Hello everyone, we are back with another interesting topic today, i.e., Enforcing Screen Lock for Android Devices in Intune as per CIS Benchmarks in Intune. In this article, let’s learn CIS benchmarks and how they can be implemented in Intune to achieve data security and protection on devices enrolled to access your organizational data.
CIS stands for Center for Internet Security, a non-profit organization that aims to Security for IT systems and data. CIS creates CIS Benchmarks and CIS Controls that provide best practices for securing data and IT systems.
CIS creates benchmarks for Android, iOS, Windows, and MacOS. These benchmarks provide necessary recommendations for security controls to be implemented on different systems, which help to protect data. These benchmarks are prepared by reviewing real-time experience on data-based information by numerous subject matter experts.
Intune provides admins with a way to implement these recommendations. In this article, we will discuss one of CIS’s security recommendations, “Ensure ‘Screen Lock’ is set to ‘Enabled’ ” for Android devices. This is a Level 1 Profile, which provides Security benefits to the organization. We cannot implement all the benchmarks defined in the CIS document, so we create possible configurations in Intune.
- Enroll Android Devices to Android for Work in Intune
- Configure Enrolment Notifications For New Enrolled Android Devices In Intune
List of CIS Benchmarks Policies for Android Devices in Intune
In Intune, we can achieve the CIS benchmark recommendation of Screen Lock in 2 ways, using Device configuration profiles and using Compliance policies. Intune allows users to have either Numeric passcode or Alphanumeric passcode types. In this article, we will define Device configuration profiles.
In this post, we are going to give you 2 example policies of CIS Benchmarks for Android devices.
Device Configuration Profile for Android for Work Devices as per CIS Benchmarks
As Intune supports BYOD and Corporate devices (Fully managed?), we must create Device configuration profiles for both device enrolments. Let’s see how we can configure device profiles for Android for Work.
- Login to Microsoft Intune Admin Center https://intune.microsoft.com/
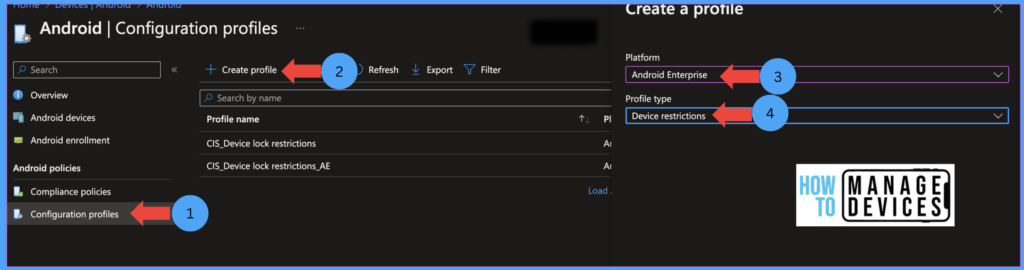
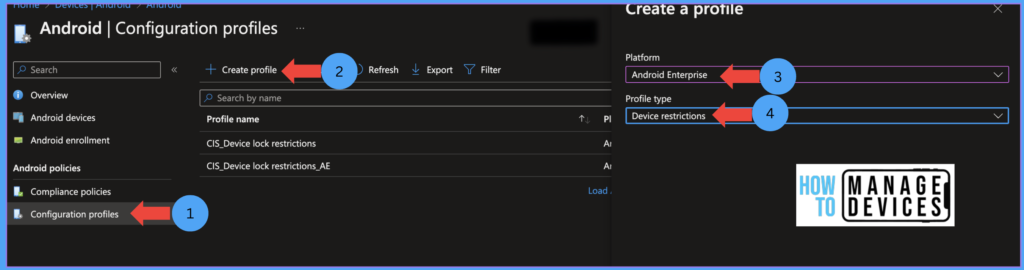
- Click on Devices > Android > Configuration Policies
- Click Create Profile > Select Android Enterprise
- Now select Device Restrictions under Personally-Owned Work Profile and click on Create.
Provide the Name and description of the restrictions and click on Next. Now click on the Password tab. Here we can see multiple options to set a device-level Password. These restrictions are applied to the personal side of the device. Let’s see what settings are available for Android devices inside the password section. Configure the settings according to your requirement.
Note! These settings work for all Android OS versions and manufacturers
- Maximum minutes of inactivity until screen locks
- Number of sign-in failures before wiping device
- Password expiration (days)
- Prevent reuse of previous passwords
- Fingerprint unlock
- Face unlock
- Iris unlock
- Smart Lock and other trust agents
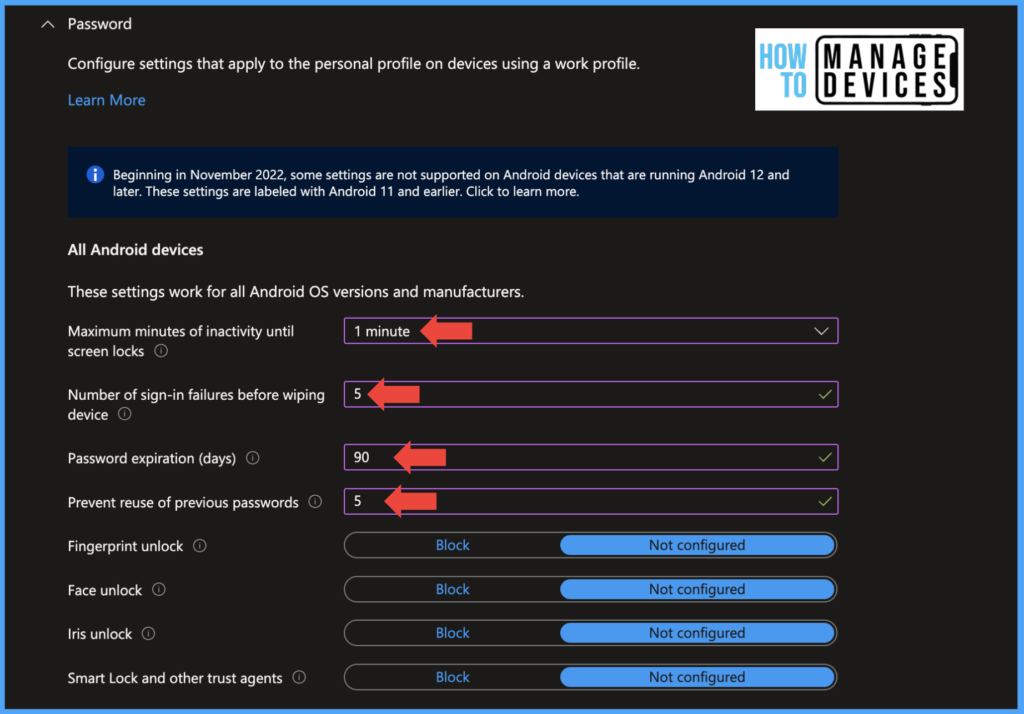
As per the CIS recommendation, a Screen lock for the device should be enabled, and the device should be locked immediately once the device goes to Sleep. To achieve this, we set Maximum minutes of inactivity until the screen locksuser’sMinute.
If the user’s device is lost or an unauthorized person gets hold of the device to wipe the work profile, set the value of the Number of sign-in failures before wiping the device to a numeric number between 4 to 11. If we set the value to 5, after five consecutive failures, the work profile will be removed, and corporate data on the device will be wiped.
To reset the device passcode after a certain number of days, set the value Password expiration (days). If you want to allow users to use Biometrics as Face Unlock, Finger Unlock, or Iris Unlock, leave them as Not Configured.
Note: From November 2022, Password settings for Android 11 devices and below OS and Android 12 above devices are segregated. This is due to Google deprecating APIs, which allow MDMs to manage the device password length and complexity via configuration and compliance policies.
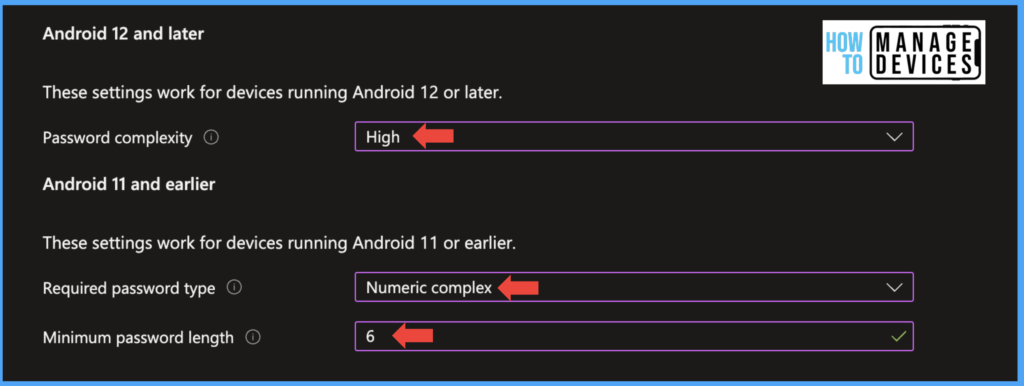
Now Under Android 12, we need to define the complexity of the Password. This forces the user to have a device passcode, either Numeric or Alphanumeric. The complexities are explained below
| Password Complexity | Type of Password Enforced |
|---|---|
| None | The device is not enforced with any kind of device lock |
| Low | A Simple Password like (000, 1234, 1111) or A Pattern to unlock devices are allowed |
| Medium | At least a four-digit PIN or At least four letters of the Alphabetic Password or At least four digit Alphanumeric Password |
| High | The numeric Passcode length allowed is 8 Alphanumeric or alphabetic password length allowed is 6 |
If you have devices that are running on Android 11 or below OS versions, we need to configure the password type and password length under Android 11 and the earlier section
Select the Required Password type to specify the type of Password required for devices to unlock and set the minimum length of Password for the device. It is always good to have lengthy passwords like 6 and above.
Now click Next, select the scope tags, if any, and click Next and assign the policy to the user group. Click next, Review the settings, and create the policy. Users in the assigned user group will be forced to set the device passcode.
Device Configuration Profile for Corporate Devices as per CIS Benchmarks
In the above, we have discussed how to force the Device passcode for personally owned Android for Work devices. In this section, let’s see how we can do the same for corporate-owned devices enrolled as COBO or COPE.
- Login to Microsoft Intune Admin Center https://intune.microsoft.com/
- Click on Devices > Android > Configuration Policies
- Click Create Profile > Select Android Enterprise
- Now select Device Restrictions under Fully managed, corporate dedicated, and corporate-owned work profile and click on Create
We need to configure passwords for the devices under the Device Password section. This will force the corporate devices to have passwords on the device. Always choose complex password configurations to follow CIS Benchmarks.
Select the Required password type, which will define the complexity of the Password, based on the complexity selected, a few additional settings will be enabled. Select Numeric complex or alphanumeric with Symbols for more complexity.
Now define the length of the Password in the Minimum password length, and set the value as six and above as per your requirement. Now define the expiry of the device passcode under the Number of days until the Password expires. We can define the value from 1-365 days. It is always better to change the Password every 90 days.
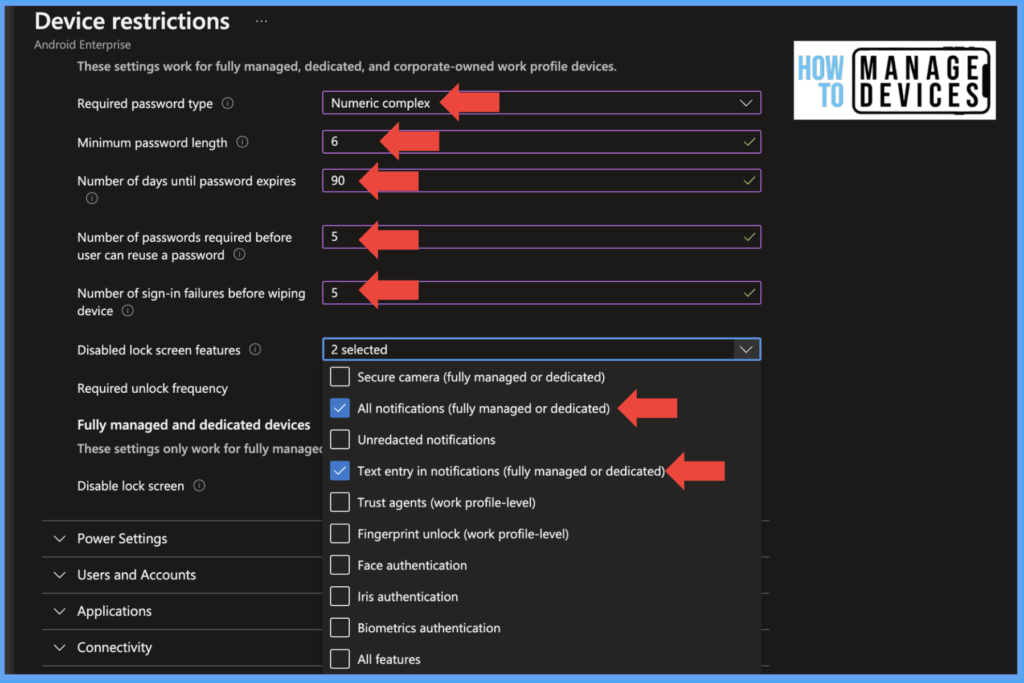
Now define how many times a user can reuse the current Password by setting a value in the Number of passwords required before the user can reuse a password. Intune supports a maximum of 24 times. For example, If we set the value as 5, the users cannot use the same Password until they change it five times.
Define after how many wrong Password attempts the device should be wiped under the Number of passwords required before the user can reuse a password the value should be 4 to 11. This setting will remove Work Profile in personal work profile devices, but on Corporate enrolled devices, it wipes the device data.
As per the CIS benchmarks, we need to block all notifications on the lock screen, which can only be achieved on Corporate devices. To block notifications, select All Notifications under Disable lock screen features. This feature is unavailable for devices enrolled under the Personal work profile method.
Now click Next, select the scope tags, if any, and click Next and assign the policy to the user group. Click next, Review the settings, and create the policy. Devices that are part of the assigned groups will be enforced with the above password restrictions.
Results of Screen Lock for Android Devices
Once the device is enrolled, the user is forced to set the device passcode as per the device configurations. If the user is already enrolled device and does not meet the criteria, the device will be forced to set the device passcode.
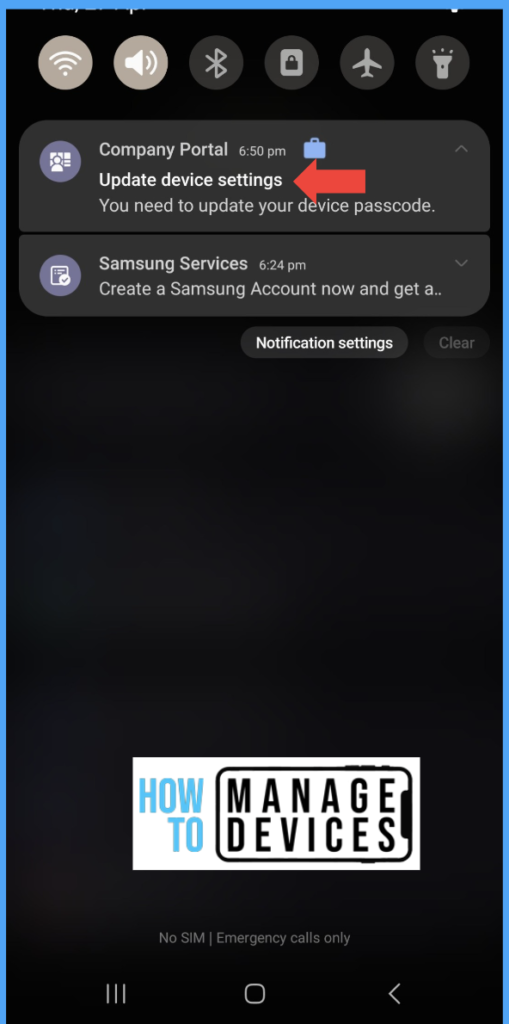
In the above screenshot, I enrolled the device in Intune, but do not have the required complexity for the passcode. Once Intue detects, the user will get a notification to update the device settings as per the above screenshot.
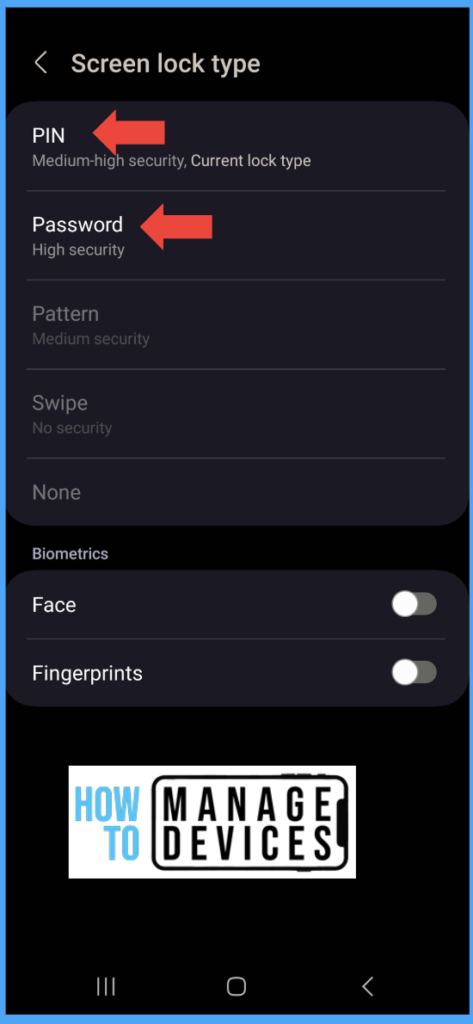
When the user clicks the notification, the user will navigate to the settings page to set the device passcode. We have set the passcode complexity to High, and the above device is running on Android 13. The user is forced to set either Passcode or Password for the device. The user will have to set 8 digit passcode. No other Screen lock is allowed, except for Biomertrics.
Conclusion
So we have learned how to enforce device lock as per CIS Benchmarks, using Device Restriction for Android for Work and Corporate device Enrolment methods. We can also enforce users to have the device passcode using Compliance Policies and Conditional Access policies. We will explain Compliance policies in a different article. Till then, Happy Learning.
Author
About Author – Narendra Kumar Malepati (Naren) has 11+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.

Hello,
Unfortunately for COBO devices, users will never get prompted to change their password once it is expired.
The issue is ongoing since two years now.