microsoft also received reports that the ASR rule “Block Win32 API calls from Office macro” is deleting the application shortcuts.
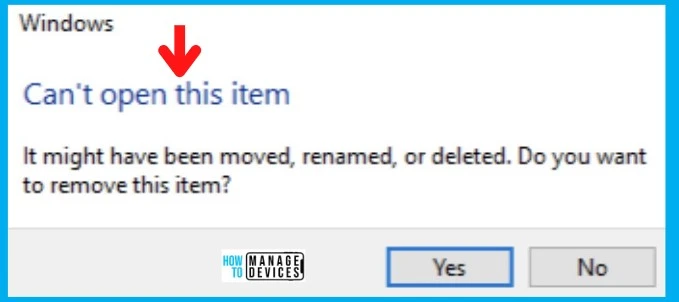
Let’s quickly look at the issue with Defender Update KB2267602 Bug. There are a lot of reports on this issue. The issue is reported by Matthew on Twitter.
Ben Owens reports on Twitter that Office updates are showing as updates, but shortcuts, start menu icons, and pinned taskbar items have gone. Many users are reporting this issue on social media platforms such as Twitter. Many customers have raised Sev A incidents to fix this issue, but no hardback from Microsoft yet on any fix.
James Robinson @SkipToEndpoint also confirmed the behavior of this. ASR for “Block Win32 API calls from Office macro” all over the place following Security Intelligence Update – KB2267602.
Workaround – Deletion of Shortcuts and Block Win32 API calls from Office macro
If you are using Intune, disabling the ASR rule did work. After a service sync, we can now recreate Shortcuts. For Office, a repair did the trick on my machine.
Wouter Visser confirmed that he changed the ASR rule from Block to Audit, which helped him to cover the impact for now in case you are managing Defender updates with Intune.
PowerShell Workaround to Stop the Impact
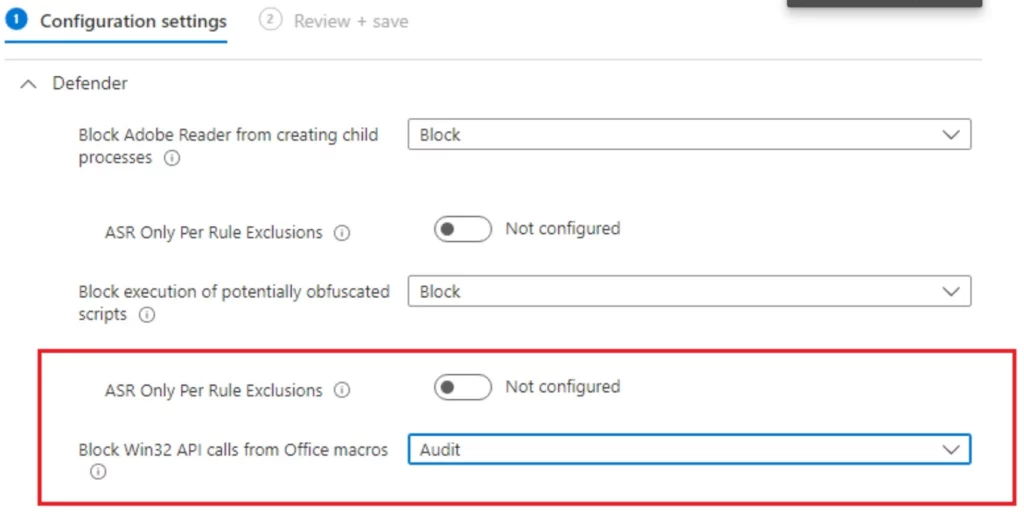
Microsoft recommends putting the ASR rule in Audit Mode to avoid further impact. This can be done through the following options.
- Using Powershell:
Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditModeIntune Workaround to Stop the Impact
Using Intune – https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
Group Policy Workaround to Stop the Impact
Using Group Policy – https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
Note that ASR rule “Block Win32 API calls from Office macros” with ID: 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b.
You can also set the rule to disabled mode. In that case, please use the following Powershell command:
Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions DisabledRestore Shortcuts Links using PowerShell Script
Update – Microsoft shared the various ways to restore the shortcuts. Microsoft has confirmed steps that customers can take to recreate start menu links for a significant subset of the affected applications that were deleted. Version 3.0 is now streamlined, so the script will perform all the actions, including running the MpRecoverTaskbar.exe.
- Download both AddShortcuts.ps1 and MpTaskBarRecover.exe.
- If you are using System Center Config Manager or Group Policy Object Editor, or third-party tools, then deploy both files and run the command “powershell -ep bypass -file .\AddShortcuts.ps1 -MpTaskBarRecoverUtilLocal” as Administrator.
- If you are using Intune or no management tool, deploy AddShortcuts.ps1 and run the command “powershell –ep bypass –file .\AddShortcuts.ps1 –MpTaskBarRecoverUtilDownload” as Administrator. This will automatically download MPTaskBarRecover.exe from the Microsoft download center onto the user’s machine and run the script. Detailed instructions on how to deploy the script using Microsoft Intune are here.
- The changes will come into effect after users log out and log in to their accounts.
- The MPRecoverTaskbar.exe can be run multiple times on end-user machines if necessary. If end-users are missing taskbar icons after completing this process, try running it a second time from %windir%\MPRecoverTaskbar.exe in the user context.
More details -> https://aka.ms/asrfprecovery
Restoring shortcuts is another issue now with many organizations, there are some ideas shared on Twitter (Paul Bendall -@paulbendall). The next problem is how to recover the deleted shortcuts. More details about restoring shortcuts Restoring shortcuts for Microsoft SI MO497128 deleting shortcuts in start menu.
There is another script to create the shortcuts, but I don’t how efficient this would be – PowerShell is fun 🙂 Recreate Start Menu shortcuts.
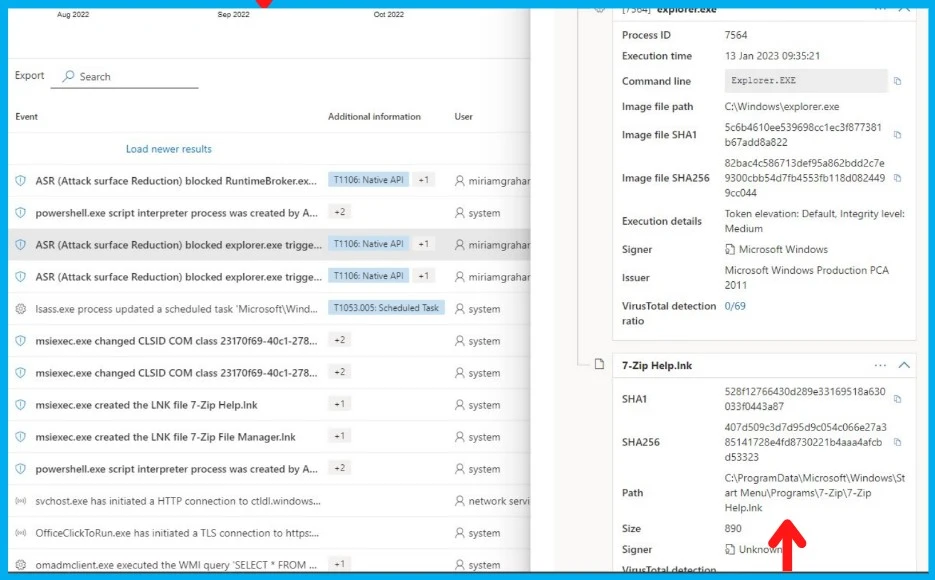
M365 Defender can tell us the files impacted per machine by looking at the timeline logs (they’ll be marked with T1204.002 Malicious File). Not sure whether the .LNK files are recoverable from quarantine.
- MpCmdRun -Restore -ListAll
NOTE – There is another update on Twitter that the above option to restore is not working. No luck on our end so far. Not all deletions are making it to our “Advanced Hunting” console. The deleted shortcuts don’t end up in local quarantine either.
Query to Find Impacted Shortcut Links
Let’s also share the query to find the impacted shortcut links. This is shared by Marius Sandbu on Twitter. Try the following query to analyze the impact on your environment.
DeviceEvents | where ActionType == "AsrOfficeMacroWin32ApiCallsBlocked" and Timestamp >= datetime("2023-01-13 00:00:00Z") | order by Timestamp
| where FileName contains ".lnk"
| summarize count() by FileName, DeviceNameRoot Cause
Root cause: During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to an affected security intelligence build(s) 1.381.2134.0, 1.381.2140.0, 1.381.2152, and 1.381.2163.0. These detections resulted in identifying certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of IT experience (calculation done in 2021). He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.

Any way to script the shortcuts back after the rule is disabled? New users on a PC seem file but returning ones the problem exists.
You are very fast sir !
Thank you
Dear Anoop,
You are gem for information, appreciate everything you share.
Thanks!
$TargetFile = “C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.exe”
$ShortcutFile = “C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Outlook.lnk”
$WScriptShell = New-Object -ComObject WScript.Shell
$Shortcut = $WScriptShell.CreateShortcut($ShortcutFile)
$Shortcut.TargetPath = $TargetFile
$Shortcut.Save()
##### You can change paths for your apps.
I’m using this to re-add the icons to the desktop and Start Menu. Doesn’t help for the taskbar which from what I’m seeing isn’t easy. tech.nicolonsky.ch/intune-create-desktop-shortcut/
When does the problem appear–immediately on installation of the update, on use of Defender, or on a reboot following installation? Both my Win10 and Win11 machines have this update (1.381.2140.0), and I have *so far* noticed no problems…
As for now18:33 CET, I am still getting popups from Defender that runtimebroker.exe is blocked
Rule: Block Win32 API calls from Office macro
Items:
AppData\Roaming\Microsoft\Windows\Libraries\Pictures.library-ms
So even after the MS defender update, this is still going on.
powershell, credits to squeueue from Reddit.
worked for me, at least Office icons to return
$Programs = @{
‘Excel’ = ‘Excel.exe’
‘Word’ = ‘Winword.exe’
‘Outlook’ = ‘OUTLOOK.EXE’
‘Access’ =’MSACCESS.EXE’
‘Publisher’ = ‘MSPUB.EXE’
‘OneNote’ = ‘OneNote.exe’
‘PowerPoint’ = ‘powerpnt.exe’
}
foreach( $p in $Programs.Keys ){
$WShell = New-Object -comObject WScript.Shell
$Shortcut = $WShell.CreateShortcut(“C:\ProgramData\Microsoft\Windows\Start Menu\Programs\$p.lnk”)
$Shortcut.TargetPath = [string](Get-ItemProperty -Path “HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\$($programs.$p)”).'(default)’
$Shortcut.save()
}
From what I’ve seen, there is not log off all the .lnk files it deleted. I see it even ventured in ..\AppData\Roaming\Microsoft\Windows\Network Shortcuts and deleted the target.lnk files out of the Network Locations.
I wrote a simple ps script to scan a folder of shortcuts and if exe is on target machine, copy over shortcut (and make sure shortcut folder is preserved.. simple but could help others get out of this mess
#folder to scan shortcuts in
$scanPath = “#### path of folder containing working shortcuts”
$startmenuPath = “C:ProgramDataMicrosoftWindowsStart MenuPrograms”
$WScript = New-Object -ComObject WScript.Shell
#for each shortcuts file found
$links = Get-ChildItem -Recurse -Path “$($scanPath)*.lnk” | ForEach-Object {
$exePath = $WScript.CreateShortcut($_.FullName).TargetPath
#if target exe exists
if (Test-Path -Path $exePath){
write-host “have programe installed”
#get the proposed new sartmenu ile path
$menuPath = $($_.FullName).replace(“$($scanPath)”,”$($startmenuPath)”)
#if shortcuts folder path dosent exists create it
if (-not(Test-Path -Path (Split-Path -Path “$($menuPath)”))){
New-Item (Split-Path -Path “$($menuPath)”) -ItemType Directory
}
#if shortcuts dosent exists copy it
if (-not(Test-Path -Path “$($menuPath)”)){
Copy-Item $_.FullName -Destination (Split-Path -Path “$($menuPath)”)
}
}
}