Here in his post, we will help you in understand how to Implement Password Complexity Policy Using Intune. We are going to use Configuration Profiles of Intune to implement this policy. Our main purpose here is to help you in acquiring knowledge of how to Implement Password Complexity Policy Using Intune.
Implement Password Complexity Policy refers to the process of defining and enforcing specific requirements for the passwords used by users within an organization. The goal is to enhance the security of user accounts and sensitive information by ensuring that passwords are strong, difficult to guess, and resistant to common hacking techniques.
By enforcing a Password Complexity Policy, organizations can reduce the likelihood of successful password-based attacks, such as brute force, dictionary attacks, and password guessing. This, in turn, helps protect sensitive data, prevent unauthorized access, and enhance overall cybersecurity.
It is essential to strike a balance between strong password requirements and user convenience to ensure that employees can still manage their passwords effectively. To accomplish this, we are using Intune’s Configuration Profiles.

A typical Password Complexity Policy may include several parameters to make an attack-prone password. Below mentioned are some of the parameters:
- Minimum Password Length: Set a minimum number of characters that a password must contain.
- Minimum Password Age: Set a maximum duration for which a password can be used before it needs to be changed.
- Character Types: Specify the types of characters that must be included in the password. Common categories include:
- Uppercase letters (A-Z)
- Lowercase letters (a-z)
- Numbers (0-9)
- Special characters (e.g., !, @, #, $, %, etc.)
- Configure Registry Processing Policy using Intune
- Prevent All Accessing Dangerous Websites Policy using Intune
Implement Password Complexity Policy using Intune
To Implement Password Complexity Policy Using Intune, follow the steps stated below:
- Sign in to the Intune Admin Center portal https://intune.microsoft.com/.
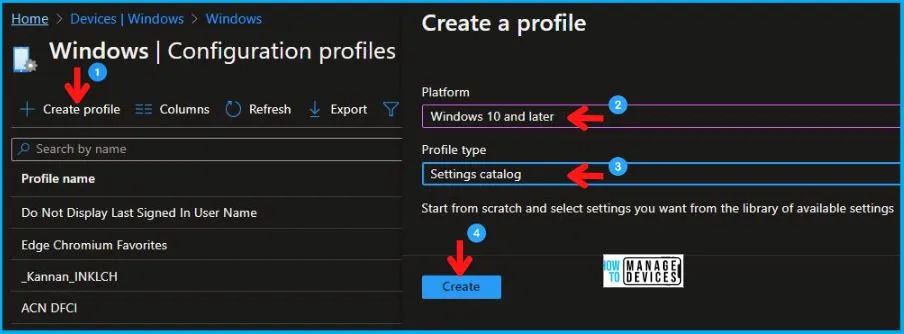
- Select Devices > Windows > Configuration profiles > Create a profile.
In Create Profile, I select Windows 10 and later in Platform and select Profile Type as Settings catalog. Click on Create button.
| Platform | Profile Type |
|---|---|
| Windows 10 and later | Settings Catalog |
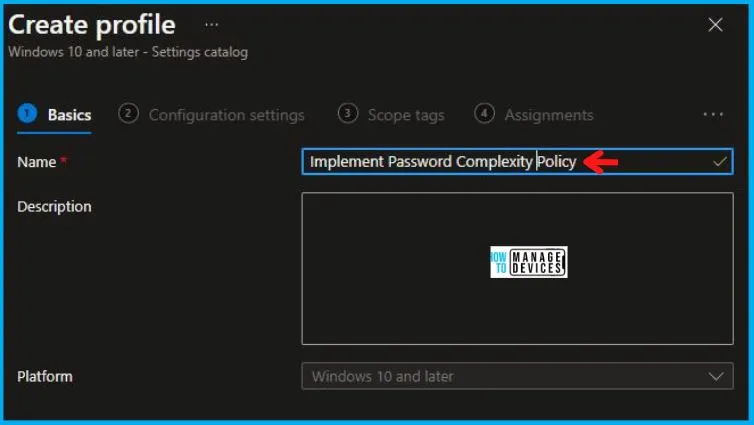
On the Basics tab pane, I provide a name for the policy as “Implement Password Complexity Polic.” Optionally, if you want, you can enter a description for the policy and then proceed by selecting “Next.
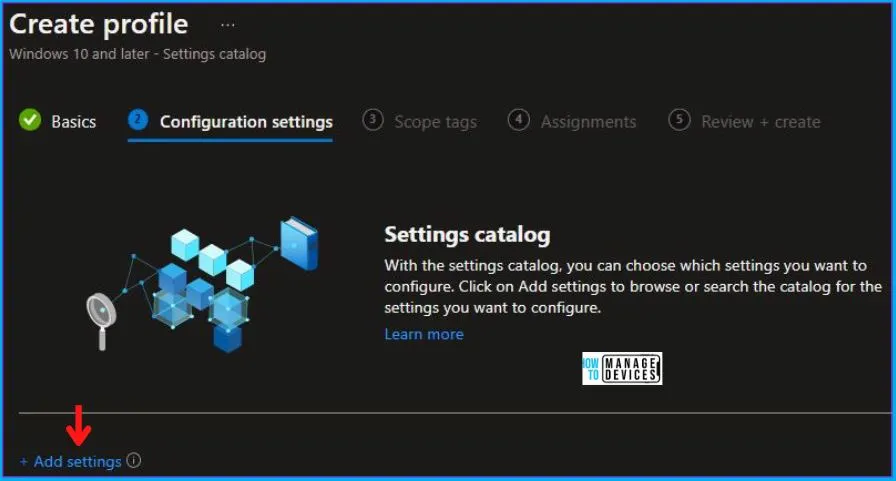
Now in Configuration Settings, click Add Settings to browse or search the catalog for the settings I want to configure.
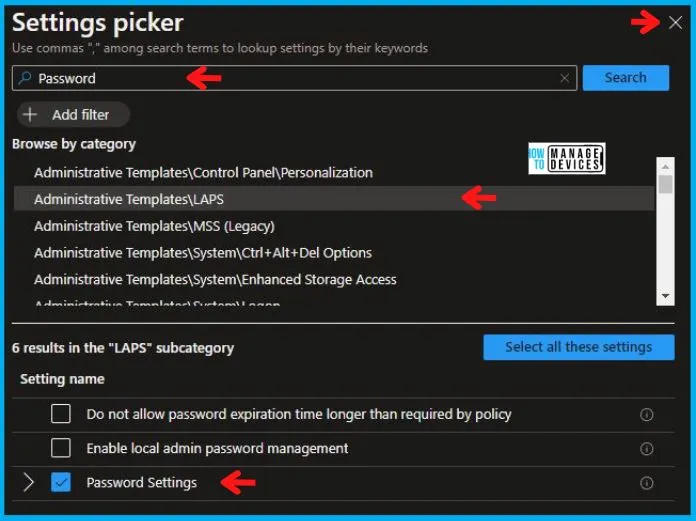
In the Settings Picker windows, I searched for the keyword Password, and among many, I found the category Administrative Templates\LAPS and selected this.
When I select that option as stated above, I see one sub-category, Password Settings. After selecting that, click the cross mark at the right-hand corner, as shown below.
Now, after enabling Password Settings in the Administrative Templates, you will see that three more sub-categories appear, as shown below.
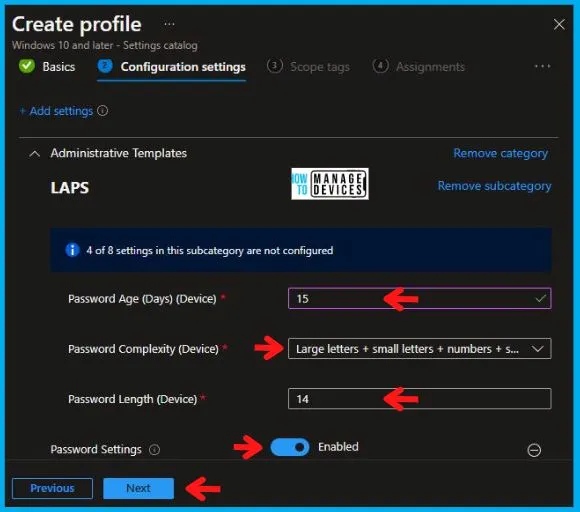
- Password Age (Days) (Device): You can enter the numeric value here, specifying the days when the password expires.
- Password Complexity (Device): Here, you can choose the complexity of the password by choosing characters. It will have the following options:
- Large letters
- Large letters + small letters
- Large letters + small letters + numbers
- Large letters + small letters + numbers + specials
- Password Length (Device): You can enter the numeric value here, specifying the minimum length of the password.
I am putting the details as mentioned below:
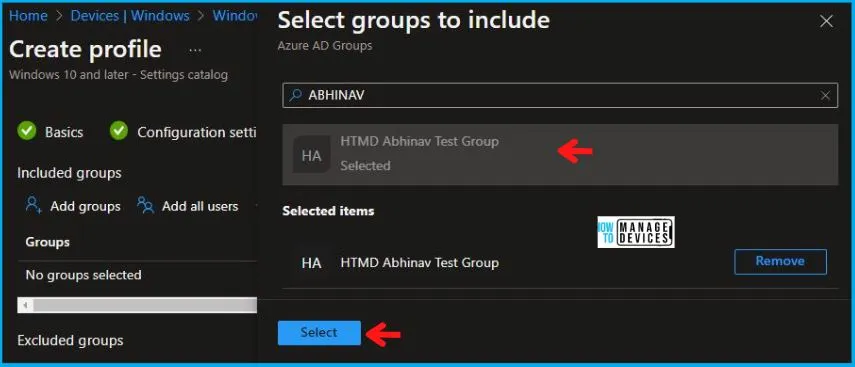
Using Scope tags, you can assign a tag to filter the profile to specific IT groups. One can add scope tags (if required) and click Next to continue. Now in Assignments, in Included Groups, you need to click on Add Groups, choose Select Groups to include one or more groups, and click Next to continue.
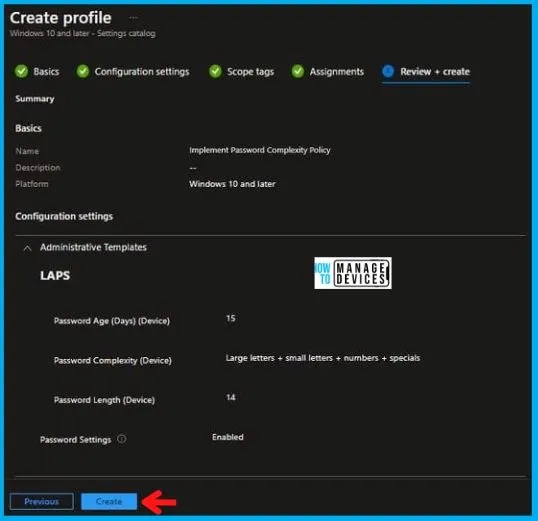
In the Review + Create tab, I review settings. After clicking on Create, changes are saved, and the profile is assigned.
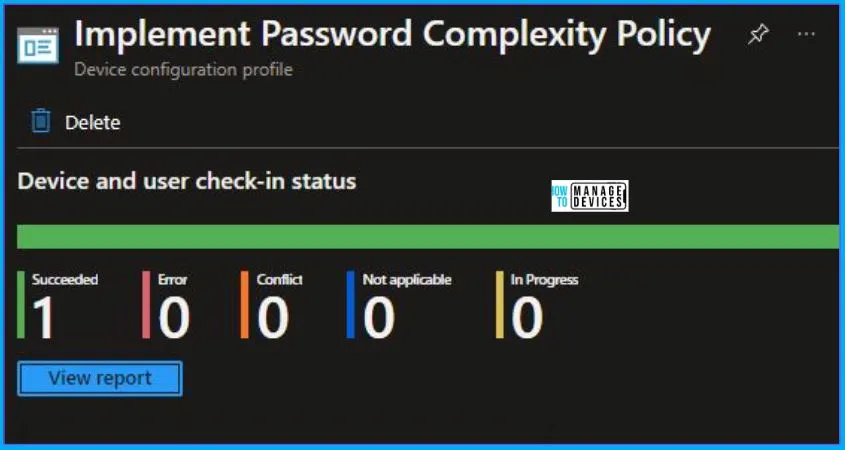
Upon successfully creating the “Implement Password Complexity Policy,” notification will appear in the top right-hand corner, confirming the action. You can also verify the policy’s existence by navigating to the Configuration Profiles list, where it will be prominently displayed.
Your groups will receive your profile settings when the devices check in with the Intune service. The Policy applies to the device.
Intune Report for Implement Password Complexity Policy
From Intune Portal, you can view the Intune settings catalog profile report, which provides an overview of device configuration policies and deployment status.
To track the assignment of the policy, you need to select the relevant policy from the Configuration Profiles list. By reviewing the device and user check-in status, you can determine if the policy has been successfully applied. If you require more detailed information, you can click on “View Report” to access additional insights.
Intune MDM Event Log
To verify the successful implementation of String or integer policies on Windows 10 or 11 devices through Intune, you can leverage event IDs 813 and 814. These event IDs provide valuable insights into the application status of the policy as well as the specific value assigned to the policy on those devices. In the case of this particular policy, the value is String and is linked to the event ID 814.
By analyzing these event IDs, you can gain a clear understanding of the policy’s application status and the corresponding value associated with it on the devices in question.
To confirm this, you can check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
MDM PolicyManager: Set policy string, Policy: (POL_AdmPwd), Area: (ADMX_AdmPwd), EnrollmentID requesting merge: (1A661A16-302C-46D4-81F0-AA73244850D8), Current User: (Device), String: (<enabled/><data id=”ELM_AdmPwd_PasswordAgeDays” value=”15″ /><data id=”ELM_AdmPwd_PasswordComplexity” value=”4″ /><data id=”ELM_AdmPwd_PasswordLength” value=”14″ />), Enrollment Type: (0x6), Scope: (0x0).
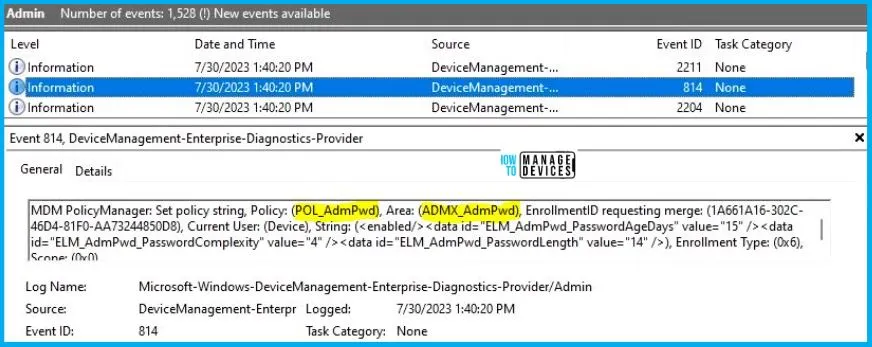
So when I open the above Event log, I found that the policy I have applied to the device is successfully implemented. By reviewing the log entry shown in the above image, the Event Viewer, I came across essential information, including the Area and Enrollment ID. These details play a significant role in identifying the corresponding registry path. To locate the specific information, please consult the table provided below:
| Area | Policy | String | Scoped | Event ID |
|---|---|---|---|---|
| ADMX_AdmPwd | POL_AdmPwd | Enabled | Device | 814 |
The details presented in the table above for the Implement Password Complexity Policy Using Intune can be employed to access the registry settings that hold the group policy configurations on a specific computer. To accomplish this, you can execute “REGEDIT.exe” on the target computer and navigate to the precise registry path where these settings are stored.
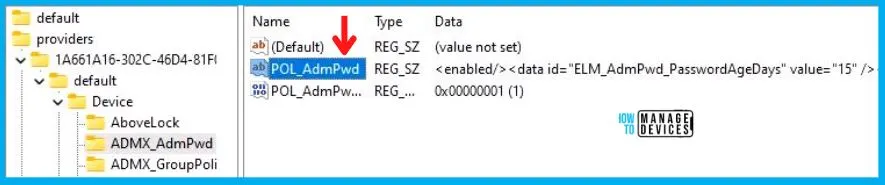
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\1A661A16-302C-46D4-81F0-AA73244850D8\default\Device\ADMX_AdmPwd
When you navigate to the above path in the Registry Editor, you will find the registry key with the name POL_AdmPwd. Also, when I navigated to the above path, I saw that the Registry Key is created, but there are three values associated with it which are as follows:
- <data id=”ELM_AdmPwd_PasswordAgeDays” value=”15″ />
- <data id=”ELM_AdmPwd_PasswordComplexity” value=”4″ />
- <data id=”ELM_AdmPwd_PasswordLength” value=”14″ />
And all of these have values associated with them as we set them previously while configuring in Intune Portal.
| Registry Name | Value |
|---|---|
| POL_AdmPwd | Enabled |
Author
Abhinav Rana is working as an SCCM Admin. He loves to help the community by sharing his knowledge. He is a B.Tech graduate in Information Technology.

Password protection is a better alternative
I don’t actually see minimum password age setting being implemented here at all.
Wait, ain’t this for LAPS admin password, not actual users’s login credentials… Why is this even relevant ?
I agree. This is LAPS and only for local Admin.