To block non Microsoft signed updates in Windows Update for Business using Intune, you can configure a policy that ensures only updates signed by Microsoft are accepted. This can be done by setting up a Windows Update policy in Intune.
And specifying that updates from other sources, such as third-party vendors, are not allowed. This way, devices managed by Intune will only install updates that are officially signed and verified by Microsoft, ensuring security and compliance.
This policy lets IT admins choose whether Windows Automatic Updates should accept updates signed by companies other than Microsoft. It’s helpful when using WSUS (Windows Server Update Services) to deliver updates for third-party software or internal apps.
The policy works for updates hosted on the company’s own WSUS server (not Microsoft’s servers) and ensures that only properly signed updates are installed. This makes managing third-party updates easier within the company.
Table of Contents
Block Non Microsoft Signed Update using Intune
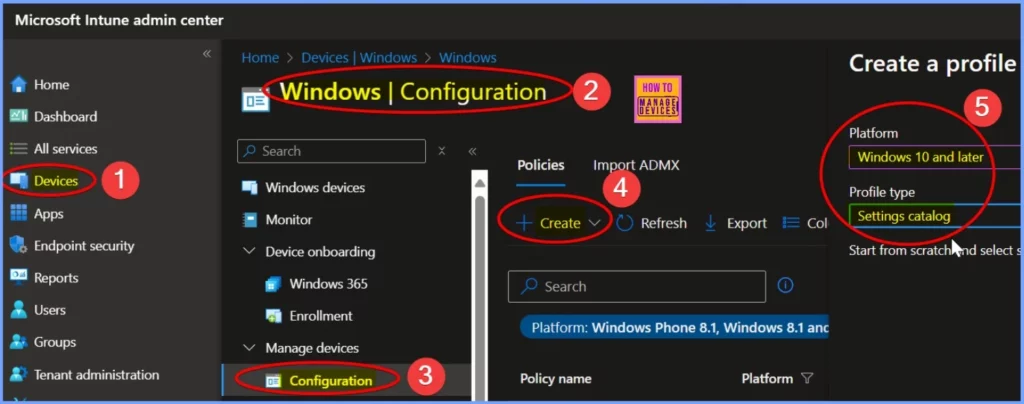
This post provides all the details on how to block non-Microsoft-signed updates in Windows Update for Business using Intune. Sign in to Microsoft Intune and Create a Configuration Profile. In Intune, go to Devices > Windows > Configuration Profiles. Click Create Profile.
- Choose Windows 10 and later as the platform and select Settings Catalog for the profile type.
- Windows Update for Business Patching using Intune | WUfB Patching Process
- Configure Windows Update for Business Reports | Intune WUfB Patching Reports
- Update Compliance Queries To Troubleshoot Intune WUfB Patch Deployment
- Configure Update Compliance Patch Management Reports Using Intune And Log Analytics
Allow Non Microsoft Signed Update
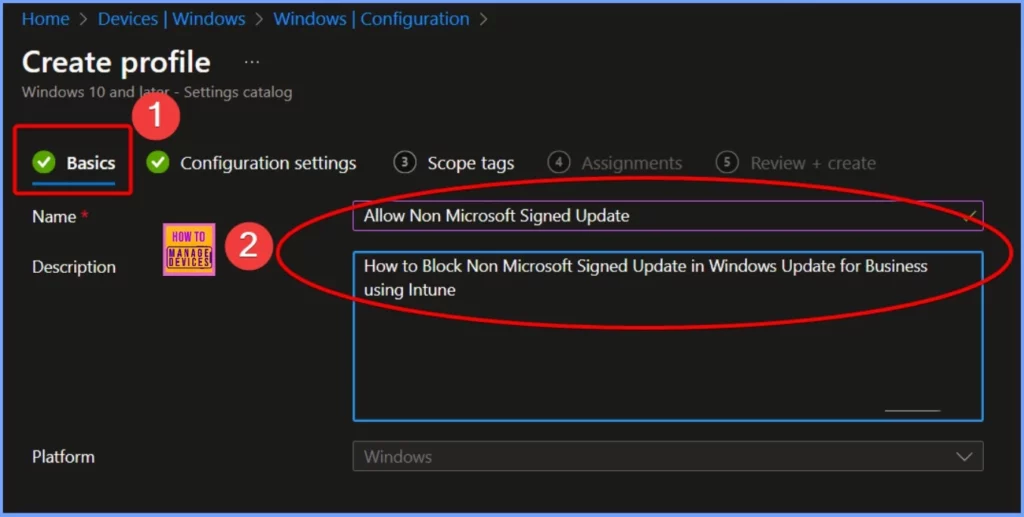
Name the policy Allow Non-Microsoft Signed Updates in the Basics settings, and set the description to Steps to Block Non-Microsoft Signed Updates in Windows Update for Business Using Intune.
Windows Update for Business
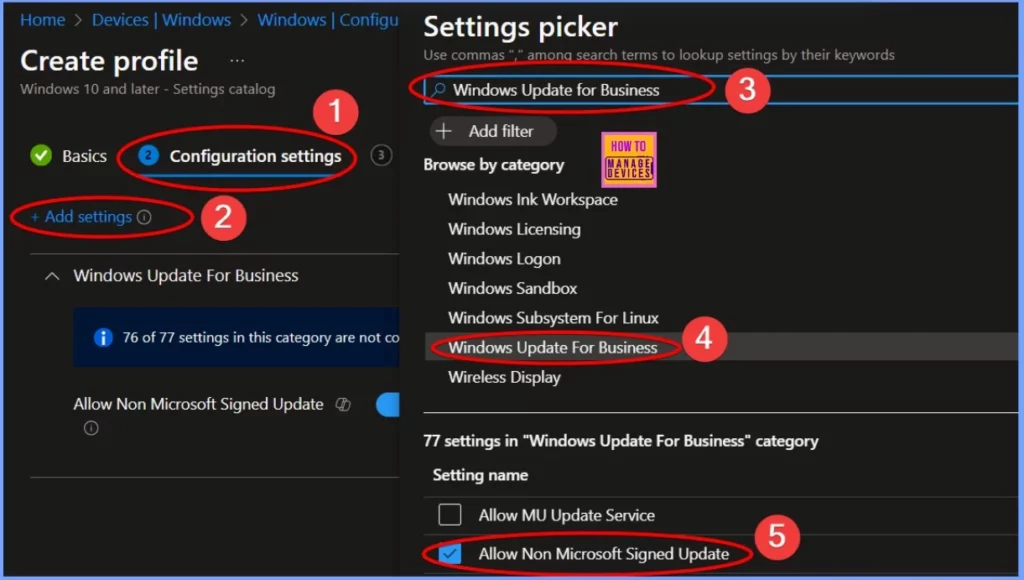
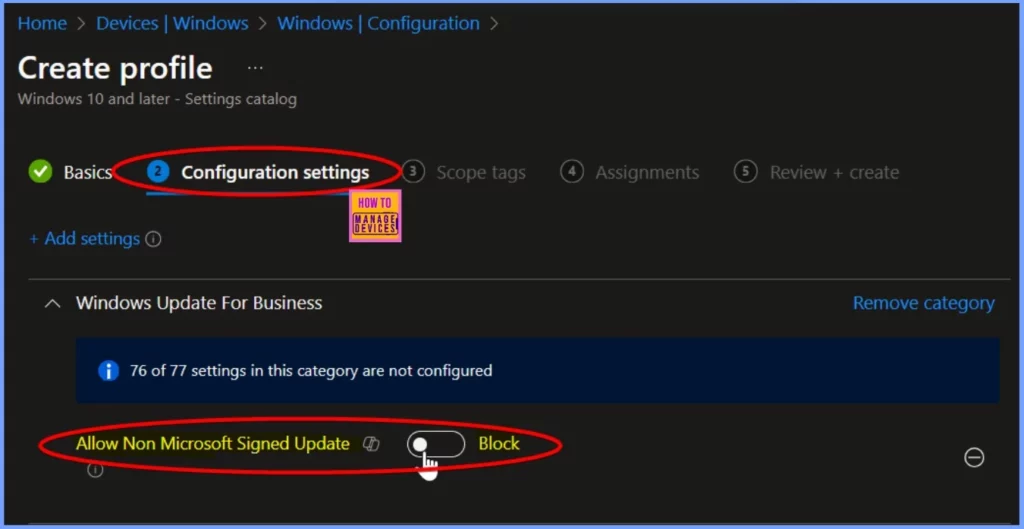
Go to the Configuration settings and click +Add settings. In the search bar, type Windows Update for Business and select it from the options. This category includes 77 settings related to Windows updates for business. To enable the policy Allow Non-Microsoft Signed Update, check the box next to the policy name in the screenshot below.
Block Non Microsoft Signed Update Policy
Allows the IT admin to manage whether Automatic Updates accepts updates signed by entities other than Microsoft when the update is found at the UpdateServiceUrl location. This policy supports using WSUS for 3rd party software and patch distribution.
Supported operations are Get and Replace. This policy is specific to desktop and local publishing via WSUS for 3rd party updates (binaries and updates not hosted on Microsoft Update) and allows IT to manage whether Automatic Updates accepts updates signed by entities other than Microsoft when the update is found on an intranet Microsoft update service location.
| Policy Name | Allow | Block |
|---|---|---|
| Allow Non Microsoft Signed Update | Toggle the pane to the Right side | Toggle the pane to the Left side |
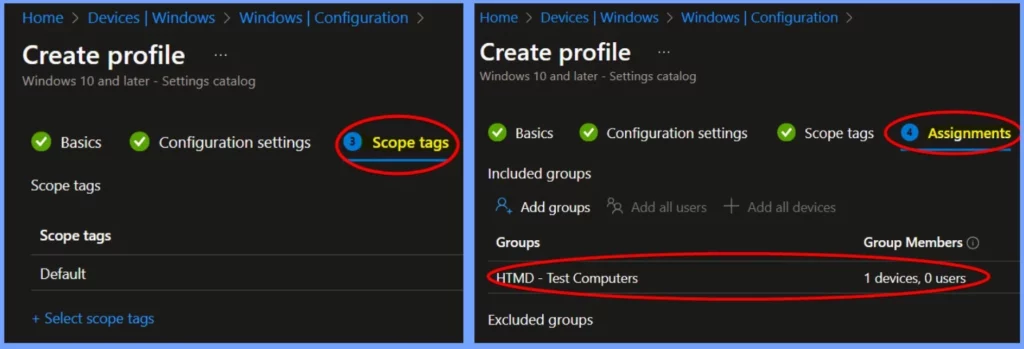
Assignments and Scope Tags
A Scope Tag in Intune is a way to group and manage devices, apps, or policies for specific teams, regions, or departments within your organisation. The Assignment Tab is where you assign a policy, app, or configuration to particular users or devices.
- Upgrade to Windows 11 using Intune Feature Update Deployment Policy
- Intune Monthly Patching Guide Software Update Patching Options with Intune WUfB
- Intune Vs. SCCM and WSUS Vs. WUfB Patching Method Differences
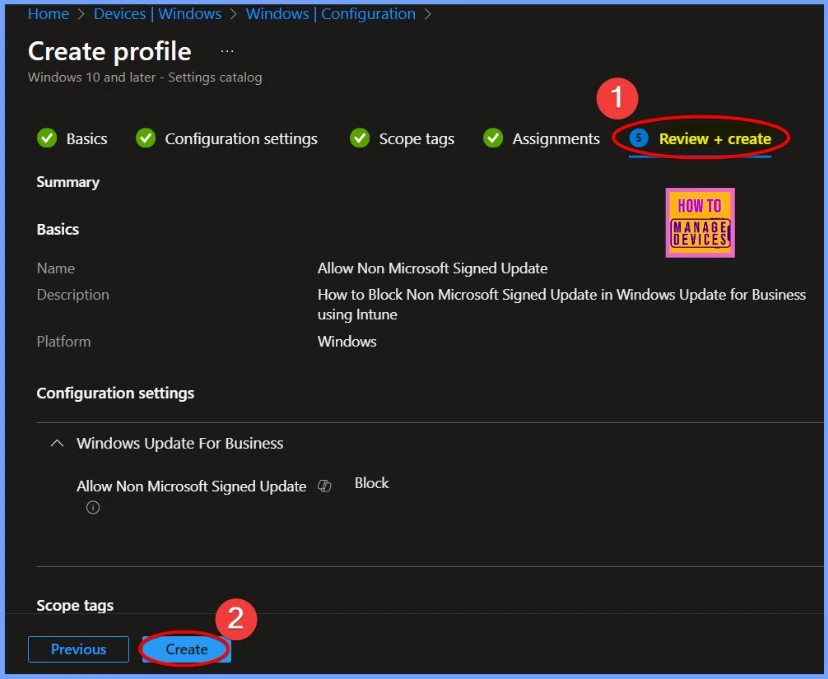
Review + Create
The Review + Create tab in Intune is the final step when configuring a policy, app, or setting. This section summarizes all the settings you have configured. Once satisfied with the review, click Create.
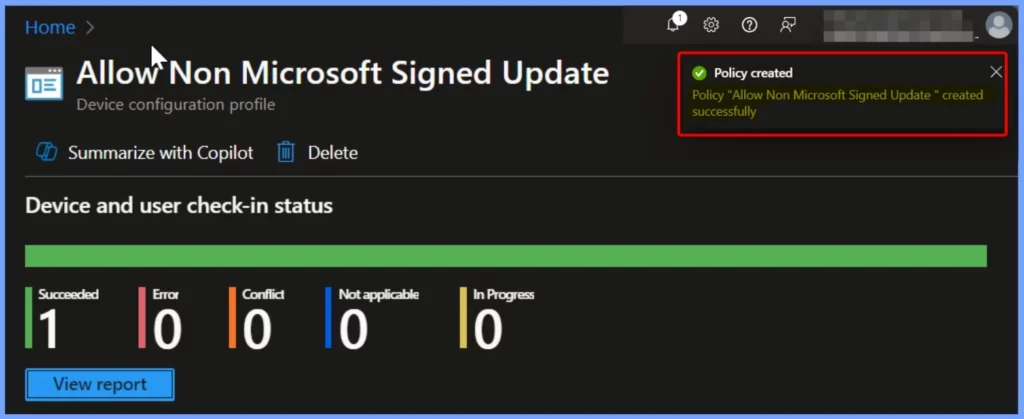
Policy Creation Status
The Allow Non-Microsoft Signed Update policy was created successfully. The screenshot below confirms this with a notification. In the Device and User Check-in Status, the number of succeeded devices is shown as one.
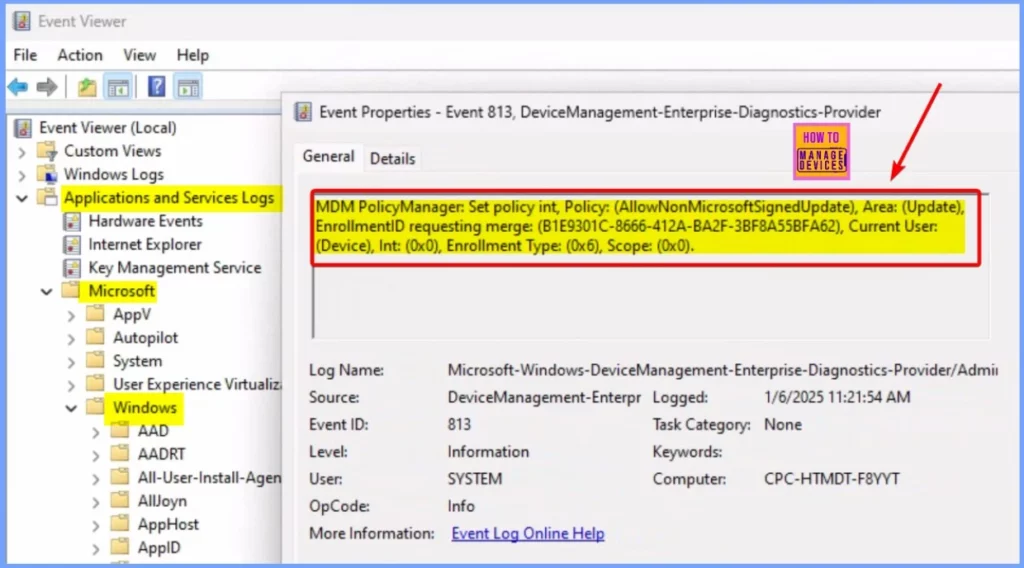
Client Side Verification
Event IDs 813 and 814 can confirm the successful application of string or integer policies, such as Block Non-Microsoft Signed Update, in Windows Update for Business. These can be checked on Windows 10 or 11 devices managed through Intune.
- To confirm this, you can check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
MDM PolicyManager: Set policy int, Policy: (AllowNonMicrosoftSignedUpdate), Area: (Update), EnrollmentID requesting merge: (B1E9301C-8666-412A-BA2F-3BF8A55BFA62), Current User: (Device), Int: (0x0), Enrollment Type: (0x6), Scope: (0x0).
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
