In this post, let’s examine the current Top Five Windows Security Challenges worldwide, as determined by Microsoft’s data analytics and threat intelligence.
This post is based on the Windows security session by David Weston, Katherine Holdsworth, and Ron Aquino.
Windows security improves with every release. See how Windows has a hardened OS at the core that keeps your devices protected and productive.
We’ll also offer a sneak peek at where we invest our engineering muscle to enhance Windows platform security.
Table of Contents
Top 5 Windows Security Challenges
Let’s check the top 5 Windows security challenges in today’s world.
- Phishing – Impersonating oneself as a trustworthy entity in a digital communication
- Untrusted Code – Anything coming to your network or Windows 10 device from a non-trusted source. This can be an attachment/macro virus/tricking an update install.
- Credential Harvesting – Once an attacker gets onto the machine as a malware application to steal the passwords/credentials.
- Data Theft – Losing a laptop / Remote hacker gets into your network and steals information data.
- Unpatched Vulnerabilities – Known Vulnerabilities issue with Windows 10.
More details – This is Windows security! – Microsoft Tech Community

- Ignite 2021 March Edition Intune Videos | Endpoint Manager Content | Endpoint Manager
- Top 8 MEM Intune ConfigMgr Ignite Nov 2021 Sessions
- Intune Support for Linux Platform Started Rolling out Silently
How to Stop Phishing
How can phishing be made more complicated on Windows 10 devices? Microsoft seems to suggest using Windows Hello for Business in the enterprise world to eliminate the passwords from the echo system.

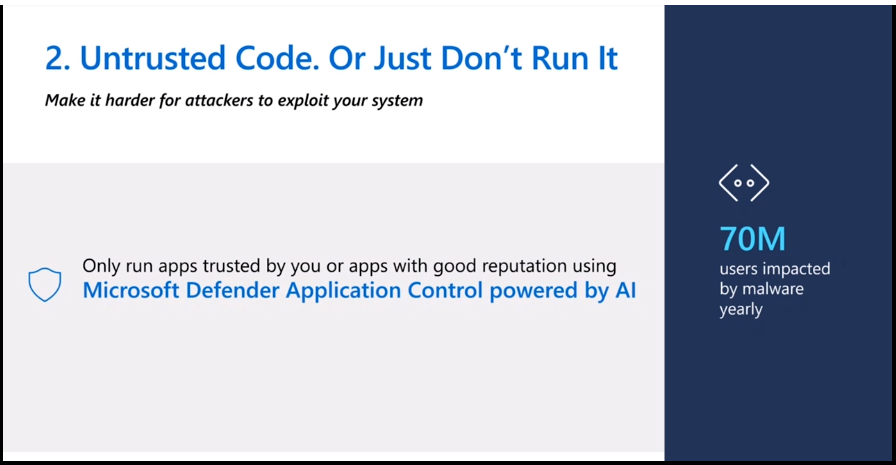
How to Isolate Untrusted Code
You can use Microsoft’s Application Guard for Office to isolate untrusted documents and files in a virtual sandbox containing the damage from bad macros.

You can use Microsoft Defender Application Control powered by AI to rate trusted sources worldwide.
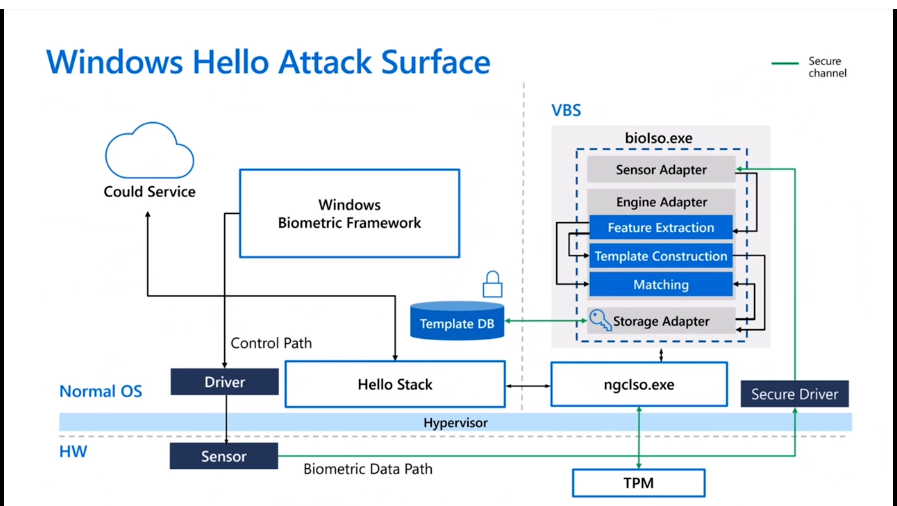
How to Prevent Credential Harvesting
With hardware-backed and VBS (Virtualization-Based Security) protection, you can raise the bar.

Windows Hello Attack Surface diagram to help to prevent Credential Harvesting.
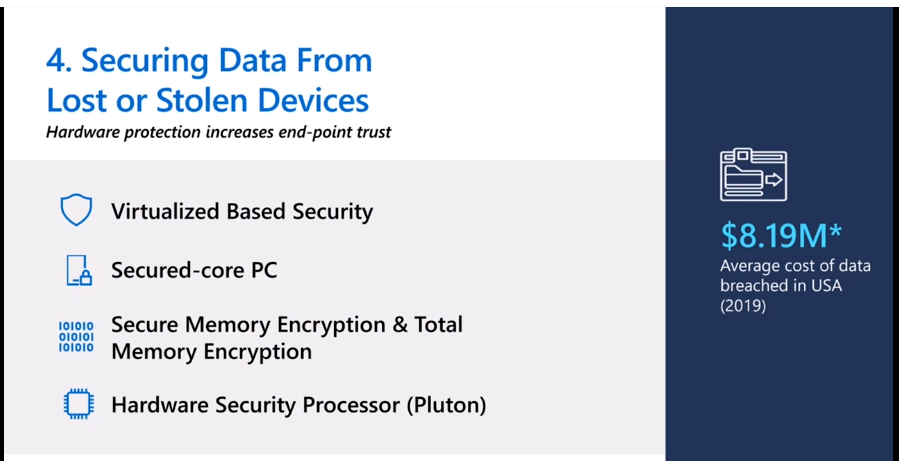
How to Prevent Data Theft in Windows 10
Securing Data from Lost or Stolen Devices with encryption and other methods listed below:
- Virtualized Based Security
- Security-core PC
- Secure Memory Encryption and Total Memory Encryption.
- Hardware Security Processor (Pluton)
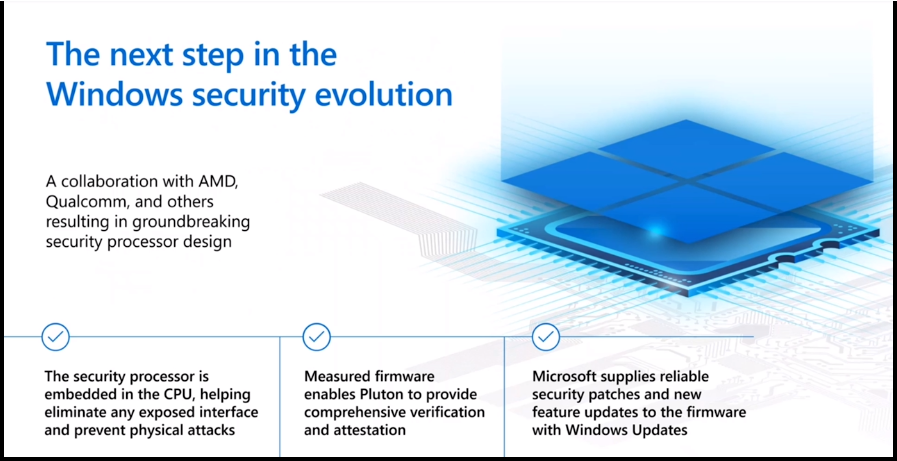
As per Microsoft, the next step in the Windows security evolution is given below:
- A collaboration with AMD, Qualcomm, and others resulted in groundbreaking security process design.
- The security processor is embedded in the CPU, helping eliminate any exposed interface and preventing physical attacks.
- Measured firmware enables Pluton to provide comprehensive verification and attestation.
- Microsoft supplied reliable security patches and new features to the firmware with Windows updates.
How to Handle Known Vulnerabilities Issues with Windows 10
Microsoft is working with internal teams and world-class PEN testers to secure their products like Windows 10. Microsoft’s security assurance and vulnerability research team focused on securing Microsoft platforms to help our developers continuously make Windows 10 safer.
The following are the strategies that Microsoft uses to secure Windows 10:
- Secure by Design
- Tools, Process, and Automation
- Mitigations
- Red Team and Vulnerability Research

Resources
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here – HTMD WhatsApp.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
