Today, I will discuss the Intune Win32 app log collection back-end process in this post. This Intune log collection feature was introduced in Feb 2019.
The Intune Win32 App Failure Log Collection is natively supported within Intune. The Intune Management Extension (IME/Win32 App) log collection feature is available only for Win32 apps with a failed instance.
If the Intune Win32 app is successfully installed on the end device, the status you can check from Intune > Devices > All Devices > Search for the device > Managed Apps. There would be no button “Collect log.”
The collect log button is only visible if the Win32 app reports a failure in Intune.
| Index |
|---|
| Collect Logs Intune Non-Win32 Apps Deployments |
| Procedure to Collect Log |
| Pre-requisites to Intune Win32 App Failure Log Collection |
| How Intune Collect Log works in the Backend |
| Intune Backend Post Call |
More Details about Intune Win32 App Deployment – Intune Management Extension (Win32 App) Level 3 Troubleshooting Guide Intune win32 App
Collect Logs Intune Non-Win32 Apps Deployments
Intune does not allow remote collection of client logs (Windows platform). However, Azure Log Analytics can achieve this. This process requires an active Azure subscription to collect Intune Managed Windows Client logs. You can read about it here.
With Windows 10 1903, Microsoft updated the DiagnosticLog CSP (v 1.4), which makes it possible to collect log files from Windows 10 via MDM (Microsoft documentation update for this CSP is yet to be made).
But as of now, this works in conjunction with Azure Blob Storage, so you would require a subscription to an Azure Storage Account. Oliver Kieselbach has already covered this in detail in his blog post here.
Procedure to Collect Log
The following is the process of collecting logs from a failed Intune Win32 App assignment. The collect log button won’t be enabled if the Win32 app installation is successful on the client device.
- Intune > Devices > All Devices > Search for the device > Managed Apps,
- Clicks on the Collect log button
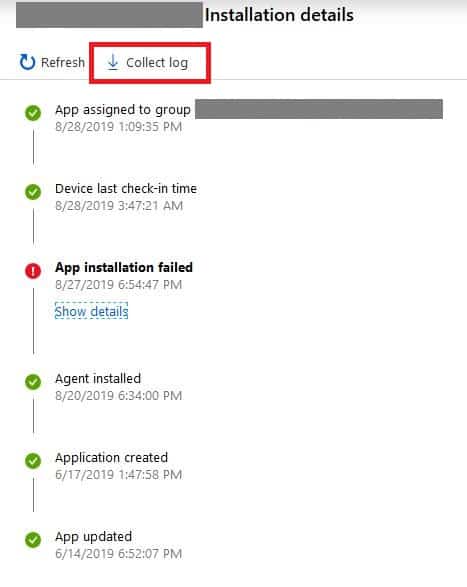
- Provide the folder path from where the log will be retrieved and click on OK
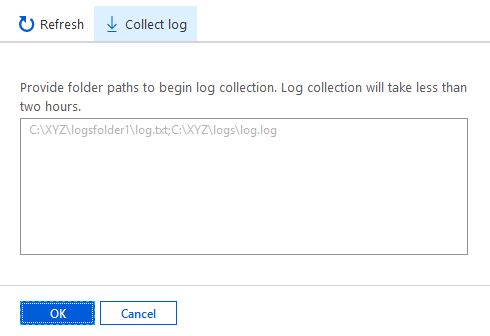
Pre-requisites to Intune Win32 App Failure Log Collection
- The user needs to be active on the end device for 2 hours.
- Exact <FileName>, along with full path details, must be provided to Intune to retrieve the log.
Once Intune has retrieved the logs, if the above criteria are met, you will see the download options in the same section.
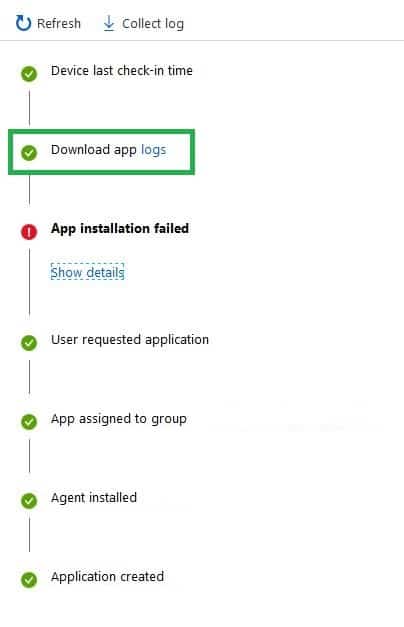
How Intune Collect Log works in the Backend
The following are Intune’s calls to Windows clients to complete the Intune Win32 App Failure Log Collection process.
Intune Portal
Admin specifies data collection (essentially the IME/Win32 app logs). Internally, Intune creates a mobileAppTroubleshootingEvents object via a Graph POST call.
RequestURL: https://graph.microsoft.com/beta/users('<User_GUID>')/mobileAppTroubleshootingEvents Request method: POST Version: HTTP/1.1 POST Data { "id": "<User_GUID>_<mdmDevice_GUID>_<App_GUID>" } Response HTTP/1.1 200/201 OK Content-Type: application/json Content-Length: # { "@odata.type": "#microsoft.graph.mobileAppTroubleshootingEvent", "id": "<User_GUID>_<mdmDevice_GUID>_<App_GUID>" }
NOTE! – The mobileAppTroubleshootingEvents objects are created in the Azure Storage Account of the Intune subscription. The object id is in the format <User_GUID>_<mdmDevice_GUID>_<App_GUID>
Intune Backend Post Call
With the mobileAppTroubleshootingEvents object id, Intune creates an appLogCollectionRequests event, also a POST call.
RequestURL: https://graph.microsoft.com/beta/users('<User_GUID>')/mobileAppTroubleshootingEvents('<ObjectID>')/appLogCollectionRequests Request method: POST Version: HTTP/1.1 POST Data { "customLogFolders": [ "Custom Log Folders value" ], "id": "<User_GUID>_<mdmDevice_GUID>_<App_GUID>" } Response HTTP/1.1 200/201 OK Content-Type: application/json Content-Length: # { "@odata.type": "#microsoft.graph.appLogCollectionRequest", "id": "<User_GUID>_<mdmDevice_GUID>_<App_GUID>", "status": "completed/pending/failed", "errorMessage": "Error Message value", "customLogFolders": [ "Custom Log Folders value" ], "completedDateTime": "" }
Intune Backend Tracking the Status
This results in a PUSH from Intune. Intune also generates a GET call simultaneously to track the status.
RequestURL: https://graph.microsoft.com/beta/users('User_GUID')/mobileAppTroubleshootingEvents('mobileAppTorubleshootingEvents_Obejct_ID')/appLogCollectionRequests/<appLogCollectionEvents_ID> Version: HTTP/1.1 Request method: GET Response HTTP/1.1 200/201 OK Content-Type: application/json Content-Length: # { "@odata.context": "https://graph.microsoft.com/beta/$metadata#users('User_GUID')/mobileAppTroubleshootingEvents('id')/appLogCollectionRequests/$entity", "id": "<User_GUID>_<mdmDevice_GUID>_<App_GUID>", "status": "pending", "errorMessage": "0", "customLogFolders": [ "Custom Log Folders value" ], "completedDateTime": "" }
Intune Management Extension (IME) agent Jason Post
Intune Management Extension (IME) agent at the client side processes the log collection (Intune Win32 App Failure Log Collection) using the JSON value as provided in the POST call (Log flow is copied below).
RequestURL: https://graph.microsoft.com/beta/users('User_GUID')/mobileAppTroubleshootingEvents('mobileAppTorubleshootingEvents_Obejct_ID')/appLogCollectionRequests/<appLogCollectionEvents_ID> Version: HTTP/1.1 Request method: GET Response HTTP/1.1 200/201 OK Content-Type: application/json Content-Length: # { "@odata.context": "https://graph.microsoft.com/beta/$metadata#users('User_GUID')/mobileAppTroubleshootingEvents('id')/appLogCollectionRequests/$entity", "id": "<User_GUID>_<mdmDevice_GUID>_<App_GUID>", "status": "pending", "errorMessage": "0", "customLogFolders": [ "Custom Log Folders value" ], "completedDateTime": "" }
IME log entries showing the log collection request as being processed
Using the JSON value as provided in the POST call above (Log flow is copied below).
[Policy] Get 1 policies for user <User_GUID> in session #
[AppLogUploadRequest] Start Processing log collection for device <Device SID> user <User_GUID>
[AppLogUploadRequest] Start processing AppLogUploadRequest for application <App_GUID>
[AppLogUploadRequest] IT Pro inputFolder/Files has 1 and distinctInputFolder/Files has 1 [currently only supports file path]
[AppLogUploadRequest] Enterring GetFullPathAndCheckTypeCoreLogicRegular for path C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\IntuneManagementExtension.log
[AppLogUploadRequest] File C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\IntuneManagementExtension.log of full file path C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\IntuneManagementExtension.log is valid.
[AppLogUploadRequest] File C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\_IntuneManagementExtension.log is valid to be collected.
[AppLogUploadRequest] zipFileName is C:\WINDOWS\TEMP\907fbd5e-b239-4541-9c69-e3fb04c7e149-5a38177e-c174-401b-a001-ad374c412c81-48027ae1-9129-4b43-ab3c-c0c0c8f41f1a-8eb1658a-61c4-4824-93a8-0b9a8c4c803d as accoundId-userId-deviceId-applicationId
[AppLogUploadRequest] Has 2 valid and distinct files to upload
[AppLogUploadRequest] Enterring ZipArchiveCoreLogic for fileC:\ProgramData\Microsoft\IntuneManagementExtension\Logs\IntuneManagementExtension.log
[AppLogUploadRequest] Catching IOException which could because of still being processed by another thread
[AppLogUploadRequest] Enterring ZipArchiveCoreLogic for file C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\_IntuneManagementExtension.log
[AppLogUploadRequest] 3 files added to the zip
[AppLogUploadRequest] Encrypted zip file size is 334 KB
[AppLogUploadRequest] C:\WINDOWS\TEMP\907fbd5e-b239-4541-9c69-e3fb04c7e149-5a38177e-c174-401b-a001-ad374c412c81-48027ae1-9129-4b43-ab3c-c0c0c8f41f1a-8eb1658a-61c4-4824-93a8-0b9a8c4c803dEncrypted.zip Status is : 5
Upload URL Details for IME Client
The PUSH from Intune also contains another important thing – the upload URL which the IME will use to upload the processed log.
[GenericPolicy] Sending results to service. session RequestPayload: [{"PolicyType":4,"ResultPayload":"{\"AccountId\":\"\",\"UserId\":\"\",\"DeviceId\":\"\",\"ApplicationId\":\"\",\"UploadLastRequstedTime\":\"\",\"UploadSASUrl\":\"https://lgmsvcsapeweu.blob.core.windows.net/####/####/637025025070097599.zip?sv=2018-03-28\\u0026sr=b\\u0026sig=Ro8O8BAxORBV9aKM5BA4ypk%2BsceG4cqJ8OZmyy%2BWO7c%3D\\u0026se=2019-08-27T16%3A35%3A07Z\\u0026sp=rw\",\"UploadPublicKey\":\"\\u003cRSAKeyValue\\u003e\\u003cModulus\\u003euc5ggCV2vFChjKM3dvInc7DTuPZLz1fbU3U31EYx56Gh8OD/Zf6FT/Czd2kVAuKnHhd03e\",\"UploadFolders\":\"C:\\\\ProgramData\\\\Microsoft\\\\IntuneManagementExtension\\\\Logs\\\\IntuneManagementExtension.log\",\"UploadState\":5,\"UploadCompletedTime\":\"\",\"UploadLastAttemptedTime\":\"\",\"UploadLastErrorCode\":0,\"ACK\":false}"}]
[GenericPolicy] Results are successfully sent. Intune Makes A Download URL – Collect Log
As IME completes the log upload process, the GET call reports the status as Success, and Intune generates another POST call to create the Download URL.
Now the Intune Win32 App Failure Log Collection process is completed. The Intune admin can download the Win32 App failure log from the Intune portal.
RequestURL: https://graph.microsoft.com/beta/users('User_GUID')/mobileAppTroubleshootingEvents('mobileAppTorubleshootingEvents_Obejct_ID')/appLogCollectionRequests/<appLogCollectionEvents_ID>/createDownloadUrl Version: HTTP/1.1 Request method: POST Response HTTP/1.1 200/201 OK Content-Type: application/json Content-Length: # { "value": { "@odata.type": "microsoft.graph.appLogCollectionDownloadDetails", "downloadUrl": "https://example.com/downloadUrl/", "decryptionKey": "Decryption Key value", "appLogDecryptionAlgorithm": "aes256" } }
Resources
- Intune Standalone – Win32 app management
- Convert MSI package to IntuneWin
- Intune Win32 App Troubleshooting Client Side Process Flow
- Intune Application Model Deployment Guide
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Joymalya Basu Roy is an experienced IT service professional with almost 5 years of experience working with Microsft Intune. He is currently working as a Senior Consultant – Architect with Atos India. He is an ex-MSFT, where he worked as a Premiere Support Engineer for Microsoft Intune. He was also associated with Wipro and TCS in the early stages of his career. He was awarded the Microsoft MVP award for Enterprise Mobility in 2021. You can find all his latest posts on his own blog site MDM Tech Space at https://joymalya.com

Hi Joymalya,
This is a great post. I wanted to understand that if there is a way to give custom permissions to users to be able to collect Win32 logs through Intune RBAC.