Hi, Today, I am glad to share with you about Microsoft Entra ID Logs now support Linkable Identifiers SID and UTI. Microsoft is introducing linkable identifiers within Entra tokens, now in preview. This feature aims to enhance identity security investigations and attack remediation.
Linkable identifiers, visible in customer logs, are a valuable tool for security analysts in evaluating and responding to identity-related threats. This cross-session tracking significantly enhances the ability to investigate and remediate identity-related attacks, leading to a more secure and transparent environment.
To enable more detailed security tracking, Microsoft utilizes two types of linkable identifiers: session-based, which links all tokens from a single authentication, and token-based, which tracks the activity of individual access and ID tokens.
In this blog post, I will provide a brief overview of the two types of linkable identifiers and how they relate to root authentication. By understanding these concepts, security analysts can more effectively identify and respond to threats, ultimately strengthening the overall security posture.

Table of Contents
Where to Find Linkable Identifiers?
Linkable identifiers are presently logged within Microsoft Entra sign-in, Exchange Online audit, and Microsoft Graph activity logs.
Linkable Identifiers : Session ID (SID) and Token -UTI
Linkable identifiers are essential for secure and reliable user identification and authentication. Microsoft uses two types of linkable identifiers to enhance security investigations. Session ID (SID)-based identifiers connect all authentication artifacts from a single root authentication.
Token-specific identifiers track actions performed by individual tokens, such as access or ID tokens, providing granular activity monitoring.
| Session ID (SID) | Token -UTI |
|---|---|
| Microsoft uses a Session ID (SID) claim to link authentication artifacts from a single root authentication | Microsoft Entra has an important security feature called the unique token identifier (UTI). The UTI is a unique GUID found in all Microsoft Entra tokens. |
| This SID, generated during interactive authentication, is included in primary refresh tokens (PRT), refresh tokens, session cookies, and subsequently, all access tokens derived from them. | It provides a unique identifier for each token or request. |
| This allows security analysts to trace all activity back to a single user session and filter by user or device. | For detailed token-level investigations, the Unique Token Identifier (UTI) provides granular tracking of suspicious tokens. |
| Security professionals use Session IDs (SIDs) to track user activity across Microsoft services by correlating sign-in logs with workload logs. | Each Access Token (AT) has a unique UTI, linked to its Session ID (SID), enabling analysts to investigate all tokens within a specific session |
| Filter results further by UserId or DeviceId, or with a token issued within a time frame of a specific session. | Use a UTI from Microsoft Entra sign-in logs to track actions linked to a specific access token by combining it with workload logs from services like Exchange Online or Microsoft Graph. |
| A key SID-based scenario is determining the current number of active sessions for a specified user or device. |
- Top 40 Microsoft Entra Interview Questions and Answers Modern Identity and Access Management Solution
- AI Agent Tool That Brings The Power Of Microsoft Graph And MS Entra
- How to use Entra Require App Protection Policy in Conditional Access for Secure Access
Linkable Identifiers in Key Log Services
Microsoft is logging linkable identifiers in key services like Entra sign-in logs, Exchange Online audit logs, and Microsoft Graph activity logs. This helps security analysts track user activity and respond to potential security threats more effectively.
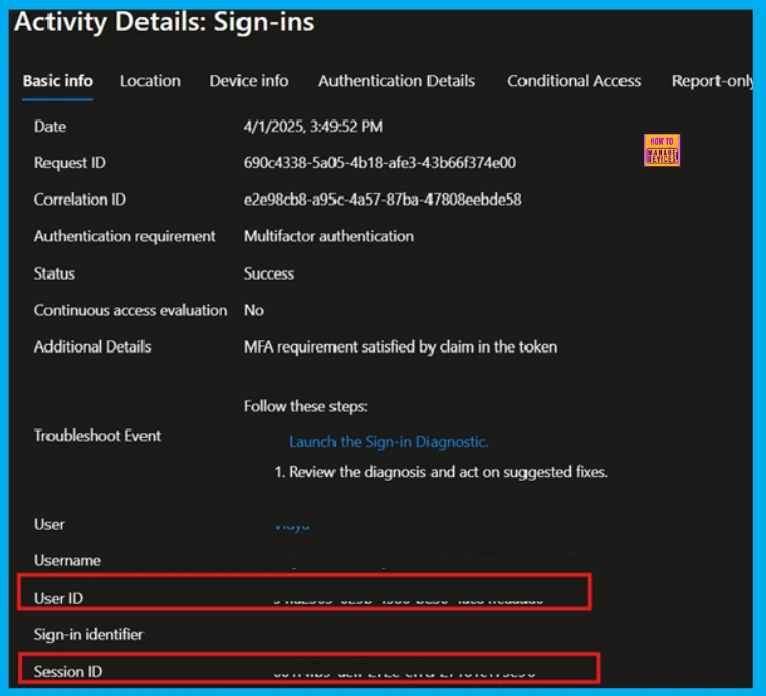
Microsoft Entra Sign-in Logs
To access sign-in logs in the Microsoft Entra admin center, log in with Reports Reader privileges or higher. Navigate to Identity > Monitoring & health > Sign-in logs. You can filter logs by time or user. Selecting a log entry displays details in the Basic Info tab, including User ID, Resource Tenant ID, Session ID, Unique Token Identifier, and Date. For registered or domain-joined devices, the Device ID is shown in the Devices tab.
- To track activities associated with a specific access token or session, manually correlate the User ID or Session ID from Microsoft Entra sign-in logs with relevant workload audit logs.
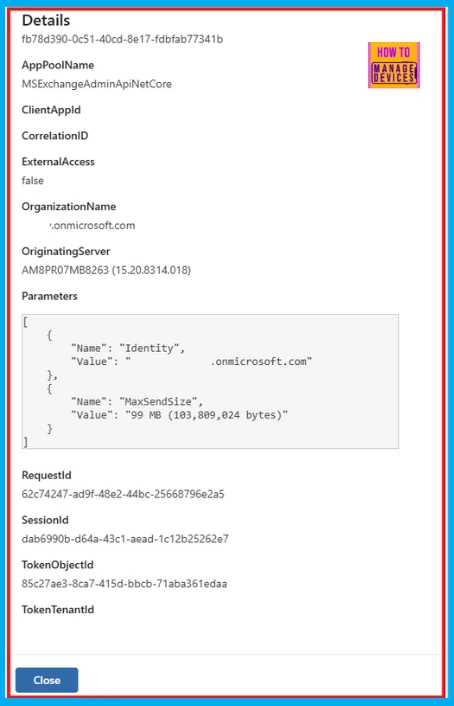
Microsoft Exchange Online Logs
Exchange Online audit logs provide valuable audit data for investigating user activities, and now include linkable identifiers from Microsoft Entra tokens for enhanced tracking. When investigating mailbox activities, such as updates, item moves, or deletions, linkable identifiers from Microsoft Entra sign-in logs are essential.
These identifiers allow you to perform targeted searches within Microsoft Purview Audit, both Standard and Premium versions, to achieve comprehensive tracking of user actions.
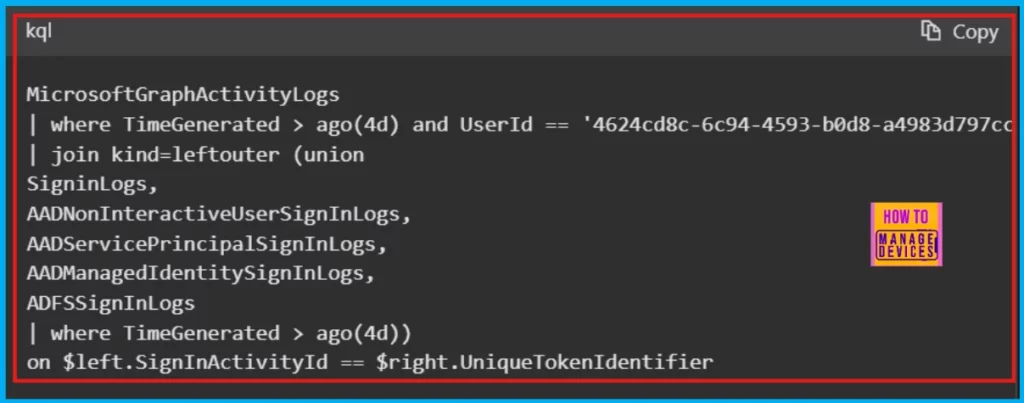
Microsoft Graph Activity Logs
Microsoft Graph activity logs provide an audit trail of all HTTP requests processed by the Microsoft Graph service for a tenant. These logs are stored in Log Analytics for in-depth analysis.
When Microsoft Graph activity logs are in a Log Analytics workspace, they enable detailed tracking using Kusto Query Language (KQL). Security analysts can examine mailbox access actions by linking identifiers from Microsoft Entra sign-in logs with the Graph activity logs. This helps analysts trace and analyze all user actions in Microsoft Graph.
Resources
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been a Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


