Loads of vulnerabilities have been reported for most versions of Java. JRE7 Update 11 is badly affected. Java vulnerabilities are also contained in prior versions of Java. More details are available here. Web browsers using any of these Java plug-ins are at high risk. Oracle (Java) agrees that unprivileged Java code can access restricted classes by leveraging a vulnerability in the Java Management Extensions (JMX) MBean components. More details about the vulnerability are available here.
As you know, most organizations are using Java plugins. The machines that are installed with Java plug are vulnerable. How do we tackle these vulnerabilities? It’s as simple as Keeping the Java version updated. As you know, we can’t directly deploy Java updates through WSUS or ConfigMgr. Even with SCUP, you must do many development tasks to deploy Java updates. In this scenario, SolarWinds Patch management software is very helpful. In a few minutes, you can download the required Java update, import it, and deploy it to the managed devices.
SolarWinds Patch manager can perform automatic patching of 3rd party applications other than Java. The SolarWinds patch Manager can update other 3rd party applications like Adobe, Apple, Dell, Google, HP, Microsoft, Mozilla, Opera, SolarWinds, Sun and Win zip. If you want to see where you’ll get the details of all the supported vendors, the best place is the ConfigMgr console (after the integration, you can see the 3rd Party Updates plug-in).
Solarwinds Patch Manager uses a native Windows update client to deploy and install these 3rd party application patches onto workstations. There is no need to install separate clients on workstations, so it basically uses an agentless architecture. So there is no overhead in installing and managing extra client software. SolarWinds Patch Manager provides key capabilities to enhance WSUS SCCM and general management experience, including enhanced command and controls, TCP/IP discovery, advanced inventory and reporting on desktops and servers.
In this post, I’ll try to explain 8 simple steps you need to follow to keep your Java plugin updated. Again, you don’t need to spend hours editing or modifying the Java update by creating prerequisite rules and finding the proper command lines. All are readily available if you install or publish them via Solarwinds Patch Manager. It’s an awesome tool. This post basically guides you in selecting your product and downloading the content, importing it, publishing it, Approving the updates, deploying it to the client, and then checking the reports.
I’m not going to cover the installation and configuration of SolarWinds Patch Manager in this post. If you would like to know more details about installation and configuration, you can refer to another post, “How to Install and Configure SolarWinds Patch Manager.”
Table of Contents
Step to Tackle Java Vulnerabilities with SolarWinds Patch Manager
1. You can download the Patch Manager from here. After installation, configuration, and the first sync, you’ll see the screen capture below (in my case, I’ve selected only Sun Java products for the update, which is why you can see only Java in my console).
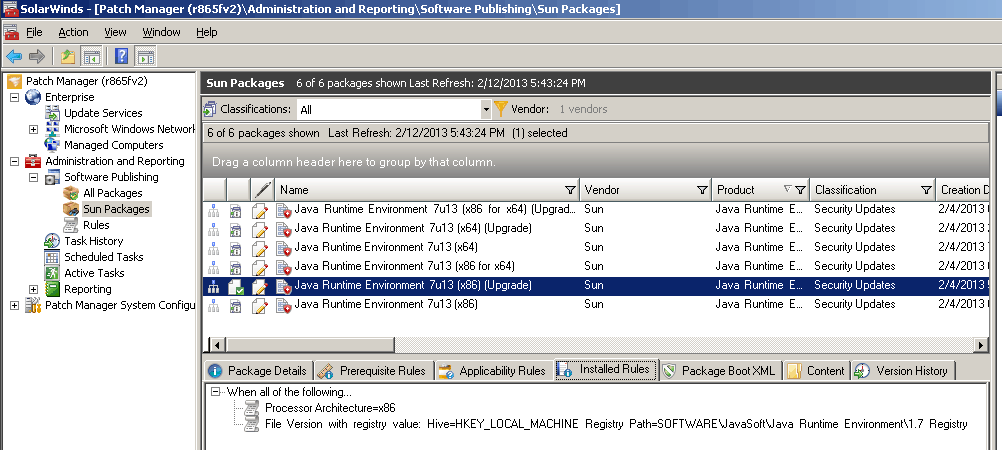
- How to Install Configure Integrate SolarWinds Patch Manager
- Advantages of Using SolarWinds System Center Extension Pack
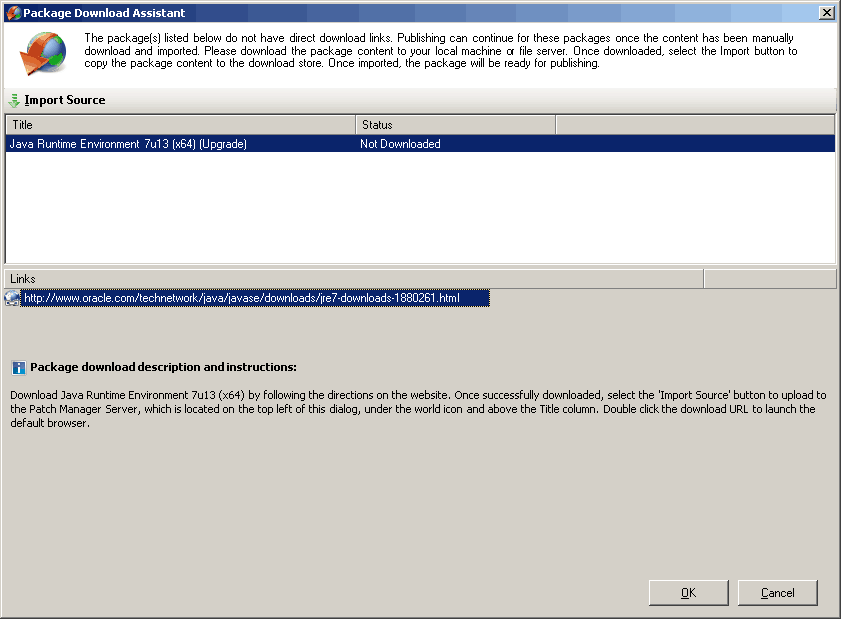
2. Right-click on any updates you want to deploy and select download content. The package Download Assistance wizard will pop up, helping you download the content from the Oracle Java Website. At the bottom, you can see the link to the vendor site.
Click on that link to download the package, and then click on the Import option (at the top of the screen) to import the Java Update Source to the patch manager. Note: Check the STATUS; in the following picture, it says It’s Not Downloaded.
| Title | Status |
|---|---|
| Java Runtime Environment 7u13 | Not Downloaded |
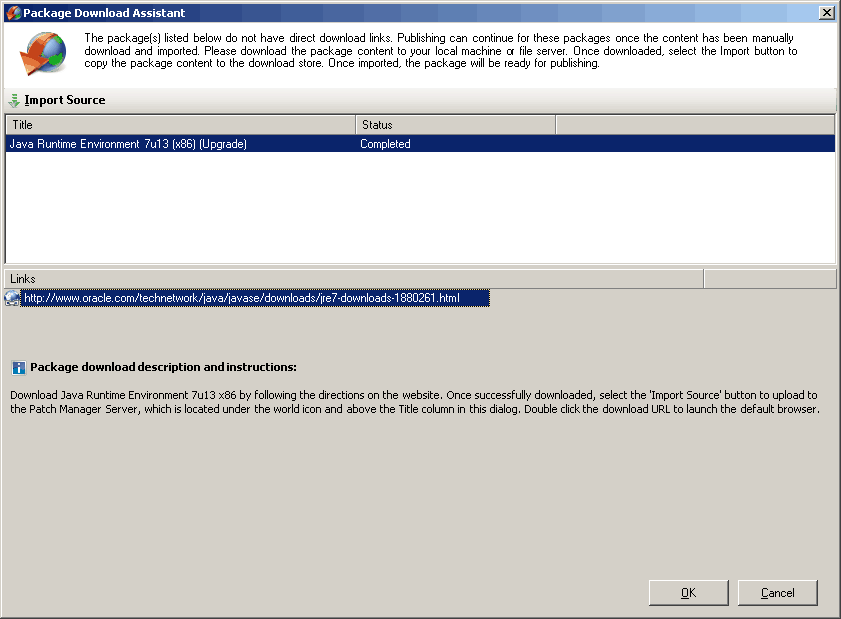
3. I downloaded the Java update from the Oracle Java site and clicked on the IMPORT SOURCE button to import the source. Once it’s imported successfully, the package Download Assistant will show the STATUS as COMPLETED!! So, we are almost done with the update deployment. Isn’t it awesome?
4. We downloaded the Sun Java package content and imported the Java Update content to SolarWinds Patch Manager. Look at what the SolarWinds Patch Manager did automatically in the background to prepare the Java update for deployment.
To get more details about the configurations done in the background, right-click on the update and select EDIT. It created all the details, such as the patch’s criticality, patch classification, reboot behavior, support URL, etc. The most important and very useful point here is that we can still edit this information. It’s NOT in read-only format. Wow, great!!
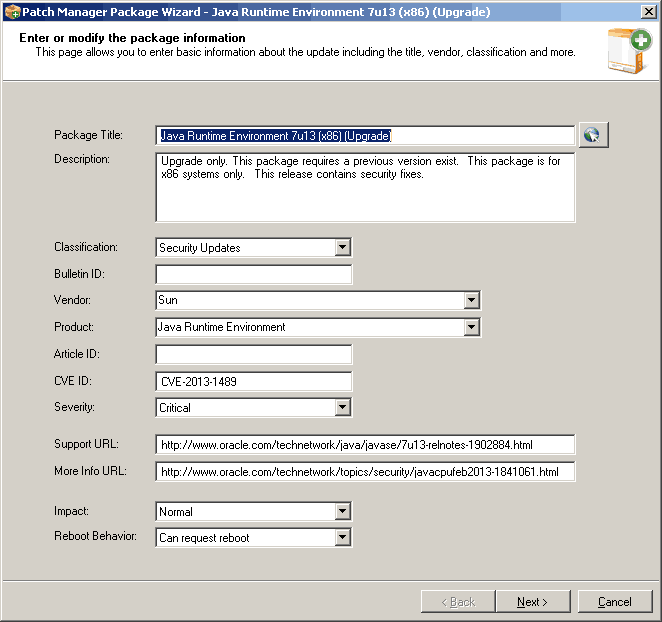
5. If you click NEXT on the above wizard, you will see more useful info. This wizard contains the Command Line, Reboot Codes, Package name and Download URL, Prerequisite rules, and Installed rules. All these options are editable, so you can change them according to your organization.
The command line populated in my case was “/s “JAVAUPDATE=0 AgreeToLicense=YES”
6. The last step is to right-click on the Java Update and Publish to WSUS. Once published successfully, we can deploy the Java package to the managed machines/devices.
7. Once the update is published, you’ve approved the updates you want to deploy. Once approved, you can deploy this update to the client systems using “Update Management.” This update management will help you deploy updates to the client. The main, I would say, CORE part of this update deployment is Package Boot, which works in tandem with Update Management.
SolarWinds Patch Manager’s Package Boot is core and very useful while deploying 3rd patches to managed machines. Look at the stuff it’s capable of performing. Before applying the update, it can stop the Java services, terminate the iexplore.exe, terminate the locked files etc. All of these will be helpful to get a good success rate in the deployment. This is one of the advantages of using SolarWinds Patch Manager for 3rd patching rather than using SCUP and struggling to get a good success rate.
8. Finally, the SolarWinds patch manager provides out-of-the-box reports to enrich reporting capability. In-depth reports are also available within the SolarWinds Reporting Console; this will help troubleshoot in case of failures. You can see that this product shows us “almost” real-time deployment progress (whether the server can establish a WMI connection, download the updates, start the installation, etc.).
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here – HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP from 2015 onwards for consecutive 10 years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His main focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career etc…
Are you familiar with creating custom packages with Solarwinds Patch Manager- Package Wizard? If yes, do you have any examples for it?
Thanks