Firewall ports and proxy exception requirements are not something you can remove from your checklist while implementing any new infra component.
Co-management is not different over here. SCCM Co-management-related components from your on-prem infra must communicate with the cloud components.
Hence, Firewall ports are proxy exception planning & documentation is essential. We do not need to open any inbound ports to your on-premises network.
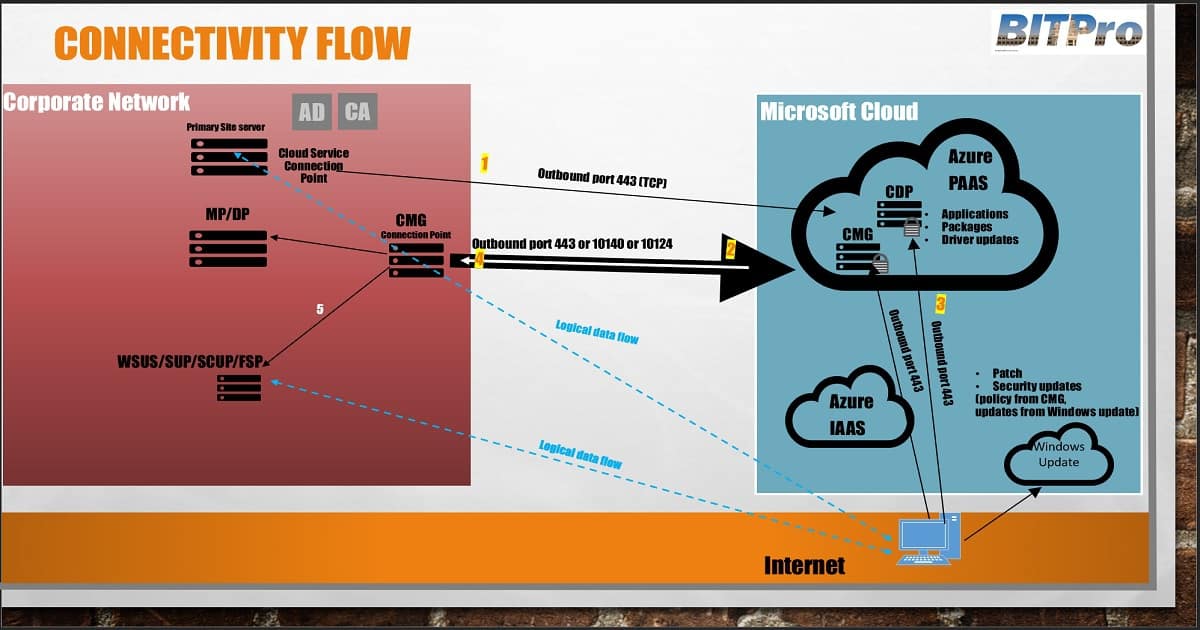
The SCCM service and CMG connection points initiate all communication with Azure and the CMG. These two site system roles must be able to create outbound connections to the Microsoft cloud.
Table of Contents
Firewall Ports Required for Co-Management, CMG, and CDP
The service connection point connects to Azure over HTTPS port 443, and the CMG connection point connects to the CMG in Azure over TCP-TLS or HTTPS. The service connection point opens the connection and builds the channel for future two-way communication.
- The client connects to the CMG over HTTPS port 443.
4. The CMG forwards the client communication over the existing connection to the on-premises CMG connection point. You don’t need to open any inbound firewall ports. 5. The CMG connection point forwards client communication to the on-premises management and software update points.
- All Co-Management Video Tutorial
- Overview Windows 10 Co-Management with Intune and SCCM Custom
- Report to Identify Machines Connected via SCCM CMG
- How to Setup Co-Management – Introduction – Prerequisites Part 1
- How to Setup Co-Management – Firewall Ports Proxy Requirements Part 2(This Post)
- Setup Co-Management – AAD Connect UPN Suffix Part 3
- Setup Co-Management – CA PKI & Certificates Part 4
- Setup Co-Management Cloud DP Azure Blob Storage Part 5
- Setup Co-Management Azure Cloud Services CMG Part 6
- SCCM Configure Settings for Client PKI Certificates Part 7
- How to Setup SCCM Co-Management to Offload Workloads to Intune – Part 8
- How to Deploy SCCM Client from Intune – Co-Management – Part 9
- End User Experience of Windows 10 Co-Management – Part 10
Some Additional Notes with the Real-world Scenario
Port 10140-10155 – CMG Connection Point connects to the first VM instance on port 10140 via TCP-TLS1 -The 2nd VM instance uses port 10141 up to the sixteenth(16th) on port 10155. Port 443 – If the CMG connection point can’t connect to the CMG via TCP-TLS1, it relates to the Azure network Load Balancer over HTTPS 443 only for one VM instance.
| Some Additional Notes with the Real-world Scenario |
|---|
| 10124-10139 – More than 2 CMG VMs with HTTPS connection – CMG_VM#1 = 10124 CMG_VM#2 = 10125 CMG_VM#3 = 10126 |
| CMG VMs connect TCP-TLS connection – CMG_VM#1 = 10140 CMG_VM#2 = 10141 CMG_VM#3 = 10142 |
| ONLY one CMG VM with HTTPS (443) connection – CMG_VM#1 = 443 |
| The following table will help you better understand the firewall port details for Co-Management, CMG, and CDP. |
Most Intune communications are via standard HTTP/HTTPS (80 & 443 ports), with no option to customize that communication. However, SCCM allows having custom ports for many contacts. CMG, CDP, and Intune communications are NOT possible via custom ports.
| From | To | TCP-TLS | TCP | Description | Direction |
|---|---|---|---|---|---|
| Client | Cloud DP (Azure) | 443 | HTTPS | Unidirection | |
| Client | Azure Cloud Management Gateway (CMG) | 443 | HTTPS Communication | Unidirection | |
| Site System – CMG connection point | Software Update Point (SUP) | 80 or 443/ 8530 or 8531 | HTTPS Communication | Unidirection | |
| Site System – CMG connection point | Management Point (MP) | 443 | HTTPS Communication | Unidirection | |
| Site System – CMG connection point #1 | Azure Cloud Management Gateway (CMG) VM#1 = 10124 | 10124 | HTTPS Communication | Unidirection | |
| Site System – CMG connection point #2 | Azure Cloud Management Gateway (CMG) VM#2 = 10125 | 10125 | HTTPS Communication | Unidirection | |
| Site System – CMG connection point #1 | Azure Cloud Management Gateway (CMG) VM#1 = 10140 | 10140 | TCP-TLS Communication | Unidirectional | |
| Site System – CMG connection point #2 | Azure Cloud Management Gateway (CMG) VM#2= 10141 | 10141 | TCP-TLS Communication | Unidirectional | |
| Site System – CMG connection point | Azure Cloud Management Gateway (CMG) – ONLY one CMG VM with HTTPS 443 | 443 | HTTP | Unidirectional |
SCCM Intune Custom Port Options?
However, some of the subsequent communications are possible only via predefined ports. SCCM does not allow you to configure ports for the following types of communication
| Site Server | Cloud DP | 443 | HTTP | Unidirectional |
- SCCM CAS/Standalone Primary Site to Primary/Secondary site
- SCCM CAS/Primary Site server to site system (MP/SUP/DP..)
- SCCM console to SMS Provider
- SCCM console to the Internet
- Connections to cloud services, such as Microsoft Intune and CDPs
Internet Proxy Exceptions for Co-Management, CDP, and CMG
SCCM service connection point & CMG connection point site system roles require an internet connection. Most organizations may not have direct internet connectivity from their servers. All those communications should go through internet proxy servers.
The TCP-TLS connection between the CMG connection point site system and Azure CMG service doesn’t support an internet proxy. However, the SCCM CMG connection point supports an internet proxy via TCP ports, as mentioned in the above table.
Co-managed devices connect to the corporate network (LAN) or the Internet to get the policies and deployments from Intune and SCCM. When the co-managed devices connect to the corporate LAN, you may need to have some proxy exception to connect to the Internet.
Co-managed devices require Intune connectivity. Hence, they are Intune-managed devices and need configurations that allow all users to access services through firewalls/proxies. The following tables list the ports and services that the Intune client accesses.
| Proxy Exception URLs | Description |
|---|---|
| https://manage.windowsazure.com/ | ManagementPortalURL |
| https://manage.windowsazure.com/publishsettings/index | PublishSettingsURL |
| https://management.core.windows.net/ | ServiceManagementEndpoint |
| https://management.azure.com/ | ResourceManagerEndpoint |
| https://login.microsoftonline.com/ | ActiveDirectoryEndpoint |
| https://gallery.azure.com/ | GalleryEndpoint |
| https://vault.azure.net/ | KeyVaultEndpoint |
| https://graph.windows.net/ | GraphEndpoint |
| core.windows.net | StorageEndpointSuffix |
| database.windows.net | SQLDatabaseDNSSuffix |
| trafficmanager.net | TrafficManagerDNSSuffix |
| vault.azure.net | KeyVaultDNSSuffix |
| servicebus.azure.com | ServiceBusEndpointSuffix |
| cloudapp.net | CloudServiceSuffix |
| *.akamaiedge.net | SCCM Updates and servicing |
| *.akamaitechnologies.com | SCCM Updates and servicing |
| *.manage.microsoft.com | SCCM Updates and servicing |
| go.microsoft.com | SCCM Updates and servicing |
| blob.core.windows.net | SCCM Updates and servicing |
| download.microsoft.com | SCCM Updates and servicing |
| download.windowsupdate.com | SCCM Updates and servicing |
| sccmconnected.a01.cloudapp.net | SCCM Updates and servicing |
| *manage.microsoft.com | Microsoft Intune |
| https://bspmts.mp.microsoft.com/V | Microsoft Intune |
| https://login.microsoftonline.com/{TenantID} | Microsoft Intune |
| download.microsoft.com | Windows 10 servicing |
| https://go.microsoft.com/fwlink/?LinkID=619849 | Windows 10 servicing |
Download Firewall & Proxy Exception Cheat Excel Spreadsheet
I have uploaded the spreadsheet with co-management. Download the SCCM CB Co-management, CDP, and CMG firewall-proxy Excel sheet. This spreadsheet can help you fill your organization’s firewall and proxy exception rule.
Download Co-management Firewall & Proxy Spreadsheet
Resources:-
- Proxy server support for SCCM
- Intune Proxy Settings and Firewall settings
- Intune & SCCM Internet Access Requirements
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP from 2015 onwards for consecutive 10 years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His main focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career etc…


Quick question – since all communication from clients to the CMG go via https, the certificate chain needs to be validated AND the CRL needs to be checked. So in order for all this to properly work, at least one CRL location must be available from the internet, meaning I need a publically available CRL correct? Or is there a way around this?
The SSL certs used by the service (also used in SCCM while creating the CMG) needs to be trusted by the SCCM client devices. If it’s issued by the same CA, then you’re good. If you get a public cert, then you’re likely good (because some of the public CAs are already trusted by Windows).
Public CRL is a best practice. If you don’t make it public, then you need to disable CRL checks.
We can use the same command line copy from Co-Management and you can add /nocrlcheck in the command link if you don’t have public CRL.
In SCCM console you have to clear the CRL & and select the option the client to use PKI
Cloud managment Gateway Client connectivity issue ResponseHeader: HTTP/1.1 401 Unauthorized in cmgservice logs – Can you please help me on this
Are you running Azure AD discovery? What is the error you are getting in CCM_STS.log ?
are you referring cloud connection sts worker log.
It is having no error and connection point is connected to azure
in the http handler and cmcservices.log we are getting this error
Now I am getting error 404 not found error
Can you please let me know what is the default setting in IIS for https management point?
Also i need to know whether I need to check ssl setting for all the mp virtual directory (ccm_client,sms_mp,sms_mp_altauth)in IIS?
Can you please let me know which log you are referring ?
CCM_STS.log .. IIS default settings – https://www.anoopcnair.com/sccm-configmgr-default-iis-configurations-troubleshooting-issues/
https://www.anoopcnair.com/best-practices-related-iis-sccm-sup-wsus-setup/
But there is no special configuration other than binding https certs (if I’m not wrong)
nice article thanks!
I think however sccmconnected.a01.cloudapp.net should be sccmconnected-a01.cloudapp.net
thanks a lot
Hey Anoop,
We are running enhanced http option for setup for CMG. It is working, however keeps getting disconnected daily. This is due to the “SMS_SITE_BACKUP” stopping all services. If i try to Restart the “SMS_EXECUTIVE” service and stop / start the CMG service the next day sometimes connects the CMG again.
Proxy options set on MP:
1. port 8081
2. port 8080
3. port 8080 + use service account with full internet access
4. port 8081 + use service account with full internet access
Which one is the correct one to set?
Looking into the SMS_CLOUD_PROXYCONNECTOR.log
• 14/08/19 – 4:05pm tested changing proxy to use port 8081 no service account
• The CMG re-connected via a service stop/start (Status: Connected)
• 7.50:48pm – SMS_CLOUD_PROXYCONNECTOR.log – the host stop has been called, shutting down 1
• 7:51:25pm: Trying to build TCP connection 73c447b6-636c-4d1e-90e7-168bfa7b1126 with server WIN10EQCCMG.CLOUDAPP.NET:10140
• 7.51.25pm: ERROR: Failed to build Http connection 35563795-b27e-43d2-a74b-44250162b259 with server WIN10EQCCMG.CLOUDAPP.NET:443
• Continuous errors since and currently disconnected.
Any help or suggestions would be great.
Thanks
B
Personally I didn’t do much work on enhanced http mode. Have you already seen Vimal post on this https://www.anoopcnair.com/sccm-cmg-sccm-cloud-management-gateway-part-1/
Checkout the latest and greatest post from Vimal here https://www.anoopcnair.com/new-sccm-cmg-setup-guide-ehttp/
Hi there
You’ve covered in detail which firewall ports need to be opened.
Can I ask what client exe files need to be allowed through a third party client firewall running on Windows 10 devices in order to use CMG services eg directly download updates from Microsoft cloud?
Does the local Windows update exe need to be allowed through, do any others? Can’t find anything online on this.
Regards
Tom