Non-Human Identities and Agent Identities Gain Access Package Support with Entra Identity Governance for AI Agents! Microsoft Entra Identity Governance has introduced full support for Access Packages for Service Principals and Agent Identities.
It makes a significant expansion in how organizations can automate and manage access for non-human identities. This update, announced during the recent MSIgnite event, brings long-awaited capabilities to Entitlement Management, enabling secure and scalable governance for application and workload identities.
At Microsoft Ignite 2025, Microsoft introduced a major upgrade to its Entra Agentic AI. Instead of depending on older Copilot tools that only respond when someone types a prompt, the new Agentic AI can work independently. It can make decisions, take action, and complete tasks without needing constant direction from a user.
The new feature makes it easier for organisations to handle access requests, approvals, and reviews for API permissions. Earlier, these steps often needed manual work or complicated setups. By expanding Access Packages to include service principals and agent identities, not just users, Entra now gives a single, automated way to manage permissions for both human and non-human identities.

Table of Contents
Non-Human Identities and Agent Identities Gain Access Package Support with Entra Identity Governance for AI Agents
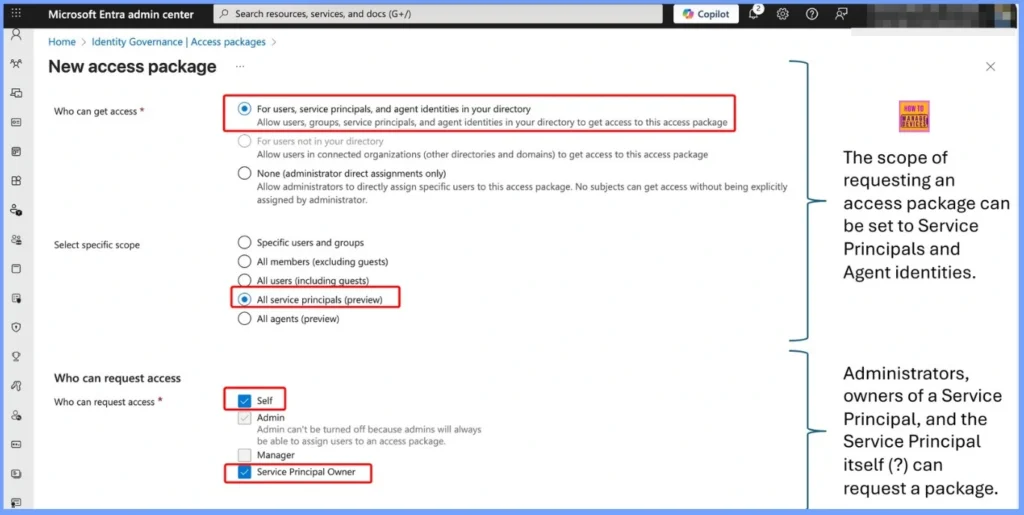
The scope for requesting an access package can now include both Service Principals and Agent Identities. This means administrators, the owners of a Service Principal, and in some cases the Service Principal itself can request an access package. This greatly expands how access can be managed and automated for non-human identities.
- Who can get Access
- For users, service principals and agent identities in your directory
- Setup Risk-Based Conditional Access for Entra Agents to Automatically Protect against Compromised Agents
- How to Manage Agents through Microsoft Entra Agent ID Interface for Security and Zero Trust Enforcement
- Best Guide to Invite B2B Guest Users to Entra ID using Intune
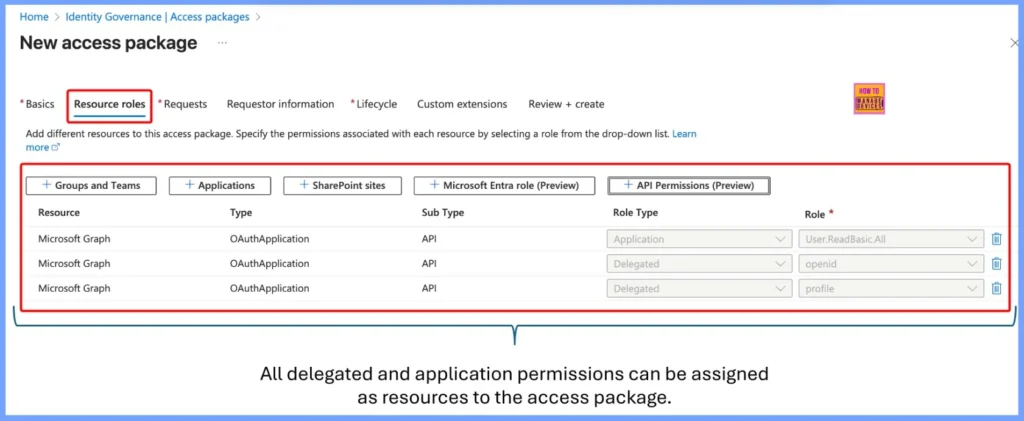
How Entra Access Packages Now Include Delegated and Application Permissions
All delegated and application permissions can now be added directly as resources inside an access package. This makes it easier for admins to manage API permissions in one place and give the right level of access to service principals, agent identities, and applications without manual setups.
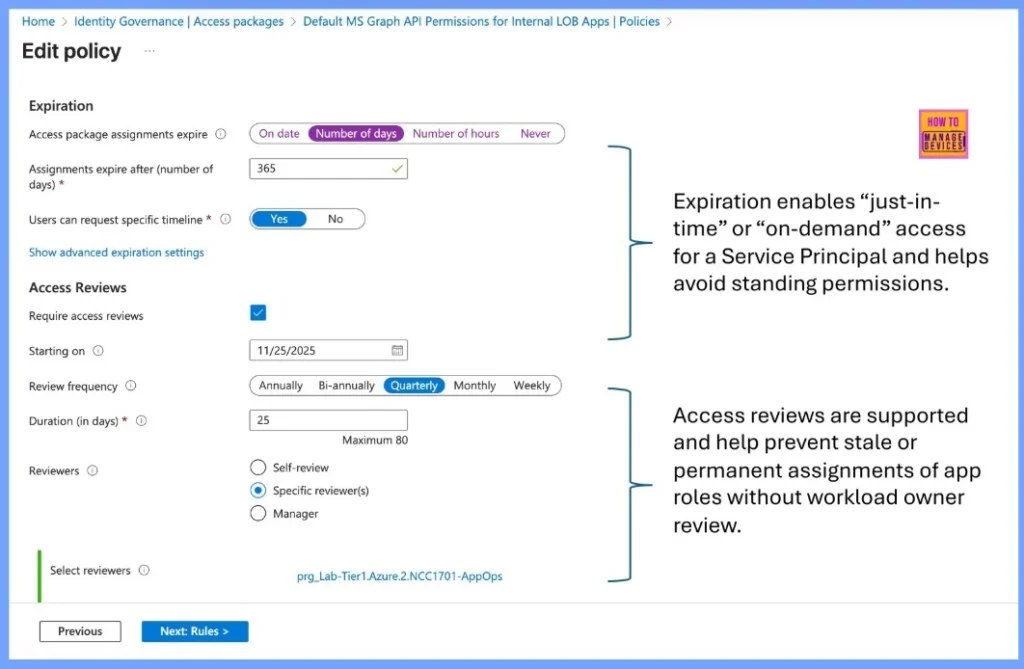
Just-in-Time Access and Access Reviews for Service Principals
Expiration policies allow Service Principals to receive “just-in-time” or on-demand access, minimizing the risks associated with standing permissions. In addition, access reviews are supported to ensure that app role assignments do not remain stale or permanent without evaluation by the workload owner, thereby maintaining secure and up-to-date access control.
- AI Agent Tool that Brings the Power of Microsoft Graph and MS Entra
- Best Guide to Invite B2B Guest Users to Entra ID using Intune
- Key Scenarios of MS Entra External Identity Deployment Architectures
- New External Authentication Methods in Microsoft Entra ID
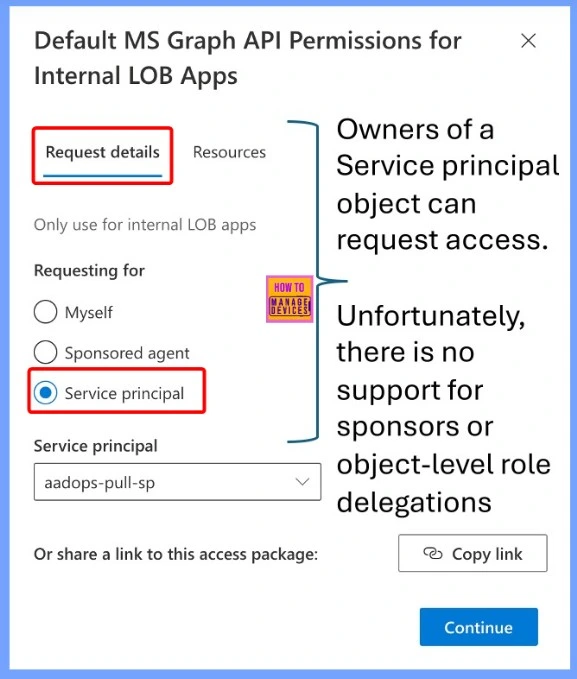
Access Requests for Service Principal Owners
Owners of a Service Principal object can request access directly. However, the system does not currently support sponsors or delegations at the object-level, limiting more granular or delegated access management.
| Feature | Supported | Details |
|---|---|---|
| Owner access requests | Yes | Owners can directly request access |
| Sponsor support | No | Sponsors cannot request access on behalf |
| Object-level role delegation | No | Role assignments cannot be delegated at object level |
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


