In the post, You will see the details about the option that allows you to duplicate Intune RBAC roles. You can easily copy an existing role that will be helpful for MEM admin to create a custom Intune role that includes any permissions required for a specific job function.
Role-based access control (RBAC) helps Intune Admins to control who can perform various Intune tasks within your enterprise. There are seven (7) built-in Intune roles (RBAC roles). You can create custom Intune roles if none of the provided roles supports your scenario.
By assigning roles to your Intune users, you can limit what they can see and change. Each role has a set of permissions that determine what users with that role can access and change within your organization.
You can assign built-in roles to groups without further configuration. You can’t delete or edit the name, description, type, or permissions of a built-in role.
- Application Manager: Manages mobile and managed applications, can read device information, and view device configuration profiles.
- Endpoint Security Manager: Manages security and compliance features, such as security baselines, device compliance, conditional access, and Microsoft Defender for Endpoint.
- Help Desk Operator: Performs remote tasks on users and devices and can assign applications or policies to users or devices.
- Intune Role Administrator: Manages custom Intune roles and adds assignments for built-in Intune roles. It’s the only Intune role that can assign permissions to Administrators.
- Policy and Profile Manager: Manages compliance policy, configuration profiles, Apple enrollment, corporate device identifiers, and security baselines.
- Read Only Operator: Views user, device, enrollment, configuration, and application information. Can’t make changes to Intune.
- School Administrator: Manages Windows 10 devices in Intune for Education.
The addition of a duplicate profile feature for the settings catalog will also be helpful for MEM admin in terms of time savior and effort to create a profile from scratch.
- Intune Role-Based Administration RBAC In Endpoint Manager Portal
- Intune Read-Only Experience Learn to Create Read-Only Operators Roles Admin Access
- Create Custom Intune Helpdesk Operator Role
Intune RBAC Strategic options – Video
In this video, we will explain Intune RBAC Strategic options | Role-Based Access Controls | Scope Groups | Intune Objects | Roles.
Duplicate Intune RBAC Roles
You can duplicate both custom and built-in roles. Your account must have Global Administrator or Intune Service Administrator permissions in Azure AD to create, edit, or assign Intune roles. Here’s how you can duplicate Intune RBAC Roles –
- Login to the Endpoint Manager Admin Center https://endpoint.microsoft.com/
- Navigate to Tenant administration > Roles > All roles.
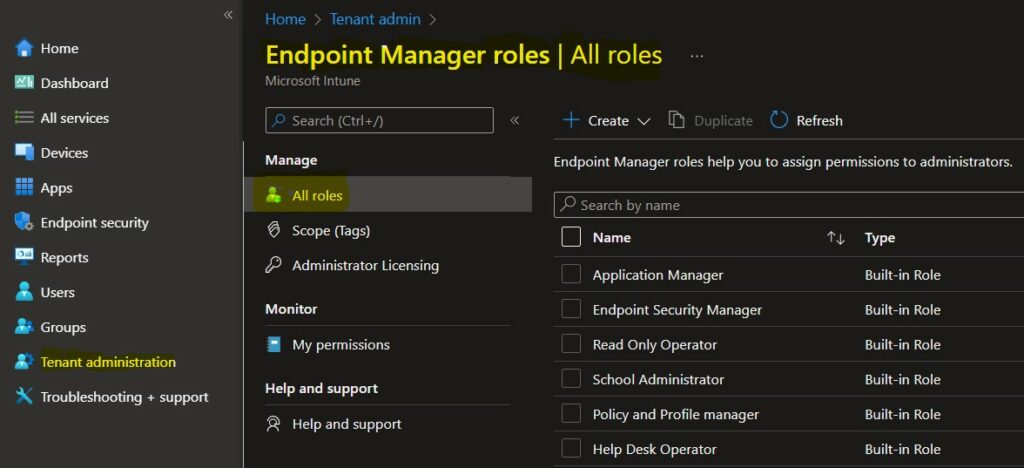
Select the checkbox for a role in the list, and choose Duplicate. For Example, I duplicated the Read Only Operator role and removed certain permissions that were not needed.
Right-click on the role and select the ellipses context menu (…) in the same row. Select Duplicate.
Note – You can’t delete or edit the name, description, type, or permissions of a built-in role. By duplicating existing built-in roles, You can create your roles with custom permissions.
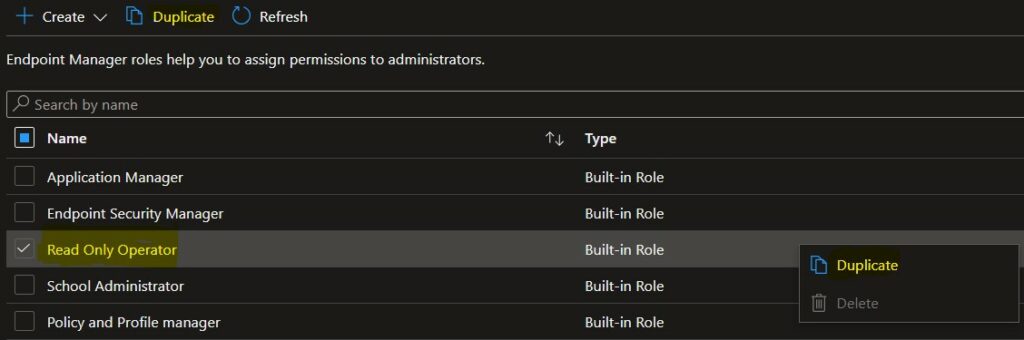
A Duplicate roles window and Enter the new Name and Description for the roles. Make sure to use a unique name.
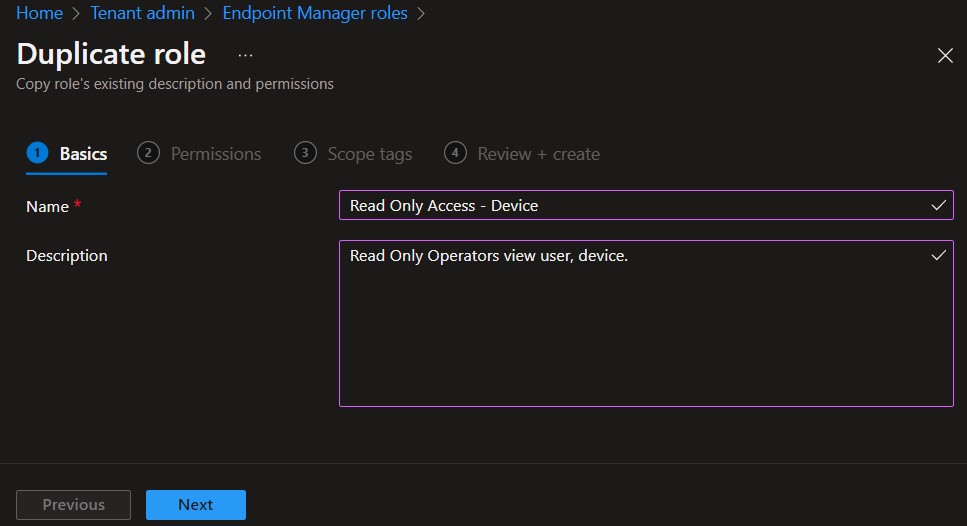
All the permissions and scope tags from the original role will already be selected. You can change the roles for the available category. The following permissions are available when creating custom roles.
On the Scope tags page, you can assign a tag to filter the profile to specific IT groups. Add scope tags and click Next.
On Review + create, review assigned roles. Click on Create.
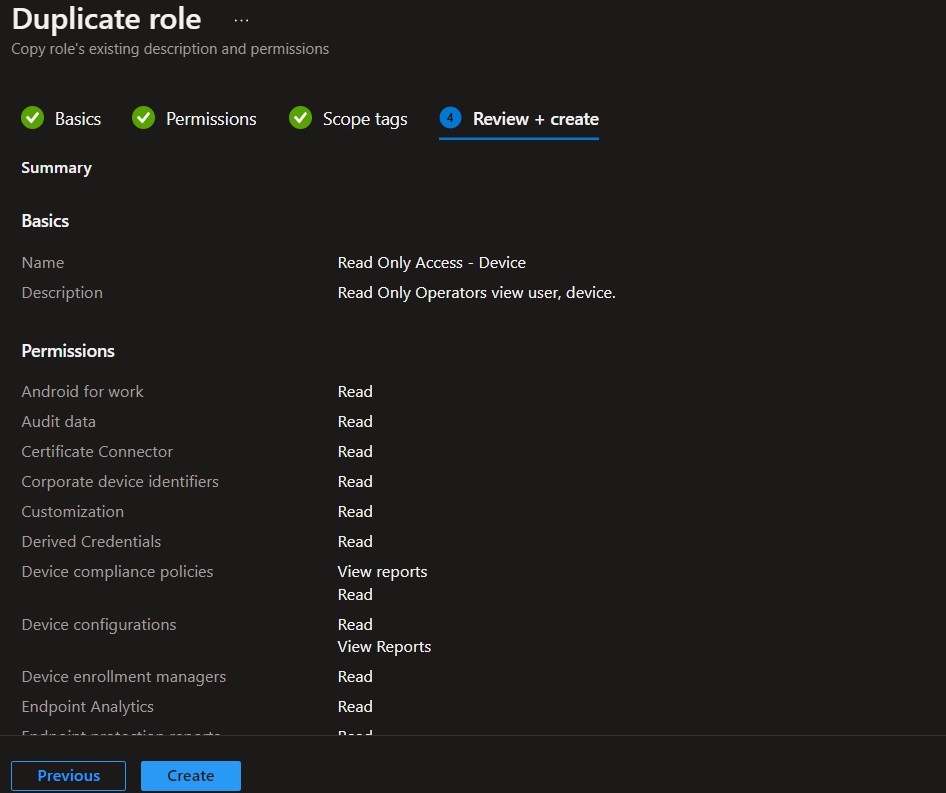
A notification will appear automatically in the top right-hand corner with a message. Here you can see, Read Only Access – Device successfully created.
Click the Refresh button at the top to quickly see the roles. You will be able to see the Custom Intune role duplicated in the roles list.
I’ve duplicated the Read Only Operator role, removed certain permissions that are not needed, and scoped to a group containing a list of members and assigned roles.
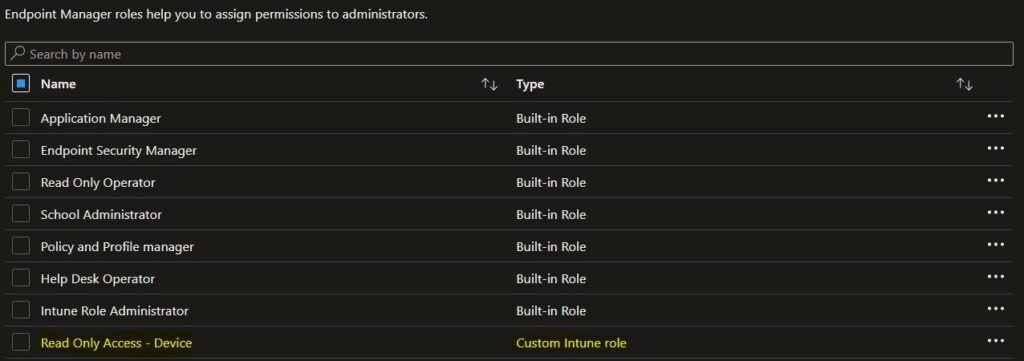
You can create a custom Intune role that includes any permissions required for a specific job function. After creating a custom role, you can assign it to any users that need those permissions.
Video Tutorial – Intune RBAC Roles
🎥Explore Video Guide From HTMD Free Intune Training to Create Intune Custom RBAC Role, and understand more about Custom role permissions.
Intune administrator Role permissions
Let’s check Intune administrator Role permissions from the following table.
| Actions | Description |
|---|---|
| microsoft.directory/bitlockerKeys/key/read | Read bitlocker metadata and key on devices |
| microsoft.directory/contacts/create | Create contacts |
| microsoft.directory/contacts/delete | Delete contacts |
| microsoft.directory/contacts/basic/update | Update basic properties on contacts |
| microsoft.directory/devices/create | Create devices (enroll in Azure AD) |
| microsoft.directory/devices/delete | Delete devices from Azure AD |
| microsoft.directory/devices/disable | Disable devices in Azure AD |
| microsoft.directory/devices/enable | Enable devices in Azure AD |
| microsoft.directory/devices/basic/update | Update basic properties on devices |
| microsoft.directory/devices/extensionAttributeSet1/update | Update the extensionAttribute1 to extensionAttribute5 properties on devices |
| microsoft.directory/devices/extensionAttributeSet2/update | Update the extensionAttribute6 to extensionAttribute10 properties on devices |
| microsoft.directory/devices/extensionAttributeSet3/update | Update the extensionAttribute11 to extensionAttribute15 properties on devices |
| microsoft.directory/devices/registeredOwners/update | Update registered owners of devices |
| microsoft.directory/devices/registeredUsers/update | Update registered users of devices |
| microsoft.directory/deviceManagementPolicies/standard/read | Read standard properties on device management application policies |
| microsoft.directory/deviceRegistrationPolicy/standard/read | Read standard properties on device registration policies |
| microsoft.directory/groups/hiddenMembers/read | Read hidden members of Security groups and Microsoft 365 groups, including role-assignable groups |
| microsoft.directory/groups.security/create | Create Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/delete | Delete Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/basic/update | Update basic properties on Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/classification/update | Update the classification property on Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/dynamicMembershipRule/update | Update the dynamic membership rule on Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/members/update | Update members of Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/owners/update | Update owners of Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/visibility/update | Update the visibility property on Security groups, excluding role-assignable groups |
| microsoft.directory/users/basic/update | Update basic properties on users |
| microsoft.directory/users/manager/update | Update manager for users |
| microsoft.directory/users/photo/update | Update photo of users |
| microsoft.azure.supportTickets/allEntities/allTasks | Create and manage Azure support tickets |
| microsoft.cloudPC/allEntities/allProperties/allTasks | Manage all aspects of Windows 365 |
| microsoft.intune/allEntities/allTasks | Manage all aspects of Microsoft Intune |
| microsoft.office365.supportTickets/allEntities/allTasks | Create and manage Microsoft 365 service requests |
| microsoft.office365.webPortal/allEntities/standard/read | Read basic properties on all resources in the Microsoft 365 admin center |
References:-
- Assigning administrator roles in Azure Active Directory
- Role-based access control (RBAC) for Microsoft Intune
