Let’s discuss how to Collect Serial Number Alarms Breach Info Security Breach and More using Intune Inventory. The System Enclosure property gives information about the outer case of the computer, also called the chassis. It includes details like whether the device has a built-in alarm, if any part of the case has been opened or tampered with, and whether a lock is available on the device.
It also shows the make and model of the case and reports any security issues, such as a breach or warning. This helps IT teams keep track of the physical safety and condition of each device. This feature works only on Windows devices.
It helps collect the same type of hardware details from all Windows systems, allowing IT administrators to easily track and manage devices across their organization, no matter how varied the hardware setup is.
This post covers everything you need to know about how Intune inventory collects and displays information related to the system enclosure and its security details. It explains how data such as chassis type, lock status, security breaches, and other physical characteristics are collected and presented within Intune for Windows devices.
Table of Contents
How Intune Inventory Collects and Displays System Enclosure and Security Details
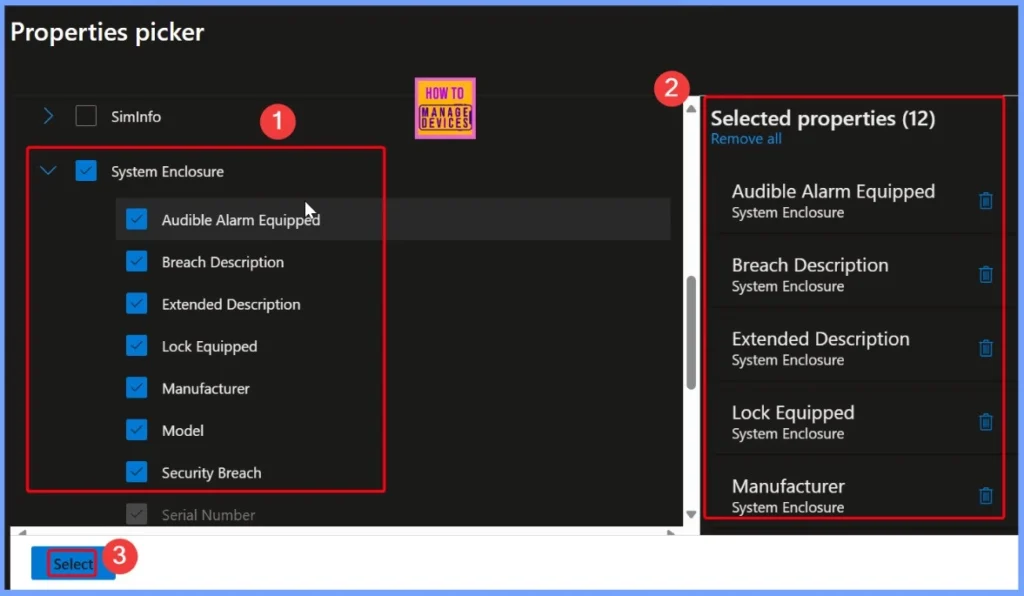
The properties collected under the System Enclosure section in Intune offer valuable insights that help IT admins and organizations maintain better control over their hardware assets. Information such as Serial Number, Manufacturer, and Model helps with accurate asset tracking and inventory management.
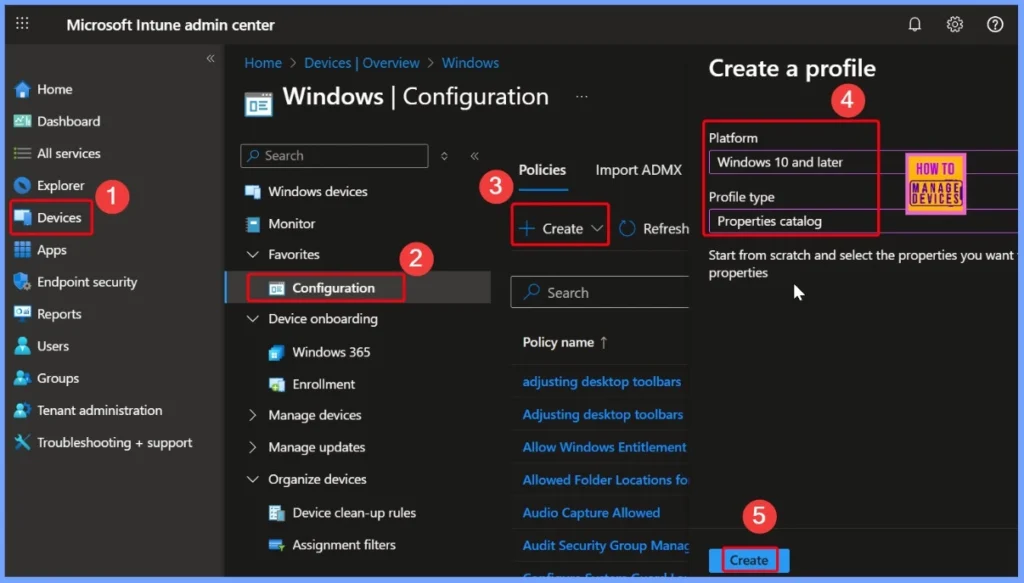
- Go to the Microsoft Intune admin center and sign in with your account.
- In the left-hand menu, click Devices.
- Select Manage devices, then choose Configuration.
- Click on Create and select New Policy.
- In the setup window:
- Choose Windows 10 and later as the platform.
- From the list of profile types, select Settings catalog
- How to use Intune to Collect BIOS Information from Windows Devices
- How to Retrieve CPU Information from Windows Devices using Intune
- How to Collect Disk Drive ID Details using Intune Property Catalog
Security Related Fields
Security-related fields such as LockEquipped, AudibleAlarmEquipped, VisibleAlarmEquipped, and SecurityBreach allow admins to monitor physical security features and detect any unauthorized access or tampering attempts.
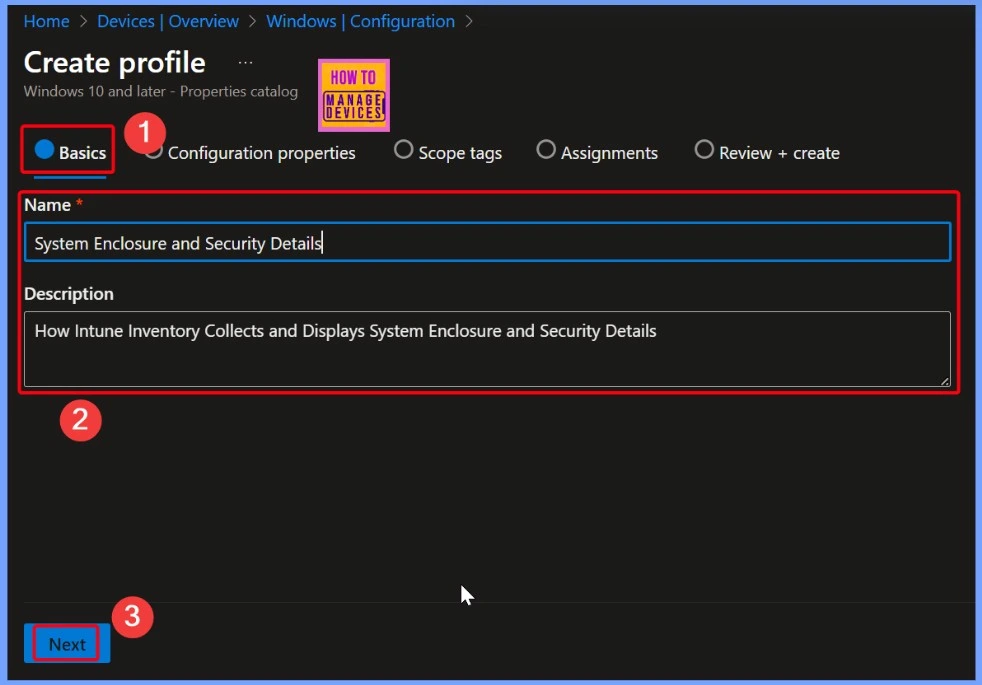
- Name – System Enclosure and Security Details
- Description – How Intune Inventory Collects and Displays System Enclosure and Security Details
Descriptions
Descriptions such as BreachDescription, ExtendedDescription, and Status provide more context to assess device conditions. Additionally, details such as SmBiosAssetTag and SKU support hardware auditing and lifecycle planning. By gathering all of this data, Intune enables organizations to proactively manage device health, security, and compliance across their Windows fleet.
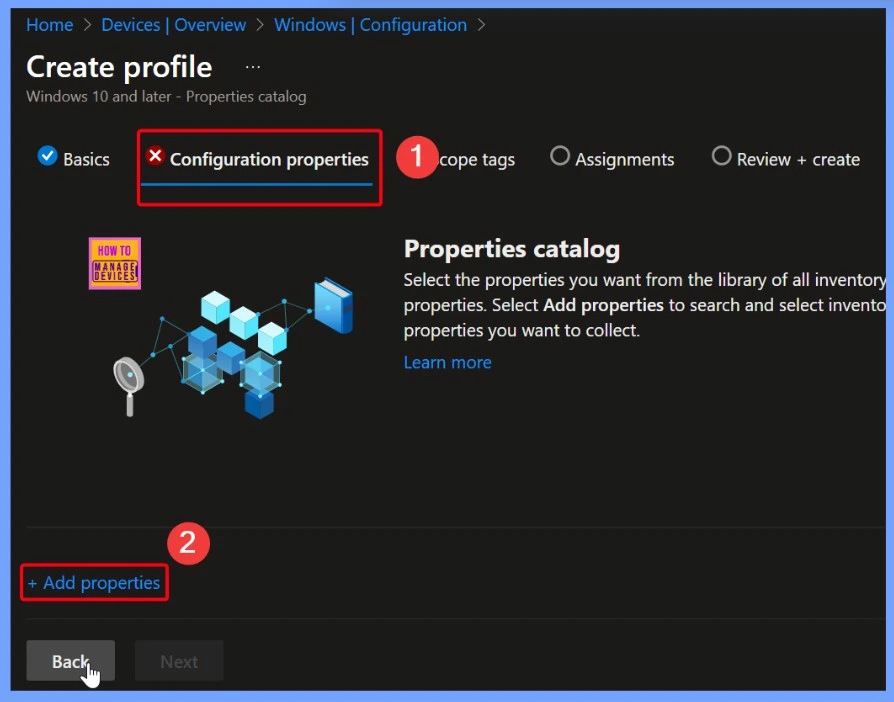
- Select the +Add properties hyperlink from the below window
Property and Supported Platforms
The System Enclosure is the outer case of a computer that holds and protects all the important parts such as the motherboard, processor, hard drive, and power supply. It keeps everything in place and safe from damage. This case is also known as the chassis and can come in different shapes and sizes, depending on whether the device is a desktop, laptop, or tablet.
| Property | Description | Supported platforms |
|---|---|---|
| SerialNumber | The serial number of the chassis. | Windows single and multi device query |
| AudibleAlarmEquipped | If TRUE, the frame is equipped with an audible alarm. | Windows single and multi device query |
| BreachDescription | If provided, gives a more detailed description of a detected security breach. | Windows single and multi device query |
| ChassisTypes | A comma-separated list of chassis types, such as Desktop or Laptop. | Windows single device query |
| ExtendedDescription | An extended description of the chassis if available. | Windows single and multi device query |
| LockEquipped | If TRUE, the frame is equipped with a lock. | Windows single and multi device query |
| Manufacturer | The manufacturer of the chassis. | Windows single and multi device query |
| Model | The model of the chassis. | Windows single and multi device query |
| SecurityBreach | The physical status of the chassis such as Breach Successful, Breach Attempted, etc. | Windows single and multi device query |
| SmBiosAssetTag | The assigned asset tag number of the chassis. | Windows single and multi device query |
| Sku | The Stock Keeping Unit number if available. | Windows single and multi device query |
| Status | If available, gives various operational or nonoperational statuses such as OK, Degraded, and Pred Fail. | Windows single and multi device query |
| VisibleAlarmEquipped | If TRUE, the frame is equipped with a visual alarm. | Windows single and multi device query |
- How to Track Device Battery Information using Intune Property Catalog
- How to Collect Physical and Virtual Memory Information using Intune Properties Catalog
- Intune Managing OneDrive File Downloads for Low Disk Space
Audible Alarm Equipped
The System Enclosure section in Intune gives details about the physical case of a computer. This information is automatically refreshed every 24 hours, so IT admins always have up-to-date data about the physical security and condition of the device.
- Audible Alarm Equipped – Refresh every 24 hours
- Breach Description – Refresh every 24 hours
- Extended Description – Refresh every 24 hours
- Lock Equipped – Refresh every 24 hours
- Manufacturer – Refresh every 24 hours
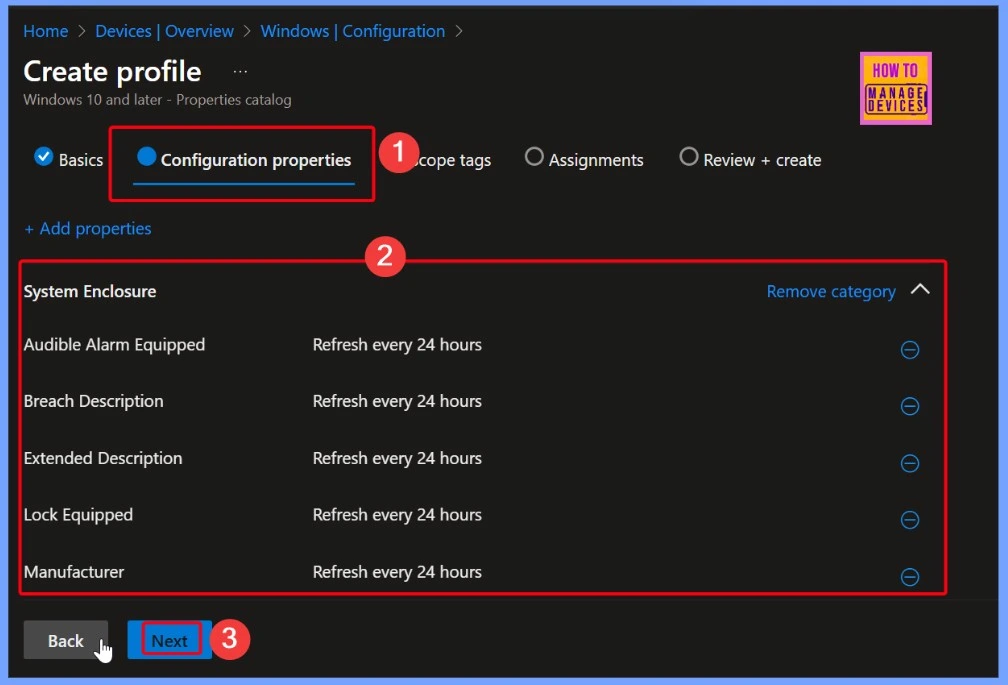
Divide Management Responsibilities based on Region
Scope tags are useful because they help divide management responsibilities based on region, department, or specific roles within an organization. This allows different IT teams to focus only on the resources they are responsible for. By limiting access to only what’s necessary, scope tags also improve security and reduce the risk of unauthorized changes.
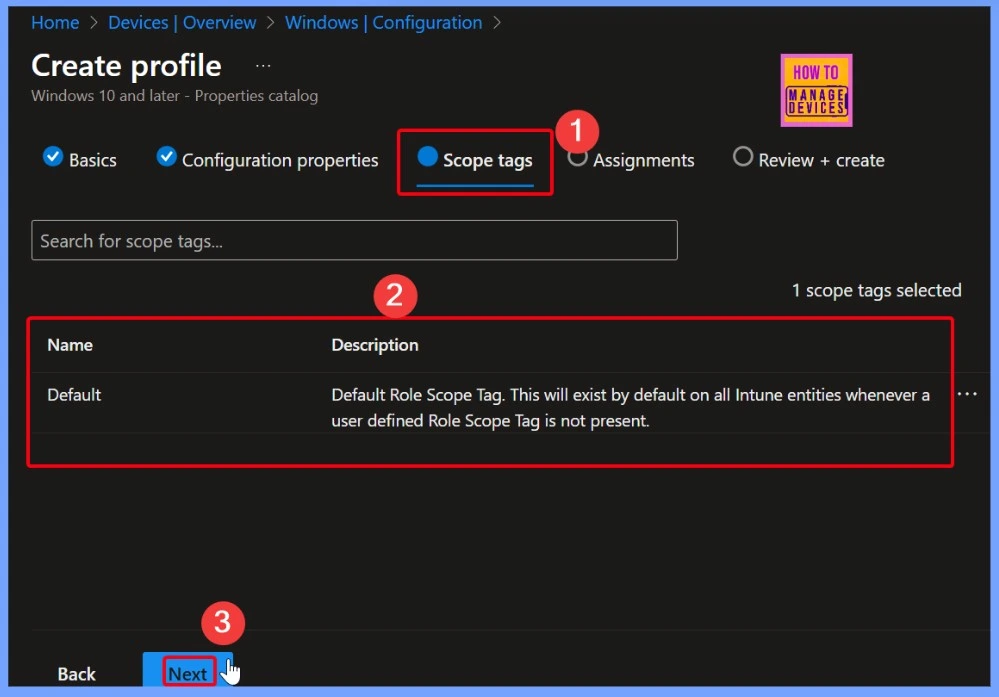
Configuration Reaches the Right Endpoint
Without proper assignment, a policy or app does not apply, which could lead to non-compliant or insecure devices. Assignments ensure that the intended configuration reaches the right endpoints. The below screenshot helps you to show more details.
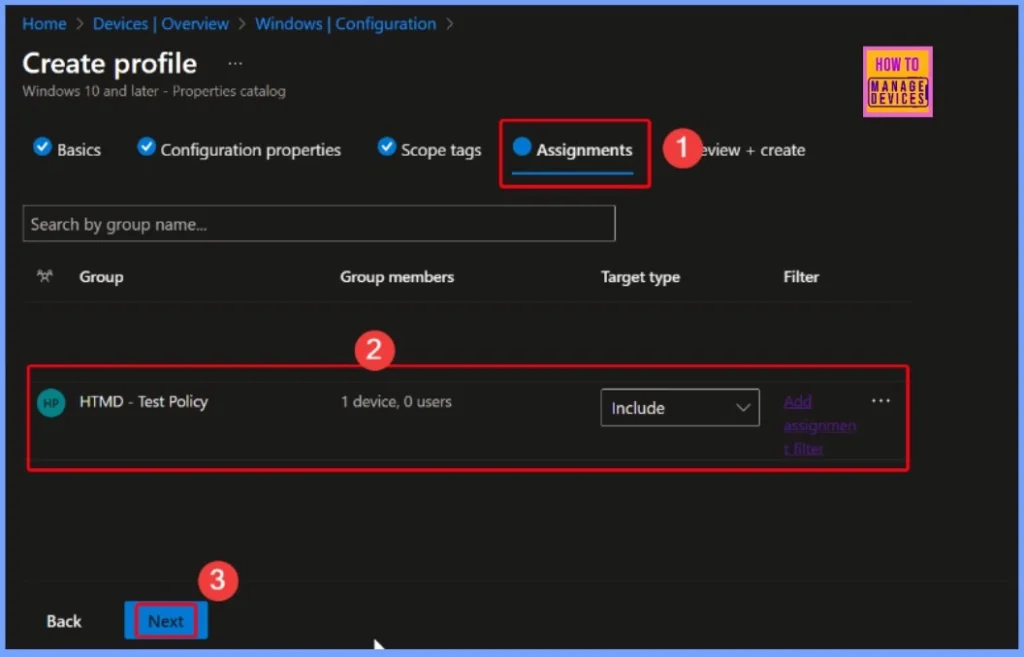
Reducing the Risk of Misconfiguration
This step gives admins a chance to double-check everything, reducing the risk of misconfiguration or accidental impact on users or devices. It ensures that policies are applied accurately and confidently across the organization.
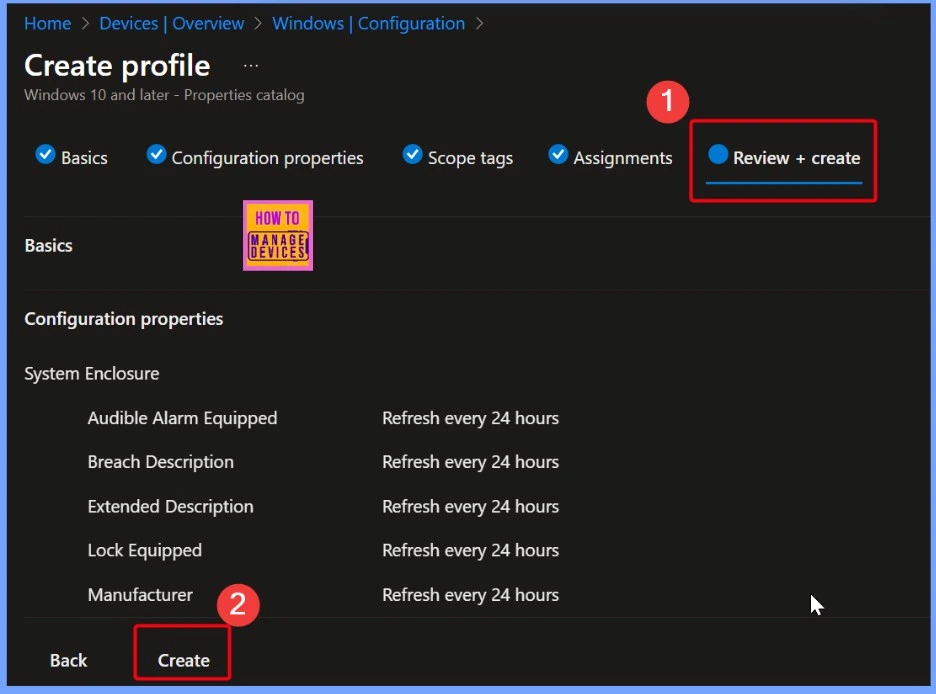
Notification Message to Confirms a Task or Action
In Microsoft Intune, a successful notification is a message that confirms a task or action has been completed without any issues. These notifications appear throughout the Intune admin center to let IT admins know that a process, like creating a policy, assigning an app, etc, is successful.
| Notification Message |
|---|
| System Enclosure and Security Details has successfully been Created |
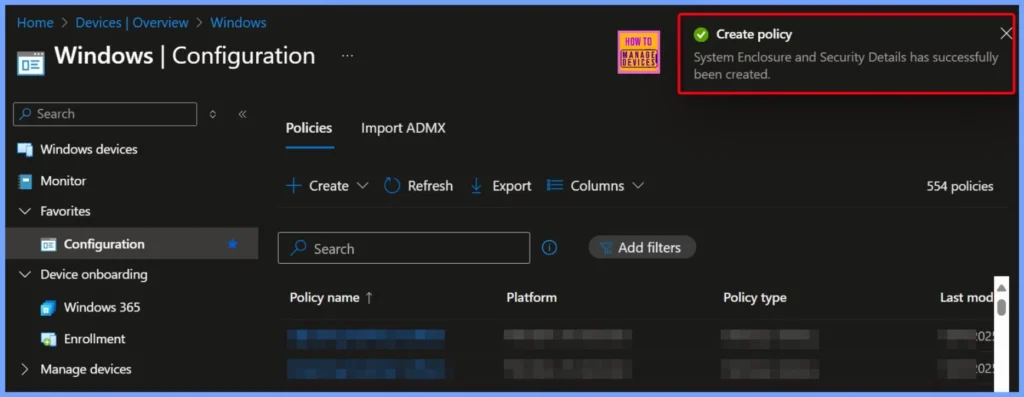
End Result
Using Resource Explorer in Intune helps IT admins by giving them detailed visibility into a device’s hardware and system information. It allows them to quickly check data such as processor details, memory, disk partitions, BIOS, and more, all in one place. Instead of needing to access the device physically or use separate tools, admins can view this information remotely, saving time and improving efficiency in managing multiple devices across the organization.
Note – Chassis Types property is currently not supported for Inventory or Device query for multiple devices.
Read More – Key Difference between Resource Explorer and Hardware Tab in Microsoft Intune
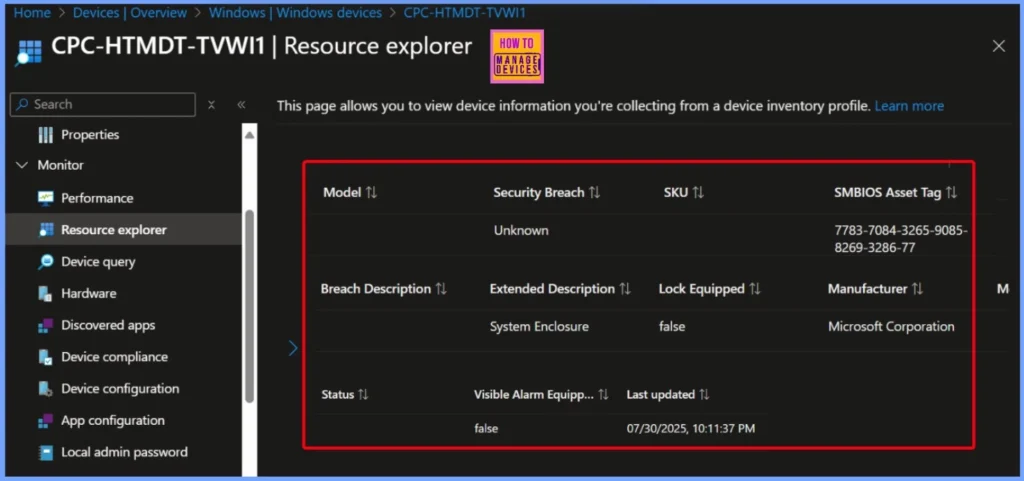
| Serial Number | Audible Alarm equipped | Breach Description | Extended Description | Lock Equipped | Manufacturer | Model | Security Breach | SKU | SMBIOS Asset Tag | Status | Visible Alarm Equipped | Last updated |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 9958-5815-4351-1673-5000-9702-23 | false | System Enclosure | false | Microsoft Corporation | Unknown | 7783-7084-3265-9085-8269-3286-77 | false | 07/30/2025, 10:11:37 PM |
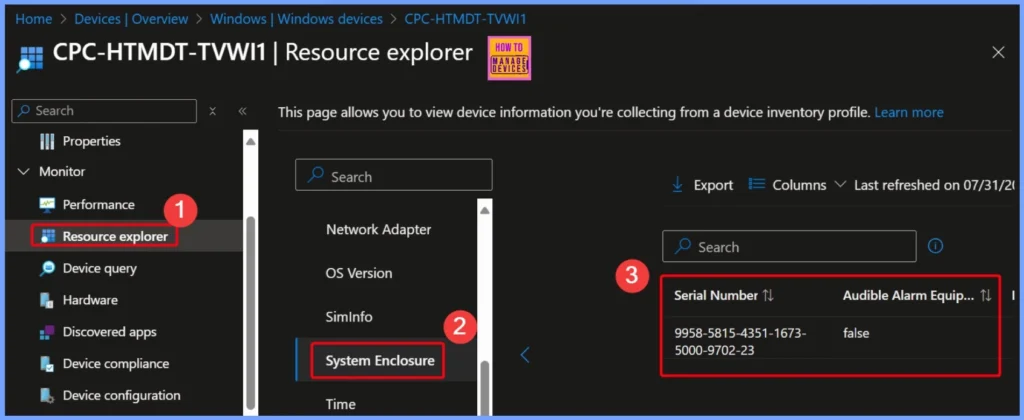
Result Status
The system enclosure does not have an audible or visible alarm, and it is not equipped with a lock. The manufacturer is listed as Microsoft Corporation, but the model and SKU information are missing. A security breach has been noted, but its nature is unknown. The SMBIOS Asset Tag and Serial Number are recorded, and the last update was on July 30, 2025, at 10:11 PM.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


